标签:
基于声明的认证方式,主要用于第三方认证.
A claim is a statement that one subject makes about itself or another subject. The statement can be about a name, identity, key, group, privilege, or capability, for example. Claims are issued by a provider, and they are given one or more values and then packaged in security tokens that are issued by an issuer, commonly known as a security token service (STS).
Claim is piece of information that describes given identity on some aspect. Take claim as name-value pair. Claims are held in authentication token that may have also signature so you can be sure that token is not tampered on its way from remote machine to your system. You can think of token as envelop that contains claims about user.
Token may contain different claims:
System can use claims to identify and describe given user from more than one aspect. This is something you don’t achieve easily with regular username-password based authentication mechanisms.
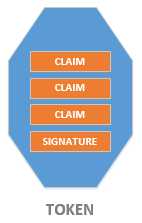
Claims are a set of information stored in a key – value pair form. Claims are used to store information about user like full name, phone number, email address.... and the most important thing is that you can use claims as a replacement of roles, that you can transfer the roles to be a claim for a user.
The most important benefit from claims is that you can let a third party authenticate users, and the third party will retrieve to you if this user is authenticated or not and also what claims are for this user.
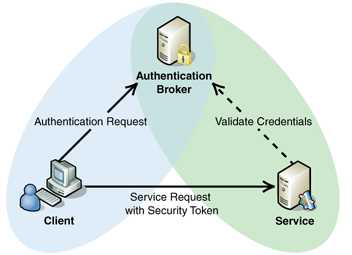
Token store a set of data in (local/session storage or cookies), these could be stored in server or client side, the token itself is represented in hash of the cookie or session.
In token based authentication, when a request comes, it should have the token with it, the server first will authenticate the attached token with the request, then it will search for the associated cookie for it and bring the information needed from that cookie.
https://msdn.microsoft.com/zh-cn/library/ff359101.aspx
https://msdn.microsoft.com/en-us/library/ff359108.aspx
Claims Based Authentication and Token Based Authentication
标签:
原文地址:http://www.cnblogs.com/imust2008/p/5613786.html