标签:
Router Switching Mechanisms
Using Standard IP switching, The following steps occur with process switching and fast switching:
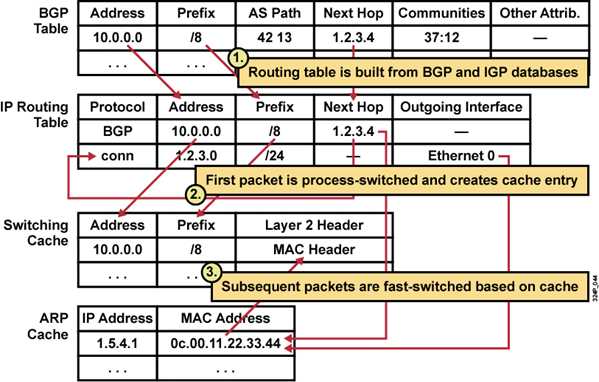
Step 1: When a BGP update is received and processed in the BGP table, an entry is creted in the routing table if it is selected as the best route.
Step 2: When the first packet arrives for this destination, the router tries to find the destination in the fast-switching cache. Because the destination is not in the fast-switching cache, process switching has to switch the packet. A recursive lookup is performed to find the outgoing interface. If the Layer 2 address is not found in the cache, an ARP request is triggered. Finally, an entry is created in the fast-switching cache.
Step 3: All subsequent packets for the same destination are fast-switched, as follows:
What is CEF Switching Architecture?
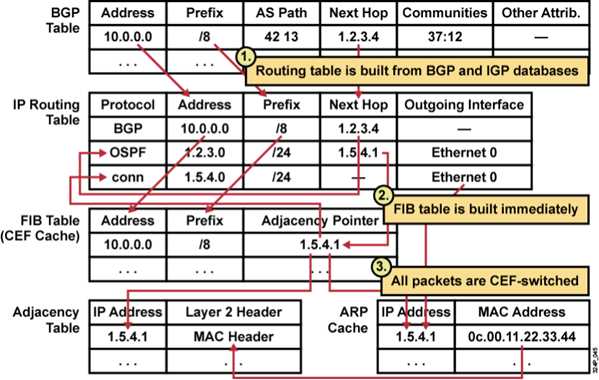
CEF uses a complete IP swiching table. the FIB table, which holds the same information as the IP routing table. The generation of entries in the FIB table is not packet-trigged but change-triggered. When something changes in the IP routing table, the change is also reflected in the FIB table.
Routers have many of the same hardware and software components that are found in other computers including:
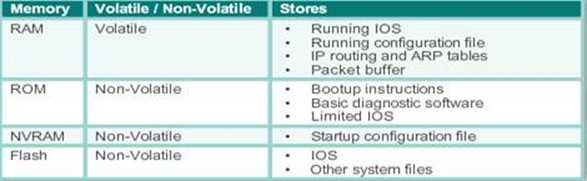
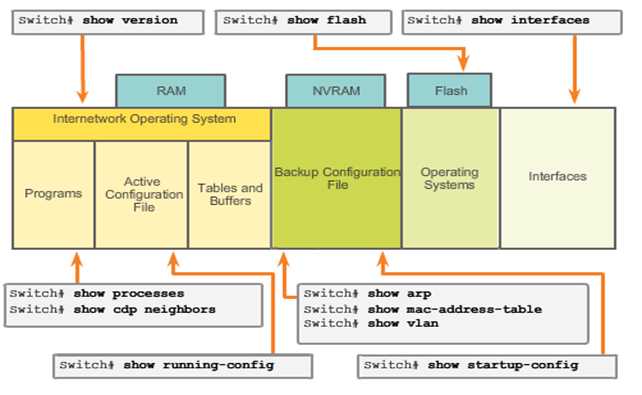
When a router powers up, it knows nothing about the network topology. It does not even know that there are devices on the other end of its links. The only information that a router has is from its own saved configuration file stored in NVRAM.
Router interfaces can be divided into two major groups (Show ip interface brief)
Routing Table
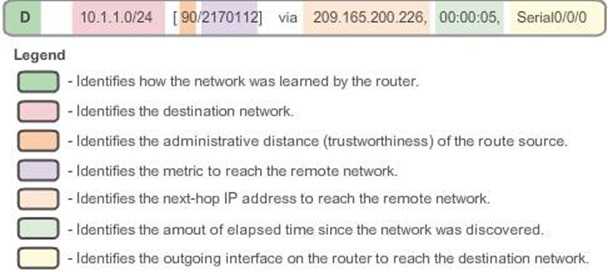
What is a gateway of last resort?
The IP address of another router.
What is the purpose of a routing protocol?
Allows a router to share information about known networks with other routers
Principle 1: "Every router makes its decision alone, based on the information it has in its own routing table."
Principle 2: "The fact that one router has certain information in its routing table does not mean that other routers have the same information."
