标签:and window number exec png fse symbol 技术分享 glob
直接上图了
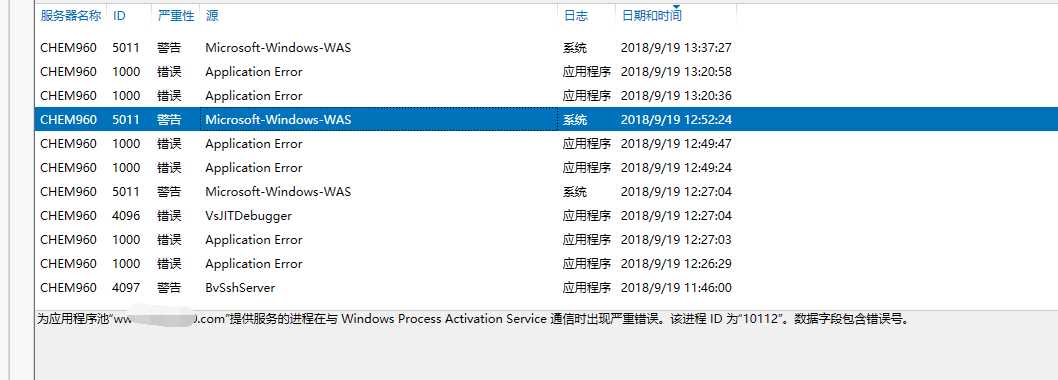
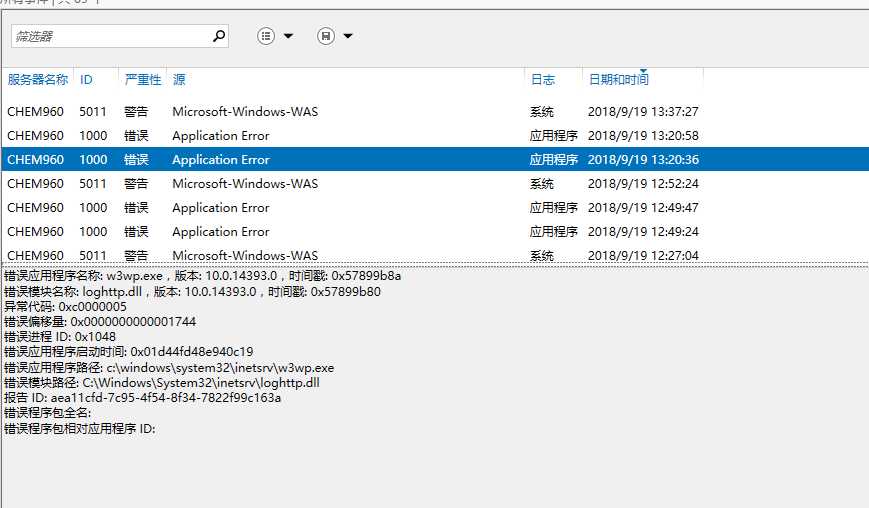
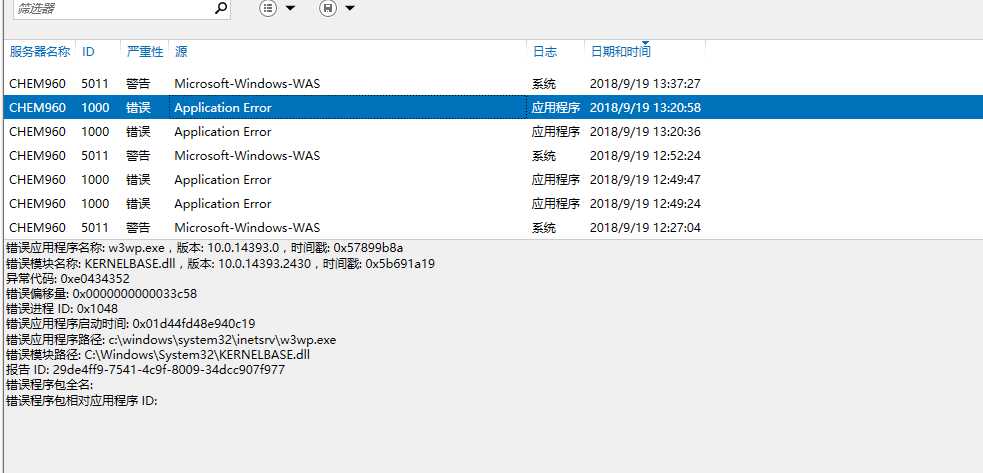
上图三个错误最近频繁出现,出现一次iis就奔溃一次,抓取的dump分析后如下:
Couldn‘t resolve error at ‘ls‘ 0:100> !analyze -v ******************************************************************************* * * * Exception Analysis * * * ******************************************************************************* GetUrlPageData2 (WinHttp) failed: 12002. DUMP_CLASS: 2 DUMP_QUALIFIER: 400 CONTEXT: (.ecxr) rax=736f686c61636f6c rbx=000001ac72f5c580 rcx=000001ac72f5c580 rdx=736f686c61636f6c rsi=0000000000000000 rdi=0000000020000000 rip=00007ffd0e0d1744 rsp=0000005a9667d6a0 rbp=000001ac72f5c580 r8=000001ac72f5c580 r9=000001ac6666cd50 r10=00000fffa0b9f15a r11=5555555515555555 r12=000001a7513e5ab0 r13=000001ac72f5c580 r14=0000000000000000 r15=000001ac6666cd50 iopl=0 nv up ei pl zr na po cy cs=0033 ss=002b ds=002b es=002b fs=0053 gs=002b efl=00010247 loghttp!RequestDoWork+0x84: 00007ffd`0e0d1744 488b08 mov rcx,qword ptr [rax] ds:736f686c`61636f6c=???????????????? Resetting default scope FAULTING_IP: loghttp!RequestDoWork+84 00007ffd`0e0d1744 488b08 mov rcx,qword ptr [rax] EXCEPTION_RECORD: (.exr -1) ExceptionAddress: 00007ffd0e0d1744 (loghttp!RequestDoWork+0x0000000000000084) ExceptionCode: c0000005 (Access violation) ExceptionFlags: 00000000 NumberParameters: 2 Parameter[0]: 0000000000000000 Parameter[1]: ffffffffffffffff Attempt to read from address ffffffffffffffff PROCESS_NAME: w3wp.exe ERROR_CODE: (NTSTATUS) 0xc0000005 - <Unable to get error code text> EXCEPTION_CODE: (NTSTATUS) 0xc0000005 - <Unable to get error code text> EXCEPTION_CODE_STR: c0000005 EXCEPTION_PARAMETER1: 0000000000000000 EXCEPTION_PARAMETER2: ffffffffffffffff FOLLOWUP_IP: loghttp!RequestDoWork+84 00007ffd`0e0d1744 488b08 mov rcx,qword ptr [rax] READ_ADDRESS: ffffffffffffffff WATSON_BKT_PROCSTAMP: 57899b8a WATSON_BKT_PROCVER: 10.0.14393.0 