标签:
1 004016D5 . 83C4 1C add esp,0x1C 2 004016D8 . 52 push edx ; |FileName => "KwazyWeb.bit" 3 004016D9 . E8 1C010000 call <jmp.&KERNEL32.CreateFileA> ; \CreateFileA 4 004016DE . 83F8 FF cmp eax,-0x1 5 004016E1 . 74 64 je short PacMe.00401747 6 004016E3 . A3 44344000 mov dword ptr ds:[0x403444],eax 7 004016E8 . 6A 00 push 0x0 ; /pOverlapped = NULL 8 004016EA . 68 48344000 push PacMe.00403448 ; |pBytesRead = PacMe.00403448 9 004016EF . 6A 01 push 0x1 ; |BytesToRead = 0x1 10 004016F1 . 68 FA344000 push PacMe.004034FA ; |Buffer = PacMe.004034FA 11 004016F6 . FF35 44344000 push dword ptr ds:[0x403444] ; |hFile = 00000264 (window) 12 004016FC . E8 11010000 call <jmp.&KERNEL32.ReadFile> ; \ReadFile 设读取出的为number 13 00401701 . 0FB605 FA344000 movzx eax,byte ptr ds:[0x4034FA] ; 文件中第一个字符指明个数eax=number 14 00401708 . 85C0 test eax,eax 15 0040170A . 74 3B je short PacMe.00401747 ; 如果文件内容空 退出 16 0040170C . 6A 00 push 0x0 ; /pOverlapped = NULL 17 0040170E . 68 48344000 push PacMe.00403448 ; |pBytesRead = PacMe.00403448 18 00401713 . 50 push eax ; |BytesToRead 19 00401714 . 68 88324000 push PacMe.00403288 ; |Buffer = PacMe.00403288 20 00401719 . FF35 44344000 push dword ptr ds:[0x403444] ; |hFile = 00000264 (window) 21 0040171F . E8 EE000000 call <jmp.&KERNEL32.ReadFile> ; \ReadFile 22 00401724 . E8 D7F8FFFF call PacMe.00401000 ; 根据上面的eax=number读取number个字符 23 { 24 00401000 /$ 33C0 xor eax,eax 25 00401002 |. 33D2 xor edx,edx 26 00401004 |. 33C9 xor ecx,ecx 27 00401006 |. 8A0D FA344000 mov cl,byte ptr ds:[0x4034FA] 28 0040100C |. BE 88324000 mov esi,PacMe.00403288 ; ASCII 29 00401011 |> AC /lods byte ptr ds:[esi] ; 从esi指向的空间取出一个字符 30 00401012 |. 03D0 |add edx,eax ; 相加 31 00401014 |.^ E2 FB \loopd short PacMe.00401011 32 00401016 |. 8815 FB344000 mov byte ptr ds:[0x4034FB],dl ;将number个字符相加最后得到的低8位(设为k1)放到4034FB中 33 0040101C \. C3 retn 34 } 35 00401729 . 6A 00 push 0x0 ; /pOverlapped = NULL 36 0040172B . 68 48344000 push PacMe.00403448 ; |pBytesRead = PacMe.00403448 37 00401730 . 6A 12 push 0x12 ; |BytesToRead = 12 (18.) 38 00401732 . 68 E8344000 push PacMe.004034E8 ; |Buffer = PacMe.004034E8 39 00401737 . FF35 44344000 push dword ptr ds:[0x403444] ; |hFile = 00000264 (window) 40 0040173D . E8 D0000000 call <jmp.&KERNEL32.ReadFile> ; \ReadFile 此处读取的是在number之后的字符串
