标签:sed cas model browser computer store ros answer tac
Analyze the malware found in the file Lab07-02.exe.
How does this program achieve persistence?
A: This program does not achieve persistence. It runs once and then exits.
What is the purpose of this program?
A: The program displays an advertisement web page to the user.
When will this program finish executing?
A: The program finishes executing after displaying the advertisement.
We begin with some basic static analysis. While we don’t see any interesting ASCII strings, we do see one interesting Unicode string: http://www.malwareanalysisbook.com/ad.html. We check the imports and exports of the program, and see only a few imports in addition to the standard imports, as follows:
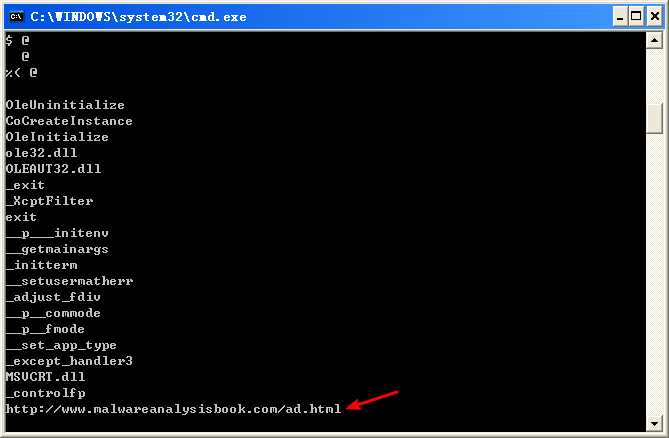
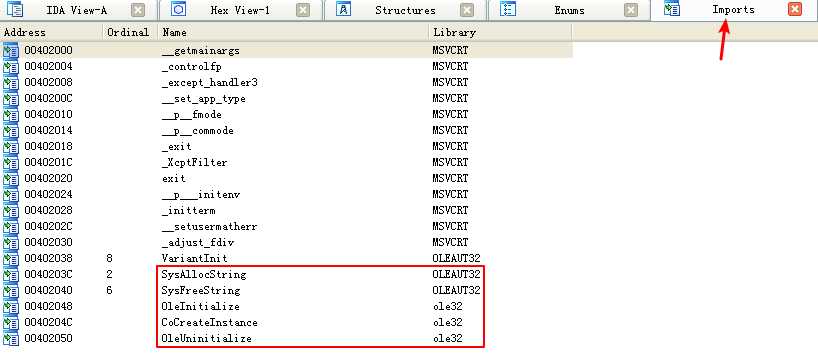
All of these functions are COM-related. The CoCreateInstance and OleInitialize functions in particular are required in order to use COM functionality.
Next, we try dynamic analysis. When we run this program, it opens Internet Explorer and displays an advertisement. There’s no evidence of the program modifying the system or installing itself to execute when the computer is restarted.
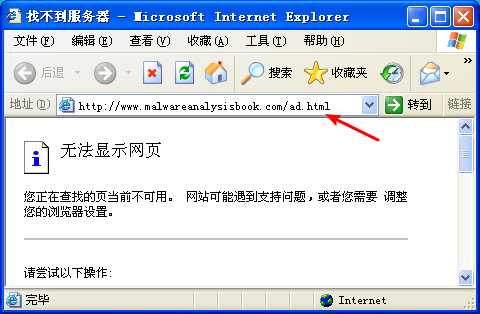
注:这是我掐断网络,运行 Lab07-02 的结果。
Now we can analyze the code in IDA Pro. We navigate to the *_main* method and see the code shown in the following listing.