PROCESS_VER_PRODUCT: Internet Information Services WATSON_BKT_MODULE: loghttp.dll WATSON_BKT_MODSTAMP: 57899b80 WATSON_BKT_MODOFFSET: 1744 WATSON_BKT_MODVER: 10.0.14393.0 MODULE_VER_PRODUCT: Internet Information Services BUILD_VERSION_STRING: 10.0.14393.2214 (rs1_release_1.180402-1758) MODLIST_WITH_TSCHKSUM_HASH: a0ec544a1ec8d5dfa0a915fcd0de4fe39c075455 MODLIST_SHA1_HASH: 8789da5e655c37daf1ea0c1b0559023ff06eb1fc NTGLOBALFLAG: 0 PROCESS_BAM_CURRENT_THROTTLED: 0 PROCESS_BAM_PREVIOUS_THROTTLED: 0 APPLICATION_VERIFIER_FLAGS: 0 PRODUCT_TYPE: 3 SUITE_MASK: 400 DUMP_FLAGS: 8000c07 DUMP_TYPE: 3 MISSING_CLR_SYMBOL: 0 ANALYSIS_SESSION_HOST: DESKTOP-UO1I8RL ANALYSIS_SESSION_TIME: 09-19-2018 13:47:13.0800 ANALYSIS_VERSION: 10.0.15063.468 amd64fre MANAGED_CODE: 1 MANAGED_ENGINE_MODULE: clr MANAGED_ANALYSIS_PROVIDER: SOS MANAGED_THREAD_ID: f94 THREAD_ATTRIBUTES: ADDITIONAL_DEBUG_TEXT: SOS.DLL is not loaded for managed code. Analysis might be incomplete OS_LOCALE: CHS PROBLEM_CLASSES: ID: [0n292] Type: [@ACCESS_VIOLATION] Class: Addendum Scope: BUCKET_ID Name: Omit Data: Omit PID: [Unspecified] TID: [0xf94] Frame: [0] : loghttp!RequestDoWork ID: [0n264] Type: [INVALID_POINTER_READ] Class: Primary Scope: DEFAULT_BUCKET_ID (Failure Bucket ID prefix) BUCKET_ID Name: Add Data: Omit PID: [Unspecified] TID: [0xf94] Frame: [0] : loghttp!RequestDoWork ID: [0n234] Type: [NOSOS] Class: Addendum Scope: DEFAULT_BUCKET_ID (Failure Bucket ID prefix) BUCKET_ID Name: Add Data: Omit PID: [Unspecified] TID: [Unspecified] Frame: [0] BUGCHECK_STR: APPLICATION_FAULT_INVALID_POINTER_READ_NOSOS DEFAULT_BUCKET_ID: INVALID_POINTER_READ_NOSOS PRIMARY_PROBLEM_CLASS: APPLICATION_FAULT LAST_CONTROL_TRANSFER: from 00007ffd0e0d16ad to 00007ffd0e0d1744 STACK_TEXT: 0000005a`9667d6a0 00007ffd`0e0d16ad : 000001ac`72f5c580 00000000`00000001 00000000`00000000 00000000`00000000 : loghttp!RequestDoWork+0x84 0000005a`9667d8a0 00007ffd`05ced3d9 : 00000000`00000000 00000000`00000000 000001ac`72f5c580 