标签:
WinDbg使用有点麻烦,还要符号表什么的。试了下,感觉显示很乱,分析的也不够全面。。。
试试其他的吧!今天电脑蓝屏了,就使用其dump文件测试,如下:
1、首先,最详细的,要属Osr Online这个在线分析网站了:
打开其分析地址:http://www.osronline.com/page.cfm?name=analyze
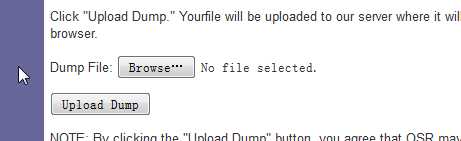
下拉,找到上传按钮(上图),将需要分析的dump文件浏览上传即可。。。dump文件一般在C:\www\minidump下
分析完成后生成的内容非常多: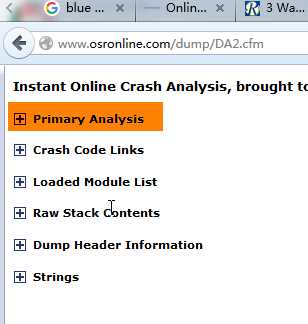
主要看第一个Primary Analysis就好了:

Crash Dump Analysis provided by OSR Open Systems Resources, Inc. (http://www.osr.com) Online Crash Dump Analysis Service See http://www.osronline.com for more information Windows 7 Kernel Version 7601 (Service Pack 1) MP (4 procs) Free x64 Product: WinNt, suite: TerminalServer SingleUserTS Built by: 7601.18741.amd64fre.win7sp1_gdr.150202-1526 Machine Name: Kernel base = 0xfffff800`04606000 PsLoadedModuleList = 0xfffff800`0484a890 Debug session time: Sun Mar 13 07:26:48.129 2016 (UTC - 4:00) System Uptime: 12 days 22:27:09.972 ******************************************************************************* * * * Bugcheck Analysis * * * ******************************************************************************* SYSTEM_SERVICE_EXCEPTION (3b) An exception happened while executing a system service routine. Arguments: Arg1: 00000000c0000005, Exception code that caused the bugcheck Arg2: fffff960000c7237, Address of the instruction which caused the bugcheck Arg3: fffff88006e6e9d0, Address of the context record for the exception that caused the bugcheck Arg4: 0000000000000000, zero. Debugging Details: ------------------ TRIAGER: Could not open triage file : e:\dump_analysis\program\triage\modclass.ini, error 2 EXCEPTION_CODE: (NTSTATUS) 0xc0000005 - The instruction at "0x%08lx" referenced memory at "0x%08lx". The memory could not be "%s". FAULTING_IP: win32k!HmgLockEx+a3 fffff960`000c7237 0fb7430c movzx eax,word ptr [rbx+0Ch] CONTEXT: fffff88006e6e9d0 -- (.cxr 0xfffff88006e6e9d0) rax=fffff900c0210000 rbx=0000000000000000 rcx=fffffa800cc05b50 rdx=fffff900c0210000 rsi=0000000000000000 rdi=fffff900c0210000 rip=fffff960000c7237 rsp=fffff88006e6f3b0 rbp=0000000000000000 r8=0000000000000001 r9=0000000000000000 r10=0000000000000000 r11=fffff88006e6f418 r12=000000006601ac00 r13=0000000000000000 r14=0000000000000001 r15=0000000000000001 iopl=0 nv up ei pl zr na po nc cs=0010 ss=0000 ds=002b es=002b fs=0053 gs=002b efl=00010246 win32k!HmgLockEx+0xa3: fffff960`000c7237 0fb7430c movzx eax,word ptr [rbx+0Ch] ds:002b:00000000`0000000c=???? Resetting default scope CUSTOMER_CRASH_COUNT: 2 DEFAULT_BUCKET_ID: WIN7_DRIVER_FAULT BUGCHECK_STR: 0x3B PROCESS_NAME: dwm.exe CURRENT_IRQL: 0 LAST_CONTROL_TRANSFER: from fffff9600028dc00 to fffff960000c7237 