标签:blog http ar sp 数据 div 2014 on log
获取对话框数据并判断长度:
004011B5 |. 6A 14 push 0x14 ; /Count = 14 (20.) 004011B7 |. 51 push ecx ; |Buffer = 0018F8B8 004011B8 |. 66:894424 2D mov word ptr [esp+0x2D], ax ; | 004011BD |. 68 E8030000 push 0x3E8 ; |ControlID = 3E8 (1000.) 004011C2 |. 52 push edx ; |hWnd 004011C3 |. C64424 20 00 mov byte ptr [esp+0x20], 0x0 ; | 004011C8 |. 884424 37 mov byte ptr [esp+0x37], al ; | 004011CC |. 33ED xor ebp, ebp ; | 004011CE |. FF15 B8504000 call dword ptr [<&USER32.GetDlgItemTe>; \GetDlgItemTextA 004011D4 |. 8D7C24 10 lea edi, dword ptr [esp+0x10] ; 堆栈地址=0018F8B8, (ASCII "Crack_Qs") 004011D8 |. 83C9 FF or ecx, 0xFFFFFFFF 004011DB |. 33C0 xor eax, eax 004011DD |. F2:AE repne scas byte ptr es:[edi] ; 取Key长度 004011DF |. F7D1 not ecx 004011E1 |. 49 dec ecx 004011E2 |. 83F9 0D cmp ecx, 0xD ; 判断Key长度是否为13 004011E5 |. 0F85 F0000000 jnz 004012DB ; 如果不是13位直接跳到函数尾
接下来检测Key的内容是否有非数字存在:
004011ED |> /8A440C 10 /mov al, byte ptr [esp+ecx+0x10] 004011F1 |. |3C 30 |cmp al, 0x30 004011F3 |. |0F8C E2000000 |jl 004012DB 004011F9 |. |3C 39 |cmp al, 0x39 004011FB |. |0F8F DA000000 |jg 004012DB 00401201 |. |41 |inc ecx 00401202 |. |83F9 0D |cmp ecx, 0xD 00401205 |.^\7C E6 \jl short 004011ED
第一次校验Key:
00401207 |. 0FBE7C24 16 movsx edi, byte ptr [esp+0x16] ; KeyBuffer 起始地址[esp+0x10] 0040120C |. 0FBE4C24 10 movsx ecx, byte ptr [esp+0x10] 00401211 |. 0FBE5424 19 movsx edx, byte ptr [esp+0x19] 00401216 |. 8D4439 A0 lea eax, dword ptr [ecx+edi-0x60] ; Key[0]+Key[6]-0x60 (两数相加取int值) 0040121A |. 83EA 26 sub edx, 0x26 ; Key[9] - 0x30 + 0xA 0040121D |. 3BC2 cmp eax, edx ; 判断 Key[0](int) + Key[6](int) 是否等于 Key[9](int) + 0xA 0040121F |. 0F85 B6000000 jnz 004012DB
第二次校验Key:
00401225 |. 8A5C24 17 mov bl, byte ptr [esp+0x17] ; Key[7] 00401229 |. 8D41 D0 lea eax, dword ptr [ecx-0x30] ; Key[0](int) 0040122C |. 99 cdq 0040122D |. 0FBEF3 movsx esi, bl ; esi = Key[7] 00401230 |. 83E2 03 and edx, 0x3 00401233 |. 03C2 add eax, edx ; (0 & 0x3) + Key[0](int) 00401235 |. 8D56 D0 lea edx, dword ptr [esi-0x30] ; Key[7](int) 00401238 |. C1F8 02 sar eax, 0x2 ; ((0 & 0x30) + key[0](int) )>> 2 0040123B |. 3BC2 cmp eax, edx ; 判断 ((0 & 0x3) + Key[0](int)) >> 2 是否等于 Key[7](int) 0040123D |. 0F85 98000000 jnz 004012DB
第三次校验Key:
00401243 |. 385C24 14 cmp byte ptr [esp+0x14], bl ; 判断 Key[4](int)是否等于 Key[7](int) 00401247 |. 0F85 8E000000 jnz 004012DB
第四次校验Key:
