标签:rtu ret 测试 屏蔽 image init.d kernel bsp 资源
一、简介
VS/NAT原理图:
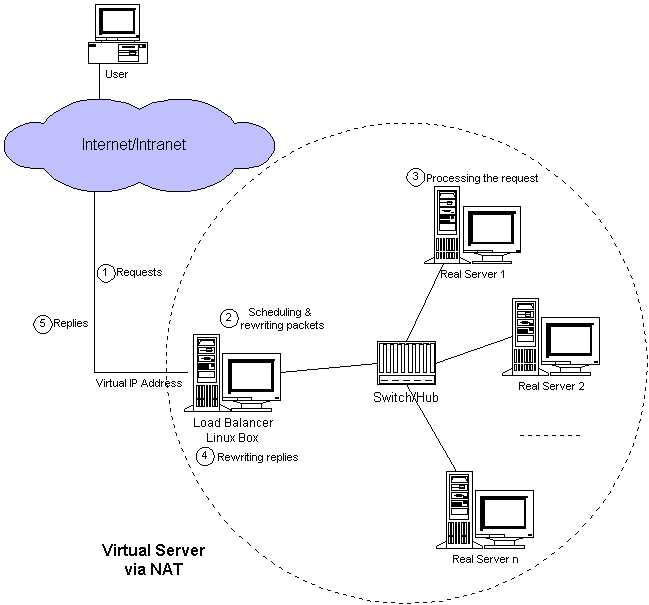
二、系统环境
实验拓扑:
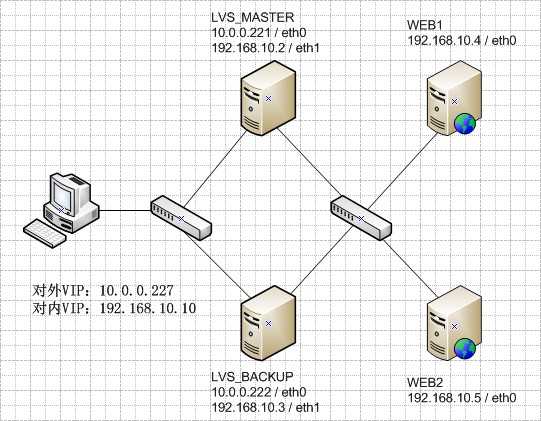
系统平台:CentOS 6.3
Kernel:2.6.32-279.el6.i686
LVS版本:ipvsadm-1.26
keepalived版本:keepalived-1.2.4
三、安装
0、安装LVS前系统需要安装popt-static,kernel-devel,make,gcc,openssl-devel,lftp,libnl*,popt*
1、在两台Director Server上分别配置LVS+Keepalived
LVS install -------------
[root@CentOS-LVS_MASTER ~]# wget http://www.linuxvirtualserver.org/software/kernel-2.6/ipvsadm-1.26.tar.gz
[root@CentOS-LVS_MASTER ~]# ln -s /usr/src/kernels/2.6.32-279.el6.i686//usr/src/linux/
[root@CentOS-LVS_MASTER ~]# tar zxvf ipvsadm-1.26.tar.gz
[root@CentOS-LVS_MASTER ~]# cd ipvsadm-1.26
[root@CentOS-LVS_MASTER ipvsadm-1.26]# make && make install
Keepalived install -------------
[root@CentOS-LVS_MASTER ~]# wget http://www.keepalived.org/software/keepalived-1.2.4.tar.gz
[root@CentOS-LVS_MASTER ~]# tar zxvf keepalived-1.2.4.tar.gz
[root@CentOS-LVS_MASTER ~]# cd keepalived-1.2.4
[root@CentOS-LVS_MASTER keepalived-1.2.4]# ./configure && make && make install
######### 将keepalived做成启动服务,方便管理##########
[root@CentOS-LVS_MASTER ~]# cp /usr/local/etc/rc.d/init.d/keepalived /etc/init.d/
[root@CentOS-LVS_MASTER ~]# cp /usr/local/etc/sysconfig/keepalived /etc/sysconfig/
[root@CentOS-LVS_MASTER ~]# mkdir /etc/keepalived/
[root@CentOS-LVS_MASTER ~]# cp /usr/local/etc/keepalived/keepalived.conf /etc/keepalived/
