标签:
系统 : Windows xp
程序 : easycrackme
程序下载地址 :http://pan.baidu.com/s/1kU9Xvkr
要求 : 注册机编写
使用工具 : OD
可在“PEDIY CrackMe 2007”中查找关于此程序的讨论,标题为“easycrackme算法分析”。
根据字符串定位关键算法:
00404051 |. 50 push eax ; /hWnd => 000706AE (class=‘Edit‘,parent=00270276)
00404052 |. E8 ADFCFFFF call <jmp.&user32.GetWindowTextLength>; \GetWindowTextLengthA
00404057 |. 8BD0 mov edx, eax
00404059 |. 8BDA mov ebx, edx
0040405B |. 85DB test ebx, ebx
0040405D |. 7E 10 jle short 0040406F
0040405F |> 8D45 F8 /lea eax, dword ptr [ebp-8]
00404062 |. BA D4414000 |mov edx, 004041D4
00404067 |. E8 6CEEFFFF |call 00402ED8
0040406C |. 4B |dec ebx
0040406D |.^ 75 F0 \jnz short 0040405F
0040406F |> 6A 32 push 32
00404071 |. 8B45 F8 mov eax, dword ptr [ebp-8]
00404074 |. E8 27EFFFFF call 00402FA0
00404079 |. 50 push eax ; |Buffer
0040407A |. A1 34654000 mov eax, dword ptr [406534] ; |
0040407F |. 50 push eax ; |hWnd => 000706AE (class=‘Edit‘,parent=00270276)
00404080 |. E8 77FCFFFF call <jmp.&user32.GetWindowTextA> ; \GetWindowTextA
00404085 |. A1 30654000 mov eax, dword ptr [406530]
0040408A |. 50 push eax ; /hWnd => 000506DC (class=‘Edit‘,parent=00270276)
0040408B |. E8 74FCFFFF call <jmp.&user32.GetWindowTextLength>; \GetWindowTextLengthA
00404090 |. 8BD0 mov edx, eax
00404092 |. 8BDA mov ebx, edx
00404094 |. 85DB test ebx, ebx
00404096 |. 7E 10 jle short 004040A8
00404098 |> 8D45 FC /lea eax, dword ptr [ebp-4]
0040409B |. BA D4414000 |mov edx, 004041D4
004040A0 |. E8 33EEFFFF |call 00402ED8
004040A5 |. 4B |dec ebx
004040A6 |.^ 75 F0 \jnz short 00404098
004040A8 |> 6A 32 push 32
004040AA |. 8B45 FC mov eax, dword ptr [ebp-4]
004040AD |. E8 EEEEFFFF call 00402FA0
004040B2 |. 50 push eax ; |Buffer
004040B3 |. A1 30654000 mov eax, dword ptr [406530] ; |
004040B8 |. 50 push eax ; |hWnd => 000506DC (class=‘Edit‘,parent=00270276)
004040B9 |. E8 3EFCFFFF call <jmp.&user32.GetWindowTextA> ; \GetWindowTextA
004040BE |. 8B45 FC mov eax, dword ptr [ebp-4]
004040C1 |. E8 0AEEFFFF call 00402ED0
004040C6 |. 8BD0 mov edx, eax
004040C8 |. 85D2 test edx, edx
004040CA |. 7F 1F jg short 004040EB
004040CC |. 8D45 F8 lea eax, dword ptr [ebp-8]
004040CF |. BA E0414000 mov edx, 004041E0 ; your name?