1 ;这里可以猜测key的组成为 : n(指代后面有n位username) n位字符 18个要跟n位进行异或的字符 2 00401742 . E8 82F9FFFF call PacMe.004010C9 ; 验证核心 3 { 4 004010C9 /$ 55 push ebp 5 004010CA |. 8BEC mov ebp,esp 6 004010CC |. 83C4 FC add esp,-0x4 7 004010CF |. 68 65334000 push PacMe.00403365 8 ; /String2 = 9 ; **************** 10 ; C*......*...**** 11 ; .*.****...*....* 12 ; .*..**********.* 13 ; ..*....*...*...* 14 ; *.****.*.*...*** 15 ; *.*....*.******* 16 ; ..*.***..*.....* 17 ; .*..***.**.***.* 18 ; ...****....*X..* 19 ; **************** 20 004010D4 |. 68 BC314000 push PacMe.004031BC ; |String1 = PacMe.004031BC 21 004010D9 |. E8 3A070000 call <jmp.&KERNEL32.lstrcpyA> ; \lstrcpyA 22 004010DE |. C705 84314000 CC3>mov dword ptr ds:[0x403184],PacMe.004031CC ; ASCII 23 ; C*......*...**** 24 ; .*.****...*....* 25 ; .*..**********.* 26 ; ..*....*...*...* 27 ; *.****.*.*...*** 28 ; *.*....*.******* 29 ; ..*.***..*.....* 30 ; .*..***.**.***.* 31 ; ...****....*X..* 32 004010E8 |. E8 30FFFFFF call PacMe.0040101D ; 对上面的字符串和文件内容字符的和作异或 33 { 34 0040101D /$ 8A15 FB344000 mov dl,byte ptr ds:[0x4034FB] ; 第二次求和的值放到dl中 35 00401023 |. B9 12000000 mov ecx,0x12 36 00401028 |. B8 E8344000 mov eax,PacMe.004034E8 ; eax指向第三次读取的数据 37 0040102D |> 3010 /xor byte ptr ds:[eax],dl ; ds:[eax] xor k1 38 0040102F |. 40 |inc eax 39 00401030 |.^ E2 FB \loopd short PacMe.0040102D 40 00401032 \. C3 retn 41 } 42 004010ED |. C645 FE 00 mov byte ptr ss:[ebp-0x2],0x0 ; y=0 43 004010F1 |. 33C0 xor eax,eax 44 004010F3 |. 33C9 xor ecx,ecx ; 清零 45 004010F5 |> C645 FF 08 /mov byte ptr ss:[ebp-0x1],0x8 ; x=8 46 004010F9 |> 806D FF 02 |/sub byte ptr ss:[ebp-0x1],0x2 ; x=x-2=6 47 004010FD |. 0FB64D FE ||movzx ecx,byte ptr ss:[ebp-0x2] ; ecx=y=0 48 ; 每次这里拿异或后的字符其中两位(从高到低)作为移动方向 49 00401101 |. 81C1 E8344000 ||add ecx,PacMe.004034E8 ; ecx+第三次处理后字符串首地址 s 50 00401107 |. 8A01 ||mov al,byte ptr ds:[ecx] ; al = s[ecx] 51 00401109 |. 8A4D FF ||mov cl,byte ptr ss:[ebp-0x1] 52 0040110C |. D2E8 ||shr al,cl ; al >> x 53 0040110E |. 24 03 ||and al,0x3 ; al & 3 这个时候al取值有四种 代表四种方向 54 00401110 |. E8 1EFFFFFF ||call PacMe.00401033 ; 根据al的值进行移动 55 { 56 ; 0: 向上移 57 ; 1: 向右移 58 ; 2: 向下移 59 ; 3: 向左移 60 00401033 $ 55 push ebp 61 00401034 . 8BEC mov ebp,esp 62 00401036 . 83C4 F8 add esp,-0x8 63 00401039 . 8B15 84314000 mov edx,dword ptr ds:[0x403184] ; PacMe.004031CC 64 0040103F . 8955 FC mov dword ptr ss:[ebp-0x4],edx 65 00401042 . 0AC0 or al,al ; Switch (cases 0..2) 66 00401044 . 75 09 jnz short PacMe.0040104F 67 00401046 . 832D 84314000 10 sub dword ptr ds:[0x403184],0x10 ; c - 10h; Case 0 of switch 00401042 68 0040104D . EB 1F jmp short PacMe.0040106E 69 0040104F > 3C 01 cmp al,0x1 70 00401051 . 75 08 jnz short PacMe.0040105B 71 00401053 . FF05 84314000 inc dword ptr ds:[0x403184] ; c + 1; Case 1 of switch 00401042 72 00401059 . EB 13 jmp short PacMe.0040106E 73 0040105B > 3C 02 cmp al,0x2 74 0040105D . 