标签:tab files .gz socket down iptables live back wait
环境:两台lvs、两台real server(四台简化为两台)
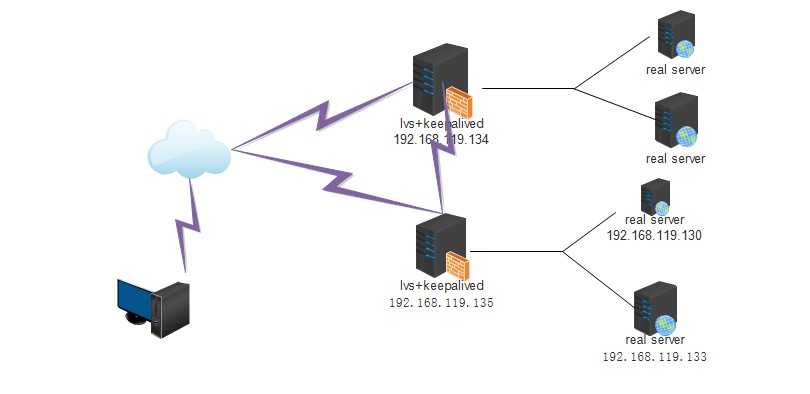
关闭所有服务器的防火墙和selinux
sed -i "s#SELINUX=enforcing#SELINUX=disabled#g" /etc/selinux/config #重启生效 reboot /etc/init.d/iptables stop
可参考 http://www.cnblogs.com/zzzhfo/p/5957113.html
两台lvs配置相同
[root@lvs02 /]# yum -y install kernel-devel gcc gcc-c++ libnl* libpopt* popt-static
2.6.32-642.4.2.el6.x86_64用tab键补全
[root@lvs01 /]# uname -r 2.6.32-431.el6.x86_64 [root@lvs01 /]# ln -s /usr/src/kernels/2.6.32-642.4.2.el6.x86_64/ /usr/src/linux
这里我们使用的2.6版本,并且注意内核是2.6版本的,如果你的版本是6.X版本的话,那么可以使用2.6版本
[root@lvs01 /]# wget http://www.linuxvirtualserver.org/software/kernel-2.6/ipvsadm-1.26.tar.gz --2016-10-05 23:52:06-- http://www.linuxvirtualserver.org/software/kernel-2.6/ipvsadm-1.26.tar.gz Resolving www.linuxvirtualserver.org... 69.56.251.119 Connecting to www.linuxvirtualserver.org|69.56.251.119|:80... connected. HTTP request sent, awaiting response... 200 OK Length: 41700 (41K) [application/x-gzip] Saving to: “ipvsadm-1.26.tar.gz” 100%[=======================================>] 41,700 41.6K/s in 1.0s 2016-10-05 23:52:23 (41.6 KB/s) - “ipvsadm-1.26.tar.gz” saved [41700/41700]
解压、配置、编译、安装
[root@lvs01 /]# tar zxvf ipvsadm-1.26.tar.gz [root@lvs01 /]# cd ipvsadm-1.26 [root@lvs01 ipvsadm-1.26]# make [root@lvs01 ipvsadm-1.26]# make install [root@lvs ipvsadm-1.26]# lsmod | grep ip_vs 把ipvs模块加载进系统,需要我们执行ipvsadm命令才会加载进去 或者modprobe ip_vs。 [root@lvs01 ipvsadm-1.26]# modprobe ip_vs [root@lvs01 ipvsadm-1.26]# lsmod | grep ip_vs ip_vs 125220 0 libcrc32c 1246 1 ip_vs ipv6 317340 142 ip_vs,ip6t_REJECT,nf_conntrack_ipv6,nf_defrag_ipv6
两台real server配置相同
web01配置 [root@web01 /]# hostname web01 [root@web01 /]# yum -y install httpd [root@web01 /]# find / -name httpd.conf /etc/httpd/conf/httpd.conf [root@web01 /]# vim /etc/httpd/conf/httpd.conf ServerName 127.0.0.1 [root@web01 /]# cd /var/www/html/ [root@web01 html]# echo "web01_192.168.119.130" > index.html [root@web01 html]# ls index.html [root@web01 html]# cat index.html web01_192.168.119.130 [root@web01 html]# /etc/init.d/httpd start Starting httpd: [ OK ] [root@web01 html]# curl localhost web01_192.168.119.130 web02配置 [root@web02 /]# hostname web02 [root@web02 /]# yum -y install httpd [root@web02 /]# vim /etc/httpd/conf/httpd.conf ServerName 127.0.0.1 [root@web02 /]# echo "web02_192.168.119.133" > /var/www/html/index.html [root@web02 /]# cat /var/www/html/index.html web02_192.168.119.133 [root@web02 /]# /etc/init.d/httpd start Starting httpd: [ OK ] [root@web02 /]# curl localhost web02_192.168.119.133
real server 脚本
用于绑定VIP和ARP抑制
[root@web01 /]# vim /usr/local/sbin/ipvs_client.sh
#!/bin/bash VIP=192.168.119.150 PORT=80 case "$1" in start) ifconfig eth0:0 $VIP/32 up route add -host $VIP dev eth0 echo "1">/proc/sys/net/ipv4/conf/lo/arp_ignore echo "2">/proc/sys/net/ipv4/conf/lo/arp_announce echo "1">/proc/sys/net/ipv4/conf/all/arp_announce echo "2">/proc/sys/net/ipv4/conf/all/arp_announce echo "start LVS of REALServer IP" ;; stop) ifconfig eth0:0 $VIP/32 down route del -host $VIP dev eth0 echo "0">/proc/sys/net/ipv4/conf/lo/arp_ignore echo "0">/proc/sys/net/ipv4/conf/lo/arp_announce echo "0">/proc/sys/net/ipv4/conf/all/arp_announce echo "0">/proc/sys/net/ipv4/conf/all/arp_announce echo "stop LVS OF REALServer" ;; *) echo "Usage: $0 {start|stop}" esac