[root@CentOS-LVS_MASTER ~]# cp /usr/local/sbin/keepalived /usr/sbin/
[root@CentOS-LVS_MASTER ~]# service keepalived start | stop
2、开启路由转发
[root@CentOS-LVS_MASTER ~]# vim /etc/sysctl.conf
net.ipv4.ip_forward = 1
[root@CentOS-LVS_MASTER ~]# sysctl -p
3、配置Keepalived
[root@CentOS-LVS_MASTER ~]# less /etc/keepalived/keepalived.conf
! Configuration File for keepalived
global_defs {
router_id LVS_MASTER #BACKUP上修改为LVS_BACKUP
}
vrrp_instance VI_1 {
state MASTER #BACKUP上修改为BACKUP
interface eth0
virtual_router_id 51
priority 100 #BACKUP上修改为80
advert_int 1
authentication {
auth_type PASS
auth_pass 1111
}
virtual_ipaddress {
10.0.0.227
}
}
vrrp_instance LAN_GATEWAY {
state MASTER #BACKUP上修改为LVS_BACKUP
interface eth1
virtual_router_id 52
priority 100 #BACKUP上修改为80
advert_int 1
authentication {
auth_type PASS
auth_pass 1111
}
virtual_ipaddress {
192.168.10.10
}
}
virtual_server 10.0.0.227 80 {
delay_loop 6
lb_algo rr
lb_kind NAT
# persistence_timeout 5
protocol TCP
real_server 192.168.10.4 80 {
weight 3
TCP_CHECK {
connect_timeout 3
nb_get_retry 3
delay_before_retry 3
connect_port 80
}
}
real_server 192.168.10.5 80 {
weight 3
TCP_CHECK {
connect_timeout 3
nb_get_retry 3
delay_before_retry 3
connect_port 80
}
}
}
BACKUP服务器同上配置,先安装lvs再安装keepalived,然后配置/etc/keepalived/keepalived.conf,只需将批注部分改一下即可。
4、分别在2台Real Server上面设置网关
把网关都设置成:192.168.10.10
5、在2台RealServer中分别配置HTTP
