标签:
首先PEID查壳: 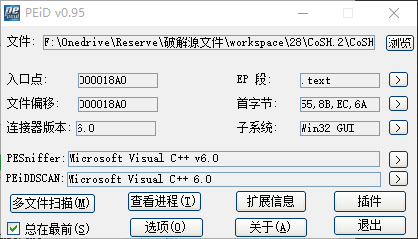
没有壳,位码验证: 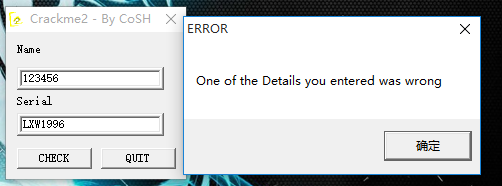
发现了错误字符串,于是OD中查找参考文本字符串进行跟进: 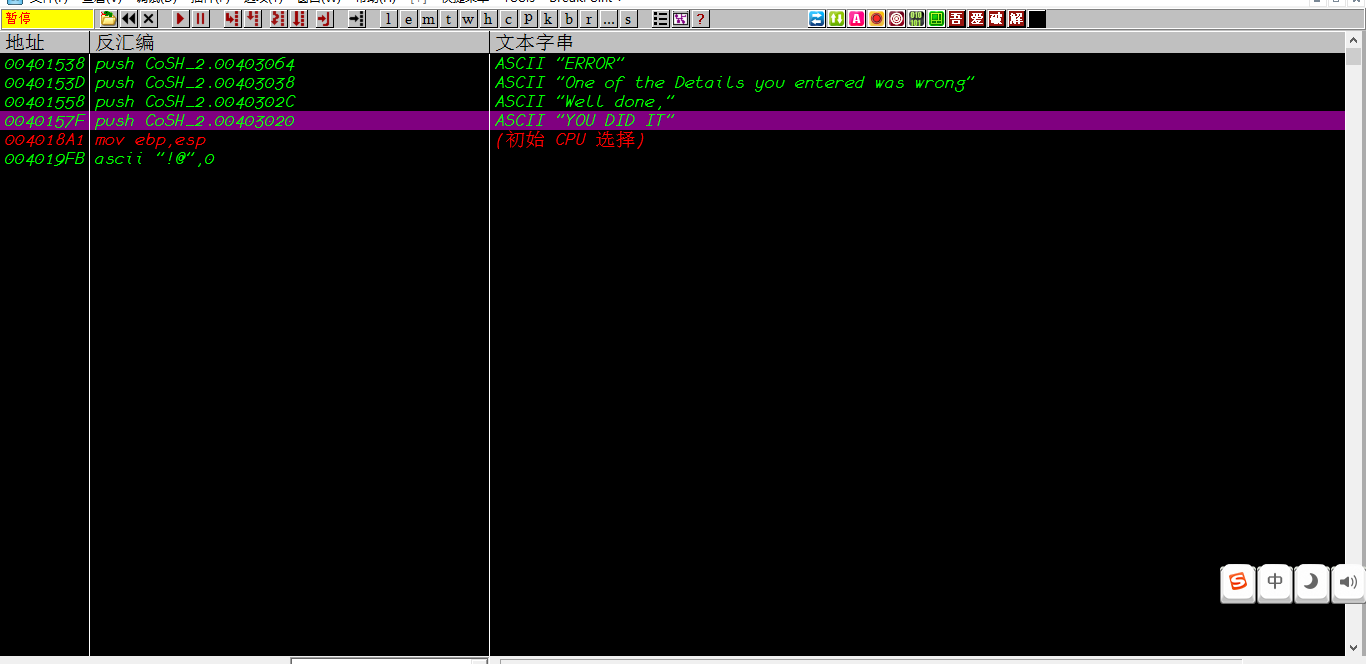
在OD中找到相应的分支结构:
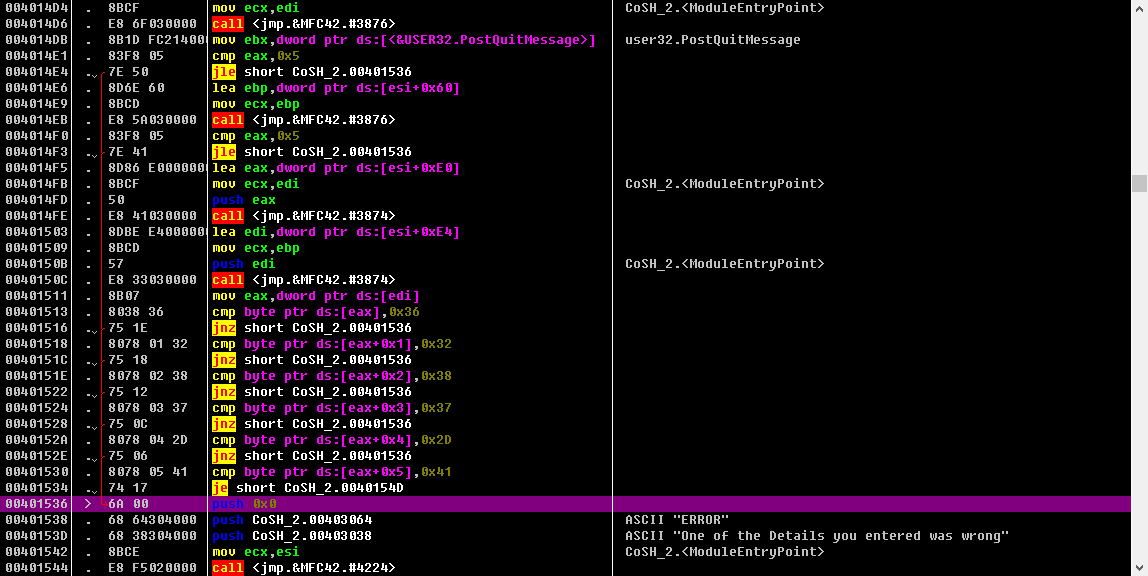
在上面的函数头部下断点,单步键入,分析代码:简单,略过,最后发现实际没有算法,就是serial硬编码,把十六进制转换成ASCII码即可。
004014CA . 56 push esi 004014CB . 8BF1 mov esi,ecx 004014CD . 57 push edi 004014CE . 8DBE A0000000 lea edi,dword ptr ds:[esi+0xA0] 004014D4 . 8BCF mov ecx,edi 004014D6 . E8 6F030000 call <jmp.&MFC42.#3876> 004014DB . 8B1D FC214000 mov ebx,dword ptr ds:[<&USER32.PostQuitMessage>] ; user32.PostQuitMessage 004014E1 . 83F8 05 cmp eax,0x5 ; ;获取name字符串的长度,判断是否大于5 004014E4 . 7E 50 jle short CoSH_2.00401536 ; ;字符串长度小于等于5,错误 004014E6 . 8D6E 60 lea ebp,dword ptr ds:[esi+0x60] 004014E9 . 8BCD mov ecx,ebp 004014EB . E8 5A030000 call <jmp.&MFC42.#3876> ; ;获取serial字符串的长度 004014F0 . 83F8 05 cmp eax,0x5 ; ;判断是否大于5 004014F3 . 7E 41 jle short CoSH_2.00401536 ; ;字符串长度小于等于5,错误 004014F5 . 8D86 E0000000 lea eax,dword ptr ds:[esi+0xE0] 004014FB . 8BCF mov ecx,edi 004014FD . 50 push eax 004014FE . E8 41030000 call <jmp.