标签:++ 自定义 公司 监控脚本 目录 zabbix安装 修改 .sh 添加
1. 修改zabbix_agent配置文件添加以下内容,重启agent
Include=/etc/zabbix/zabbix_agentd.d/
2. 在zabbix安装目录下的scripts目录下添加一下脚本
cat lvs_discovery_ActConn.sh ----监控lvs上的80端口连接数
#!/bin/bash
#filename: lvs_discovery.sh
#author:
#MY_KEY=(` sudo /sbin/ipvsadm -L -n |egrep -v ‘TCP|UDP|Virtual|LocalAddress|ActiveConn‘ | grep 443 |grep "$1"|awk ‘{print $2}‘|awk -F ":" ‘{print $1}‘`)
MY_KEY=(` sudo /sbin/ipvsadm -L -n |egrep -v ‘TCP|UDP|Virtual|LocalAddress|ActiveConn‘ | grep "$1"|awk ‘{print $2}‘|awk -F"[ ]" ‘NR<4{print $1}‘`)
#MY_KEY=(`sudo /sbin/ipvsadm -L -n |egrep -v ‘TCP|UDP|Virtual|LocalAddress|ActiveConn‘ | grep "$1"|awk ‘{print $2}‘|awk ‘{print $1}‘ | sed -e ‘s/80/http/g‘ -e ‘s/443/https/g‘)
length=${#MY_KEY[@]}
printf "{\n"
printf ‘\t‘"\"data\":["
for ((i=0;i<$length;i++))
do
printf ‘\n\t\t{‘
printf "\"{#IFNAME}\":\"${MY_KEY[$i]}\"}"
if [ $i -lt $[$length-1] ];then
printf ‘,‘
fi
done
printf "]}\n"
3. 在zabbix.agentd.d下面新建配置文件
cat ../zabbix_agentd.d/lvs_ActConn.conf
# monitor lvs status
UserParameter=lvs.status.discovery,/etc/zabbix/scripts/lvs_discovery_ActConn.sh -----lvs.status.discovery为自动发现的key值
#UserParameter=lvs.status[*],sudo /sbin/ipvsadm -L -n | egrep -v ‘TCP|UDP|Virtual|LocalAddress|ActiveConn‘ | grep "$1" | awk ‘$$5 > 0 {print $$5}‘ ----grep "$1"为位置变量
UserParameter=lvs.status[*],sudo /sbin/ipvsadm -L -n | egrep -v ‘TCP|UDP|Virtual|LocalAddress|ActiveConn‘ | grep "$1" | awk ‘{print $$5}‘ ----lvs.status[*],*为lvs_discovery_ActConn.sh脚本传过来的参数
4. 监控lvs443端口的连接数
#!/bin/bash
#filename: lvs_discovery.sh
#author:
#MY_KEY=(` sudo /sbin/ipvsadm -L -n |egrep -v ‘TCP|UDP|Virtual|LocalAddress|ActiveConn‘ | grep 443 |grep "$1"|awk ‘{print $2}‘|awk -F ":" ‘{print $1}‘`)
