标签:first link and 信息 with mobile cep get 验证
Detection of malicious base station attacks through the carrier analysis——伪基站,降维攻击
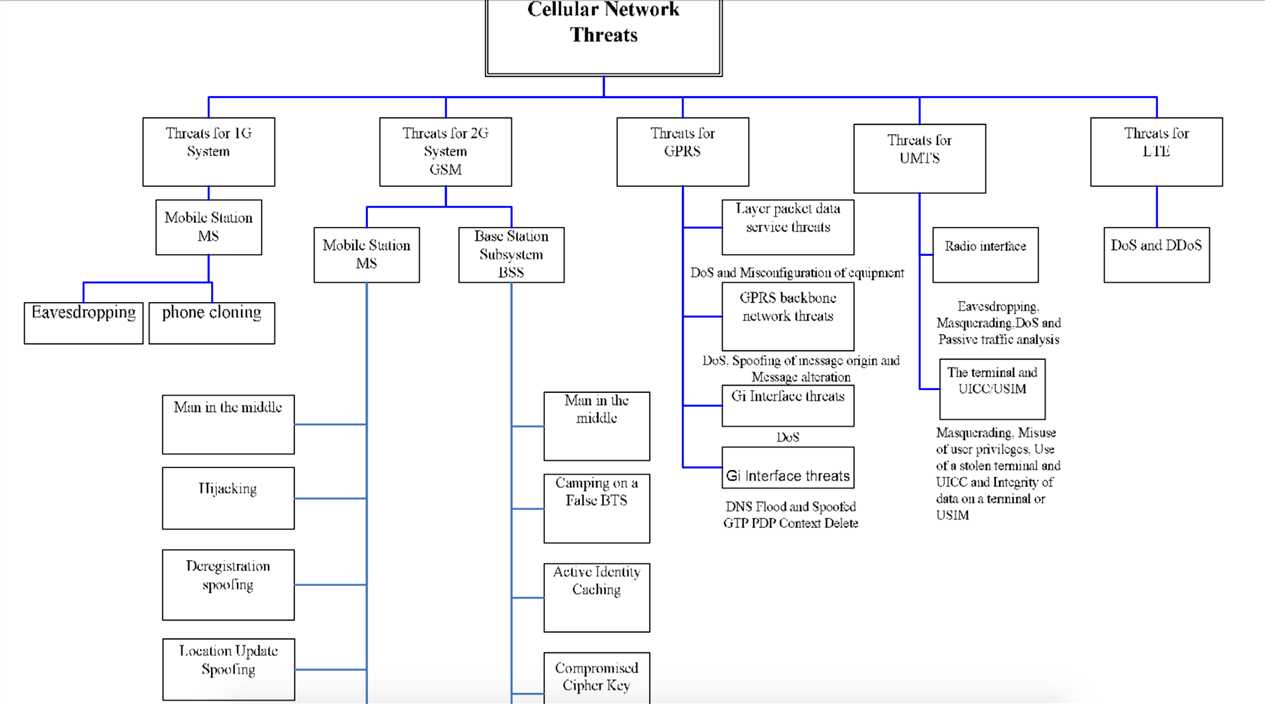
Cellular networks generations have suffered many threats such as eavesdropping and phone cloning, impersonation of a user, Man
in the middle, compromising authentication vectors in the network, spoofing, camping on a false
BTS, Denial of Service (DoS), passive identity caching, encryption suppression, suppressing
encryption between the target user and the intruder, eavesdropping on user data by suppressing
encryption, hijacking outgoing calls in networks with encryption disabled.
UMTS systems suffer from Eavesdropping signaling or control data, Masquerading as a user,
Masquerading as a serving network, jamming the user’s traffic and Denial of Service (DoS).
The common attacks in LTE are Distributed Denial of Service (DDoS) and Denial of Service (DoS)
attacks. Other threats are spam over VoIP, spoofing and misdirection, SIP registration hijacking and
interception and cryptanalysis of IP traffic.
2. SECURITY AND PRIVACY SERVICES
The most critical issue in cellular network is personal privacy requirements which would involve
security and privacy services. Due to the increasing number of m-business, security services will get
more critical in the future cellular system. Such services include entity authentication of the
principal entities, data confidentiality, data integrity, message origin and destination authentication,
anonymity, location confidentiality and identity confidentiality, untraceability, transaction
confidentiality and privacy.
Principal entities have identity structures to be authenticated. The main entities may have multiple
identities. Some of these identities may be public while others may be unknown. The identities may
be long lived or they may be short lived.
Data confidentiality protects the data against eavesdrop attack. Data integrity protects the data
against unlawful modification. Message origin and destination authentication provide corroboration
of the transmitter/receiver identities or more the associated routing addresses. These services are
provided by symmetric and asymmetric cryptographic methods.
The subscriber may not want to publish his/her identity. The subscriber identity that it may be the
system identity and international mobile subscriber identity (IMSI) is known for both the home
operator and the serving network. So it should be protected against eavesdropping on the radio
interface by any third party. The home operator is required to know the legal identity of the
subscriber.
Location confidentiality and identity confidentiality are provided by the existing systems but no
authoritative solution is yet provided for the current 2G/3G/4G systems. The issue is tied to identity
management to solve the problem of the mobile cellular and network identity management with
authentication at the link layer level.
