标签:rsa syntax add 随机数 分享图片 private asn 解密 length
ASN.1 syntax,octet string是一个8 bytes sequence string.
RSA中涉及到的Data conversion:
1)I2OSP,Integer to Octet String(8bytes sequence);
Input: x nonnegative integer to be converted
xLen intended length of resulting octet string
Output:X corrsponding octet string of length xLen
2)OS2IP,octet string to a nonnegative integer,
Input:X octet string to be converted
Output:x corresponding nonnegative integer
Encryption和decryption primitives:
1)RSAEP( (n,e), m), Input (n,e) RSA public key
m message,integer 0 - n-1
Output c ciphertext
c = m^e mod n
2)RSADP(K, c), Input K RSA private key, a pair (n,d)
a quintuple(p, q, dp, dq, qinv)
c ciphertext,integer 0 - n-1
Output m message,integer 0 - n-1
m = c^d mod n
或者:
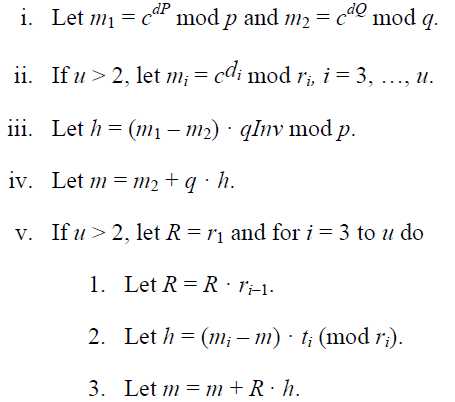
Signature和Verification privimitives:
1)RSASP1(K, m), Input K RSA private key, a pair (n, d)
a quintuple(p, q, dp, dq, qinv)
m mesage,integer 0 - n-1
Output s signature,integer 0 - n-1
s = m^d mod n
或者:
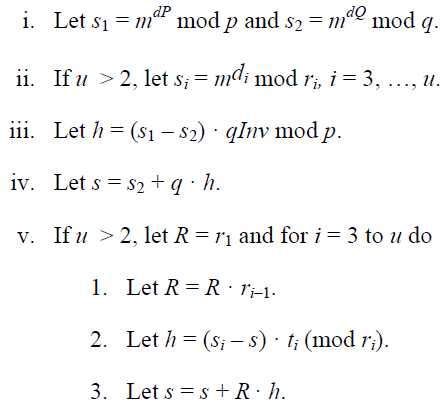
2)RSAVP1 ( (n,e), s) Input (n,e) RSA public key
s signature,integer 0 - n-1
Output m message, integer 0 - n-1
m = s^e mod n
RSASA-PSS的签名流程:1)EMSA-PSS encoding, EM = EMSA-PSS-encode(M, modbits -1)
产生的EM的长度,经过取8mod向上取整,还是n;
2)RSA signature, m = OS2IP (EM)
s = RSASP1 (K, m)
S = I2OSP (s, k)
产生的签名的长度一定是n;
RSASA-PKCS1-v1_5的签名流程:1) EM = EMSA-PKCS1-v1_5 (M, k),k的大小为n的长度;
2) RSA signature,m = OS2IP (EM);
s = RSASP1 (K, m);
S = I2OSP (s, k);
产生的签名的长度一定是n;
PKCS#1-V-1.5的signature encode方式:EMSA-PKCS1-v1_5-Encode (M, emlen)
输入:
1) Hash function;hLen表示hash function output;
2) Message;
3) emlen,最少tLen+11,tLen表示对T进行DER之后的值的长度;
输出:
