标签:认证 att 我的网站 ide war page ice nload 接收
感觉需要用日记鞭策一下自己,回顾自己的每天有没有浪费。
上午基本是玩了,只看了下英文网站,记录一下,顺便积累点单词。
The Exploit Database is maintained by Offensive Security, an information security training
company that provides various Information Security Certifications as well as high end
penetration testing services.The Exploit Database is a non-profit project that is provided as a
public service by Offensive Security.

我们是谁 Exploit Database 被一个叫Offensive Security的公司维护,一个提供多种信息安全认证和高端渗透测试服务的信息安全培训公司。Exploit Database是Offensive Security公司作为的非盈利性项目提供的。
The Exploit Database is a CVE compliant archive of public exploits and corresponding vulnerable software,developed for use by penetration testers
and vulnerability researchers. Our aim is to serve the most comprehensive collection of exploits gathered through direct submissions, mailing lists,
as well as other public sources, and present them in a freely-available and easy-to-navigate database. The Exploit Database is a repository for
exploits and proof-of-concepts rather than advisories, making it a valuable resource for those who need actionable data right away.

我们做什么 Exploit Database 是一个CVE(Common Vulnerabilities & Exposures)标准的关于公共漏洞利用和相应的漏洞软件的档案,它为渗透测试人员和漏洞研究人员开发。我们的目的是提供最全面的漏洞集合的收集,通过直接提交,邮件列表以及其他公共资源,并且把它们呈现在一个自由可用和易于导航的数据库中。Exploit Database 是一个漏洞利用(exp)和观点证明(poc)的仓库而非公告,这对于那些马上需要可操作数据的人来说是非常有价值的资源。
Each exploit in the Exploit Database may have several additional fields, such as Date, Description, Platform, Author, and D,A,V. While the first four
titles are self explanatory, the latter three are not. Here’s a short breakdown of their meanings:

Exploit Database 中的每一个漏洞利用都有若干字段,比如日期、描述、平台、作者和D,A,V等。前四个标题是不言而喻的,后三个需要解释一下。下面是这些含义的简短分解:
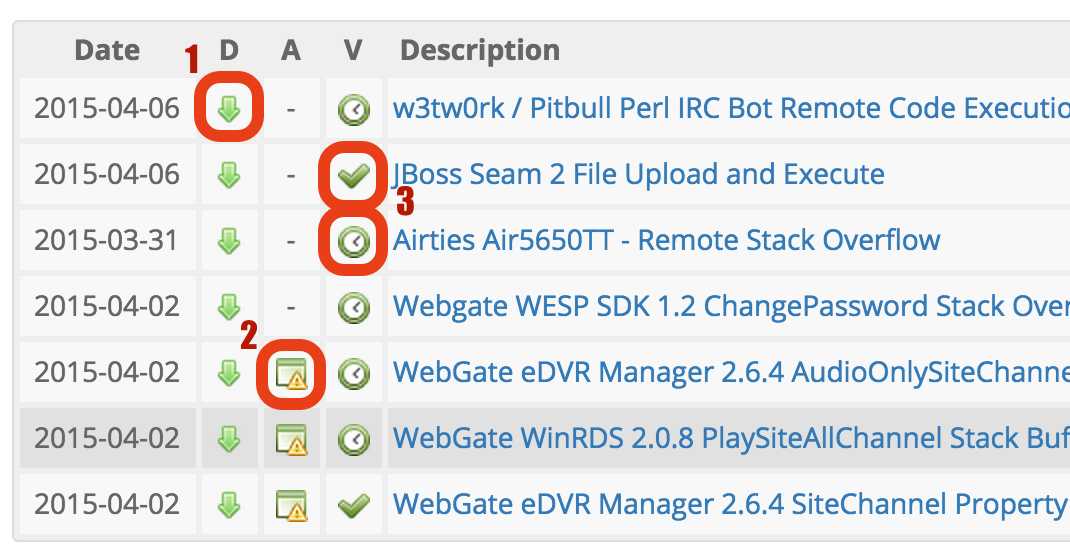
1. “D” for Download. This link will download the raw source code of the exploit as it was submitted to us.

“D”是下载。这个链接可以下载我们提交的漏洞利用的源代码。
2. “A” for Application. We make an effort to archive vulnerable applications for the benefit of researchers whenever we can. This facilitates
debugging and analysis should the vulnerable application become unavailable.

“A”是应用程序。我们尽可能的将易受攻击的应用程序存档,以造福研究人员们。这有利于调试和分析,使易受攻击的应用程序变得不可被利用。
3. “V” for Verified. We make an effort to verify exploits in our labs, when possible. A “non verified” exploit (marked by a clock icon) simply means we
did not have the opportunity to test the exploit internally.

“V”是已验证的。我们尽可能在实验室中验证漏洞利用。一个未被验证的漏洞利用(用时钟图标标记)仅仅意味着我们没有机会在内部测试漏洞利用。
Refer to our “Submit” page to review the Exploit Database guidelines for acceptance.

参考我们的“提交”页面,检查 Exploit Database 的验收规则。

你们为什么不接收我提交的漏洞? 我们不提交违反我们漏洞接收政策或者已测试的和无效的漏洞。更多的请阅读“提交”页面。
标签:认证 att 我的网站 ide war page ice nload 接收
原文地址:http://www.cnblogs.com/kuboy/p/7705172.html