004040D4 |. E8 A7EDFFFF call 00402E80
004040D9 |. 8D45 FC lea eax, dword ptr [ebp-4]
004040DC |. BA F4414000 mov edx, 004041F4 ; error
004040E1 |. E8 9AEDFFFF call 00402E80
004040E6 |. E9 98000000 jmp 00404183
004040EB |> 33F6 xor esi, esi
004040ED |. 8BDA mov ebx, edx
004040EF |. 85DB test ebx, ebx
004040F1 |. 7E 19 jle short 0040410C
004040F3 |. B8 01000000 mov eax, 1
004040F8 |> 8B4D FC /mov ecx, dword ptr [ebp-4]
004040FB |. 0FB64C01 FF |movzx ecx, byte ptr [ecx+eax-1] ; 遍历用户名
00404100 |. 8BF8 |mov edi, eax
00404102 |. 4F |dec edi
00404103 |. 0FAFCF |imul ecx, edi
00404106 |. 03F1 |add esi, ecx
00404108 |. 40 |inc eax
00404109 |. 4B |dec ebx ; 循环变量递减
0040410A |.^ 75 EC \jnz short 004040F8
0040410C |> 8D1C12 lea ebx, dword ptr [edx+edx]
0040410F |. 83C3 63 add ebx, 63
00404112 |. 81E3 FFFF0000 and ebx, 0FFFF ; 去高位
00404118 |. 81E6 FFFF0000 and esi, 0FFFF ; 去高位
0040411E |. C1E3 10 shl ebx, 10
00404121 |. 03F3 add esi, ebx
00404123 |. 8BDE mov ebx, esi
00404125 |. 8BF3 mov esi, ebx
00404127 |. 83E6 0F and esi, 0F
0040412A |. 8B1CB5 B85040>mov ebx, dword ptr [esi*4+4050B8] ; 表中取数
00404131 |. 8D45 F8 lea eax, dword ptr [ebp-8]
00404134 |. 8B4D F8 mov ecx, dword ptr [ebp-8]
00404137 |. BA 04424000 mov edx, 00404204 ; 0
0040413C |. E8 DBEDFFFF call 00402F1C ; 密码前面加上0
00404141 |. 8B45 F8 mov eax, dword ptr [ebp-8]
00404144 |. E8 57FEFFFF call 00403FA0
00404149 |. 8BF0 mov esi, eax
0040414B |. 8D45 FC lea eax, dword ptr [ebp-4]
0040414E |. BA F4414000 mov edx, 004041F4 ; error
00404153 |. E8 28EDFFFF call 00402E80
00404158 |. 8D45 F8 lea eax, dword ptr [ebp-8]
0040415B |. BA 10424000 mov edx, 00404210 ; invalid
00404160 |. E8 1BEDFFFF call 00402E80
00404165 |. 3BDE cmp ebx, esi
00404167 |. 75 1A jnz short 00404183
00404169 |. 8D45 FC lea eax, dword ptr [ebp-4]
0040416C |. BA 20424000 mov edx, 00404220 ; ok
00404171 |. E8 0AEDFFFF call 00402E80
00404176 |. 8D45 F8 lea eax, dword ptr [ebp-8]
00404179 |. BA 2C424000 mov edx, 0040422C ; thanks a lot
0040417E |. E8 FDECFFFF call 00402E80
00404183 |> 6A 00 push 0
00404185 |. 8B45 FC mov eax, dword ptr [ebp-4]
00404188 |. E8 13EEFFFF call 00402FA0
0040418D |. 50 push eax
0040418E |. 8B45 F8 mov eax, dword ptr [ebp-8]
00404191 |. E8 0AEEFFFF call 00402FA0
00404196 |. 50 push eax ; |Text
00404197 |. A1 0C654000 mov eax, dword ptr [40650C] ; |
0040419C |. 50 push eax ; |hOwner => 00270276 (‘esaycrackme bY DiKeN‘,class=‘MyWindowClass‘)
0040419D |. E8 8AFBFFFF call <jmp.&user32.MessageBoxA> ; \MessageBoxA
Fun(用户名):
004040F8 |> /8B4D FC /mov ecx, dword ptr [ebp-4]
004040FB |. |0FB64C01 FF |movzx ecx, byte ptr [ecx+eax-1] ; 遍历用户名
00404100 |. |8BF8 |mov edi, eax
00404102 |. |4F |dec edi
00404103 |. |0FAFCF |imul ecx, edi
00404106 |. |03F1 |add esi, ecx
00404108 |. |40 |inc eax
00404109 |. |4B |dec ebx ; 循环变量递减
0040410A |.^\75 EC \jnz short 004040F8
0040410C |> 8D1C12 lea ebx, dword ptr [edx+edx]
0040410F |. 83C3 63 add ebx, 63
00404112 |. 81E3 FFFF0000 and ebx, 0FFFF ; 去高位