MY_KEY=(` sudo /sbin/ipvsadm -L -n |egrep -v ‘TCP|UDP|Virtual|LocalAddress|ActiveConn‘ | grep "$1"|awk ‘{print $2}‘|awk -F"[ ]" ‘NR>3{print $1}‘`)
#MY_KEY=(`sudo /sbin/ipvsadm -L -n |egrep -v ‘TCP|UDP|Virtual|LocalAddress|ActiveConn‘ | grep "$1"|awk ‘{print $2}‘|awk ‘{print $1}‘ | sed -e ‘s/80/http/g‘ -e ‘s/443/https/g‘)
length=${#MY_KEY[@]}
printf "{\n"
printf ‘\t‘"\"data\":["
for ((i=0;i<$length;i++))
do
printf ‘\n\t\t{‘
printf "\"{#IFNAME}\":\"${MY_KEY[$i]}\"}"
if [ $i -lt $[$length-1] ];then
printf ‘,‘
fi
done
printf "]}\n"
5. 新建监控lvs443端口连接数配置文件
cat ../zabbix_agentd.d/lvs_ActConnPort443.conf
# monitor lvs status
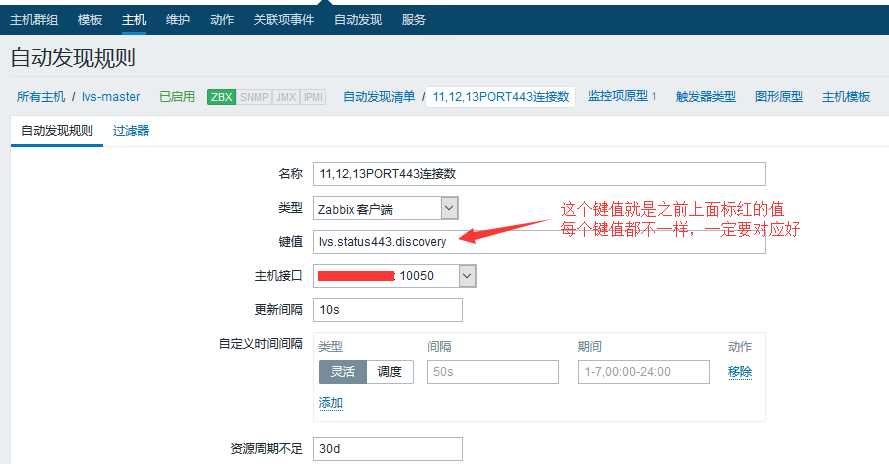
UserParameter=lvs.status443.discovery,/etc/zabbix/scripts/lvs_discovery_ActConnPort443.sh
#UserParameter=lvs.status[*],sudo /sbin/ipvsadm -L -n | egrep -v ‘TCP|UDP|Virtual|LocalAddress|ActiveConn‘ | grep "$1" | awk ‘$$5 > 0 {print $$5}‘
UserParameter=lvs.status443[*],sudo /sbin/ipvsadm -L -n | egrep -v ‘TCP|UDP|Virtual|LocalAddress|ActiveConn‘ | grep "$1" | awk ‘{print $$5}‘
6. 新建监控lvs443端口流量和包
cat lvs_discovery_ActConn80.sh
#!/bin/bash
#filename: lvs_discovery.sh
#author:
#MY_KEY=(` sudo /sbin/ipvsadm -L -n |egrep -v ‘TCP|UDP|Virtual|LocalAddress|ActiveConn‘ | grep 443 |grep "$1"|awk ‘{print $2}‘|awk -F ":" ‘{print $1}‘`)
#MY_KEY=(` sudo /sbin/ipvsadm -L -n |egrep -v ‘TCP|UDP|Virtual|LocalAddress|ActiveConn‘ | grep "$1"|awk ‘{print $2}‘|awk -F"[ ]" ‘NR<4{print $1}‘`)
MY_KEY=(`sudo /sbin/ipvsadm -L -n |egrep -v ‘TCP|UDP|Virtual|LocalAddress|ActiveConn‘ | grep "$1"|awk ‘{print $2}‘|awk ‘NR<4{print $1}‘`)
length=${#MY_KEY[@]}
printf "{\n"
printf ‘\t‘"\"data\":["
for ((i=0;i<$length;i++))
do
printf ‘\n\t\t{‘
printf "\"{#IFNAME}\":\"${MY_KEY[$i]}\"}"
if [ $i -lt $[$length-1] ];then