000001ac`6666ccc8 : loghttp!CIISHttpModule::OnSendResponse+0x1d 0000005a`9667d8e0 00007ffd`05cecd7c : 000001ac`6666ccc8 0000005a`9667d9f1 00000000`00000001 000001ac`6666cd50 : iiscore!NOTIFICATION_CONTEXT::RequestDoWork+0xb9 0000005a`9667d930 00007ffd`05cecbc6 : 000001a7`51ac36b0 00000000`00000000 000001ac`6666ccc8 00000000`00000000 : iiscore!NOTIFICATION_CONTEXT::CallModulesInternal+0x19c 0000005a`9667da40 00007ffd`05cf1147 : 0000005a`9667dac0 00000100`00000000 000001ac`72f5c580 00007ffc`c2fbaef6 : iiscore!NOTIFICATION_CONTEXT::CallModules+0x36 0000005a`9667daa0 00007ffd`05cefd4c : 00000000`00000000 00007ffd`05cf15e0 00000000`80004005 00000000`00000000 : iiscore!NOTIFICATION_SEND_RESPONSE::DoWork+0x87 0000005a`9667db20 00007ffd`05cedca2 : 000001aa`00000000 00000000`00000001 00000000`00000000 000001ac`72f5c580 : iiscore!W3_RESPONSE::Flush+0x39c 0000005a`9667dbb0 00007ffd`05ce7956 : 00007ffd`05ce7880 000001a9`9346f610 000001ac`6666bc08 000001a7`51ac36b0 : iiscore!NOTIFICATION_MAIN::DoWork+0x272 0000005a`9667ded0 00007ffd`1fcdfb01 : 000001ac`72f5c580 00007ffd`05ce7880 0000005a`9667e060 00007ffd`22574cd5 : iiscore!W3_CONTEXT_BASE::IndicateCompletion+0xd6 0000005a`9667df50 00007ffd`1fce25e2 : 0000005a`9667e1b0 0000005a`9667e1b0 0000005a`9667e178 00007ffc`c5413be5 : webengine4!W3_MGD_HANDLER::IndicateCompletion+0x5d 0000005a`9667df80 00007ffc`c542240e : 000001a9`9346e970 0000005a`9667e050 0000005a`9667dfa0 00006dc0`f7918fa1 : webengine4!MgdIndicateCompletion+0x22 0000005a`9667dfb0 00007ffc`c5411a14 : 000001aa`1208fc40 000001a9`9346e698 0000005a`9667e180 0000005a`9667e138 : 0x00007ffc`c542240e 0000005a`9667e070 00007ffc`c54107f3 : ffffffff`fffffffe 000001ac`6666b7f0 ffffffff`fffffffe 00000000`00000000 : 0x00007ffc`c5411a14 0000005a`9667e210 00007ffc`c540f5e2 : 00000000`00000000 000001ac`66364ee0 ffffffff`fffffffe 0000005a`00000000 : 0x00007ffc`c54107f3 0000005a`9667e250 00007ffd`22572473 : ffffffff`ffffffff 00007ffd`00000001 000001a7`51949801 