标签:style blog http color io os ar for strong
RunJS
此bat中国互联网公司三巨头bat
常用引导,有时启动某个应用需要环境变量可以这样启动应用,会对启动的进程生效,即被继承
set PATH=D:\Developer\sdk\platform-tools;%PATH% D: chdir D:\Developer\Cygwin\bin REM 推荐注释REM,次之::。 set AndBug=D:\Developer\Cygwin\home\Sansan\AndBug set PATH=D:\Developer\sdk\platform-tools;%PATH% set PYTHONPATH=%AndBug%\lib;%PYTHONPATH% D: chdir %AndBug% C:\Python27\python.exe andbug
获取目录举例
:: Demo.bat/Demo.cmd文件 @echo off setlocal EnableDelayedExpansion echo 批处理文件%~df0 echo %%0 = %0 echo 当前正在运行的批处理文件所在路径: echo ^^!cd^^! = !cd! echo 当前目录是:%cd% echo %%cd%% = %cd% echo 当前的盘符及路径:%~dp0 echo %%~dp0 = %~dp0 echo 当前的盘符及路径的短文件名格式: echo %%~sdp0 = %~sdp0 :: set "abc=%cd%" :: 批处理文件C:\Masm64\Masm64\Examples\Console\d.cmd REM %0 = "C:\Masm64\Masm64\Examples\Console\d.cmd" :: 当前正在运行的批处理文件所在路径: REM !cd! = C:\Masm64\Masm64\Examples\Console :: 当前目录是:C:\Masm64\Masm64\Examples\Console REM %cd% = C:\Masm64\Masm64\Examples\Console :: 当前的盘符及路径:C:\Masm64\Masm64\Examples\Console\ REM %~dp0 = C:\Masm64\Masm64\Examples\Console\ :: 当前的盘符及路径的短文件名格式: REM %~sdp0 = C:\Masm64\Masm64\Examples\Console\ :: 转义 ::1、代码XXX中如含><&| 需在每个这类符号前加转义符 ^ ::2、符号%不能用^而是双写自己,如echo %%windir%% 输出字符串%windir%。当然如果是想把本次批处理中的某变量值传递到新批处理中(即在新批处理中此处已是常量)另当别论,从某个意义上说,这种情况用批处理建批处理有一定实际意义——只有运行本批处理,才能得到运行另一批处理需要的数据 ::3、如果你写这句代码处在某括号之中,那么括号也很特殊,可能也要加 ^ 来转义其他的我没仔细想,也许还有,例如符号 !
::总之可能对本批处理会起到改变命令作用的都要转义 ::4、如果代码中有转义符本身,则它也要转义,等于是双写 ::5、如果写入另一批处理的代码较多,且排除了上一条所说的传递变量值的情况,可用另一方法不用转义就照代码需要格式写,方法是在本批处理最后加一句 ::more +8 %0>123.bat&exit (这里的数字8表示到本行共有多少行,据实改) ::表示把本批处理第8行之后的内容写入新批处理并退出(即不执行之后的代码)再把要写入的所有代码写在本批处理的最后 pause
%0即代表该批处理的全称(包括驱动器盘符、路径、文件名和扩展类型)
组合修饰符来得到多重结果 %~df0

In addition, substitution of FOR variable references has been enhanced. You can now use the following optional syntax: %~I - expands %I removing any surrounding quotes (") %~fI - expands %I to a fully qualified path name %~dI - expands %I to a drive letter only %~pI - expands %I to a path only %~nI - expands %I to a file name only %~xI - expands %I to a file extension only %~sI - expanded path contains short names only %~aI - expands %I to file attributes of file %~tI - expands %I to date/time of file %~zI - expands %I to size of file %~$PATH:I - searches the directories listed in the PATH environment variable and expands %I to the fully qualified name of the first one found. If the environment variable name is not defined or the file is not found by the search, then this modifier expands to the empty string The modifiers can be combined to get compound results: %~dpI - expands %I to a drive letter and path only %~nxI - expands %I to a file name and extension only %~fsI - expands %I to a full path name with short names only %~dp$PATH:I - searches the directories listed in the PATH environment variable for %I and expands to the drive letter and path of the first one found. %~ftzaI - expands %I to a DIR like output line In the above examples %I and PATH can be replaced by other valid values. The %~ syntax is terminated by a valid FOR variable name. Picking upper case variable names like %I makes it more readable and avoids confusion with the modifiers, which are not case sensitive.
