k8s集群中的应用通常是通过ingress实现微服务发布的,前文介绍过在K8S集群中使用traefik实现服务的自动发布,其实现方式是traefik通过集群的DNS服务来解析service对应的集群地址(clusterip),从而将用户的访问请求转发到集群地址上。因此,在部署完集群后的第一件事情应该是配置DNS服务,目前可选的方案有skydns, kube-dns, coredns。
kube-dns是Kubernetes中的一个内置插件,目前作为一个独立的开源项目维护,见https://github.com/kubernetes/dns。该DNS服务器利用SkyDNS的库来为Kubernetes pod和服务提供DNS请求。
CoreDNS项目是SkyDNS2的作者,Miek Gieben采用更模块化,可扩展的框架构建,将此DNS服务器作为Kube-DNS的替代品。CoreDNS作为CNCF中的托管的一个项目,在Kuberentes1.9版本中,使用kubeadm方式安装的集群可以通过以下命令直接安装CoreDNS。
kubeadm init --feature-gates=CoreDNS=true。
本文将介绍coredns的配置
关于在1.5.2 rpm集群版本上配置skydns服务请参考:
http://blog.51cto.com/ylw6006/2067923
关于traefik实现微服务发布请参考:
http://blog.51cto.com/ylw6006/2072667
http://blog.51cto.com/ylw6006/2073718
关于kube-dns的详细介绍可以参考大牛博客:
https://jimmysong.io/posts/configuring-kubernetes-kube-dns/
一、准备yaml配置文件
1、coredns-sa.yaml文件,创建ServiceAccount
# cat coredns-sa.yaml
apiVersion: v1
kind: ServiceAccount
metadata:
name: coredns
namespace: kube-system
labels:
kubernetes.io/cluster-service: "true"
addonmanager.kubernetes.io/mode: Reconcile2、coredns-rbac.yaml文件,创建rbac ClusterRole和ClusterRoleBinding
# cat coredns-rbac.yaml
apiVersion: rbac.authorization.k8s.io/v1
kind: ClusterRole
metadata:
labels:
kubernetes.io/bootstrapping: rbac-defaults
addonmanager.kubernetes.io/mode: Reconcile
name: system:coredns
rules:
- apiGroups:
- ""
resources:
- endpoints
- services
- pods
- namespaces
verbs:
- list
- watch
---
apiVersion: rbac.authorization.k8s.io/v1
kind: ClusterRoleBinding
metadata:
annotations:
rbac.authorization.kubernetes.io/autoupdate: "true"
labels:
kubernetes.io/bootstrapping: rbac-defaults
addonmanager.kubernetes.io/mode: EnsureExists
name: system:coredns
roleRef:
apiGroup: rbac.authorization.k8s.io
kind: ClusterRole
name: system:coredns
subjects:
- kind: ServiceAccount
name: coredns
namespace: kube-system3、coredns-configmap.yaml文件,定义Corefile配置文件的参数配置
# cat coredns-configmap.yaml
apiVersion: v1
kind: ConfigMap
metadata:
name: coredns
namespace: kube-system
data:
Corefile: |
.:53 {
errors
log
health
kubernetes cluster.local 10.254.0.0/18
proxy . /etc/resolv.conf
cache 30
}4、coredns-deployment.yaml文件,定义pod的创建模板
# cat coredns-deployment.yaml
apiVersion: extensions/v1beta1
kind: Deployment
metadata:
name: coredns
namespace: kube-system
labels:
k8s-app: coredns
kubernetes.io/cluster-service: "true"
kubernetes.io/name: "CoreDNS"
spec:
replicas: 1
selector:
matchLabels:
k8s-app: coredns
template:
metadata:
labels:
k8s-app: coredns
annotations:
scheduler.alpha.kubernetes.io/critical-pod: ‘‘
scheduler.alpha.kubernetes.io/tolerations: ‘[{"key":"CriticalAddonsOnly", "operator":"Exists"}]‘
spec:
serviceAccountName: coredns
containers:
- name: coredns
image: coredns/coredns:latest
imagePullPolicy: Always
args: [ "-conf", "/etc/coredns/Corefile" ]
volumeMounts:
- name: config-volume
mountPath: /etc/coredns
ports:
- containerPort: 53
name: dns
protocol: UDP
- containerPort: 53
name: dns-tcp
protocol: TCP
livenessProbe:
httpGet:
path: /health
port: 8080
scheme: HTTP
initialDelaySeconds: 60
timeoutSeconds: 5
successThreshold: 1
failureThreshold: 5
dnsPolicy: Default
volumes:
- name: config-volume
configMap:
name: coredns
items:
- key: Corefile
path: Corefile5、 coredns-service.yaml文件,定义服务的名称
# cat coredns-service.yaml
apiVersion: v1
kind: Service
metadata:
name: coredns
namespace: kube-system
labels:
k8s-app: coredns
kubernetes.io/cluster-service: "true"
kubernetes.io/name: "CoreDNS"
spec:
selector:
k8s-app: coredns
clusterIP: 10.254.0.2
ports:
- name: dns
port: 53
protocol: UDP
- name: dns-tcp
port: 53
protocol: TCP二、通过yaml配置文件创建coredns
# kubectl get node
# kubectl get pod,svc,deployment,rc
# kubectl get pod,svc,deployment,rc -n kube-system
# cd yaml/coredns/
# ls -l
# kubectl create -f .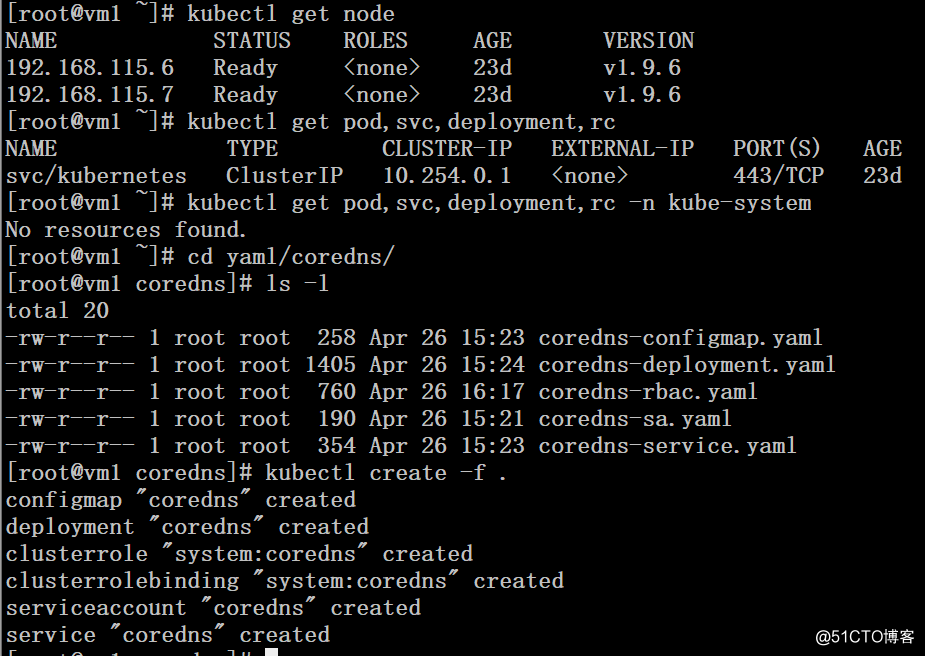
# kubectl get pod,svc,deployment,rc -n kube-system
三、创建一个nginx服务用于测试
# kubectl create -f .
# kubectl get pod,svc,deployment,rc
# kubectl run -i --tty busybox --image=registry.59iedu.com/busybox /bin/sh 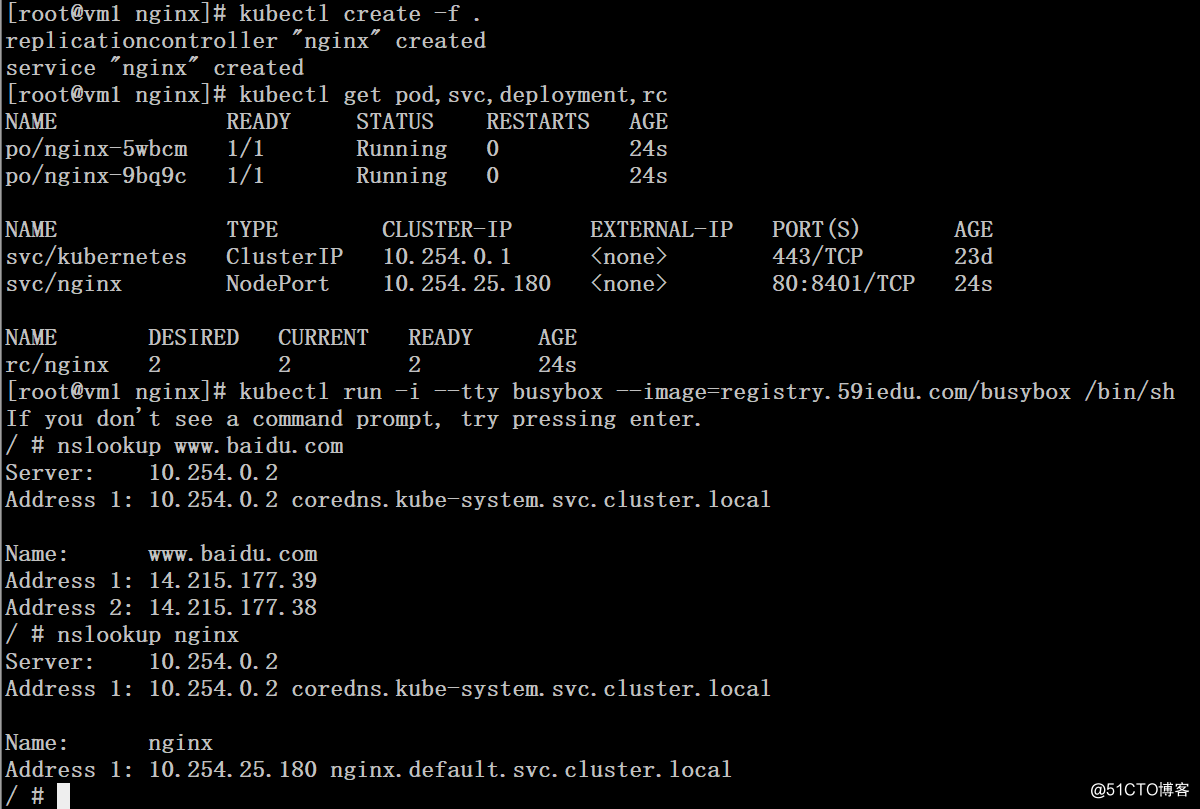
原文地址:http://blog.51cto.com/ylw6006/2108426