标签:
系统 : Windows xp
程序 : abexcrackme2
程序下载地址 :http://pan.baidu.com/s/1qXhyt8C
要求 : 注册机编写
使用工具 : OD
可在“PEDIY CrackMe 2007”中查找关于此程序的破文,标题为“abex‘ #2的算法分析(VB简单)”。
程序是用VB语言编写,所以可以参考下这篇文章:http://www.cnblogs.com/bbdxf/p/3793545.html,大部分反汇编出来的函数名都可以在其中查到。
话不多说,我们采用OD载入程序,并利用超级字串参考插件查找宽字符串“yep, this key is right!”,并定位调用位置。向上搜索,定位关键代码:
00403191 . 8B1D 4C104000 mov ebx, dword ptr [<&MSVBVM60.#632>>; MSVBVM60.rtcMidCharVar
00403197 > 85C0 test eax, eax ; eax为0则结束循环
00403199 . 0F84 06010000 je 004032A5
0040319F . 8D95 64FFFFFF lea edx, dword ptr [ebp-9C]
004031A5 . 8D45 DC lea eax, dword ptr [ebp-24]
004031A8 . 52 push edx
004031A9 . 50 push eax
004031AA . C785 6CFFFFFF>mov dword ptr [ebp-94], 1
004031B4 . 89BD 64FFFFFF mov dword ptr [ebp-9C], edi
004031BA . FF15 A8104000 call dword ptr [<&MSVBVM60.__vbaI4Var>; MSVBVM60.__vbaI4Var
004031C0 . 8D4D 8C lea ecx, dword ptr [ebp-74]
004031C3 . 50 push eax
004031C4 . 8D95 54FFFFFF lea edx, dword ptr [ebp-AC]
004031CA . 51 push ecx
004031CB . 52 push edx
004031CC . FFD3 call ebx
004031CE . 8D95 54FFFFFF lea edx, dword ptr [ebp-AC]
004031D4 . 8D4D AC lea ecx, dword ptr [ebp-54]
004031D7 . FFD6 call esi
004031D9 . 8D8D 64FFFFFF lea ecx, dword ptr [ebp-9C]
004031DF . FF15 0C104000 call dword ptr [<&MSVBVM60.__vbaFreeV>; MSVBVM60.__vbaFreeVar
004031E5 . 8D45 AC lea eax, dword ptr [ebp-54]
004031E8 . 8D8D 78FFFFFF lea ecx, dword ptr [ebp-88] ; ↓从字符串特点位置上获取其值
004031EE . 50 push eax ; /String8
004031EF . 51 push ecx ; |ARG2
004031F0 . FF15 80104000 call dword ptr [<&MSVBVM60.__vbaStrVa>; \__vbaStrVarVal
004031F6 . 50 push eax ; /String
004031F7 . FF15 1C104000 call dword ptr [<&MSVBVM60.#516>] ; \rtcAnsiValueBstr
004031FD . 8D95 24FFFFFF lea edx, dword ptr [ebp-DC] ; ↑传回字符码
00403203 . 8D4D AC lea ecx, dword ptr [ebp-54]
00403206 . 66:8985 2CFFF>mov word ptr [ebp-D4], ax ; 保存字符码
0040320D . 89BD 24FFFFFF mov dword ptr [ebp-DC], edi
00403213 . FFD6 call esi
00403215 . 8D8D 78FFFFFF lea ecx, dword ptr [ebp-88] ; ↓释放出字符串所占的内存
0040321B . FF15 CC104000 call dword ptr [<&MSVBVM60.__vbaFreeS>; MSVBVM60.__vbaFreeStr
00403221 . 8D55 AC lea edx, dword ptr [ebp-54]