printf ‘,‘
fi
done
printf "]}\n"
7. 新建监控lvs80端口的流量配置文件
cat lvs_ActConn443.conf
# monitor lvs status
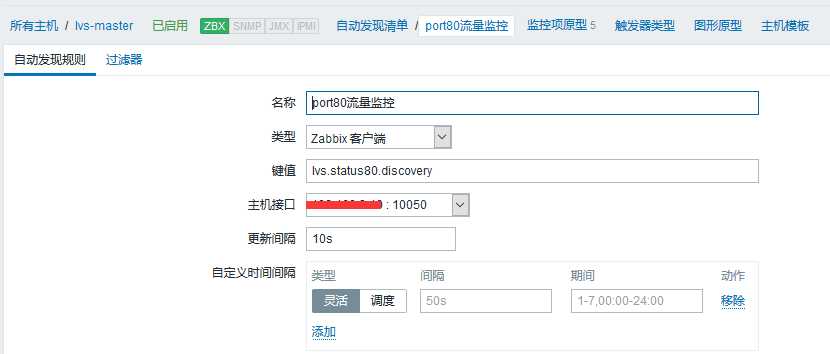
UserParameter=lvs.status80.discovery,/etc/zabbix/scripts/lvs_discovery_ActConn80.sh
#UserParameter=lvs.status[*],sudo /sbin/ipvsadm -L -n | egrep -v ‘TCP|UDP|Virtual|LocalAddress|ActiveConn‘ | grep "$1" | awk ‘$$5 > 0 {print $$5}‘
#UserParameter=lvs.status[*],sudo /sbin/ipvsadm -L -n | egrep -v ‘TCP|UDP|Virtual|LocalAddress|ActiveConn‘ | grep "$1" | awk ‘{print $$5}‘
UserParameter=lvs.CPS80[*],sudo /sbin/ipvsadm -L --rate | egrep -v ‘IP|Port|TCP‘ | sed ‘1,3s/http/80/g‘| grep "$1" |awk ‘{print $$3}‘
UserParameter=lvs.InPPS80[*],sudo /sbin/ipvsadm -L --rate | egrep -v ‘IP|Port|TCP‘ | sed ‘1,3s/http/80/g‘ | grep "$1"| awk ‘{print $$4}‘
UserParameter=lvs.OutPPS80[*],sudo /sbin/ipvsadm -L --rate | egrep -v ‘IP|Port|TCP‘ | sed ‘1,3s/http/80/g‘| grep "$1" | awk ‘{print $$5}‘
UserParameter=lvs.InByte80[*],sudo /sbin/ipvsadm -L --rate | egrep -v ‘IP|Port|TCP‘ | sed ‘1,3s/http/80/g‘| grep "$1" | awk ‘{print $$6}‘
#UserParameter=lvs.InByte[*],sudo /sbin/ipvsadm -L --rate | egrep -v ‘IP|Port|TCP‘ | grep "$1" |grep 443 | awk ‘{print $$6}‘
UserParameter=lvs.OutByte80[*],sudo /sbin/ipvsadm -L --rate | egrep -v ‘IP|Port|TCP‘| sed ‘1,3s/http/80/g‘ | grep "$1" | awk ‘{print $$7}‘
8. 新建监控lvs443端口流量
cat ../scripts/lvs_discovery_ActConnhttp.sh
#!/bin/bash
#filename: lvs_discovery.sh
#author:
#MY_KEY=(` sudo /sbin/ipvsadm -L -n |egrep -v ‘TCP|UDP|Virtual|LocalAddress|ActiveConn‘ | grep 443 |grep "$1"|awk ‘{print $2}‘|awk -F ":" ‘{print $1}‘`)
MY_KEY=(` sudo /sbin/ipvsadm -L -n |egrep -v ‘TCP|UDP|Virtual|LocalAddress|ActiveConn‘ | grep "$1"|awk ‘{print $2}‘|awk -F"[ ]" ‘NR>3{print $1}‘ | sed ‘s/443/https/g‘`)