&MFC42.#3874> 00401503 . 8DBE E4000000 lea edi,dword ptr ds:[esi+0xE4] 00401509 . 8BCD mov ecx,ebp 0040150B . 57 push edi 0040150C . E8 33030000 call <jmp.&MFC42.#3874> 00401511 . 8B07 mov eax,dword ptr ds:[edi] 00401513 . 8038 36 cmp byte ptr ds:[eax],0x36 ; ;serila的第一个与0x36比较 00401516 . 75 1E jnz short CoSH_2.00401536 00401518 . 8078 01 32 cmp byte ptr ds:[eax+0x1],0x32 ; ;serila的第二个字符与0x32比较 0040151C . 75 18 jnz short CoSH_2.00401536 0040151E . 8078 02 38 cmp byte ptr ds:[eax+0x2],0x38 ; ;serila的第三个字符与0x38比较 00401522 . 75 12 jnz short CoSH_2.00401536 00401524 . 8078 03 37 cmp byte ptr ds:[eax+0x3],0x37 ; ;serila的第四个字符与0x37比较 00401528 . 75 0C jnz short CoSH_2.00401536 0040152A . 8078 04 2D cmp byte ptr ds:[eax+0x4],0x2D ; ;serila的第五个字符与0x2D比较 0040152E . 75 06 jnz short CoSH_2.00401536 00401530 . 8078 05 41 cmp byte ptr ds:[eax+0x5],0x41 ; ;serila的第六个字符与0x41比较 00401534 . 74 17 je short CoSH_2.0040154D 00401536 > 6A 00 push 0x0 00401538 . 68 64304000 push CoSH_2.00403064 ; ASCII "ERROR" 0040153D . 68 38304000 push CoSH_2.00403038 ; ASCII "One of the Details you entered was wrong" 00401542 . 