1) EM,encoded message;
2) Error,“message too long”, encoded message length too short;
流程:
1)进行hash运算; H = Hash(m);
2)将hash function和hash value进行ASN.1的DER编码,输出T,T的长度为tLen;
3)如果emLen < tLen + 11,输出error信息;
4)产生一个PS的字符串,以FF为最后一个有效字符;最少8个byte
5)将数据拼接起来,组成EM;
![]()
几种hash算法的T的值:
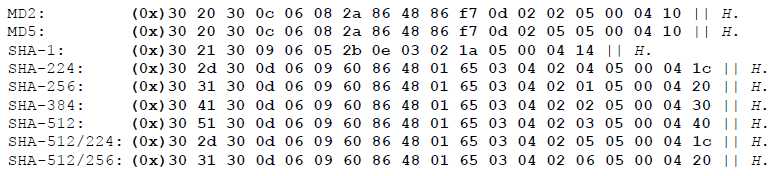
SHA-1的T的长度:120+160 = 280
SHA-224、SHA-512/224的T的长度:154+224 = 378
SHA-256、SHA-512/256的T的长度:154+256 = 410
SHA-384的T的长度:154+384 = 538
SHA-512的T的长度:154+512 = 666
PKCS#1 PSS sign encode(M, embits) options: Hash function,hLen表示hash function的输出octets的长度;
MGF mask generation function;
sLen,length in octets of the salt;
Input:M message to be encoded;
embits 8hLen + 8sLen + 9 < embits < EM的长度;
Output:EM,encoded message;EMLen = embits/8向上取整;
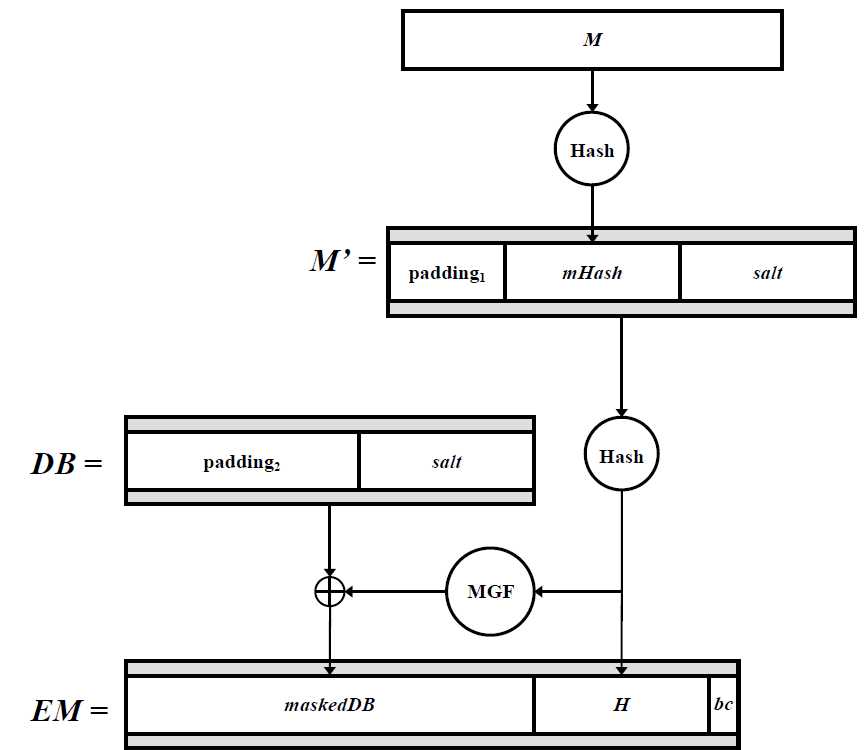
流程:1) mHash = Hash(M),hLen的长度;
2) emLen < hLen + sLen + 2,直接报错;
3) 产生随机数sLen长度的salt,sLen为0时,salt为空字符串;
4) M‘ = (0x)00 00 00 00 00 00 00 00 || mHash || salt,M‘的长度为8+hLen+sLen
5) H = Hash(m‘),长度hLen;
6) 产生字符串 PS,emLen - sLen -hLen -2个字符;
7) DB = PS || 0x01 || salt,DB的长度为emLen - hLen -1;
8) dbmask = MGF(H, emLen-hLen-1)
9) maskDB = DB^+dbmask;
10) 设置maskedDB的最左边的8emLen - emBits个字符为零;
11) EM = maskDB || H || 0xbc;
MGF function:对输入的数据进行hash压缩或扩展;
MGF1(mgfseed, maskLen) Options Hash
Input: mgfseed,seed from which mask is generated;
maskLen,输出mask的长度,最大2^32hLen;
Output:mask,输出mask;
流程:
1)首先判断maskLen < 2^32hLen;否则报错;
2)T清空;
3)counter 从0 到 maskLen/hLen -1 做hash运算和拼接操作;
C = I2OSP (counter, 4), C一共是32byte;
T = T || Hash(mgfSeed || C)
验签与签名的流程,完全相反,
加解密的流程,padding方式与sign/verify不同,
标签:rsa syntax add 随机数 分享图片 private asn 解密 length
原文地址:http://www.cnblogs.com/-9-8/p/7997965.html