#MY_KEY=(`sudo /sbin/ipvsadm -L -n |egrep -v ‘TCP|UDP|Virtual|LocalAddress|ActiveConn‘ | grep "$1"|awk ‘{print $2}‘|awk ‘{print $1}‘ | sed -e ‘s/80/http/g‘ -e ‘s/443/https/g‘)
length=${#MY_KEY[@]}
printf "{\n"
printf ‘\t‘"\"data\":["
for ((i=0;i<$length;i++))
do
printf ‘\n\t\t{‘
printf "\"{#IFNAME}\":\"${MY_KEY[$i]}\"}"
if [ $i -lt $[$length-1] ];then
printf ‘,‘
fi
done
printf "]}\n"
9. 新建监控lvs443端口流量配置文件
# monitor lvs status
UserParameter=lvs.stat.discovery,/etc/zabbix/scripts/lvs_discovery_ActConnhttp.sh
#UserParameter=lvs.status[*],sudo /sbin/ipvsadm -L -n | egrep -v ‘TCP|UDP|Virtual|LocalAddress|ActiveConn‘ | grep "$1" | awk ‘$$5 > 0 {print $$5}‘
#UserParameter=lvs.status[*],sudo /sbin/ipvsadm -L -n | egrep -v ‘TCP|UDP|Virtual|LocalAddress|ActiveConn‘ | grep "$1" | awk ‘{print $$5}‘
UserParameter=lvs.CPS[*],sudo /sbin/ipvsadm -L --rate | egrep -v ‘IP|Port|TCP‘ | grep "$1" |awk ‘{print $$3}‘
UserParameter=lvs.InPPS[*],sudo /sbin/ipvsadm -L --rate | egrep -v ‘IP|Port|TCP‘ | grep "$1" | awk ‘{print $$4}‘
UserParameter=lvs.OutPPS[*],sudo /sbin/ipvsadm -L --rate | egrep -v ‘IP|Port|TCP‘ | grep "$1" | awk ‘{print $$5}‘
UserParameter=lvs.InByte[*],sudo /sbin/ipvsadm -L --rate | egrep -v ‘IP|Port|TCP‘ | grep "$1" | awk ‘{print $$6}‘
#UserParameter=lvs.InByte[*],sudo /sbin/ipvsadm -L --rate | egrep -v ‘IP|Port|TCP‘ | grep "$1" |grep 443 | awk ‘{print $$6}‘
UserParameter=lvs.OutByte[*],sudo /sbin/ipvsadm -L --rate | egrep -v ‘IP|Port|TCP‘ | grep "$1" | awk ‘{print $$7}‘
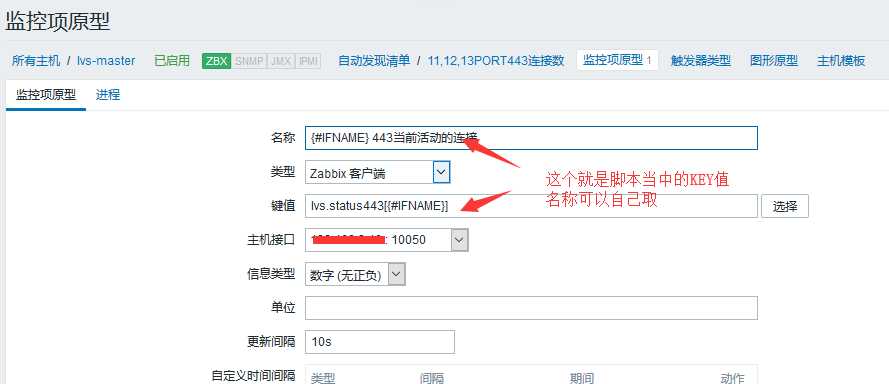
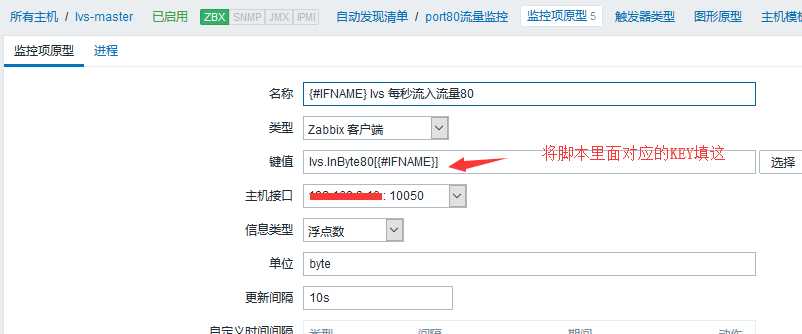
监控脚本和配置文件有点乱,还来不及作修改,只需要在配置文件里面第二行UserParameter=lvs.stat.discovery,/etc/zabbix/scripts/lvs_discovery_ActConnhttp.sh与脚本名对上就OK.另外加红的部分每个配置文件必须不一样,这个是自动发现的key值.