STACK_TEXT: fffff880`06e6f3b0 fffff960`0028dc00 : fffff900`cddb1320 000006ff`31355348 fffff900`c00cd010 fffff900`d3bc6010 : win32k!HmgLockEx+0xa3 fffff880`06e6f420 fffff960`001e3a4c : fffff900`cddb1320 fffff900`cddb1320 fffff900`c00cd010 fffff900`c00cd070 : win32k!SFMLOGICALSURFACE::OwnsSurfaceCleanup+0x40 fffff880`06e6f450 fffff960`001570f9 : fffff900`00000001 fffff900`d3bc6028 00000000`00000000 00000029`00000029 : win32k!GreTransferDwmStateToSpriteState+0xf4 fffff880`06e6f540 fffff960`0015768d : 00000000`00000001 00000000`00000000 00000000`00000001 fffff960`00000000 : win32k!zzzDecomposeDesktop+0x139 fffff880`06e6f5d0 fffff960`0012c40b : fffffa80`0c132690 fffff880`06e6fae0 00000000`00000001 00000000`00000000 : win32k!xxxDwmStopRedirection+0x69 fffff880`06e6f620 fffff960`000cad71 : 00000000`00000000 00000000`00000000 fffff900`c04010e0 fffffa80`0cc05b00 : win32k!xxxDwmProcessShutdown+0x3b fffff880`06e6f650 fffff960`000ef8d3 : fffff900`c2197c48 fffff900`c2197c20 fffff900`c2197c20 fffff900`c2197c20 : win32k!xxxDestroyThreadInfo+0x5a9 fffff880`06e6f720 fffff960`000c6c10 : 00000000`00000000 fffffa80`0cc05b50 fffffa80`0cc05b50 00000000`00000001 : win32k!UserThreadCallout+0x93 fffff880`06e6f750 fffff800`04952615 : 00000000`00000000 00000000`00000000 00000000`00000000 fffffa80`0cc05b00 : win32k!W32pThreadCallout+0x78 fffff880`06e6f780 fffff800`04938a75 : 00000000`c0000005 00000000`00000000 00000000`78457300 00000000`00000000 : nt!PspExitThread+0x285 fffff880`06e6f880 fffff800`0466e6fa : 00000000`00000002 fffffa80`0cc05c58 fffff880`06e6fa10 fffff800`047f7e80 : nt!PsExitSpecialApc+0x1d fffff880`06e6f8b0 fffff800`0466ea40 : 00000000`000ff530 fffff880`06e6f930 fffff800`049389e8 00000000`00000001 : nt!KiDeliverApc+0x2ca fffff880`06e6f930 fffff800`0467a1f7 : fffffa80`0cc05b50 00000000`000ff418 fffff880`06e6fa88 00000000`00000000 : nt!KiInitiateUserApc+0x70 fffff880`06e6fa70 00000000`76e0186a : 00000000`00000000 00000000`00000000 00000000`00000000 00000000`00000000 : nt!KiSystemServiceExit+0x9c 00000000`000ff3f8 00000000`00000000 : 00000000`00000000 00000000`00000000 00000000`00000000 00000000`00000000 : 0x76e0186a FOLLOWUP_IP: win32k!HmgLockEx+a3 fffff960`000c7237 0fb7430c movzx eax,word ptr [rbx+0Ch] SYMBOL_STACK_INDEX: 0 SYMBOL_NAME: win32k!HmgLockEx+a3 FOLLOWUP_NAME: MachineOwner MODULE_NAME: win32k IMAGE_NAME: win32k.sys DEBUG_FLR_IMAGE_TIMESTAMP: 54ee9222 STACK_COMMAND: .cxr 0xfffff88006e6e9d0 ; kb FAILURE_BUCKET_ID: X64_0x3B_win32k!HmgLockEx+a3 BUCKET_ID: X64_0x3B_win32k!HmgLockEx+a3 Followup: MachineOwner ---------
里面提到的重点就是dwm.exe和win32k.sys。事实的确如此,今天我电脑蓝屏前,就是dwm.exe先异常的!!!
