标签:windows 7 prot written string install ima lease word ESS
一、 Frist Continue to jot down notes about the Nmap
1、nmap -sn [ip] This command will send an ARP request to the LAN broadcast address and will determine whether the host is live
eg: we use the command to gathering system information (as follow ,it‘s mine windows7 system) ,in addition we combination of linux and others system are used ,I have written about install kali and Ubuntu 、Metasploitable2 system on my previous blog .you can refer the installing on the Vmware . and then fire start the ubuntu system and use the same command to gathering information .
the step one : gathering win7 system
Starting Nmap 7.70 ( https://nmap.org ) at 2019-01-17 20:48 EST
Nmap scan report for 10.130.209.131
Host is up (0.82s latency).
Not shown: 986 closed ports
PORT STATE SERVICE VERSION
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
443/tcp open ssl/https
| fingerprint-strings:
| FourOhFourRequest:
| HTTP/1.1 404 Not Found
| Date: Fri, 18 Jan 2019 01:48:39 GMT
| Connection: close
| Content-Type: text/plain; charset=utf-8
| X-Frame-Options: DENY
| Content-Length: 0
| GetRequest:
| HTTP/1.1 403 Forbidden
| Date: Fri, 18 Jan 2019 01:48:39 GMT
| Connection: close
| Content-Type: text/plain; charset=utf-8
| X-Frame-Options: DENY
| Content-Length: 0
| HTTPOptions:
| HTTP/1.1 501 Not Implemented
| Date: Fri, 18 Jan 2019 01:48:39 GMT
| Connection: close
| Content-Type: text/plain; charset=utf-8
| X-Frame-Options: DENY
| Content-Length: 0
| RTSPRequest:
| HTTP/1.1 400 Bad Request
| Date: Fri, 18 Jan 2019 01:48:49 GMT
| Connection: close
| Content-Type: text/html
| Content-Length: 50
| <HTML><BODY><H1>400 Bad Request</H1></BODY></HTML>
| SIPOptions:
| HTTP/1.1 400 Bad Request
| Date: Fri, 18 Jan 2019 01:49:52 GMT
| Connection: close
| Content-Type: text/html
| Content-Length: 50
|_ <HTML><BODY><H1>400 Bad Request</H1></BODY></HTML>
|_http-title: Site doesn‘t have a title (text/plain; charset=utf-8).
| ssl-cert: Subject: commonName=VMware/countryName=US
| Not valid before: 2017-10-09T12:32:16
|_Not valid after: 2018-10-09T12:32:16
|_ssl-date: TLS randomness does not represent time
| vmware-version:
| Server version: VMware Workstation 14.1.1
| Build: 7528167
| Locale version: INTL
| OS type: win32-x86
|_ Product Line ID: ws
445/tcp open microsoft-ds Windows 7 Ultimate 7601 Service Pack 1 microsoft-ds (workgroup: WorkGroup)
514/tcp filtered shell
902/tcp open ssl/vmware-auth VMware Authentication Daemon 1.10 (Uses VNC, SOAP)
912/tcp open vmware-auth VMware Authentication Daemon 1.0 (Uses VNC, SOAP)
1025/tcp open msrpc Microsoft Windows RPC
1026/tcp open msrpc Microsoft Windows RPC
1027/tcp open msrpc Microsoft Windows RPC
1033/tcp open msrpc Microsoft Windows RPC
1055/tcp open msrpc Microsoft Windows RPC
5357/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Service Unavailable
8082/tcp open blackice-alerts?