The intruder may not able to derive the name or network address of the subscriber, but could
successfully trace the subscriber based on radio transmission properties. This arises the concepts of
untraceability and transaction confidentiality privacy.
3. THREATS/ INTRUDERS
Two main motivations for attackers are theft of service and interception of data. Theft of service
comes in many forms, but the most technically interesting is the cloning of a phone. When
“cloning” a phone, attackers steal the identifying information from a legitimate phonetic and load it
to another phone.
Data interception of mobile phone networks is a similar threat to other wireless networks. Using
relatively unsophisticated tools can listen to the transmissions of the phone and the base station in
an effort to eavesdrop on the voice and data transmissions occurring. The largest defense to this
type of attack is encryption of the data in the air.
An intruder may be attempted to eavesdrop on user traffic, signaling data and control data, or
disappear in many forms such as a legitimate party in the use and saving or management of cellular
network services.
The role of the intruders attempts to violate the confidentiality, integrity, availability of Cellular
network, their services or fraud users, home environments or serving networks or any other party.
蜂窝网络世代 1G 2G 3G。。。
遭受了许多威胁,如窃听和电话克隆,冒充用户,Man
在中间,妥协网络中的身份验证向量,欺骗,露营假
BTS,拒绝服务(DoS),被动身份缓存,加密抑制,抑制
目标用户和入侵者之间的加密,通过抑制来窃听用户数据
加密,在禁用加密的网络中劫持拨出呼叫。
UMTS系统遭受窃听信令或控制数据,伪装成用户,
伪装成服务网络,干扰用户的流量和拒绝服务(DoS)。
LTE中的常见攻击是分布式拒绝服务(DDoS)和拒绝服务(DoS)
攻击。其他威胁包括VoIP上的垃圾邮件,欺骗和误导,SIP注册劫持和
IP流量的拦截和密码分析。
蜂窝网络中最关键的问题是涉及的个人隐私要求
安全和隐私服务。由于移动商务的数量不断增加,安全服务将会得到
在未来的蜂窝系统中更为关键。这些服务包括实体认证
主体实体,数据机密性,数据完整性,消息来源和目的地认证,
匿名,位置保密和身份保密,无法追踪,交易
保密和隐私。
其中关于3G的威胁说到:
威胁安全的分类可以分为几类。以下部分
描述了威胁安全的分类。
未经授权访问敏感数据
窃听:入侵者拦截消息而不进行检测。伪装:入侵者
欺骗授权用户相信他们是获得机密的合法系统
来自用户的信息。流量分析:入侵者观察时间,速率,长度,来源和
消息的目的地以确定用户的位置。浏览:入侵者搜索数据存储
敏感信息。泄漏:入侵者通过利用获取敏感信息
合法访问数据的进程。推论:一个入侵者看到一个反应
系统通过向系统发送查询或信号。
未经授权操纵入侵者可能修改,插入,重放或删除的敏感数据
消息。
令人不安或误用网络的服务包括以下威胁:干预:入侵者可能
使用干扰用户的流量,信令或控制数据来阻止授权用户使用
服务。资源耗尽:入侵者可能会使用超载服务来阻止授权
用户使用服务。滥用权限:用户或服务网络想要获取
未经授权的服务或信息利用他们的特权。滥用服务:入侵者
可能会滥用某些特殊服务来获取优势或导致网络中断。
拒绝:用户或网络拒绝发生的行为。
未经授权的访问服务会暴露给入侵者,入侵者可以通过访问获得服务
伪装成用户或网络实体和用户或网络实体,可能会被未经授权
滥用访问权限访问服务。
空口侧的威胁包含:
无线电接口受到不同的攻击,例如:
窃听:入侵者窃听用户流量的用户流量。
窃听信令或控制数据,入侵者窃听信令数据或控制数据
用于访问安全管理数据或其他信息并将其传递给活动
攻击系统。
伪装成通信,参与者:入侵者伪装成网络元素
拦截用户流量,信令数据或控制。
被动流量分析,入侵者观察时间,速率,长度,来源或目的地
消息获得对信息的访问。
拒绝服务(DoS)攻击有几种类型,例如:
·物理干预:入侵者可能会阻止用户流量,信令数据和控制数据
通过物理手段在无线电接口上传输。
·协议干预:入侵者可能会阻止用户流量,信令数据或控制数据
通过诱导特定的协议故障在无线电接口上传输。
·伪装成通信的拒绝服务(DoS),参与者:入侵者可以
通过阻止用户流量,信令数据或控制数据来拒绝向合法用户提供服务
通过伪装成网络元素在无线电接口上传输。
4G的安全问题——核心还是Dos攻击
4GSystem(LTE)安全
现代LTE蜂窝网络为超过数十亿用户提供高级服务
传统语音和短消息流量。 即将到来的LTE攻击是分布式拒绝
服务(DDoS)攻击。 通信系统的可用性解释了重要性
增强移动网络抵御拒绝服务(DoS)和DDoS威胁的灵活性
确保LTE网络可用性免受安全攻击。
威胁的例子包括VoIP上的垃圾邮件,欺骗和误导,SIP注册劫持和
IP流量的拦截和密码分析。
文中一幅图说明很好:
标签:first link and 信息 with mobile cep get 验证
原文地址:https://www.cnblogs.com/bonelee/p/10075983.html