75 09 jnz short PacMe.00401068 75 0040105F . 8305 84314000 10 add dword ptr ds:[0x403184],0x10 ; c + 10h; Case 2 of switch 00401042 76 00401066 . EB 06 jmp short PacMe.0040106E 77 00401068 > FF0D 84314000 dec dword ptr ds:[0x403184] ; c - 1; Default case of switch 00401042 78 0040106E > 8B15 84314000 mov edx,dword ptr ds:[0x403184] ; edx指向移动后的位置 79 00401074 . 8A02 mov al,byte ptr ds:[edx] 80 00401076 . 3C 2A cmp al,0x2A ; 检查al是否为* 81 00401078 . 75 06 jnz short PacMe.00401080 ; 是* 则不移动 返回0 82 0040107A . 33C0 xor eax,eax 83 0040107C . C9 leave 84 0040107D . C3 retn 85 0040107E . EB 33 jmp short PacMe.004010B3 86 00401080 > 3C 58 cmp al,0x58 ; 看al是不是X 87 00401082 75 2F jnz short PacMe.004010B3 ; 是X就注册成功 否则跳转 88 00401084 . 6A 00 push 0x0 ; /Style = MB_OK|MB_APPLMODAL 89 00401086 . 8D15 59334000 lea edx,dword ptr ds:[0x403359] ; | 90 0040108C . 52 push edx ; |Title => "Success.." 91 0040108D . 8D15 EC324000 lea edx,dword ptr ds:[0x4032EC] ; | 92 00401093 . 52 push edx ; |Text => "Congratulations! 93 00401094 . 6A 00 push 0x0 ; |hOwner = NULL 94 00401096 . 8D15 AC174000 lea edx,dword ptr ds:[0x4017AC] ; | 95 0040109C . FFD2 call edx ; \MessageBoxA 96 0040109E . 8D15 7B324000 lea edx,dword ptr ds:[0x40327B] 97 004010A4 . 52 push edx ; /Text => "Cracked by : uuuuuuu" 98 004010A5 . FF35 20344000 push dword ptr ds:[0x403420] ; |hWnd = 001E01D0 (‘UNREGISTERED!‘,class=‘Edit‘,parent=001B0394) 99 004010AB . 8D15 DC174000 lea edx,dword ptr ds:[0x4017DC] ; | 100 004010B1 . FFD2 call edx ; \SetWindowTextA 101 004010B3 > 8B15 84314000 mov edx,dword ptr ds:[0x403184] ; 当前位置记录为C 102 004010B9 . C602 43 mov byte ptr ds:[edx],0x43 103 004010BC . 8B55 FC mov edx,dword ptr ss:[ebp-0x4] 104 004010BF . C602 20 mov byte ptr ds:[edx],0x20 ; 刚刚走的位置记录为空格 105 004010C2 . B8 01000000 mov eax,0x1 ; 返回1代表没有结束 106 004010C7 . C9 leave 107 004010C8 . C3 retn 108 } 109 00401115 |. 85C0 ||test eax,eax ; eax如果返回0 则注册成功 110 00401117 |. 74 11 ||je short PacMe.0040112A 111 00401119 |. 0FB655 FF ||movzx edx,byte ptr ss:[ebp-0x1] ; 不为0 则 edx=x 112 0040111D |. 85D2 ||test edx,edx ; 如果四个方向遍历了,就结束内层循环 113 0040111F |.^ 75 D8 |\jnz short PacMe.004010F9 ; 否则再小循环,往其他方向走 114 00401121 |. FE45 FE |inc byte ptr ss:[ebp-0x2] ; y+1 115 00401124 |. 807D FE 12 |cmp byte ptr ss:[ebp-0x2],0x12 ; if y>18 结束外层循环 116 00401128 |.^ 75 CB \jnz short PacMe.004010F5 ; 外层循环18次 117 ;总共循环 18*4 次 在这个范围内必须走到X 118 0040112A |> C9 leave 119 0040112B \. C3 retn 120 } 121 122 00401754 > FF75 14 push dword ptr ss:[ebp+0x14] ; /lParam; Default case of switch 004012D8 123 00401757 . FF75 10 push dword ptr ss:[ebp+0x10] ; |wParam 124 0040175A . FF75 0C push dword ptr ss:[ebp+0xC] ; |Message 125 0040175D . FF75 08 push dword ptr ss:[ebp+0x8] ; |hWnd 126 00401760 . E8 17000000 call <jmp.&USER32.DefWindowProcA> ; \DefWindowProcA 127 00401765 . C9 leave 128 00401766 . C2 1000 retn 0x10 129 00401769 > 33C0 xor eax,eax 130 0040176B . C9 leave 131 0040176C . C2 1000 retn 0x10