启动脚本
[root@web01 /]# chmod 755 /usr/local/sbin/ipvs_client.sh [root@web01 /]# ipvs_client.sh start start LVS of REALServer IP [root@web01 /]# ifconfig eth0:0 eth0:0 Link encap:Ethernet HWaddr 00:0C:29:1B:BA:FB inet addr:192.168.119.150 Bcast:255.255.255.255 Mask:0.0.0.0 UP BROADCAST RUNNING MULTICAST MTU:1500 Metric:1
安装keepalived
可参考 http://www.cnblogs.com/zzzhfo/p/6070065.html
lvs01和lvs02
检查下
[root@lb01 /]# ln -s /usr/src/kernels/2.6.32-642.6.2.el6.x86_64/ /usr/src/linux [root@lb01 /]# ls -l /usr/src/ total 8 drwxr-xr-x. 2 root root 4096 Sep 23 2011 debug drwxr-xr-x. 3 root root 4096 Oct 6 11:05 kernels lrwxrwxrwx 1 root root 43 Oct 6 11:09 linux -> /usr/src/kernels/2.6.32-642.6.2.el6.x86_64/
下载keepalived
[root@lvs01 /]# wget http://www.keepalived.org/software/keepalived-1.2.16.tar.gz
安装依赖包
报错 configure: error: !!! OpenSSL is not properly installed on your system. !!! !!! Can not include OpenSSL headers files. !!! 解决 [root@lvs01 /]# yum -y install openssl openssl-devel
解压、配置、编译、安装
[root@lvs01 /]# tar zxvf keepalived-1.2.16.tar.gz [root@lvs01 /]# cd keepalived-1.2.16 [root@lvs01 keepalived-1.2.16]# ./configure Keepalived configuration ------------------------ Keepalived version : 1.2.16 Compiler : gcc Compiler flags : -g -O2 -I/usr/include/libnl3 Extra Lib : -lssl -lcrypto -lcrypt -lnl-genl-3 -lnl-3 Use IPVS Framework : Yes IPVS sync daemon support : Yes IPVS use libnl : Yes fwmark socket support : Yes Use VRRP Framework : Yes Use VRRP VMAC : Yes SNMP support : No SHA1 support : No Use Debug flags : No [root@lvs01 keepalived-1.2.16]# make && make install [root@lvs01 keepalived-1.2.16]# cp /usr/local/etc/rc.d/init.d/keepalived /etc/init.d/ [root@lvs01 keepalived-1.2.16]# cp /usr/local/etc/sysconfig/keepalived /etc/sysconfig/ [root@lvs01 keepalived-1.2.16]# mkdir /etc/keepalived [root@lvs01 keepalived-1.2.16]# cp /usr/local/etc/keepalived/keepalived.conf /etc/keepalived/ [root@lvs01 keepalived-1.2.16]# cp /usr/local/sbin/keepalived /usr/sbin/ [root@lvs01 keepalived-1.2.16]# /etc/init.d/keepalived start Starting keepalived: [ OK ] [root@lvs01 keepalived-1.2.16]# ps -ef | grep keepalived root 3217 1 0 01:08 ? 00:00:00 keepalived -D root 3219 3217 0 01:08 ? 00:00:00 keepalived -D root 3220 3217 0 01:08 ? 00:00:00 keepalived -D root 3222 1074 0 01:08 pts/0 00:00:00 grep keep [root@lvs01 keepalived-1.2.16]# /etc/init.d/keepalived stop Stopping keepalived: [ OK ]
修改配置文件(单实例)
lvs01
[root@lvs01 keepalived-1.2.16]# cd /etc/keepalived/ [root@lvs01 keepalived]# cp keepalived.conf keepalived.conf.bak [root@lvs01 keepalived]# vim keepalived.conf ! Configuration File for keepalived global_defs { notification_email { acassen@firewall.loc failover@firewall.loc sysadmin@firewall.loc } notification_email_from Alexandre.Cassen@firewall.loc smtp_server 192.168.200.1 smtp_connect_timeout 30 router_id LVS_01 } vrrp_instance VI_1 { state MASTER interface eth0 virtual_router_id 51 priority 150 advert_int 1 authentication { auth_type PASS auth_pass 1111 } virtual_ipaddress { 192.168.119.150 } } virtual_server 192.168.119.150 80 { delay_loop 6 lb_algo wrr lb_kind DR nat_mask 255.255.255.0 persistence_timeout 300 protocol TCP real_server 192.168.119.130 80 { weight 1 TCP_CHECK connect_timeout 8 nb_get_retry 3 delay_before_retry 3 connect_port 80 } } real_server 192.168.119.133 80 { weight 1 TCP_CHECK connect_timeout 8 nb_get_retry 3 delay_before_retry 3 connect_port 80 } }