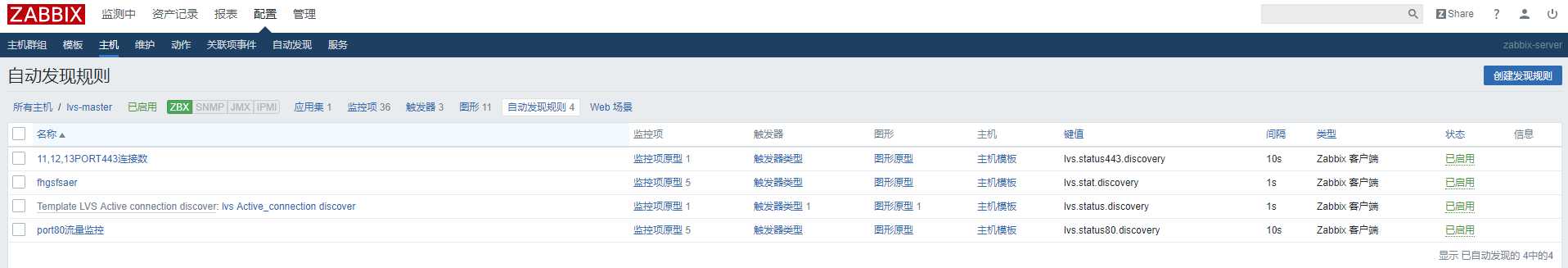
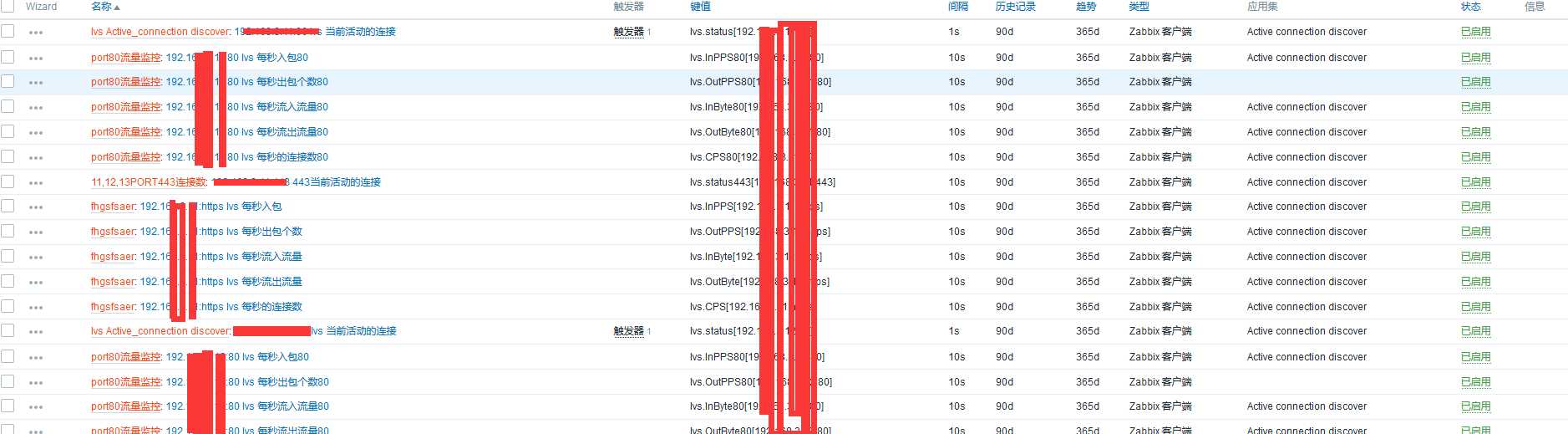
10. 开始配置自动发现规则和key值
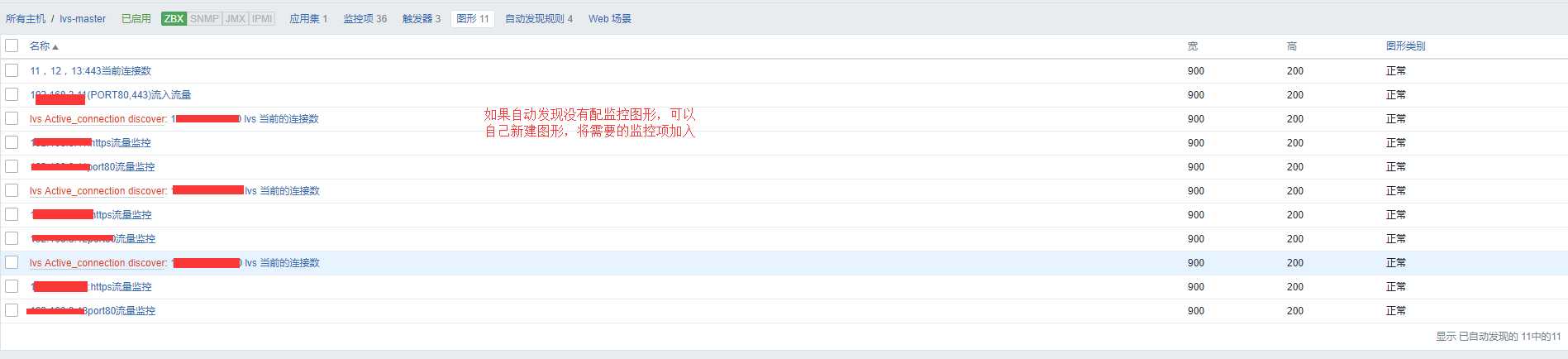
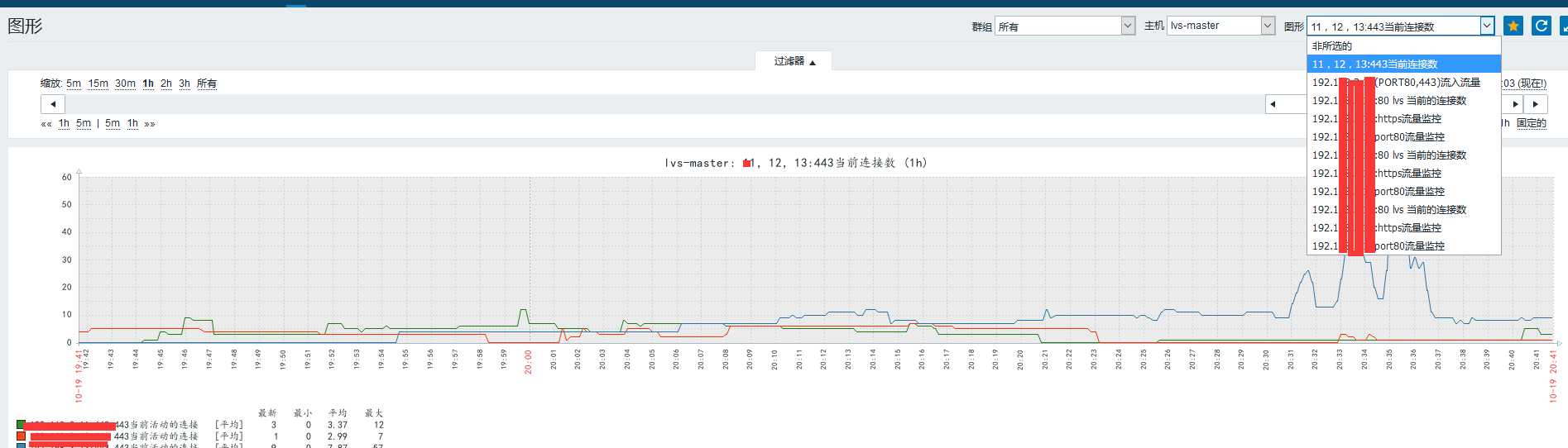
https://pan.baidu.com/s/1Sn7LVTdtjZHQvbyHjvNrqg 密码:302i这个模版还是有点问题的,不适合我们公司这种两个端口的Lvs,我在上面做了修改,以及自己加的图形。
先导入模版之后,创建主机,关联模版,进入主机,选择自动发现规则开始配置。


标签:++ 自定义 公司 监控脚本 目录 zabbix安装 修改 .sh 添加
原文地址:https://www.cnblogs.com/The-day-of-the-wind/p/9818683.html