0040124D |. 0FBE4424 11 movsx eax, byte ptr [esp+0x11] ; Key[1] 00401252 |. 8D1430 lea edx, dword ptr [eax+esi] ; Key[1]+Key[7] 00401255 |. 03D1 add edx, ecx ; Key[1]+Key[7]+Key[0] 00401257 |. 03D7 add edx, edi ; Key[1]+Key[7]+Key[0]+Key[6] 00401259 |. 81FA D4000000 cmp edx, 0xD4 ; 判断 Key[1]+Key[7]+Key[0]+Key[6] 是否等于 0xd4 0040125F |. 75 7A jnz short 004012DB
第五次校验Key:
00401261 |. 0FBE5424 12 movsx edx, byte ptr [esp+0x12] ; key[2] 00401266 |. 0FBE7424 15 movsx esi, byte ptr [esp+0x15] ; key[5] 0040126B |. 03F2 add esi, edx ; key[2]+key[5] 0040126D |. 03C1 add eax, ecx ; Key[0]+Key[1] 0040126F |. 3BC6 cmp eax, esi ; 判断 Key[0]+Key[1] 是否等于 key[2]+key[5] 00401271 |. 75 68 jnz short 004012DB
第六次校验Key:
00401273 |. 0FBE4424 13 movsx eax, byte ptr [esp+0x13] ; key[3] 00401278 |. 42 inc edx ; key[2]+1 00401279 |. 3BD0 cmp edx, eax ; 判断key[2]+1 是否等于 key[3] 0040127B |. 75 5E jnz short 004012DB
第七八九校验Key:
0040127D |. 807C24 16 38 cmp byte ptr [esp+0x16], 0x38 ; 判断key[6] 是否等于 ‘8‘ 00401282 |. 75 57 jnz short 004012DB 00401284 |. 807C24 10 39 cmp byte ptr [esp+0x10], 0x39 ; 判断key[0] 是否等于 ‘9‘ 00401289 |. 75 50 jnz short 004012DB 0040128B |. 807C24 18 30 cmp byte ptr [esp+0x18], 0x30 ; 判断key[8] 是否等于 ‘0‘ 00401290 |. 75 49 jnz short 004012DB
第十次校验Key(判断key里是不是有3个‘2’):
00401292 |. 33C0 xor eax, eax 00401294 |. B1 32 mov cl, 0x32 00401296 |> 384C04 10 /cmp byte ptr [esp+eax+0x10], cl ; if(key[i] == ‘2‘) 0040129A |. 75 01 |jnz short 0040129D 0040129C |. 45 |inc ebp ; j++ 0040129D |> 40 |inc eax 0040129E |. 83F8 0D |cmp eax, 0xD 004012A1 |.^ 7C F3 \jl short 00401296 004012A3 |. 83FD 03 cmp ebp, 0x3 004012A6 |. 75 33 jnz short 004012DB
第十一次校验Key:
004012A8 |. 0FBE4424 1B movsx eax, byte ptr [esp+0x1B] ; key[11] 004012AD |. 0FBE4C24 1A movsx ecx, byte ptr [esp+0x1A] ; key[10] 004012B2 |. 8D50 FF lea edx, dword ptr [eax-0x1] ; key[11]-1 004012B5 |. 3BCA cmp ecx, edx ; key[10] == key[11]-1 004012B7 |. 75 22 jnz short 004012DB
第十二次校验Key:
004012B9 |. 83C1 D0 add ecx, -0x30 ; key[10](int) 004012BC |. 83C0 D0 add eax, -0x30 ; key[11](int) 004012BF |. 0FAFC8 imul ecx, eax ; key[10](int)*key[11](int) 004012C2 |. 0FBE4424 1C movsx eax, byte ptr [esp+0x1C] ; key[c] 004012C7 |. 83E8 30 sub eax, 0x30 ; key[c](int) 004012CA |. 33D2 xor edx, edx 004012CC |. 3BC8 cmp ecx, eax ; key[10](int)*key[11](int) == key[c](int)
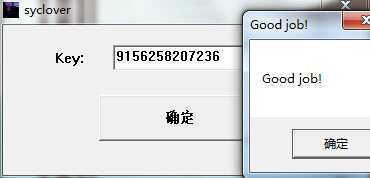
Key: 9156258207236
Bin下载链接:http://pan.baidu.com/s/1mgA4Kje 密码:vvmi
标签:blog http ar sp 数据 div 2014 on log
原文地址:http://www.cnblogs.com/ReverseSec/p/4027608.html