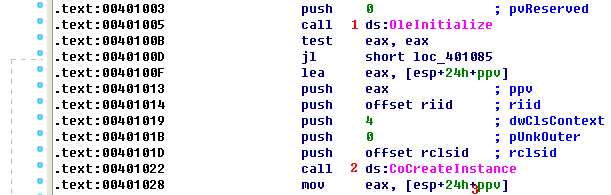
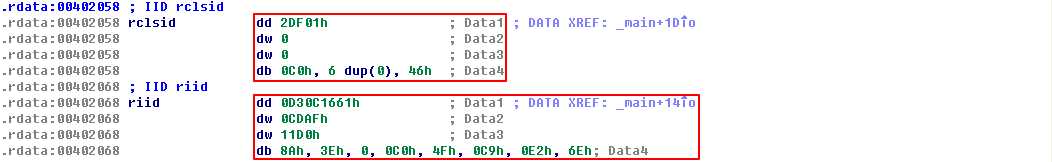
The first thing the malware does is initialize COM and obtain a pointer to a COM object with OleInitialize at \({\color{red} 1 }\) and CoCreateInstance at \({\color{red} 2 }\). The COM object returned will be stored on the stack in a variable that IDA Pro has labeled ppv, as shown at \({\color{red} 3}\). In order to determine what COM functionality is being used, we need to examine the interface identifier (IID) and class identifier (CLSID).
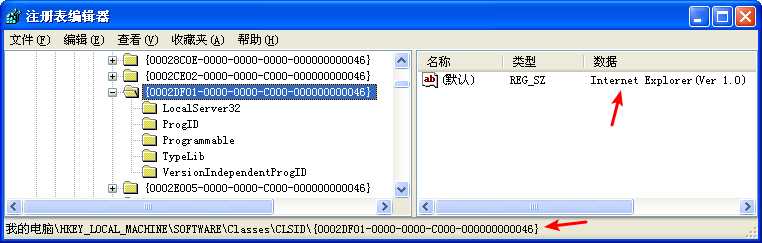
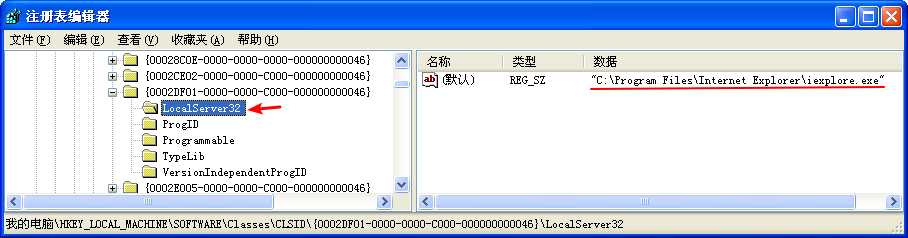
Clicking rclsid and riid shows that they are 0002DF01-0000-0000-C000-000000000046 and D30C1661-CDAF-11D0-8A3E-00C04FC9E26E, respectively. To determine which program will be called, check the registry for the CLSID, or search for the IID on the Internet for any documentation. In this case, these values are the same identifiers we used in “The Component Object Model” on page 154. The IID is for IWebBrowser2, and the CLSID is for Internet Explorer.
As shown in the following listing, the COM object returned by CoCreateInstance is accessed a few instructions later at \({\color{red} 1 }?\).
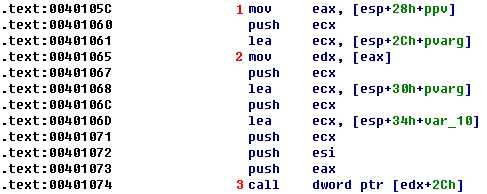
Following this instruction, EAX points to the location of the COM object. At \({\color{red}2}\), EAX is dereferenced and EDX points to the beginning of the COM object itself. At \({\color{red} 3}\), the function at an offset of +0x2C from the object is called. As discussed in the chapter, the offset 0x2C for the IWebBrowser2 interface is the Navigate function, and we can use the Structures window in IDA Pro to create a structure and label the offset. When Navigate is called, Internet Explorer navigates to the web address http://www.malwareanalysisbook.com/ad.html.
