标签:
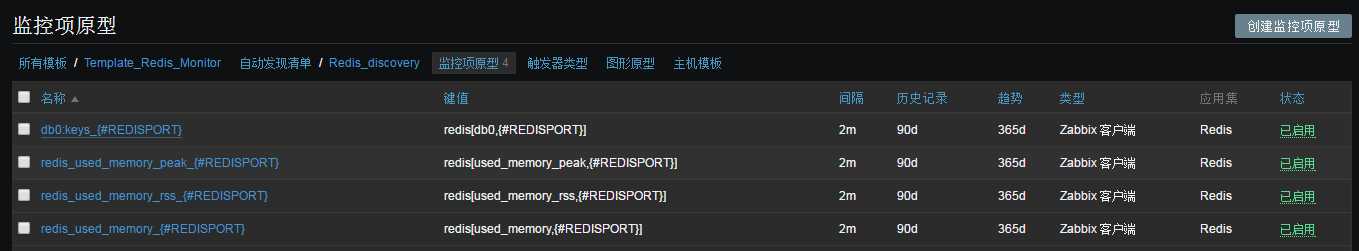
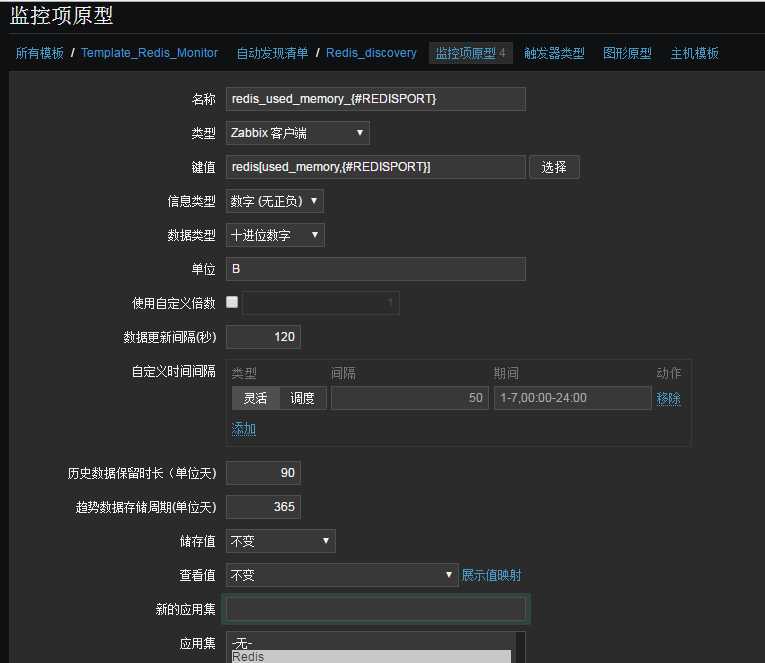
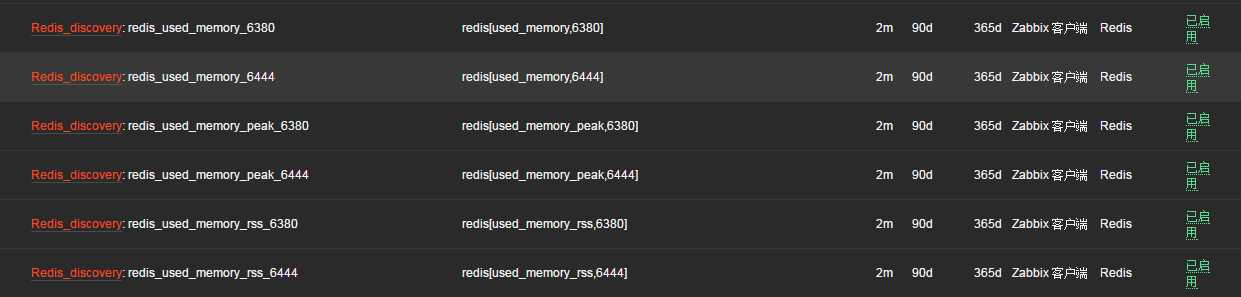
UnsafeUserParameters=1 #允许zabbix用户运行root命令 UserParameter=redis.discovery,/data/zabbix/externalscripts/redis_port.py #获取json格式数据,上报端口 UserParameter=redis[*],/data/zabbix/externalscripts/redis_stats.sh $1 $2 #自定义Key值
用到的两个脚本内容如下:
发现端口的脚本:
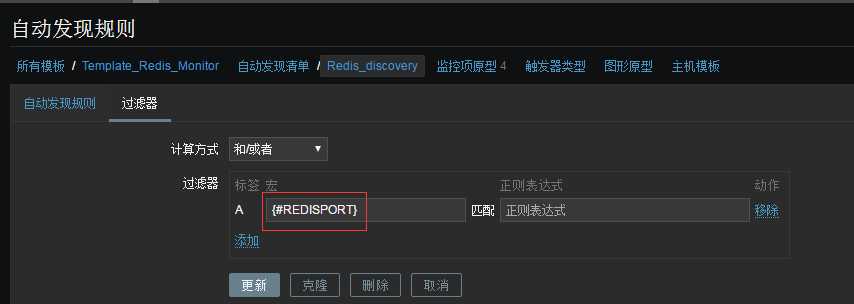