Principle 3: "Routing information about a path from one network to another does not provide routing information about the reverse, or return path."
share information about the reliability and status of remote networks. Dynamic routing protocols perform several activities, including:
Packet forwarding involves two functions:
One of three path determinations results from this search:
Equal cost load balancing: when a router has two or more paths to a destination with equal cost metrics, then the router forwards the packets using both paths equally.
Only EIGRP supports unequal cost load balancing.
What does a router do with a packet received from one network and destined for another network?
The router performs the following three major steps:
|
Router#erase startup-config Router#reload // 清除所有现有配置
Router(config)#no ip domain-lookup //禁用DNS查找 Router(config)#line console 0 Router(config-line)#logging synchronous //IOS no longer interfere with your typing. Router(config)#no exec-timeout 0 0 //退出时间 0 min 0 sec |
|
Router(config)#hostname XXX Router(config)#enable secret XXX Router(config)#line console 0 Router(config-line)#password cisco Router(config-line)#login
Router(config)#line vty 0 4 Router(config)#password cisco Router(config)#login Router(config)#banner motd #message# R1(config)#service password-encryption R1#copy running-config startup-config |
|
R1(config)#ipv6 unicast-routing //begins sending ICMPv6 router advertisement messages R1(config)#interface type number R1(cofig-if)#description XXXX R1(config-if)#ipv6 address 2001:db8:acad:1::1/64 [link-local] [eui-64] // Configure IPv6 Address R1(config-if)#ipv6 address ipv6-address/prefix-length //create a global unicast R1(config-if)#ipv6 address ipv6-address/prefix-length eui-64 //configure a global unicast IPv6 address with an interface ID in the low-order 64 bits of the IPv6 address using the EUI-64 R1(config-if)ipv6 address ipv6-address/prefix-length link-local // create a static lik-local R1(config-if)# no shutdown
R1# show ipv6 route S1#show ip interface //display the IP interface status and configuration S1#show ip interface brief //display a brief summary of IP status and configuration S1#show ip route connected //displays a list of active directly connected networks S1#show history S1#terminal history size 200 |
Command History Feature: ctrl + p or up arrow

Perspective and Background
Routing protocols are used to facilitate the exchange of routing information between routers. Routing protocols allow routers to dynamically share information about remote networks and automatically add this information to their own routing tables.
Network discovery and Routing table maintenance
A routing protocol is a set of processes, algorithms, and messages that are used to exchange routing information and populate the routing table with the routing protocol‘s choice of best paths. The purpose of a routing protocol includes:
What are the components of a routing protocol?
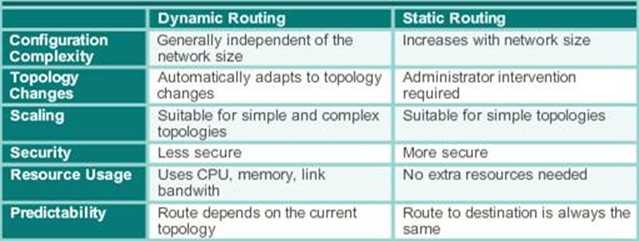
Dynamic Routing Advantages
Disadvantages:
Dynamic Routing Protocol Operation
In general, the operations of a dynamic routing protocol can be described as follows:
Classifying Dynamic Routing Protocols
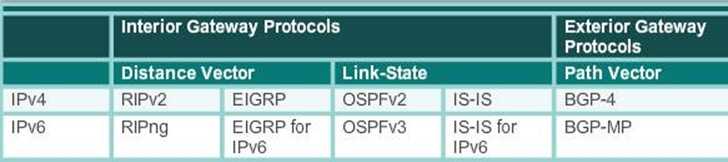
Routing protocols can be classified by their:
IGP and EGP
An autonomous system (AS) - otherwise known as a routing domain - is a collection of routers under a common administration.
Distance Vector and Link State
Distance vector protocols work best in situations where:
Link-state protocols work best in situations where:
Classful and Classless
Classful routing protocols do not send subnet mask information in routing updates.
Classless routing protocols include the subnet mask with the network address in routing updates.
Convergence
The speed of achieving convergence consists of:
Purpose of Metric
A metric is a value used by routing protocols to assign costs to reach remote networks. The metric is used to determine which path is most preferable when there are multiple paths to the same remote network.
Metrics used in IP routing protocols include:
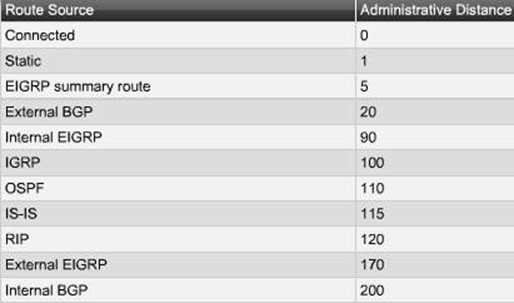
Administrative Distances
Administrative distance (AD) defines the preference of a routing source. Each routing source - including specific routing protocols, static routes, and even directly connected networks - is prioritized in order of most- to least-preferable using an administrative distance value.
标签:
原文地址:http://www.cnblogs.com/elewei/p/5063314.html