标签:type file pre incr 作用 dex eee osi 技术
In wireless networks, theexposed node problem occurs when a node is prevented from sending packets to other nodes because of a neighboring transmitter. Consider an example of 4 nodes labeled R1, S1, S2, and R2, where the two receivers (R1, R2) are out of range of each other, yet the two transmitters (S1, S2) in the middle are in range of each other. Here, if a transmission between S1 and R1 is taking place, node S2 is prevented from transmitting to R2 as it concludes after carrier sense that it will interfere with the transmission by its neighbor S1. However note that R2 could still receive the transmission of S2 without interference because it is out of range of S1.[1]
IEEE 802.11 RTS/CTS mechanism helps to solve this problem only if the nodes are synchronized and packet sizes and data rates are the same for both the transmitting nodes. When a node hears an RTS from a neighboring node, but not the corresponding CTS, that node can deduce that it is an exposed node and is permitted to transmit to other neighboring nodes.[1]
If the nodes are not synchronised (or if the packet sizes are different or the data rates are different) the problem may occur that the sender will not hear the CTS or the ACK during the transmission of data of the second sender.
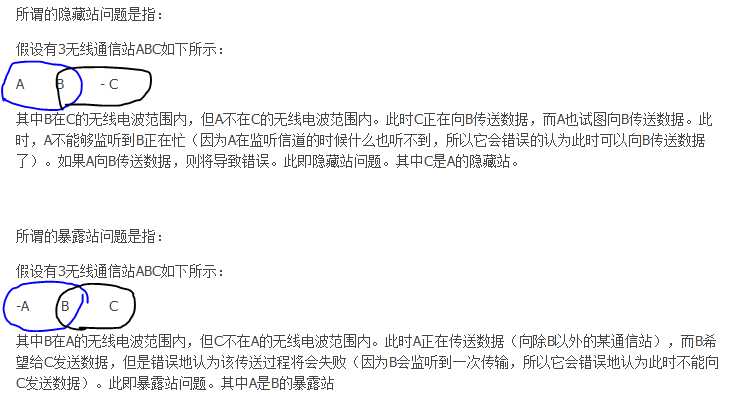
在无线网络中,当由于邻近的发射机阻止节点发送分组到其他节点时,出现暴露的节点问题。考虑标记为R1,S1,S2和R2的4个节点的示例,其中两个接收机(R1,R2)彼此超出范围,但是中间的两个发射机(S1,S2)在每个节点的范围内其他。这里,如果S1和R1之间的传输正在发生,那么节点S2在载波侦听之后结束将被阻止发送到R2,以致它会干扰其邻居S1发送。但是请注意,由于S2超出S1的范围,所以R2仍然可以不受干扰地接收S2的传输。[1]
IEEE 802.11 RTS / CTS机制只有在节点同步并且发送节点的数据包大小和数据速率相同时才有助于解决此问题。当节点从相邻节点听到RTS而不是相应的CTS时,该节点可以推断出它是一个暴露的节点,并被允许传送到其他相邻节点。[1]
如果节点不同步(或者如果分组大小不同或数据速率不同),则可能会发生发送方在传送第二个发送者的数据期间不会听到CTS或ACK的问题。
In wireless networking, the hidden node problem or hidden terminal problem occurs when a node is visible from a wireless access point (AP), but not from other nodes communicating with that AP.[1] This leads to difficulties in media access control sublayer.
Hidden nodes in a wireless network are nodes that are out of range of other nodes or a collection of nodes. Take a physical star topology with an access point with many nodes surrounding it in a circular fashion: Each node is within communication range of the AP, but the nodes cannot communicate with each other, as they do not have a physical connection to each other. In a wireless network, it is likely that the node at the far edge of the access point‘s range, which is known as A, can see the access point, but it is unlikely that the same node can see a node on the opposite end of the access point‘s range, C. These nodes are known as hidden. The problem is when nodes A and C start to send packetssimultaneously to the access point B. Because the nodes A and C are out of range of each other and so cannot detect a collision while transmitting, Carrier sense multiple access with collision detection (CSMA/CD) does not work, and collisions occur, which then corrupt the data received by the access point. To overcome the hidden node problem, RTS/CTS handshaking (IEEE 802.11 RTS/CTS) is implemented in conjunction with the Carrier sense multiple access with collision avoidance (CSMA/CA) scheme. The same problem exists in a MANET.