00403224 . 8D85 24FFFFFF lea eax, dword ptr [ebp-DC]
0040322A . 52 push edx ; /var18
0040322B . 8D8D 64FFFFFF lea ecx, dword ptr [ebp-9C] ; |
00403231 . 50 push eax ; |var28
00403232 . 51 push ecx ; |saveto8
00403233 . C785 2CFFFFFF>mov dword ptr [ebp-D4], 64 ; |
0040323D . 89BD 24FFFFFF mov dword ptr [ebp-DC], edi ; |
00403243 . FF15 AC104000 call dword ptr [<&MSVBVM60.__vbaVarAd>; \__vbaVarAdd
00403249 . 8BD0 mov edx, eax
0040324B . 8D4D AC lea ecx, dword ptr [ebp-54]
0040324E . FFD6 call esi
00403250 . 8D55 AC lea edx, dword ptr [ebp-54]
00403253 . 8D85 64FFFFFF lea eax, dword ptr [ebp-9C]
00403259 . 52 push edx
0040325A . 50 push eax
0040325B . FF15 94104000 call dword ptr [<&MSVBVM60.#573>] ; MSVBVM60.rtcHexVarFromVar
00403261 . 8D95 64FFFFFF lea edx, dword ptr [ebp-9C]
00403267 . 8D4D AC lea ecx, dword ptr [ebp-54]
0040326A . FFD6 call esi
0040326C . 8D4D BC lea ecx, dword ptr [ebp-44]
0040326F . 8D55 AC lea edx, dword ptr [ebp-54]
00403272 . 51 push ecx
00403273 . 8D85 64FFFFFF lea eax, dword ptr [ebp-9C]
00403279 . 52 push edx
0040327A . 50 push eax
0040327B . FF15 84104000 call dword ptr [<&MSVBVM60.__vbaVarCa>; MSVBVM60.__vbaVarCat
00403281 . 8BD0 mov edx, eax
00403283 . 8D4D BC lea ecx, dword ptr [ebp-44]
00403286 . FFD6 call esi
00403288 . 8D8D BCFEFFFF lea ecx, dword ptr [ebp-144]
0040328E . 8D95 CCFEFFFF lea edx, dword ptr [ebp-134]
00403294 . 51 push ecx ; /TMPend8
00403295 . 8D45 DC lea eax, dword ptr [ebp-24] ; |
00403298 . 52 push edx ; |TMPstep8
00403299 . 50 push eax ; |Counter8
0040329A . FF15 C0104000 call dword ptr [<&MSVBVM60.__vbaVarFo>; \__vbaVarForNext
004032A0 .^ E9 F2FEFFFF jmp 00403197
004032A5 > 8B45 08 mov eax, dword ptr [ebp+8]
004032A8 . 50 push eax
004032A9 . 8B08 mov ecx, dword ptr [eax]
004032AB . FF91 04030000 call dword ptr [ecx+304]
004032B1 . 8D95 74FFFFFF lea edx, dword ptr [ebp-8C]
004032B7 . 50 push eax
004032B8 . 52 push edx
004032B9 . FF15 38104000 call dword ptr [<&MSVBVM60.__vbaObjSe>; MSVBVM60.__vbaObjSet
004032BF . 8BF8 mov edi, eax
004032C1 . 8D8D 78FFFFFF lea ecx, dword ptr [ebp-88]
004032C7 . 51 push ecx
004032C8 . 57 push edi
004032C9 . 8B07 mov eax, dword ptr [edi]
004032CB . FF90 A0000000 call dword ptr [eax+A0]
004032D1 . 85C0 test eax, eax
004032D3 . DBE2 fclex
004032D5 . 7D 12 jge short 004032E9
004032D7 . 68 A0000000 push 0A0
004032DC . 68 68234000 push 00402368
004032E1 . 57 push edi
004032E2 . 50 push eax
004032E3 . FF15 24104000 call dword ptr [<&MSVBVM60.__vbaHresu>; MSVBVM60.__vbaHresultCheckObj
004032E9 > 8B85 78FFFFFF mov eax, dword ptr [ebp-88]
004032EF . BF 08000000 mov edi, 8
004032F4 . 8D95 64FFFFFF lea edx, dword ptr [ebp-9C]
004032FA . 8D4D CC lea ecx, dword ptr [ebp-34]
004032FD . C785 78FFFFFF>mov dword ptr [ebp-88], 0
00403307 . 8985 6CFFFFFF mov dword ptr [ebp-94], eax
0040330D . 89BD 64FFFFFF mov dword ptr [ebp-9C], edi
00403313 . FFD6 call esi
00403315 . 8D8D 74FFFFFF lea ecx, dword ptr [ebp-8C]
0040331B . FF15 C8104000 call dword ptr [<&MSVBVM60.__vbaFreeO>; MSVBVM60.__vbaFreeObj
00403321 . 8D55 BC lea edx, dword ptr [ebp-44]
00403324 . 8D45 CC lea eax, dword ptr [ebp-34]
00403327 . 52 push edx ; /var18
00403328 . 50 push eax ; |var28
00403329 . FF15 58104000 call dword ptr [<&MSVBVM60.__vbaVarTs>; \__vbaVarTstEq
0040332F . 66:85C0 test ax, ax ; 判断核心
00403332 . 0F84 D0000000 je 00403408
以上,就是关键算法,其实注册算法相当简单:用户名字符+0x64即序列号。
没有学过VB的朋友对于其相当奇葩的函数调用和变量引用会理解的相对很吃力。这个crackme发布于1999年,2007年它的破文在看雪论坛发表。而今天,2016年1月12日由我来破解这个程序。时隔17年,时代变了,技术不断更新,VB语言也渐渐没落了。也许有一天,VB会被彻底淘汰。但对于曾用VB做开发,或是曾逆向过VB程序的程序员来说,我们会将它存入一个不知名的文件夹,连同过去的记忆一并,深埋心底。
好了,过去归于过去。现在的路还要好好的走。我们打开http://www.cnblogs.com/ZRBYYXDM/p/5115596.html中搭建的框架,并修改OnBtnDecrypt函数如下:
void CKengen_TemplateDlg::OnBtnDecrypt()
{
// TODO: Add your control notification handler code here
CString str;
GetDlgItemText( IDC_EDIT_NAME,str ); //获取用户名字串基本信息。
int len = str.GetLength();
if ( len >= 4 ){ //格式控制。
CString PassWord = "";
CString Temp = "";
for ( int i = 0 ; i != 4 ; i++ ){
Temp.Format( "%X",( str[i] + 0x64 ) );
PassWord += Temp;
}
SetDlgItemText( IDC_EDIT_PASSWORD,PassWord );
}
else
MessageBox( "用户名格式错误!" );
}
再在OnInitDialog中添加此代码修改标题:SetWindowText(_T("abexcrackme2_Keygen"));
运行效果:
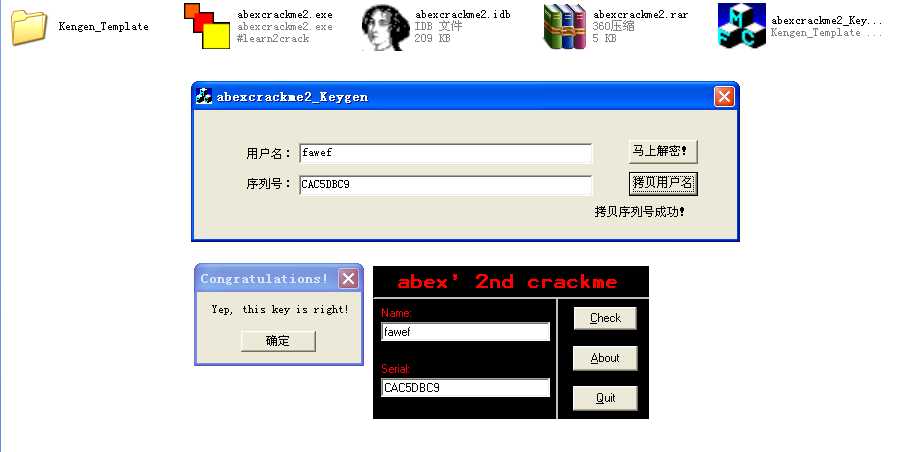
标签:
原文地址:http://www.cnblogs.com/ZRBYYXDM/p/5123920.html