标签:color 的区别 根据 user unifi sync art -- 文档
参考文档:
# 在任意控制节点创建数据库,数据库自动同步,以controller01节点为例; [root@controller01 ~]# mysql -uroot -pmysql_pass MariaDB [(none)]> CREATE DATABASE keystone; MariaDB [(none)]> GRANT ALL PRIVILEGES ON keystone.* TO ‘keystone‘@‘localhost‘ IDENTIFIED BY ‘keystone_dbpass‘; MariaDB [(none)]> GRANT ALL PRIVILEGES ON keystone.* TO ‘keystone‘@‘%‘ IDENTIFIED BY ‘keystone_dbpass‘; MariaDB [(none)]> flush privileges; MariaDB [(none)]> exit;
# 在全部控制节点安装keystone,以controller01节点为例; [root@controller01 ~]# yum install openstack-keystone httpd mod_wsgi mod_ssl -y
# 在全部控制节点设置,以controller01节点为例; # 红色加粗字体为修改部分 [root@controller01 ~]# cp /etc/keystone/keystone.conf /etc/keystone/keystone.conf.bak [root@controller01 ~]# egrep -v "^$|^#" /etc/keystone/keystone.conf [DEFAULT] [application_credential] [assignment] [auth] [cache] backend = oslo_cache.memcache_pool enabled = true memcache_servers = controller01:11211,controller02:11211,controller03:11211 [catalog] [cors] [credential] [database] connection = mysql+pymysql://keystone:keystone_dbpass@controller/keystone [domain_config] [endpoint_filter] [endpoint_policy] [eventlet_server] [federation] [fernet_tokens] [healthcheck] [identity] [identity_mapping] [ldap] [matchmaker_redis] [memcache] [oauth1] [oslo_messaging_amqp] [oslo_messaging_kafka] [oslo_messaging_notifications] [oslo_messaging_rabbit] [oslo_messaging_zmq] [oslo_middleware] [oslo_policy] [paste_deploy] [policy] [profiler] [resource] [revoke] [role] [saml] [security_compliance] [shadow_users] [signing] [token] provider = fernet [tokenless_auth] [trust] [unified_limit]
# 任意控制节点操作 [root@controller01 ~]# su -s /bin/sh -c "keystone-manage db_sync" keystone # 查看验证 [root@controller01 ~]# mysql -h controller01 -ukeystone -pkeystone_dbpass -e "use keystone;show tables;"
# 选定任意控制节点(controller01)做fernet秘钥初始化,在/etc/keystone/生成相关秘钥及目录 [root@controller01 ~]# keystone-manage fernet_setup --keystone-user keystone --keystone-group keystone [root@controller01 ~]# keystone-manage credential_setup --keystone-user keystone --keystone-group keystone # 向controller02/03节点同步秘钥 [root@controller01 ~]# scp -r /etc/keystone/fernet-keys/ /etc/keystone/credential-keys/ root@172.30.200.32:/etc/keystone/ [root@controller01 ~]# scp -r /etc/keystone/fernet-keys/ /etc/keystone/credential-keys/ root@172.30.200.33:/etc/keystone/ # 同步后,注意controller02/03节点上秘钥权限 [root@controller02 ~]# chown keystone:keystone /etc/keystone/credential-keys/ -R [root@controller02 ~]# chown keystone:keystone /etc/keystone/fernet-keys/ -R [root@controller03 ~]# chown keystone:keystone /etc/keystone/credential-keys/ -R [root@controller03 ~]# chown keystone:keystone /etc/keystone/fernet-keys/ -R
# 在全部控制节点设置,以controller01节点为例; [root@controller01 ~]# cp /etc/httpd/conf/httpd.conf /etc/httpd/conf/httpd.conf.bak [root@controller01 ~]# sed -i "s/#ServerName www.example.com:80/ServerName ${HOSTNAME}/" /etc/httpd/conf/httpd.conf # 注意不同的节点替换不同的ip地址 [root@controller01 ~]# sed -i "s/Listen\ 80/Listen\ 172.30.200.31:80/g" /etc/httpd/conf/httpd.conf [root@controller02 ~]# sed -i "s/Listen\ 80/Listen\ 172.30.200.32:80/g" /etc/httpd/conf/httpd.conf [root@controller03 ~]# sed -i "s/Listen\ 80/Listen\ 172.30.200.33:80/g" /etc/httpd/conf/httpd.conf
# 在全部控制节点操作,以controller01节点为例; # 复制wsgi-keystone.conf文件; # 或者针对wsgi-keystone.conf创建软链接 [root@controller01 ~]# cp /usr/share/keystone/wsgi-keystone.conf /etc/httpd/conf.d/ # 修改wsgi-keystone.conf文件,注意各节点对应的ip地址或主机名等,以controller01节点为例 [root@controller01 ~]# sed -i "s/Listen\ 5000/Listen\ 172.30.200.31:5000/g" /etc/httpd/conf.d/wsgi-keystone.conf [root@controller01 ~]# sed -i "s/Listen\ 35357/Listen\ 172.30.200.31:35357/g" /etc/httpd/conf.d/wsgi-keystone.conf [root@controller01 ~]# sed -i "s/*:5000/172.30.200.31:5000/g" /etc/httpd/conf.d/wsgi-keystone.conf [root@controller01 ~]# sed -i "s/*:35357/172.30.200.31:35357/g" /etc/httpd/conf.d/wsgi-keystone.conf
# 任意控制节点操作; # 初始化admin用户(管理用户)与密码,3种api端点,服务实体可用区等 [root@controller01 ~]# keystone-manage bootstrap --bootstrap-password admin_pass \ --bootstrap-admin-url http://controller:35357/v3/ --bootstrap-internal-url http://controller:5000/v3/ --bootstrap-public-url http://controller:5000/v3/ --bootstrap-region-id RegionTest
# 在全部控制节点操作,以controller01节点为例 [root@controller01 ~]# systemctl enable httpd.service [root@controller01 ~]# systemctl restart httpd.service [root@controller01 ~]# systemctl status httpd.service
# projrct/user等基于domain存在; # 在”认证引导”章节中,初始化admin用户即生成”default” domain [root@controller01 ~]# openstack domain list
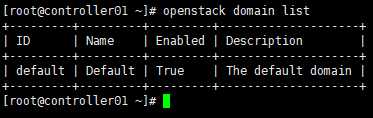
# 如果需要生成新的domain, [root@controller01 ~]# openstack domain create --description "An Example Domain" example [root@controller01 ~]# openstack domain list
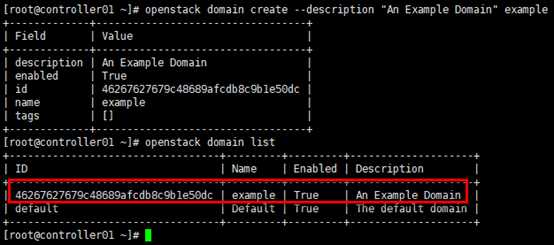
# project属于某个domain; # 以创建demo项目为例,demo项目属于”default” domain [root@controller01 ~]# openstack project create --domain default --description "Demo Project" demo
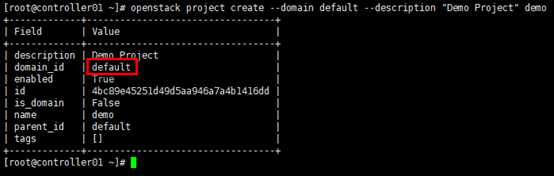
# user属于某个domain; # 以创建demo用户为例,demo用户属于”default” domain [root@controller01 ~]# openstack user create --domain default --password=demo_pass demo
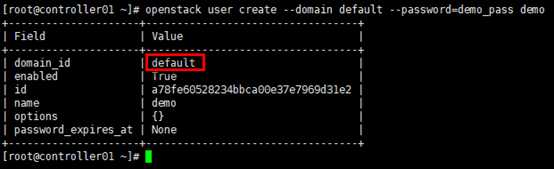
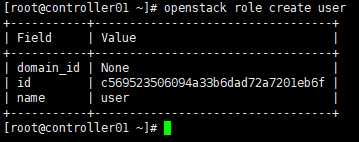
# 创建普通用户角色(区别于admin用户) [root@controller01 ~]# openstack role create user
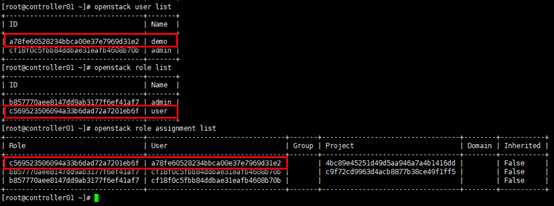
# 向demo项目的demo用户赋予user权限, [root@controller01 ~]# openstack role add --project demo --user demo user # 查看权限分配 [root@controller01 ~]# openstack user list [root@controller01 ~]# openstack role list [root@controller01 ~]# openstack role assignment list
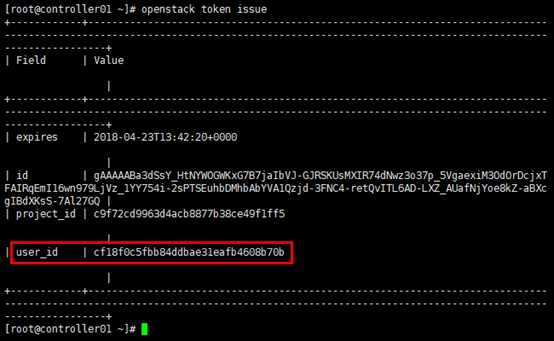
# openstack client环境脚本定义client调用openstack api环境变量,以方便api的调用(不必在命令行中携带环境变量); # 根据不同的用户角色,需要定义不同的脚本; # 这里以“认证引导”章节定义的admin用户为例,设置其环境脚本,再根据需要分发到需要运行openstack client工具的节点; # 一般将脚本创建在用户主目录 [root@controller01 ~]# touch admin-openrc [root@controller01 ~]# chmod u+x admin-openrc [root@controller01 ~]# vim admin-openrc export OS_PROJECT_DOMAIN_NAME=Default export OS_USER_DOMAIN_NAME=Default export OS_PROJECT_NAME=admin export OS_USERNAME=admin export OS_PASSWORD=admin_pass export OS_AUTH_URL=http://controller:5000/v3 # 从安全角度考虑,一般不对client暴露admin-api,这里admin-api与public-api共用1个vip地址 # export OS_AUTH_URL=http://controller:35357/v3 export OS_IDENTITY_API_VERSION=3 export OS_IMAGE_API_VERSION=2 # 验证 [root@controller01 ~]# openstack token issue
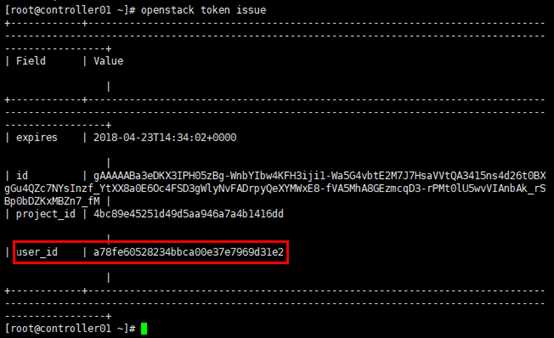
# 同admin-openrc,注意project/user/password的区别 [root@controller01 ~]# touch demo-openrc [root@controller01 ~]# chmod u+x demo-openrc [root@controller01 ~]# vim demo-openrc export OS_PROJECT_DOMAIN_NAME=Default export OS_USER_DOMAIN_NAME=Default export OS_PROJECT_NAME=demo export OS_USERNAME=demo export OS_PASSWORD=demo_pass export OS_AUTH_URL=http://controller:5000/v3 export OS_IDENTITY_API_VERSION=3 export OS_IMAGE_API_VERSION=2 # 验证 [root@controller01 ~]# openstack token issue
# 分发脚本 [root@controller01 ~]# scp admin-openrc demo-openrc root@172.30.200.32:~/ [root@controller01 ~]# scp admin-openrc demo-openrc root@172.30.200.33:~/
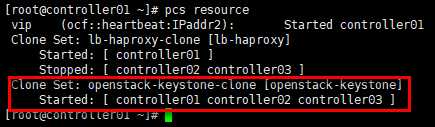
# 在任意控制节点操作; # 添加资源openstack-keystone-clone; # pcs实际控制的是各节点system unit控制的httpd服务 [root@controller01 ~]# pcs resource create openstack-keystone systemd:httpd --clone interleave=true [root@controller01 ~]# pcs resource
高可用OpenStack(Queen版)集群-4.keystone集群
标签:color 的区别 根据 user unifi sync art -- 文档
原文地址:https://www.cnblogs.com/netonline/p/9210520.html