标签:normal ott ESS top efi 方法 packet root next
连接先看报错:
There were 11 failed login attempts since the last successful login.
先前有上百上千失败login,被攻击了,把短时间尝试登录失败的ip加入黑名单
写个脚本:
#! /bin/bash
cat /var/log/secure|awk ‘/Failed/{print $(NF-3)}‘|sort|uniq -c|awk ‘{print $2"="$1;}‘ > /root/black.txt
DEFINE="10"
for i in `cat /root/black.txt`
do
IP=`echo | awk ‘{split("‘${i}‘", array, "=");print array[1]}‘`
NUM=`echo | awk ‘{split("‘${i}‘", array, "=");print array[2]}‘`
if [ $NUM -gt $DEFINE ];then
grep $IP /etc/hosts.deny > /dev/null
if [ $? -gt 0 ];then
echo "sshd:$IP:deny" >> /etc/hosts.deny
fi
fi
done
然后定时执行
crontab -e
*/1 * * * * sh /root/secure_ssh.sh
一分钟执行一次
攻击解决了,但是还是慢
把网上流行做法,都做了
systemcts status systemd-logind
因为确实有login超时
也顺便
systemctl restart dbus
了一下,没用
费力气安装stract,用它来查看栈信息
strace -o ~/starce_ssh.txt -T ssh localhost
tail -f ~/starce_ssh.txt
但是看不懂。。。。。。
下面的肯定先做了
vim /etc/ssh/sshd_config
做
UseDNS no
#service sshd restart
修改GSSAPIAuthentication参数为 no,默认是yes
#service sshd restart
显然是没用,采用上上面的方法
也调试日志了
ssh -vvv root@*.*.*.*
输入密码后,在这里等待
debug1: Next authentication method: password root@118.89.234.31‘s password: debug3: packet_send2: adding 48 (len 65 padlen 15 extra_pad 64) debug2: we sent a password packet, wait for reply debug3: Wrote 148 bytes for a total of 1393 debug1: Authentication succeeded (password). debug1: channel 0: new [client-session] debug3: ssh_session2_open: channel_new: 0 debug2: channel 0: send open debug1: Requesting no-more-sessions@openssh.com debug1: Entering interactive session. debug3: Wrote 136 bytes for a total of 1529
很久以后
debug1: Entering interactive session. debug3: Wrote 136 bytes for a total of 1529 debug1: client_input_global_request: rtype hostkeys-00@openssh.com want_reply 0 debug2: callback start debug2: client_session2_setup: id 0 debug2: channel 0: request pty-req confirm 1 debug2: channel 0: request shell confirm 1 debug2: fd 3 setting TCP_NODELAY debug2: callback done debug2: channel 0: open confirm rwindow 0 rmax 32768 debug3: Wrote 376 bytes for a total of 1905 debug2: channel_input_status_confirm: type 99 id 0 debug2: PTY allocation request accepted on channel 0 debug2: channel 0: rcvd adjust 2097152 debug2: channel_input_status_confirm: type 99 id 0 debug2: shell request accepted on channel 0 Last failed login: Thu Jun 28 19:16:02 CST 2018 from 112.85.42.201 on ssh:notty There were 396 failed login attempts since the last successful login. Last login: Thu Jun 28 18:52:28 2018 from 124.204.55.194 [root@VM_128_5_centos ~]#
分析了很久很多停顿时候以及前后的打印信息,对比
这些客户端信息正常
查看服务器日志:
tail -f /var/log/messages
登录时认证很快,并创建session
Jun 28 19:22:35 localhost systemd: Started Session 134942 of user root. Jun 28 19:22:35 localhost systemd-logind: New session 134942 of user root. Jun 28 19:22:35 localhost systemd: Starting Session 134942 of user root.
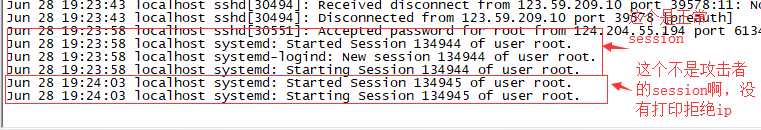
详细日志
Jun 28 19:23:58 localhost sshd[30551]: Accepted password for root from 124.204.55.194 port 61347 ssh2 Jun 28 19:23:58 localhost systemd: Started Session 134944 of user root. Jun 28 19:23:58 localhost systemd-logind: New session 134944 of user root. Jun 28 19:23:58 localhost systemd: Starting Session 134944 of user root. Jun 28 19:24:03 localhost systemd: Started Session 134945 of user root. Jun 28 19:24:03 localhost systemd: Starting Session 134945 of user root. Jun 28 19:25:01 localhost systemd: Started Session 134946 of user root. Jun 28 19:25:02 localhost systemd: Starting Session 134946 of user root. Jun 28 19:26:01 localhost systemd: Started Session 134947 of user root. Jun 28 19:26:01 localhost systemd: Starting Session 134947 of user root. Jun 28 19:27:01 localhost sshd[30887]: Failed password for root from 123.59.209.10 port 38628 ssh2 Jun 28 19:27:01 localhost systemd: Started Session 134948 of user root. Jun 28 19:27:01 localhost systemd: Starting Session 134948 of user root. Jun 28 19:27:02 localhost sshd[30887]: Received disconnect from 123.59.209.10 port 38628:11: Normal Shutdown, Thank you for playing [preauth] Jun 28 19:27:02 localhost sshd[30887]: Disconnected from 123.59.209.10 port 38628 [preauth] Jun 28 19:28:01 localhost systemd: Started Session 134949 of user root. Jun 28 19:28:01 localhost systemd: Starting Session 134949 of user root.
前面并没有这么多凭空的session产生,现在为什么这么多?
线索:https://www.depesz.com/2010/12/13/a-tale-of-slow-ssh-connections/
https://major.io/2015/07/27/very-slow-ssh-logins-on-fedora-22/
https://serverfault.com/questions/707377/slow-ssh-login-activation-of-org-freedesktop-login1-timed-out#
https://bugs.debian.org/cgi-bin/bugreport.cgi?bug=793814
标签:normal ott ESS top efi 方法 packet root next
原文地址:https://www.cnblogs.com/liugh-wait/p/9240340.html