这个程序主要就是进行一个深搜 - - 保证在 18*4内搜索到X就好
1 #include <iostream> 2 #include <fstream> 3 #include <iomanip> 4 using namespace std; 5 #define ROW 9 6 #define COL 16 7 #define TIMES 18*4 8 9 unsigned char key[TIMES] = { 0 }; 10 int des[4][2]= 11 { 12 {-1,0},//上 13 {0,1},//右 14 {1,0},//下 15 {0,-1}//左 16 }; 17 bool keygen(char g[ROW][COL],int x,int y,int keyn) 18 { 19 if (g[x][y] == ‘X‘) 20 return true; 21 if (keyn > TIMES) 22 return false; 23 g[x][y] = ‘ ‘; 24 for (int i = 0;i < 4;i++) 25 { 26 int nx = des[i][0] + x; 27 int ny = des[i][1] + y; 28 if (nx >= 0 && ny >= 0 && (nx < ROW) && (ny < COL)&&g[nx][ny]!=‘*‘&&g[nx][ny] != ‘ ‘) 29 { 30 key[keyn] = i; 31 if (keyn == 70) 32 cout << ‘ ‘; 33 if (keygen(g, nx, ny, keyn + 1)) 34 return true; 35 g[nx][ny] = ‘.‘; 36 key[keyn] = -1; 37 } 38 } 39 } 40 41 int main() 42 { 43 unsigned char name[8] = { 0 }; 44 char g[ROW][COL] = { 0 }; 45 unsigned char kk[TIMES / 4] = { 0 }; 46 for (int i = 0;i < TIMES;i++) 47 key[i] = -1; 48 for (int i = 0;i < ROW;i++) 49 for (int j = 0; j < COL; j++) 50 cin >> g[i][j]; 51 ofstream outfile; 52 outfile.open("KwazyWeb.bit"); 53 if (keygen(g, 0, 0, 0)) 54 { 55 for (int i = 0;i < TIMES;i += 4) 56 { 57 char kx = key[i]; 58 kx = (kx << 2) | key[i + 1]; 59 kx = (kx << 2) | key[i + 2]; 60 kx = (kx << 2) | key[i + 3]; 61 cout << hex<< kx << ‘ ‘; 62 kk[i / 4] = kx; 63 } 64 cout << endl; 65 } 66 unsigned int number; 67 cout << "请输入用户名字符个数"; 68 cin >> number; 69 outfile << hex << unsigned char(number); 70 cout << "请输入用户名"; 71 cin >> name; 72 unsigned int c = 0; 73 for (int i = 0;i < number;i++) 74 { 75 c += name[i]; 76 outfile << hex << name[i]; 77 } 78 cout << unsigned char(c); 79 for (int i = 0;i < TIMES / 4;i++) 80 { 81 kk[i] ^= unsigned char(c); 82 cout << hex << kk[i]<<‘ ‘; 83 outfile << hex << kk[i]; 84 } 85 outfile.close(); 86 system("pause"); 87 return 0; 88 }
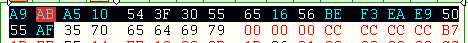 嗯 基本对了 0 0 .。 之后看python怎么样。。。C++不是太会字符处理
嗯 基本对了 0 0 .。 之后看python怎么样。。。C++不是太会字符处理
----------------------------------之后终于改好了---------------------------------------效果如下:
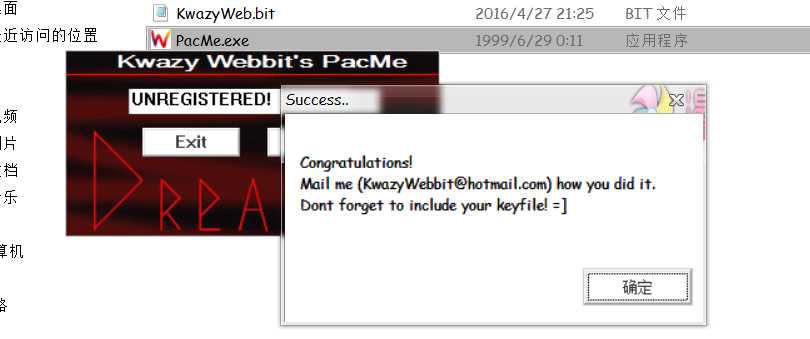
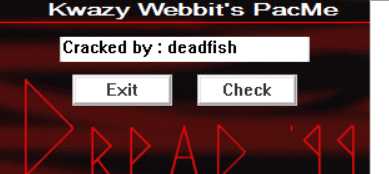
还好很好玩的 - - 不过本人愚笨,弄了一天
标签:
原文地址:http://www.cnblogs.com/driedfish/p/5440403.html