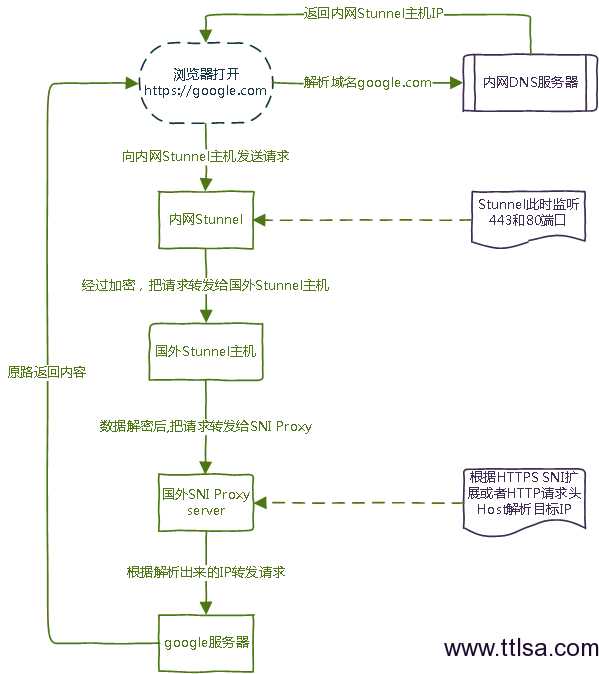
Stunnel可加密网络数据的TCP连接,采用Client/Server将CIient端数据采用SSL加密,安全传输到指定的Server端再解密还原然后发送到目的端口,其使用TLS对tcp协议进行加密
创建CA根私钥及根证书:
根私钥: openssl genrsa -des3 -out /etc/pki/CA/rootca.key 1024
根证书: openssl req -new -x509 -key /etc/pki/CA/rootca.key -out /etc/pki/CA/rootca.crt -days 365
用CA根证书对子证书授权:
用户私钥: openssl genrsa -des3 -out ~/Mysql-master.key 1024
用户证书: openssl req -new -key ~/Mysql-master.key -out ~/Mysql-master.csr
拷贝到CA进行签名: scp Susers.csr root@CA-IP:/ca/
在CA端对csr请求签名:
touch /etc/pki/CA/{index.txt,serial}
echo "01" > /etc/pki/CA/serial
openssl ca -keyfile /etc/pki/CA/rootca.key -cert /etc/pki/CA/rootca.crt -in ./Mysql-master.csr -out ./Mysql-master.pem -days 365
-----------------------------------------------------------------
隧道环境: [Master@192.168.1.2:3306 -- stunnel:3508] ---------------------------- [stunnel:3408 -- Slave@192.168.1.1]
/etc/stunnel/stunnel.conf
Server 端:
client=no 服务端
compression=zlib
syslog=yes
debug=7
output=/var/log/stunnel.log
setuid=root
setgid=root
pid=/var/run/stunnel.pid
cert=/etc/ssl/cert/Mysql-master.pem 证书
key=/etc/ssl/private/Mysql-master.key 私钥
#CAfile = /etc/pki/CA/certs/rootca.crt 根证书
[mysql]
accept=3306 加密本地3306数据
connect=192.168.1.2:99999 监听本机192.168.1.2:3306端口的加密数据并传输至对端的99999端口
Client 端:
client=yes
pid=/tmp/stunnel.pid
debug=7
foreground=no
verify=0 客户端认证:如开启则双方都使用SSL
#CAfile = /etc/pki/CA/certs/rootca.crt 根证书
[mysql]
accept=99999
connect=192.168.1.2:3306
流程图: