标签:linux
智能DNS
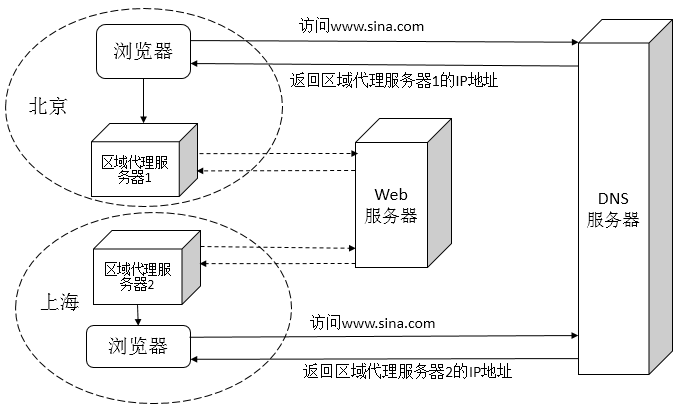
智能DNS实现如下图:当用户通过浏览器访问www.sina.com,浏览器向DNS服务器查找服务器地址,北京的用户,返回区域代理服务器1的ip地址,上海的用户返回区域服务器2的ip地址,以此类推。以北京用户为例:当DNS服务器返回区域代理服务器1的地址,用户访问区域代理服务器1,区域代理服务器一般存放静态的一些内容,当用户只访问静态的内容时,区域代理服务器1提供服务,当用户访问一些动态内容时,区域代理服务器1就向web服务器寻找,然后返回给用户。
实验:实现上海和北京和其他地区的智能DNS管理
说明: 实现当上海地区访问www.sina.com 返回ip为6.6.6.6
当北京地区访问www.sina.com 返回ip为1.1.1.1
当其他地区访问www.sina.com 返回ip为2.2.2.2
以ip地址来划分区域,上海的ip地址段为:
192.168.191.0/24;
192.168.192.0/24;
北京的ip地址段为:
172.17.251.0/24;
172.18.251.0/24;
以此来模拟智能DNS实现过程。
实现步骤:三大步:
第一、准备数据库文件
地址www.sina.com 返回的地址等信息
第二、定义acl
定义某个区域的ip地址
第三、定义view
关联acl和数据库文件
1、安装包
yum install bind
2、启动服务
systemctl start named
注意:DNS服务的包名为bind ,服务名为named
主配置文件:/etc/named.conf, /etc/named.rfc1912.zones,/etc/rndc.key
解析库文件: /var/named/ZONE_NAME.ZONE
3、创建DNS数据库文件
cd /var/named
vim sina.com.zone.beijing
$TTL 1D @ IN SOA dns1 rname.invalid. ( 2017101101 ; serial 1D ; refresh 1H ; retry 1W ; expire 3H ) ; minimum @ NS dns1 dns1 A 172.17.251.107 dns1 A 192.168.191.107 www A 1.1.1.1
vim sina.com.zone.shanghai
$TTL 1D @ IN SOA dns1 rname.invalid. ( 2017101101 ; serial 1D ; refresh 1H ; retry 1W ; expire 3H ) ; minimum @ NS dns1 dns1 A 172.17.251.107 dns2 A 192.168.191.107 www A 6.6.6.6
vim sina.com.zone.other
$TTL 1D @ IN SOA dns1 rname.invalid. ( 2017101101 ; serial 1D ; refresh 1H ; retry 1W ; expire 3H ) ; minimum @ NS dns1 dns1 A 172.17.251.107 dns1 A 192.168.191.107 www A 2.2.2.2
4、创建acl和view
vim /etc/named.conf
(1)注释这两行
options {
// listen-on port 53 { localhost; };
listen-on-v6 port 53 { ::1; };
directory "/var/named";
dump-file "/var/named/data/cache_dump.db";
statistics-file "/var/named/data/named_stats.txt";
memstatistics-file "/var/named/data/named_mem_stats.txt";
// allow-query { any; };第一行代表53端口绑定的ip,allow-query {};表示允许查询的主机
将这两行注释;或者改成上面,localhost表示允许该主机上的所有ip都可以绑定53端口,any代表所有ip
(2)在该文件添加
acl shanghainet {
192.168.191.0/24;
192.168.192.0/24;
};
acl beijingnet {
172.17.251.0/24;
172.18.251.0/24;
};(3)创建view
将下面的文件修改成下面
创建view的方法1:关联数据库文件时,直接写文件名
方法2:将文件写在/etc/named.rfc1912.zone.shanghai,中,在该文件中指定文件。
view beijingview {
match-clients { beijingnet;}; //连接acl
zone "sina.com" {
type master;
file "sina.com.zone.beijing"; // 指定数据库文件
};
zone "." IN {
type hint; //允许该地区的用户直接访问根地址
file "named.ca";
};
};
view shanghaiview {
match-clients { shanghainet;};
include "/etc/named.rfc1912.zones.shanghai";
zone "." IN {
type hint;
file "named.ca";
};
};
view otherview {
match-clients {any;};
include "/etc/named.rfc1912.zones.other";
zone "." IN {
type hint;
file "named.ca";
};
};
include "/etc/named.root.key";整个文件如下
acl shanghainet {
192.168.191.0/24;
192.168.192.0/24;
};
acl beijingnet {
172.17.251.0/16;
172.18.251.0/16;
};
options {
// listen-on port 53 { localhost; };
listen-on-v6 port 53 { ::1; };
directory "/var/named";
dump-file "/var/named/data/cache_dump.db";
statistics-file "/var/named/data/named_stats.txt";
memstatistics-file "/var/named/data/named_mem_stats.txt";
// allow-query { any; };
allow-transfer { none; };
/*
- If you are building an AUTHORITATIVE DNS server, do NOT enable recursion.
- If you are building a RECURSIVE (caching) DNS server, you need to enable
recursion.
- If your recursive DNS server has a public IP address, you MUST enable access
control to limit queries to your legitimate users. Failing to do so will
cause your server to become part of large scale DNS amplification
attacks. Implementing BCP38 within your network would greatly
reduce such attack surface
*/
recursion yes;
dnssec-enable no;
dnssec-validation no;
/* Path to ISC DLV key */
bindkeys-file "/etc/named.iscdlv.key";
managed-keys-directory "/var/named/dynamic";
pid-file "/run/named/named.pid";
session-keyfile "/run/named/session.key";
};
logging {
channel default_debug {
file "data/named.run";
severity dynamic;
};
};
logging {
channel default_debug {
file "data/named.run";
severity dynamic;
};
};
view beijingview {
match-clients { beijingnet;};
zone "sina.com" {
type master;
file "sina.com.zone.beijing";
};
zone "." IN {
type hint;
file "named.ca";
};
};
view shanghaiview {
match-clients { shanghainet;};
include "/etc/named.rfc1912.zones.shanghai";
zone "." IN {
type hint;
file "named.ca";
};
};
view otherview {
match-clients {any;};
include "/etc/named.rfc1912.zones.other";
zone "." IN {
type hint;
file "named.ca";
};
};
include "/etc/named.root.key"; 5、 将/etc/named.rfc1912.zones 复制两份命名为/etc/named.rfc1912.zones.shanghai
/etc/named.rfc1912.zones.other
vim /etc/named.rfc1912.zones.shanghai
添加如下内容
zone "sina.com" IN {
type master;
file "sina.com.zone.shanghai";
};vim /etc/named.rfc1912.zones.other
添加如下内容
zone "sina.com" IN {
type master;
file "sina.com.zone.other";
};6、启动服务
重新加载服务:rndc reload
注意:在centos6或centos7上最好不要用restart,容易把服务死掉,起不来服务。
这里rndc reload 这个命令时专门管理DNS服务的,如果必要重启服务了,先关闭服务,再开启服务。
7、测试:
在某一客户端上,将该客户端的DNS执行服务器主机
(1)如果网络是自动获取的,则修改vim /etc/resolv.conf
nameserver 172.17.251.107
(2)如果网络时自己配置的,/etc/sysconfig/network-scripts ,修改该目录下的桥接网卡的DNS1=172.17.251.107 。
重启服务 systemctl restart network
在客户端测试:
dig www.sina.com @192.168.191.107
dig www.sina.com @172.17.251.107
[root@centos7 named]# dig www.sina.com @192.168.191.107
; <<>> DiG 9.9.4-RedHat-9.9.4-37.el7 <<>> www.sina.com @192.168.191.107
;; global options: +cmd
;; Got answer:
;; ->>HEADER<<- opcode: QUERY, status: SERVFAIL, id: 57522
;; flags: qr rd ra; QUERY: 1, ANSWER: 0, AUTHORITY: 0, ADDITIONAL: 1
;; OPT PSEUDOSECTION:
; EDNS: version: 0, flags:; udp: 4096
;; QUESTION SECTION:
;www.sina.com. IN A
;; Query time: 0 msec
;; SERVER: 192.168.191.107#53(192.168.191.107)
;; WHEN: Thu Oct 12 11:10:48 CST 2017
;; MSG SIZE rcvd: 41
遇到错误
排错:1、查看防火墙iptables -vnL ,清除防火墙策略iptables -F
2、查看网络连接。dig www.baidu.com
rndc flush 清除缓存
rndc reload 重新启动
发现这两个都清除了,还是出现相同错误
最后发现是数据库文件的权限问题,在运行DNS时,是用named这个用户,执行操作的,所以当文件的所有者,所属组为root是,将权限改成644
上海用户,解析出来6.6.6.6。成功
[root@centos6 network-scripts]# dig www.sina.com @192.168.191.107
; <<>> DiG 9.8.2rc1-RedHat-9.8.2-0.62.rc1.el6 <<>> www.sina.com @192.168.191.107
;; global options: +cmd
;; Got answer:
;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 63539
;; flags: qr aa rd ra; QUERY: 1, ANSWER: 1, AUTHORITY: 1, ADDITIONAL: 2
;; QUESTION SECTION:
;www.sina.com. IN A
;; ANSWER SECTION:
www.sina.com. 86400 IN A 6.6.6.6
;; AUTHORITY SECTION:
sina.com. 86400 IN NS dns1.sina.com.
;; ADDITIONAL SECTION:
dns1.sina.com. 86400 IN A 172.17.251.107
dns1.sina.com. 86400 IN A 192.168.191.107
;; Query time: 2 msec
;; SERVER: 192.168.191.107#53(192.168.191.107)
;; WHEN: Mon Oct 9 13:34:41 2017
;; MSG SIZE rcvd: 97
本文出自 “Linux 学习记录” 博客,请务必保留此出处http://guanm.blog.51cto.com/13126952/1971653
标签:linux
原文地址:http://guanm.blog.51cto.com/13126952/1971653