# cat redis_port.py #!/usr/bin/env python import os import json p=os.popen("""sudo netstat -anp|awk -F: ‘/redis-server/&&/LISTEN/{sub(/ .*/,"",$2);if($2)print $2}‘ """) ports = [] for port in p.readlines(): r = os.path.basename(port.strip()) ports += [{‘{#REDISPORT}‘:r}] print json.dumps({‘data‘:ports},sort_keys=True,indent=4,separators=(‘,‘,‘:‘))
获取监控数据的脚本:
# cat redis_stats.sh #!/bin/bash METRIC="$1" PORT="${2:-6379}" CACHE_FILE="/data/zabbix/externalscripts/redis_$PORT.cache" redis-cli -p ${PORT} -a ‘USLF93SUVwtSF$$#@W‘ info > ${CACHE_FILE} 2>/dev/null || exit 1 awk -F‘[:,]+‘ ‘/‘"${METRIC}"‘:/{gsub(/^[^0-9]+/,"",$2);print $2}‘ ${CACHE_FILE}
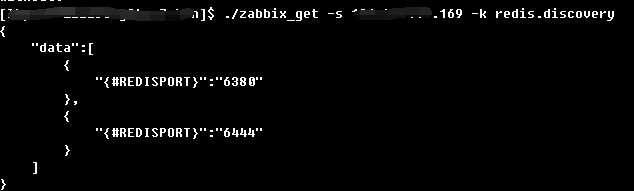
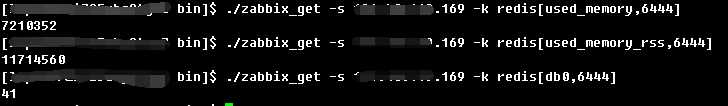
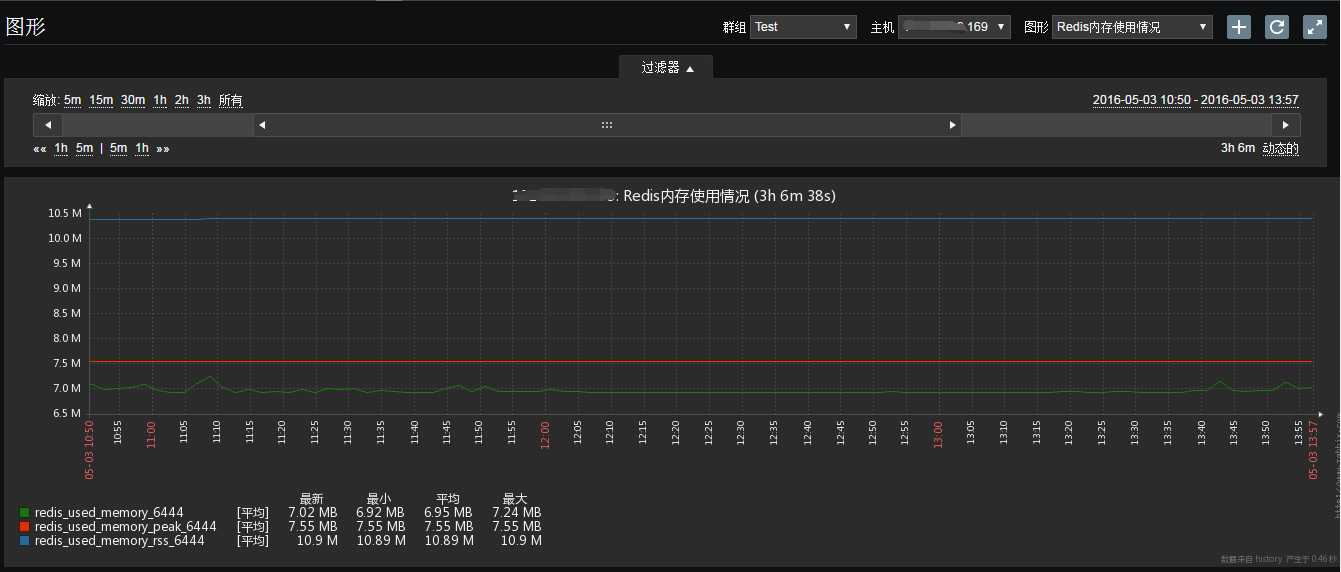
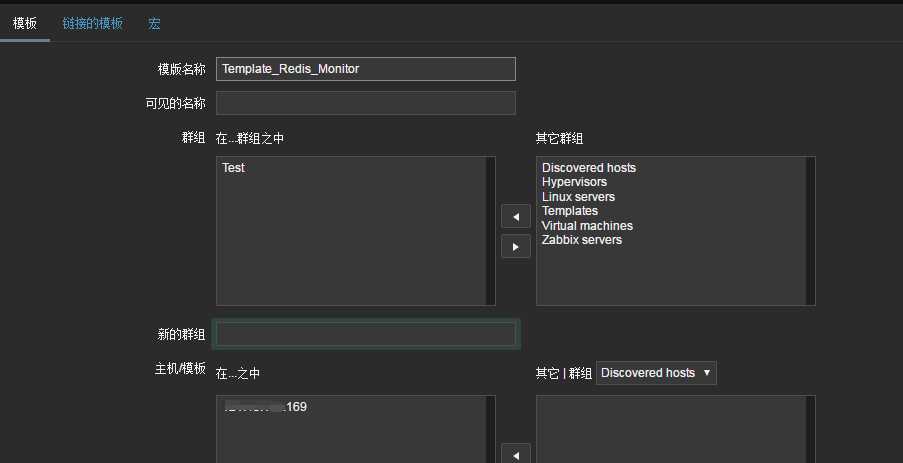
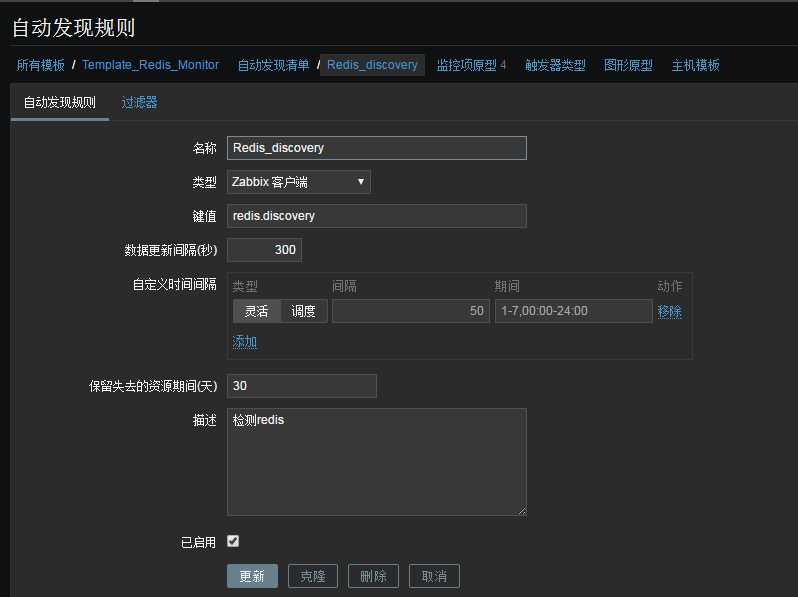
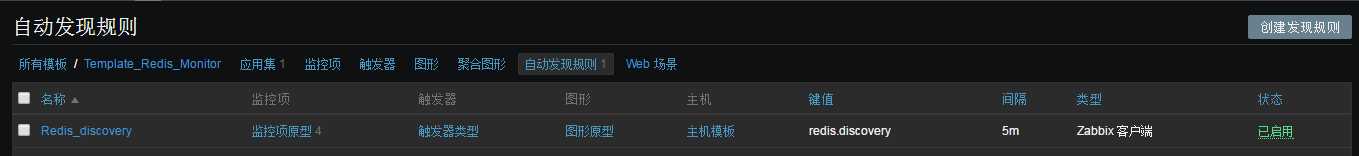
Zabbix监控redis多实例(low level discovery)
标签:
原文地址:http://www.cnblogs.com/Eivll0m/p/5455210.html