标签:
My friend she showed me a screenshot as below yesterday. The name of this document is “EnCase Forensic Features and Functionality”. She asked me that why some feature is missing in her EnCase Forensic software???
Then she showed me what’s missing in her EnCase as below. She said to me that’s it – “Active Directory Information Extractor”. It’s very interesting. I’ve been using EnCase for such a very long time and I’ve never seen this feature before.
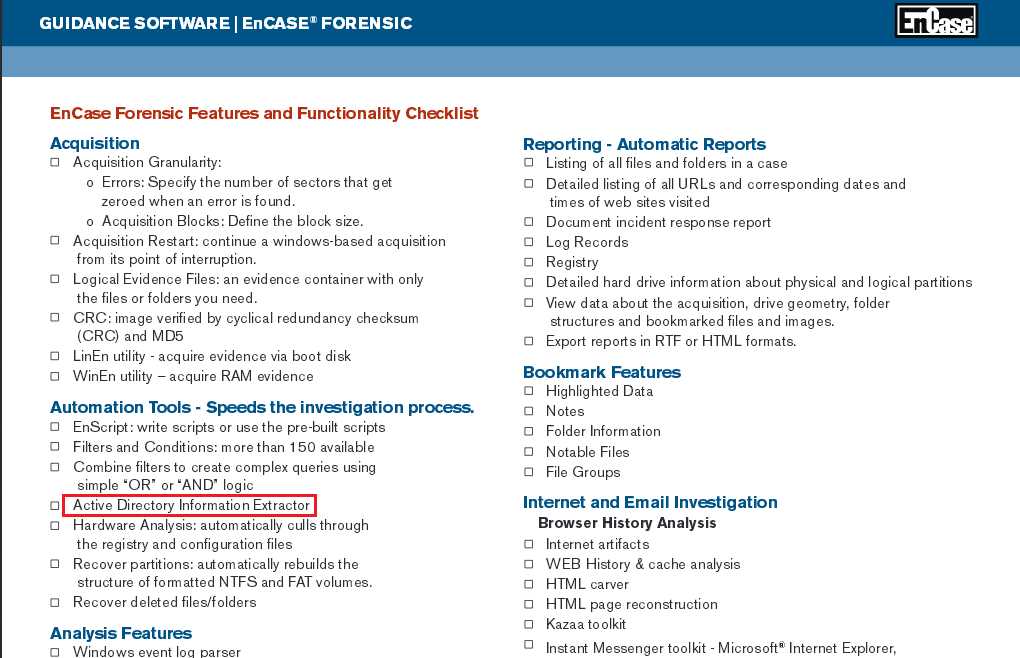
I conduct an investigation on it and it seems that it’s an EnScript as below:
This EnScript is designed to extract the Username (Both Displayname and Login Name), the SID, the Home directory, the Email address of each User and the Last Login, Last Failed Login, and Next Password Change dates for each account. Existing Group Names are also located and presented.
Now my question is where to get this EnScript and what version of Windows Server it supports. I’d appreciate your providing me any info you have. Thanks.
Where is "Active Directory Information Extractor"?
标签:
原文地址:http://www.cnblogs.com/pieces0310/p/5616190.html