2、BlueScreenView 和 WhoCrashed
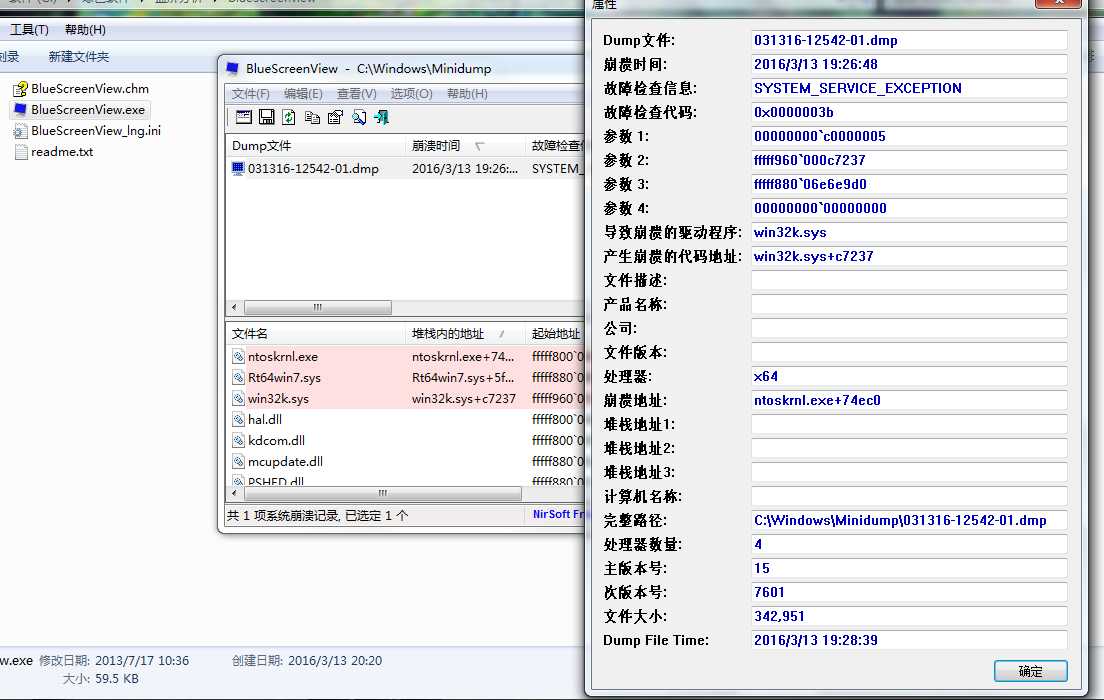
bluescreenview大小才几十kb,有绿色汉化的。打开后,它会列出C:\www\minidump下的崩溃文件。双击相应条目,弹出更详细的属性信息:
WhoCrashed home版显示的更不怎么详细,同样的dmp文件才显示如下的一点内容而已。不推荐~
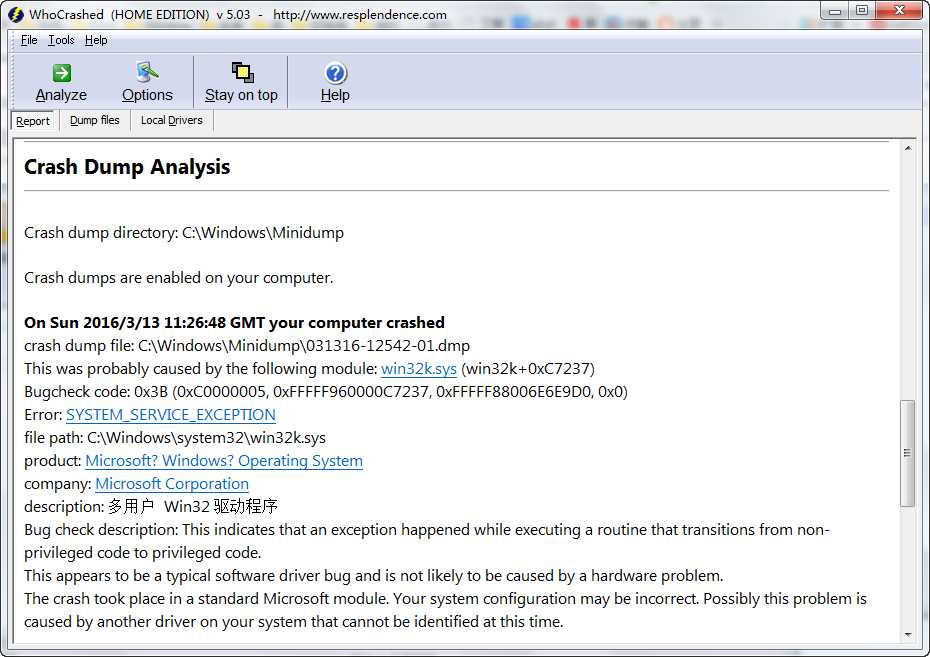
后面两个软件只定位到win32k.sys这个文件,至于更详细的内容基本没了。
推荐第一个在线分析网站,对dump文件分析的很全面!也不需要安装什么软件~~~
标签:
原文地址:http://www.cnblogs.com/sfqh/p/5273326.html