8BCE mov ecx,esi 00401544 . E8 F5020000 call <jmp.&MFC42.#4224> 00401549 . 6A 00 push 0x0 0040154B . FFD3 call ebx ; user32.PostQuitMessage 0040154D > 8D8E E0000000 lea ecx,dword ptr ds:[esi+0xE0] 00401553 . 8D5424 14 lea edx,dword ptr ss:[esp+0x14] 00401557 . 51 push ecx 00401558 . 68 2C304000 push CoSH_2.0040302C ; ASCII "Well done," 0040155D . 52 push edx 0040155E . E8 D5020000 call <jmp.&MFC42.#926>
检验一下serial:
6287-A
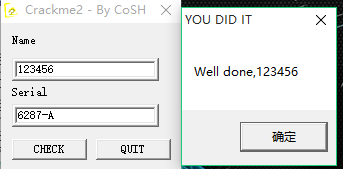
最后,根据程序的流程写注册机
C++:
#include <iostream> #include <cstring> using namespace std; #define N 100 int main() { char name[N]; char serial_true[N]={0x36,0x32,0x38,0x37,0x2D,0x41}; char serial_false[N]; cout<<"Please input your name:"<<endl; cin>>name; cout<<"Please input your serial:"<<endl; cin>>serial_false; if(strlen(name)<=5||strlen(serial_false)<=5) { cout<<"Error!"<<endl; return 0; } else { cout<<"True serial is only behind the string:"<<endl; for(int i=0;i<=6;i++) { cout<<serial_true[i]; } cout<<endl; } return 0; }
运行结果:
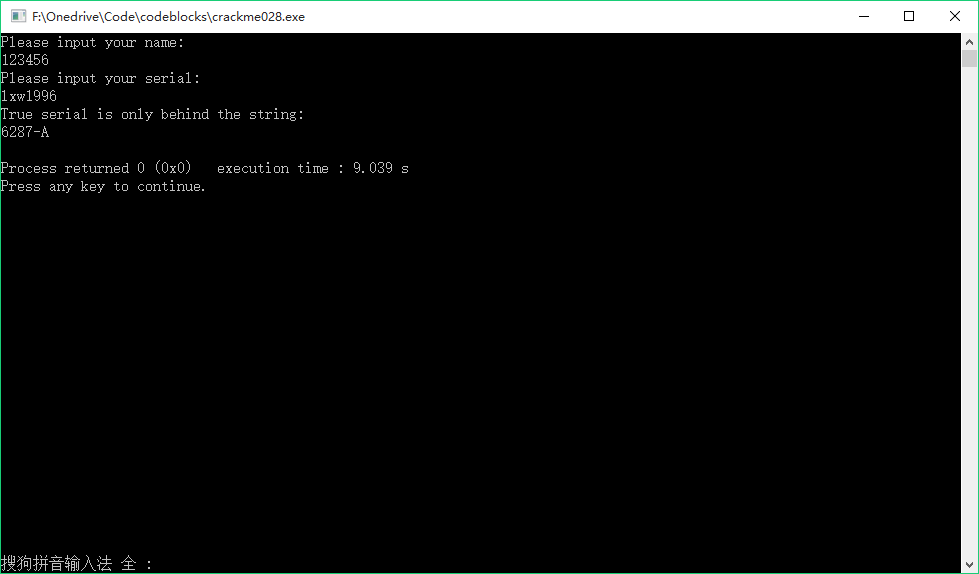
真是水题..
标签:
原文地址:http://www.cnblogs.com/Space-of-Bruce/p/5558169.html