启动keepalived
[root@lvs01 keepalived]# /etc/init.d/keepalived start
Starting keepalived: [ OK ]
查看VIP
[root@lvs01 keepalived]# ip add 1: lo: <LOOPBACK,UP,LOWER_UP> mtu 16436 qdisc noqueue state UNKNOWN link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00 inet 127.0.0.1/8 scope host lo inet6 ::1/128 scope host valid_lft forever preferred_lft forever 2: eth0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc pfifo_fast state UP qlen 1000 link/ether 00:0c:29:6e:24:e0 brd ff:ff:ff:ff:ff:ff inet 192.168.119.134/24 brd 192.168.119.255 scope global eth0 inet 192.168.119.150/32 scope global eth0 inet6 fe80::20c:29ff:fe6e:24e0/64 scope link valid_lft forever preferred_lft forever
查看ipvs
[root@lvs01 keepalived]# ipvsadm -ln IP Virtual Server version 1.2.1 (size=4096) Prot LocalAddress:Port Scheduler Flags -> RemoteAddress:Port Forward Weight ActiveConn InActConn TCP 192.168.119.150:80 rr persistent 300 -> 192.168.119.130:80 Masq 1 0 0 -> 192.168.119.133:80 Masq 1 0 0
lvs02配置
[root@lvs02 keepalived]# vim keepalived.conf ! Configuration File for keepalived global_defs { notification_email { acassen@firewall.loc failover@firewall.loc sysadmin@firewall.loc } notification_email_from Alexandre.Cassen@firewall.loc smtp_server 192.168.200.1 smtp_connect_timeout 30 router_id LVS_02 } vrrp_instance VI_1 { state BACKUP interface eth0 virtual_router_id 51 priority 100 advert_int 1 authentication { auth_type PASS auth_pass 1111 } virtual_ipaddress { 192.168.119.150 } } virtual_server 192.168.119.150 80 { delay_loop 6 lb_algo wrr lb_kind DR nat_mask 255.255.255.0 persistence_timeout 300 protocol TCP real_server 192.168.119.130 80 { weight 1 TCP_CHECK connect_timeout 8 nb_get_retry 3 delay_before_retry 3 connect_port 80 } } real_server 192.168.119.133 80 { weight 1 TCP_CHECK connect_timeout 8 nb_get_retry 3 delay_before_retry 3 connect_port 80 } }
查看vip和ipvs
(没有VIP但lvs服务启动、不接受请求)
[root@lvs02 keepalived]# ip add | grep 192.168.119.150 [root@lvs02 keepalived]# ip add | grep 192.168.119.150 [root@lvs02 keepalived]# ip add | grep 192.168.119.150 [root@lvs02 keepalived]# ip add | grep 192.168.119.150 [root@lvs02 keepalived]# ipvsadm -ln IP Virtual Server version 1.2.1 (size=4096) Prot LocalAddress:Port Scheduler Flags -> RemoteAddress:Port Forward Weight ActiveConn InActConn [root@lvs02 keepalived]# ipvsadm -ln IP Virtual Server version 1.2.1 (size=4096) Prot LocalAddress:Port Scheduler Flags -> RemoteAddress:Port Forward Weight ActiveConn InActConn TCP 192.168.119.150:80 wrr persistent 300 -> 192.168.119.130:80 Route 1 0 0 -> 192.168.119.133:80 Route 1 0 0 [root@lvs02 keepalived]# ipvsadm -ln IP Virtual Server version 1.2.1 (size=4096) Prot LocalAddress:Port Scheduler Flags -> RemoteAddress:Port Forward Weight ActiveConn InActConn TCP 192.168.119.150:80 wrr persistent 300 -> 192.168.119.130:80 Route 1 0 0 -> 192.168.119.133:80 Route 1 0 0 [root@lvs02 keepalived]# ip add | grep 192.168.119.150
测试
标签:tab files .gz socket down iptables live back wait
原文地址:http://www.cnblogs.com/zzzhfo/p/6079374.html