上传包以后解压
tar zxf DenyHosts-2.6.tar.gz
进入目录
cd DenyHosts-2.6
重启日志记录器
echo "" > /var/log/secure && service rsyslog restart
用python执行脚本
python setup.py install
进入目录
cd /usr/share/denyhosts/
备份一下
cp denyhosts.cfg-dist denyhosts.cfg
cp daemon-control-dist daemon-control
授予权限
chown root daemon-control
chmod 700 daemon-control
开启daemon
./daemon-control start
设置开机自启
ln -sf /usr/share/denyhosts/daemon-control /etc/init.d/denyhosts
chkconfig --add denyhosts
chkconfig --level 2345 denyhosts on
写到开机启动项
echo "/usr/share/denyhosts/daemon-control start" >> /etc/rc.local
修改配置文件
DAEMON_PURGE = 1y #一年后清除已经被禁止的ip
BLOCK_SERVICE = sshd #不允许访问ssh服务
DENY_THRESHOLD_INVALID = 5 #允许无效用户登录失败的次数
DENY_THRESHOLD_VALID = 5 #允许普通用户登录失败的次数
DENY_THRESHOLD_ROOT = 2 #允许root用户登录失败的次数
重启denyhosts
/etc/init.d/denyhosts restart
每次删除被封的ip时,也需要重启
解除被封的ip
# vim /etc/hosts.deny
# vim /usr/share/denyhosts/data/users-hosts
# vim /usr/share/denyhosts/data/hosts
# vim /usr/share/denyhosts/data/hosts-restricted
# vim /usr/share/denyhosts/data/hosts-root
这些文件里删除被误封的ip后,重启denyhosts服务
测试开始192.168.0.106是攻击者 192.168.0.104是服务器
ssh root@192.168.0.104 三次后
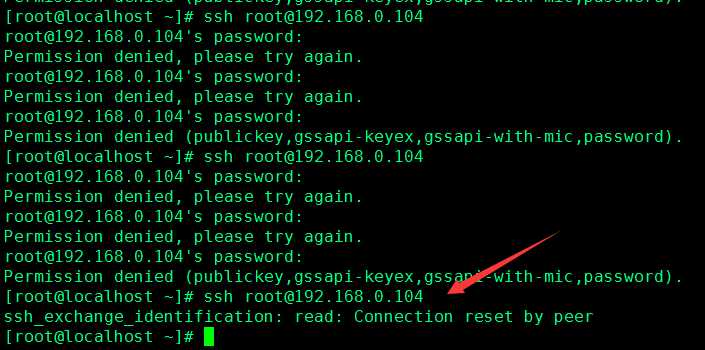
会显示无法连接ssh
[root@localhost ~]# ssh root@192.168.0.104
ssh_exchange_identification: read: Connection reset by peer
防暴力破解成功
点一杯星巴克庆祝一下!