注:标识 edx + 2Ch(重命名偏移 2Ch):
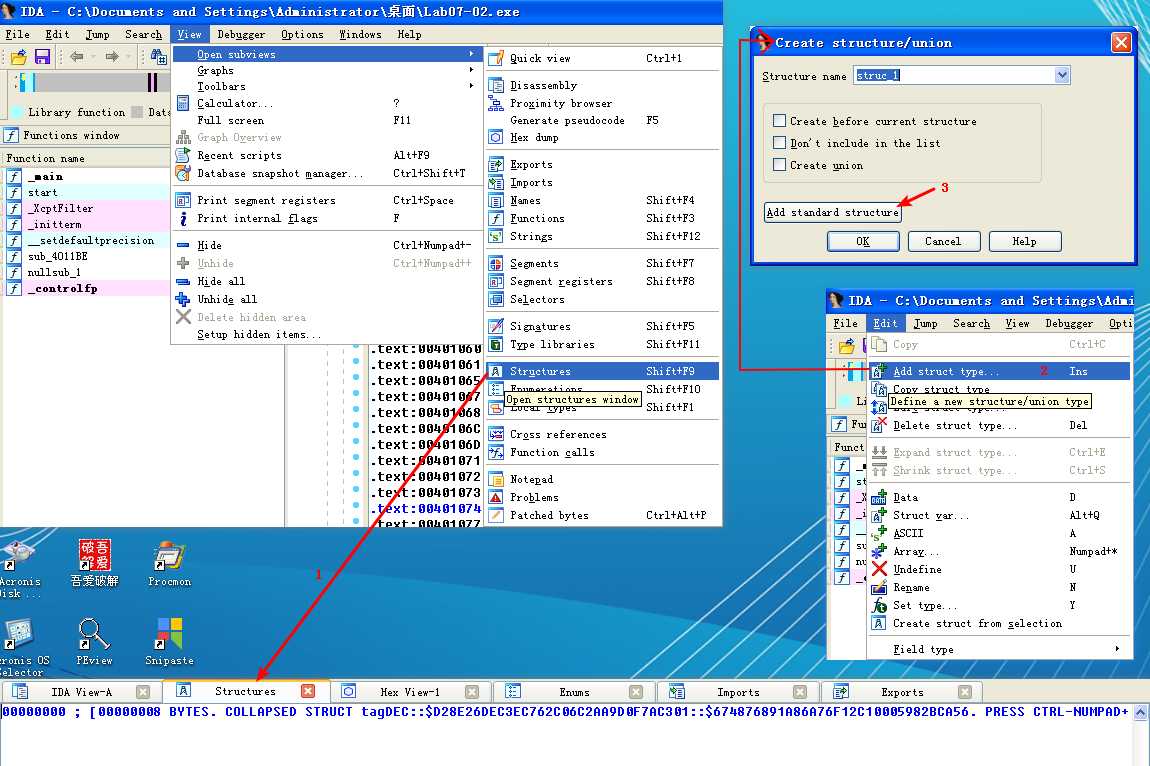
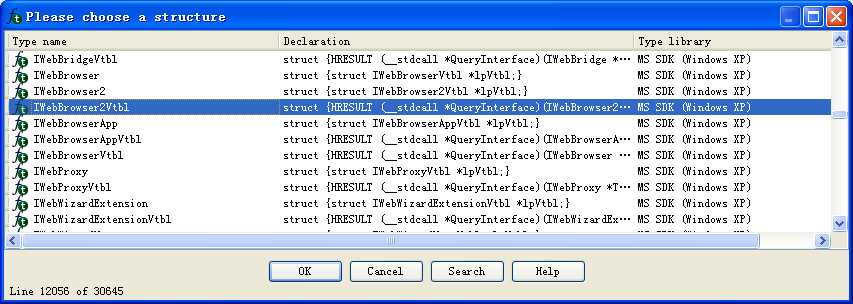
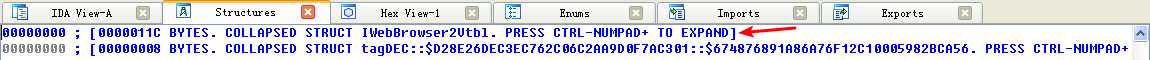
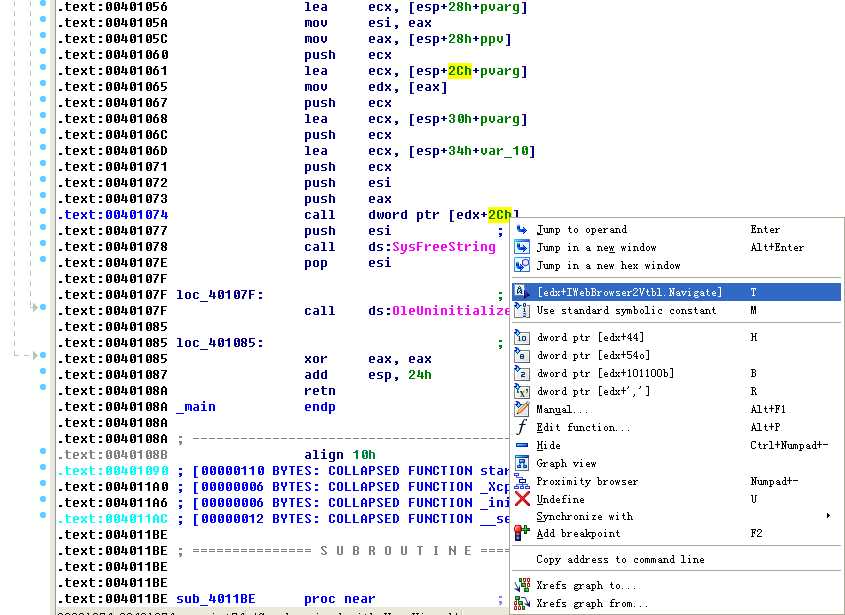
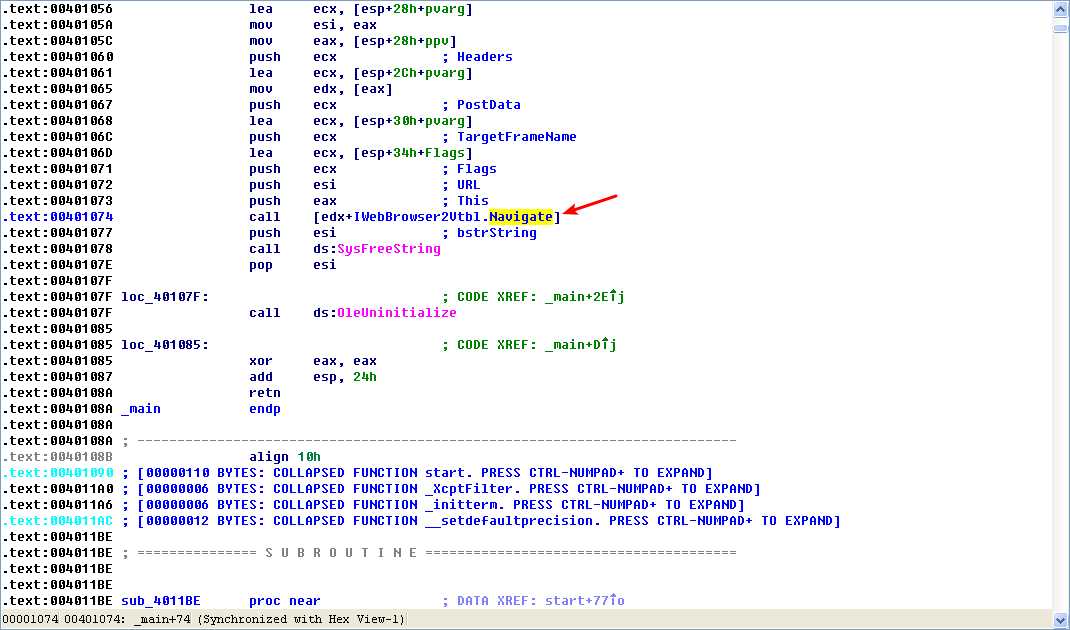
注结束。
After the call to Navigate, there are a few cleanup functions and then the program ends. The program doesn’t install itself persistently, and it doesn’t modify the system. It simply displays a one-time advertisement.
When you encounter a simple program like this one, you should consider it suspect. It may come packaged with additional malware, of which this is just one component.
标签:sed cas model browser computer store ros answer tac
原文地址:https://www.cnblogs.com/d0ct0rx/p/10281419.html