| fingerprint-strings:
| FourOhFourRequest, GenericLines, GetRequest, HTTPOptions, RTSPRequest, SIPOptions:
| HTTP/1.1 400 Error
| Server: QQ/1.0.0 (Tencent)
| Content-Length: 18
| Connection: close
|_ unkown the request
2 services unrecognized despite returning data. If you know the service/version, please submit the following fingerprints at https://nmap.org/cgi-bin/submit.cgi?new-service :
==============NEXT SERVICE FINGERPRINT (SUBMIT INDIVIDUALLY)==============
SF-Port443-TCP:V=7.70%T=SSL%I=7%D=1/17%Time=5C41307C%P=x86_64-pc-linux-gnu
SF:%r(GetRequest,A5,"HTTP/1\.1\x20403\x20Forbidden\r\nDate:\x20Fri,\x2018\
SF:x20Jan\x202019\x2001:48:39\x20GMT\r\nConnection:\x20close\r\nContent-Ty
SF:pe:\x20text/plain;\x20charset=utf-8\r\nX-Frame-Options:\x20DENY\r\nCont
SF:ent-Length:\x200\r\n\r\n")%r(HTTPOptions,AB,"HTTP/1\.1\x20501\x20Not\x2
SF:0Implemented\r\nDate:\x20Fri,\x2018\x20Jan\x202019\x2001:48:39\x20GMT\r
SF:\nConnection:\x20close\r\nContent-Type:\x20text/plain;\x20charset=utf-8
SF:\r\nX-Frame-Options:\x20DENY\r\nContent-Length:\x200\r\n\r\n")%r(FourOh
SF:FourRequest,A5,"HTTP/1\.1\x20404\x20Not\x20Found\r\nDate:\x20Fri,\x2018
SF:\x20Jan\x202019\x2001:48:39\x20GMT\r\nConnection:\x20close\r\nContent-T
SF:ype:\x20text/plain;\x20charset=utf-8\r\nX-Frame-Options:\x20DENY\r\nCon
SF:tent-Length:\x200\r\n\r\n")%r(RTSPRequest,B3,"HTTP/1\.1\x20400\x20Bad\x
SF:20Request\r\nDate:\x20Fri,\x2018\x20Jan\x202019\x2001:48:49\x20GMT\r\nC
SF:onnection:\x20close\r\nContent-Type:\x20text/html\r\nContent-Length:\x2
SF:050\r\n\r\n<HTML><BODY><H1>400\x20Bad\x20Request</H1></BODY></HTML>")%r
SF:(SIPOptions,B3,"HTTP/1\.1\x20400\x20Bad\x20Request\r\nDate:\x20Fri,\x20
SF:18\x20Jan\x202019\x2001:49:52\x20GMT\r\nConnection:\x20close\r\nContent
SF:-Type:\x20text/html\r\nContent-Length:\x2050\r\n\r\n<HTML><BODY><H1>400
SF:\x20Bad\x20Request</H1></BODY></HTML>");
==============NEXT SERVICE FINGERPRINT (SUBMIT INDIVIDUALLY)==============
SF-Port8082-TCP:V=7.70%I=7%D=1/17%Time=5C41307B%P=x86_64-pc-linux-gnu%r(Ge
SF:tRequest,6D,"HTTP/1\.1\x20400\x20Error\x20\r\nServer:\x20QQ/1\.0\.0\x20
SF:\(Tencent\)\x20\r\nContent-Length:\x2018\r\nConnection:\x20close\r\n\r\
SF:nunkown\x20the\x20request")%r(FourOhFourRequest,6D,"HTTP/1\.1\x20400\x2
SF:0Error\x20\r\nServer:\x20QQ/1\.0\.0\x20\(Tencent\)\x20\r\nContent-Lengt
SF:h:\x2018\r\nConnection:\x20close\r\n\r\nunkown\x20the\x20request")%r(Ge
SF:nericLines,6D,"HTTP/1\.1\x20400\x20Error\x20\r\nServer:\x20QQ/1\.0\.0\x
SF:20\(Tencent\)\x20\r\nContent-Length:\x2018\r\nConnection:\x20close\r\n\
SF:r\nunkown\x20the\x20request")%r(HTTPOptions,6D,"HTTP/1\.1\x20400\x20Err
SF:or\x20\r\nServer:\x20QQ/1\.0\.0\x20\(Tencent\)\x20\r\nContent-Length:\x
SF:2018\r\nConnection:\x20close\r\n\r\nunkown\x20the\x20request")%r(RTSPRe
SF:quest,6D,"HTTP/1\.1\x20400\x20Error\x20\r\nServer:\x20QQ/1\.0\.0\x20\(T
SF:encent\)\x20\r\nContent-Length:\x2018\r\nConnection:\x20close\r\n\r\nun
SF:kown\x20the\x20request")%r(SIPOptions,6D,"HTTP/1\.1\x20400\x20Error\x20
SF:\r\nServer:\x20QQ/1\.0\.0\x20\(Tencent\)\x20\r\nContent-Length:\x2018\r
SF:\nConnection:\x20close\r\n\r\nunkown\x20the\x20request");
Device type: general purpose
Running: Microsoft Windows XP|7|2012
OS CPE: cpe:/o:microsoft:windows_xp::sp3 cpe:/o:microsoft:windows_7 cpe:/o:microsoft:windows_server_2012
OS details: Microsoft Windows XP SP3, Microsoft Windows XP SP3 or Windows 7 or Windows Server 2012
Network Distance: 2 hops
Service Info: Host: NETPOLICE; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
|_clock-skew: mean: -2h40m05s, deviation: 4h37m07s, median: -5s
|_nbstat: NetBIOS name: NETPOLICE, NetBIOS user: <unknown>, NetBIOS MAC: a4:db:30:5b:69:3a (Liteon Technology)
| smb-os-discovery:
| OS: Windows 7 Ultimate 7601 Service Pack 1 (Windows 7 Ultimate 6.1)
| OS CPE: cpe:/o:microsoft:windows_7::sp1
| Computer name: NetPolice
| NetBIOS computer name: NETPOLICE\x00
| Workgroup: WorkGroup\x00
|_ System time: 2019-01-18T09:51:14+08:00
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
| smb2-security-mode:
| 2.02:
|_ Message signing enabled but not required
| smb2-time:
| date: 2019-01-17 20:51:14
|_ start_date: 2019-01-17 19:39:29
TRACEROUTE (using port 3389/tcp)
HOP RTT ADDRESS
1 1.88 ms 192.168.142.2
2 1000.69 ms 10.130.209.131
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 242.79 seconds
the setp two :gathering the Ubuntu information
eg: Ubuntu system information
Starting Nmap 7.70 ( https://nmap.org ) at 2019-01-17 21:13 EST
Nmap scan report for 192.168.142.171
Host is up (0.00068s latency).