[root@WEB1 ~]# yum -y install httpd
[root@WEB1 ~]# cd /var/www/html/
[root@WEB1 html]# cat index.html
<h1>WEB1/192.168.10.4</h1>
[root@WEB1 html]# /etc/init.d/httpd start
另一台机器配置一样,过程略。
6、分别在CentOS-LVS_MASTER、CentOS-LVS_BACKUP上执行service keepalived start启动keepalived就可实现负载均衡及高可用集群了;
[root@CentOS-LVS_MASTER keepalived]# service keepalived start
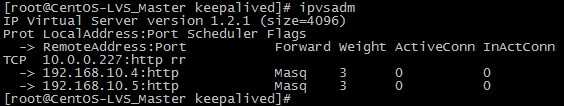
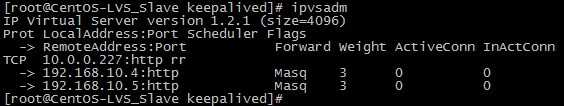
四、测试
####高可用性测试####
模拟故障,将CentOS-LVS_MASTER上的keepalived服务停掉,然后观察CentOS-LVS_BACKUP上的日志,信息如下
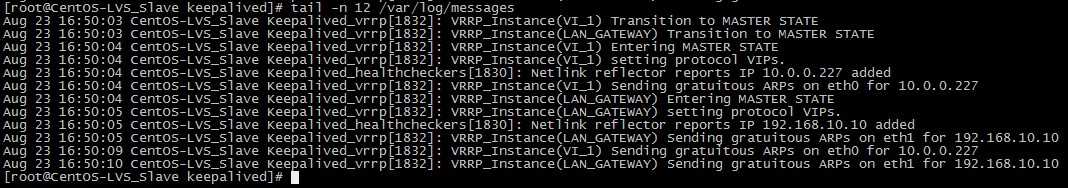
从日志中可知,主机出现故障后,备机立刻检测到,此时备机变为MASTER角色,并且接管了主机的虚拟IP资源,最后将虚拟IP绑定在etho设备上。
将CentOS-LVS_MASTER 上的keepalived服务开启后,CentOS-LVS_BACKUP的日志状态。
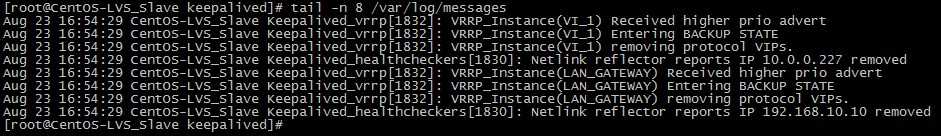
从日志可知,备机在检测到主机重新恢复正常后,释放了虚拟IP资源重新成为BACKUP角色
####故障切换测试####
故障切换是测试当某个节点出现故障后,Keepalived监制模块是否能及时发现然后屏蔽故障节点,同时将服务器转移到正常节点来执行。
将WEB2节点服务停掉,假设这个节点出现故障,然后主、备机日志信息如下
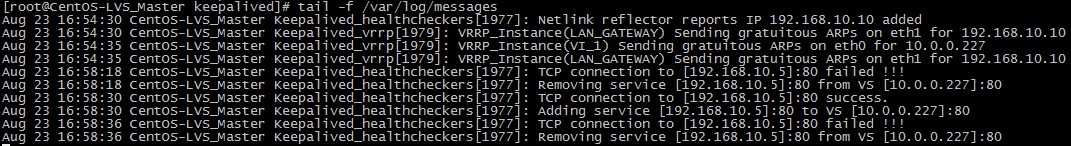
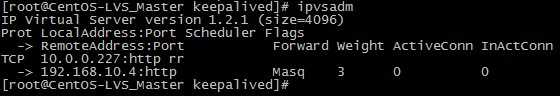
从以上可以看出,Keepalived监控模块检测到192.168.10.5这台主机出现故障后,将WEB2从集群系统中剔除掉了。 此时访问http://10.0.0.227只能看到WEB1了)
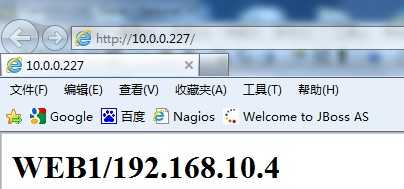
重新启动WEB2节点的服务,日志信息如下:
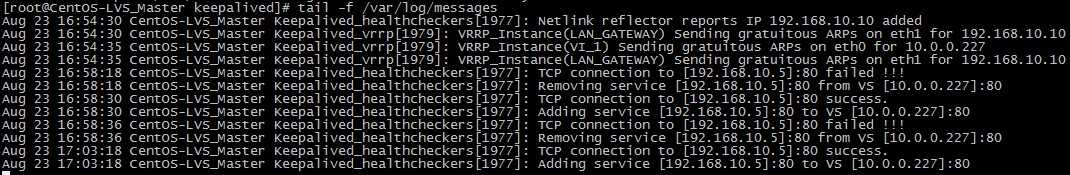
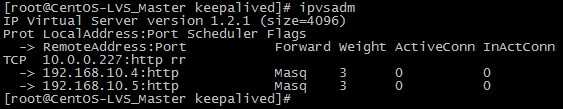
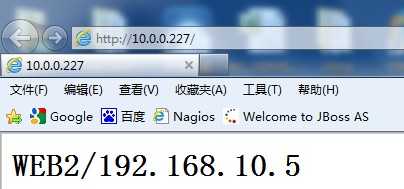
Keepalived监控模块检测到192.168.10.5这台主机恢复正常后,又将此节点加入集群系统中,再次访问就可以访问到WEB2页面了)
标签:rtu ret 测试 屏蔽 image init.d kernel bsp 资源
原文地址:http://www.cnblogs.com/jtlin/p/6159813.html