00404118 |. 81E6 FFFF0000 and esi, 0FFFF ; 去高位
0040411E |. C1E3 10 shl ebx, 10
00404121 |. 03F3 add esi, ebx
00404123 |. 8BDE mov ebx, esi
00404125 |. 8BF3 mov esi, ebx
00404127 |. 83E6 0F and esi, 0F
0040412A |. 8B1CB5 B85040>mov ebx, dword ptr [esi*4+4050B8] ; 表中取数
Fun(密码):
00403FA0 /$ 55 push ebp
00403FA1 |. 8BEC mov ebp, esp
00403FA3 |. 83C4 F8 add esp, -8
00403FA6 |. 53 push ebx
00403FA7 |. 33D2 xor edx, edx
00403FA9 |. 8955 F8 mov dword ptr [ebp-8], edx
00403FAC |. 8945 FC mov dword ptr [ebp-4], eax
00403FAF |. 8B45 FC mov eax, dword ptr [ebp-4]
00403FB2 |. E8 D9EFFFFF call 00402F90
00403FB7 |. 33C0 xor eax, eax
00403FB9 |. 55 push ebp
00403FBA |. 68 16404000 push 00404016
00403FBF |. 64:FF30 push dword ptr fs:[eax]
00403FC2 |. 64:8920 mov dword ptr fs:[eax], esp
00403FC5 |. 8D45 F8 lea eax, dword ptr [ebp-8]
00403FC8 |. 8B55 FC mov edx, dword ptr [ebp-4]
00403FCB |. E8 B0EEFFFF call 00402E80
00403FD0 |. 8B45 F8 mov eax, dword ptr [ebp-8]
00403FD3 |. E8 F8EEFFFF call 00402ED0 ; 算出序列号长度
00403FD8 |. 8BC8 mov ecx, eax
00403FDA |. 41 inc ecx
00403FDB |. 33D2 xor edx, edx
00403FDD |. B8 01000000 mov eax, 1
00403FE2 |> 03D2 /add edx, edx ; edx * 2
00403FE4 |. 8D1492 |lea edx, dword ptr [edx+edx*4] ; 快速计算 edx * 5
00403FE7 |. 8B5D F8 |mov ebx, dword ptr [ebp-8]
00403FEA |. 0FB65C03 FF |movzx ebx, byte ptr [ebx+eax-1] ; 遍历 序列号
00403FEF |. 03D3 |add edx, ebx ; 累加
00403FF1 |. 83EA 30 |sub edx, 30
00403FF4 |. 40 |inc eax
00403FF5 |. 3BC8 |cmp ecx, eax
00403FF7 |.^ 75 E9 \jnz short 00403FE2
00403FF9 |. 8BDA mov ebx, edx
00403FFB |. 33C0 xor eax, eax
00403FFD |. 5A pop edx
00403FFE |. 59 pop ecx
00403FFF |. 59 pop ecx
00404000 |. 64:8910 mov dword ptr fs:[eax], edx
00404003 |. 68 1D404000 push 0040401D
00404008 |> 8D45 F8 lea eax, dword ptr [ebp-8]
0040400B |. BA 02000000 mov edx, 2
00404010 |. E8 F7EDFFFF call 00402E0C
00404015 \. C3 retn
比较简单的二元函数,可以直接看出Fun(密码)是对从表中取的数字进行10进制->16进制的转换。
打开http://www.cnblogs.com/ZRBYYXDM/p/5115596.html中搭建的框架,将OnBtnDecrypt函数编辑如下:
void CKengen_TemplateDlg::OnBtnDecrypt()
{
// TODO: Add your control notification handler code here
CString str;
GetDlgItemText( IDC_EDIT_NAME,str ); //获取用户名字串基本信息。
int len = str.GetLength();
if ( len != 0 ){ //格式控制。
DWORD NumList[] = {
0x19791126, 0x19791007, 0x11261979, 0x10071979,
0x12345678, 0x9ABCDEF0, 0x12123434, 0x78787878,
0xCCC6CCC6, 0xCC00CC00, 0xFFEFEFFF, 0xDDCC5555,
0x67678789, 0xCECECBCC, 0x778899AB, 0x44337766
};
DWORD Res = 0;
for ( int i = 0 ; i != len ; i++ )
Res += ( str[i] * i );
DWORD Offset = 0;
Offset = ( (len*2+0x63) & 0xFFFF ) << 0x10;
Offset += Res & 0xFFFF;
Offset &= 0xF;
DWORD NameRes = NumList[Offset];
CString PassWord;
PassWord.Format( "%u",NameRes );
SetDlgItemText( IDC_EDIT_PASSWORD,PassWord );
}
else
MessageBox( "用户名格式错误!" );
}
再在OnInitDialog中添加此代码修改标题:SetWindowText(_T("Keygen"));
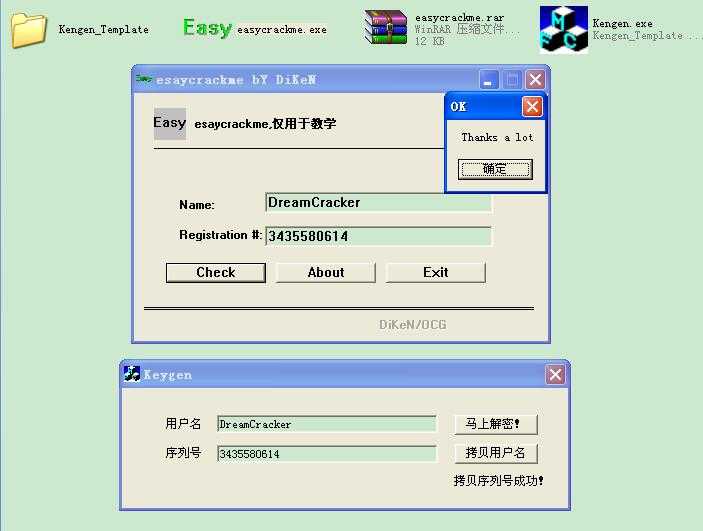
运行效果:
标签:
原文地址:http://www.cnblogs.com/ZRBYYXDM/p/5745667.html