Not shown: 999 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.1 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 ac:b1:ea:b8:39:3f:c2:61:74:82:d8:a7:06:4c:57:ec (RSA)
| 256 9b:36:1f:ce:79:c8:04:6e:cf:96:72:2b:0a:99:a5:71 (ECDSA)
|_ 256 87:06:4a:2c:f2:d9:3a:81:22:f1:fd:18:bb:f5:54:d6 (ED25519)
MAC Address: 00:0C:29:26:DB:DD (VMware)
Device type: general purpose
Running: Linux 3.X|4.X
OS CPE: cpe:/o:linux:linux_kernel:3 cpe:/o:linux:linux_kernel:4
OS details: Linux 3.2 - 4.9
Network Distance: 1 hop
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE
HOP RTT ADDRESS
1 0.68 ms 192.168.142.171
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 15.10 seconds
2、if we don‘t know the host ip is livewe can use the dash-notation to scan teh LAN network , but we use the command to scan another LAN ,it‘s means permormed against remoter hosts on a different LAN ,the response will not include system the MAC address ..
the command is : namp -sn 192.168.5.0-255 or we can use the command 192.168.5.0/24
another if we want to scan a table list ip address the we can use the command iL like as : nmap -iL ipList.txt -sn (ipList.txt is a note write down some ip address )
eg : nmap -iL /home/iplist.txt -sn (note : in fact we can‘t make sure the correct that the host is live through only in this scan )
besides this wiget we can use the Netdisocover to gathering the system information
3、 tracert the route ,we use the tracert to track the abroad ip address .
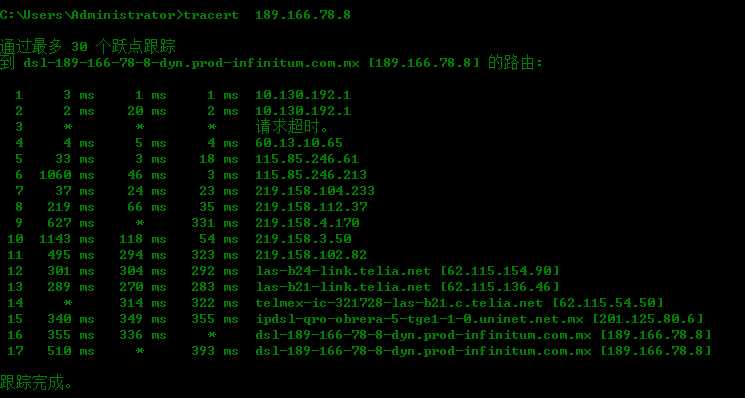
4、use openvas to scan the website
step one how to install the openvas in the kali linux . if we forget the account and password we can use the command to change the account : openvasmd --user=admin --new-password=[password] ,you can also add a new account for openvas use the command :
{openvasmd --create-user=name 创建一个新的账户 openvasmd --delete-user=name 删除一个账户} now at present we look the openvas install on the kali linux
if you want change the default configpage we can Modify configuration: general used information in the greenbone-security-assistant ,the locate in : vi /etc/default/greenbone-security-assistant/ in the page we can change the host ip "GSA_ADDRESS=127.0.0.1--------> eg you host ip address .
标签:windows 7 prot written string install ima lease word ESS
原文地址:https://www.cnblogs.com/xinxianquan/p/10289027.html