The hidden node problem can be observed easily in widespread (>50m radius) WLAN setups with many nodes that use directional antennas and have high upload. This is why IEEE 802.11 is suited for bridging the last mile for broadband access only to a very limited extent. Newer standards such as WiMAX assign time slots to individual stations, thus preventing multiple nodes from sending simultaneously and ensuring fairness even in over-subscription scenarios.
IEEE 802.11 uses 802.11 RTS/CTS acknowledgment and handshake packets to partly overcome the hidden node problem. RTS/CTS is not a complete solution and may decrease throughput even further, but adaptive acknowledgments from the base station can help too.
The comparison with hidden stations shows that RTS/CTS packages in each traffic class are profitable (even with short audio frames, which cause a high overhead on RTS/CTS frames).[2]
In the experimental environment following traffic classes are included: data (not time critical), data (time critical), video, audio. Examples for notations: (0|0|0|2) means 2 audio stations; (1|1|2|0) means 1 data station (not time critical), 1 data station (time critical), 2 video stations.
The other methods that can be employed to solve hidden node problem are :
Increasing the transmission power of the nodes can solve the hidden node problem by allowing the cell around each node to increase in size, encompassing all of the other nodes. This configuration enables the non-hidden nodes to detect, or hear, the hidden node. If the non-hidden nodes can hear the hidden node, the hidden node is no longer hidden. Because wireless LANs use the CSMA/CA protocol, nodes will wait their turn before communicating with the access point.
This solution only works if one increases the transmission power on nodes that are hidden. In the typical case of a WiFi network, increasing transmission power on the access point only will not solve the problem because typically the hidden nodes are the clients (e.g. laptops, mobile devices), not the access point itself, and the clients will still not be able to hear each other. Increasing transmission power on the access point is actually likely to make the problem worse, because it will put new clients in range of the access point and thus add new nodes to the network that are hidden from other clients.
Since nodes using directional antennas are nearly invisible to nodes that are not positioned in the direction the antenna is aimed at, directional antennas should be used only for very small networks (e.g., dedicated point-to-point connections). Use omnidirectional antennas for widespread networks consisting of more than two nodes.
Increasing the power on mobile nodes may not work if, for example, the reason one node is hidden is that there is a concrete or steel wall preventing communication with other nodes. It is doubtful that one would be able to remove such an obstacle, but removal of the obstacle is another method of remedy for the hidden node problem. Keep these types of obstacles in mind when performing a site survey.
Another method of solving the hidden node problem is moving the nodes so that they can all hear each other. If it is found that the hidden node problem is the result of a user moving his computer to an area that is hidden from the other wireless nodes, it may be necessary to have that user move again. The alternative to forcing users to move is extending the wireless LAN to add proper coverage to the hidden area, perhaps using additional access points.
There are several software implementations of additional protocols that essentially implement a polling or token passing strategy. Then, a master (typically the access point) dynamically polls clients for data. Clients are not allowed to send data without the master‘s invitation. This eliminates the hidden node problem at the cost of increased latency and less maximum throughput.