00007ffd`2257a528 : 0x00007ffc`c540f5e2 0000005a`9667e2c0 00007ffd`2263cfba : 00460054`0045004e 00007ffd`22575b35 ffffffff`fffffffe 00007ffd`2257a270 : clr!UM2MThunk_WrapperHelper+0x43 0000005a`9667e300 00007ffd`2257a9c8 : 0000005a`9667e428 00000000`00000000 000001ac`66364ee0 00007ffd`225766af : clr!UM2MThunk_Wrapper+0x60 0000005a`9667e350 00007ffd`2263d065 : 0000005a`9667e501 0000005a`00000002 0000373d`d1759c7a 0000005a`9667e560 : clr!Thread::DoADCallBack+0x13d 0000005a`9667e510 00007ffd`2257241d : 000001ac`6007b8a0 ffffffff`ffffffff 00000000`00000002 00000000`00000000 : clr!UM2MDoADCallBack+0xb3 0000005a`9667e590 00007ffd`1fc8184f : 000001a7`51f618c0 000001ac`6666b7f0 00000000`00000002 00000000`00000000 : clr!UMThunkStub+0x26d 0000005a`9667e620 00007ffd`1fc817a2 : 0000005a`00000000 000001ac`6666b7f0 00007ffd`22eb4410 0000005a`9667e800 : webengine4!W3_MGD_HANDLER::ProcessNotification+0x8e 0000005a`9667e650 00007ffd`225799e7 : 000001ac`6666b7f0 00007ffd`1fc81760 00007ffd`22eb4410 00000000`00000000 : webengine4!ProcessNotificationCallback+0x42 0000005a`9667e680 00007ffd`2257819c : 00007ffd`22579a70 0000005a`9667e700 0000005a`9667e801 00000000`0b089504 : clr!UnManagedPerAppDomainTPCount::DispatchWorkItem+0x1bc 0000005a`9667e720 00007ffd`22577f45 : 0007000e`00260026 00000000`00000001 000001ac`66364ee0 000001ac`66364ee0 : clr!ThreadpoolMgr::ExecuteWorkRequest+0x64 0000005a`9667e750 00007ffd`22622e8f : 00000000`00000000 000001a7`50c10e01 00000000`00000001 00000000`00000804 : clr!ThreadpoolMgr::WorkerThreadStart+0xf5 0000005a`9667e7f0 00007ffd`2fdb8364 : 00000000`00000000 00000000`00000000 00000000`00000000 00000000`00000000 : clr!Thread::intermediateThreadProc+0x86 0000005a`9667f7b0 00007ffd`31ede851 : 00000000`00000000 00000000`00000000 00000000`00000000 00000000`00000000 : kernel32!BaseThreadInitThunk+0x14 0000005a`9667f7e0 00000000`00000000 : 00000000`00000000 00000000`00000000 00000000`00000000 00000000`00000000 : ntdll!RtlUserThreadStart+0x21 THREAD_SHA1_HASH_MOD_FUNC: 48176150c99086579b8115dc211b995cc4b07226 THREAD_SHA1_HASH_MOD_FUNC_OFFSET: 1d00c3832e4d0c79a48c8f97b4ed56fa80edffda THREAD_SHA1_HASH_MOD: 5921a8f24cf922df9ee28e5c41febefcb341d312 FAULT_INSTR_CODE: 48088b48 SYMBOL_STACK_INDEX: 0 SYMBOL_NAME: loghttp!RequestDoWork+84 FOLLOWUP_NAME: MachineOwner MODULE_NAME: loghttp IMAGE_NAME: loghttp.dll DEBUG_FLR_IMAGE_TIMESTAMP: 57899b80 STACK_COMMAND: .ecxr ; kb FAILURE_BUCKET_ID: INVALID_POINTER_READ_NOSOS_c0000005_loghttp.dll!RequestDoWork BUCKET_ID: APPLICATION_FAULT_INVALID_POINTER_READ_NOSOS_loghttp!RequestDoWork+84 FAILURE_EXCEPTION_CODE: c0000005 FAILURE_IMAGE_NAME: loghttp.dll BUCKET_ID_IMAGE_STR: loghttp.dll FAILURE_MODULE_NAME: loghttp BUCKET_ID_MODULE_STR: loghttp FAILURE_FUNCTION_NAME: RequestDoWork BUCKET_ID_FUNCTION_STR: RequestDoWork BUCKET_ID_OFFSET: 84 BUCKET_ID_MODTIMEDATESTAMP: 57899b80 BUCKET_ID_MODCHECKSUM: 134fa BUCKET_ID_MODVER_STR: 10.0.14393.0 BUCKET_ID_PREFIX_STR: APPLICATION_FAULT_INVALID_POINTER_READ_NOSOS_ FAILURE_PROBLEM_CLASS: APPLICATION_FAULT FAILURE_SYMBOL_NAME: loghttp.dll!RequestDoWork WATSON_STAGEONE_URL: http://watson.microsoft.com/StageOne/w3wp.exe/10.0.14393.0/57899b8a/loghttp.dll/10.0.14393.0/57899b80/c0000005/00001744.htm?Retriage=1 TARGET_TIME: 2018-09-19T04:26:43.000Z OSBUILD: 14393 OSSERVICEPACK: 2214 SERVICEPACK_NUMBER: 0 OS_REVISION: 0 OSPLATFORM_TYPE: x64 OSNAME: Windows 10 OSEDITION: Windows 10 Server TerminalServer DataCenter SingleUserTS USER_LCID: 0 OSBUILD_TIMESTAMP: 2018-04-03 11:45:42 BUILDDATESTAMP_STR: 180402-1758 BUILDLAB_STR: rs1_release_1 BUILDOSVER_STR: 10.0.14393.2214 ANALYSIS_SESSION_ELAPSED_TIME: 61eb ANALYSIS_SOURCE: UM FAILURE_ID_HASH_STRING: um:invalid_pointer_read_nosos_c0000005_loghttp.dll!requestdowork FAILURE_ID_HASH: {7fc5e7af-2508-9c33-c2b7-8a9e10458ef1} Followup: MachineOwner ---------
跪求大神分析此次iis频繁奔溃的原因。
标签:and window number exec png fse symbol 技术分享 glob
原文地址:https://www.cnblogs.com/drzhong/p/9674225.html