在无线网络中,当节点从无线接入点(AP)可见时,而不是与该AP通信的其他节点发生时,会发生隐藏节点问题或隐藏终端问题。[1]这导致媒体访问控制子层的困难。
无线网络中的隐藏节点是超出其他节点或节点集合的节点。以具有多个节点的接入点进行物理星形拓扑结构,循环方式:每个节点位于AP的通信范围内,但节点之间无法进行通信,因为它们之间没有物理连接。在无线网络中,接入点范围的远端(被称为A)的节点很可能能够看到接入点,但是同一节点不太可能看到相对端的节点接入点的范围,C。这些节点被称为隐藏。问题是当节点A和C开始同时向接入点B发送数据包时。因为节点A和C彼此超出范围,因此在发送时不能检测到冲突,具有冲突检测(CSMA / CD)的载波侦听多路访问不起作用,并且发生冲突,从而使由切入点。为了克服隐藏节点问题,RTS / CTS握手(IEEE 802.11 RTS / CTS)与具有冲突避免(CSMA / CA)方案的载波侦听多路访问一起实现。
在具有许多使用定向天线并具有高上传的节点的广泛(> 50m半径)WLAN设置中,可以容易地观察到隐藏节点问题。这就是为什么IEEE 802.11适用于仅在非常有限的范围内桥接最后一公里宽带接入的原因。较新的标准如WiMAX将时隙分配给各个站,从而防止多个节点同时发送,并确保即使在超订购情况下也能公平。
IEEE 802.11使用802.11 RTS / CTS确认和握手包来部分克服隐藏节点问题。RTS / CTS不是一个完整的解决方案,并且可以进一步降低吞吐量,但来自基站的自适应确认也可以帮助。
与隐藏站的比较显示,每个流量类别中的RTS / CTS软件包都是有利可图的(即使是短帧音频,导致RTS / CTS帧的高开销)。[2]
在包括流量类别在内的实验环境中:数据(不是时间关键),数据(时间关键),视频,音频。符号示例:(0 | 0 | 0 | 2)表示2个音频电台; (1 | 1 | 2 | 0)表示1个数据站(不是时间关键),1个数据站(时间关键),2个视频站。
可用于解决隐藏节点问题的其他方法有:
增加节点的传输功率可以通过允许每个节点周围的小区来增加大小,从而解决隐藏节点的问题,包括所有其他节点。该配置使得非隐藏节点能够检测或听到隐藏节点。如果非隐藏节点可以听到隐藏节点,则隐藏节点不再隐藏。由于无线局域网使用CSMA / CA协议,所以在与接入点进行通信之前,节点将等待转机。
该解决方案仅在增加隐藏节点的传输功率时有效。在典型情况下的WiFi网络,在增加发射功率接入点只将不会因为通常隐藏节点是客户端(例如笔记本电脑,移动设备)解决问题,而不是接入点本身和客户意愿依然不能够听到对方 增加接入点的传输功率实际上可能会使问题变得更糟,因为它会将新客户端置于接入点的范围内,从而将新节点添加到隐藏于其他客户端的网络。
由于使用定向天线的节点对于天线未定位的节点几乎不可见,所以定向天线只能用于非常小的网络(例如,专用点对点连接)。对于由两个以上节点组成的广泛网络,使用全向天线。
如果一个节点隐藏的原因是有一个混凝土或钢制墙壁阻止与其他节点的通信,则增加移动节点的功率可能不起作用。令人怀疑的是,能够消除这样的障碍,但是去除障碍物是对隐藏节点问题的另一种补救方法。在进行现场调查时,请牢记这些障碍。
解决隐藏节点问题的另一种方法是移动节点,使它们都可以相互听到。如果发现隐藏节点问题是用户将其计算机移动到与其他无线节点隐藏的区域的结果,则可能需要使该用户再次移动。迫使用户移动的替代方法是扩展无线局域网,以便为隐藏区域添加适当的覆盖范围,也许使用其他接入点。
附加协议的几种软件实现基本上实现轮询或令牌传递策略。然后,主(通常是接入点)动态轮询客户端的数据。客户不允许在没有主人邀请的情况下发送数据。这消除了隐藏节点问题,代价是增加延迟和较小的最大吞吐量。
在以太网中,所有计算机都可以听到互相发送的信息;发送方只需发送一个广播表明他要发送消息即可。
而在无线网络中,并不能覆盖所有范围,分区域传播。
有三台电脑,A、B、C
A的发送范围覆盖B但是无法覆盖C,B的接收范围同时覆盖A、B
A、希望向B发送信息,这时A、B希望在发送信息的时没有人在B接收范围内发送信息,因为那样会干扰接受。就像在以太网中一样,A发送了一个广播,表明他要向B发送信息,但是在这时恰巧C也希望向B发送信息,由于 A的发送范围覆盖B但是无法覆盖C,所以C误以为没有人会向B发送信息,A也误以为所有人都听到了他要发送信息,于是两台计算机同时开始发送,互相干扰导致传送失败。
暴露站问题
C的发送范围不能覆盖B但是A的发送范围覆盖A和B,A发送了一个广播,C误以为他的发送会,于是干扰成本,降低了网络利用率
解决方案:
发送方首先发送RTS,这时所有听到的计算机静默一段时间等待CTS,接收方收到CTS后立即回复CTS,受到CTS的计算机立即安静下来(不包括发送信息的计算机),而没有受到CTS的计算机继续发送信息
instance:
hidden node and exposed node problem
标签:type file pre incr 作用 dex eee osi 技术
原文地址:http://www.cnblogs.com/wanghui626/p/6974076.html