Windows Registry Editor Version 5.00
[-HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run]
保存为reg文件双击导如即可删除此项,注意有个“-”号
Windows Registry Editor Version 5.00
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run]
"SoundMan"=-
这样可以删除此值
HKEY_CURRENT_USER\Software\Policies\Microsoft\Internet Explorer\Control Panel
HomePage=dword:00000000
C:\Users\ss>reg add /?
REG ADD KeyName [/v ValueName | /ve] [/t Type] [/s Separator] [/d Data] [/f]
[/reg:32 | /reg:64]KeyName [\\Machine\]FullKey
Machine Name of remote machine - omitting defaults to the
current machine. Only HKLM and HKU are available on remote
machines.
FullKey ROOTKEY\SubKey
ROOTKEY [ HKLM | HKCU | HKCR | HKU | HKCC ]
SubKey The full name of a registry key under the selected ROOTKEY./v The value name, under the selected Key, to add.
/ve adds an empty value name (Default) for the key.
/t RegKey data types
[ REG_SZ | REG_MULTI_SZ | REG_EXPAND_SZ |
REG_DWORD | REG_QWORD | REG_BINARY | REG_NONE ]
If omitted, REG_SZ is assumed./s Specify one character that you use as the separator in your data
string for REG_MULTI_SZ. If omitted, use "\0" as the separator./d The data to assign to the registry ValueName being added.
/f Force overwriting the existing registry entry without prompt.
/reg:32 Specifies the key should be accessed using the 32-bit registry view.
/reg:64 Specifies the key should be accessed using the 64-bit registry view.
Examples:
REG ADD \\ABC\HKLM\Software\MyCo
Adds a key HKLM\Software\MyCo on remote machine ABCREG ADD HKLM\Software\MyCo /v Data /t REG_BINARY /d fe340ead
Adds a value (name: Data, type: REG_BINARY, data: fe340ead)REG ADD HKLM\Software\MyCo /v MRU /t REG_MULTI_SZ /d fax\0mail
Adds a value (name: MRU, type: REG_MULTI_SZ, data: fax\0mail\0\0)REG ADD HKLM\Software\MyCo /v Path /t REG_EXPAND_SZ /d ^%systemroot^%
Adds a value (name: Path, type: REG_EXPAND_SZ, data: %systemroot%)
Notice: Use the caret symbol ( ^ ) inside the expand string
rem Update the Image File Execution key. reg add "HKLM\Software\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\SearchIndexer.exe" /v TracingFlags /t REG_DWORD /d 1 /f reg add "HKLM\Software\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\SearchProtocolHost.exe" /v TracingFlags /t REG_DWORD /d 1 /f reg add "HKLM\Software\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\SearchFilterHost.exe" /v TracingFlags /t REG_DWORD /d 1 /f reg query "HKLM\Software\Microsoft\Windows NT\CurrentVersion\Image File Execution Options" /s /v TracingFlagsrem Clean up registry flags. reg delete "HKLM\Software\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\SearchIndexer.exe" /v TracingFlags /f reg delete "HKLM\Software\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\SearchProtocolHost.exe" /v TracingFlags /f reg delete "HKLM\Software\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\SearchFilterHost.exe" /v TracingFlags /f reg query "HKLM\Software\Microsoft\Windows NT\CurrentVersion\Image File Execution Options" /s /v TracingFlags
Debugger参数的这种特殊作用,它又被称为“重定向”(Redirection),而利用它进行的攻击,又被称为“重定向劫持”(Redirection Hijack),它和“映像劫持”(Image Hijack,或IFEO Hijack)只是称呼不同,实际上都是一样的技术手段。
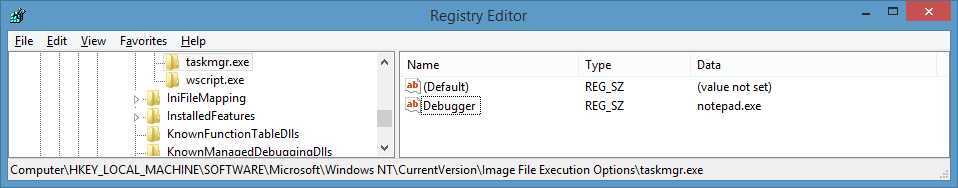
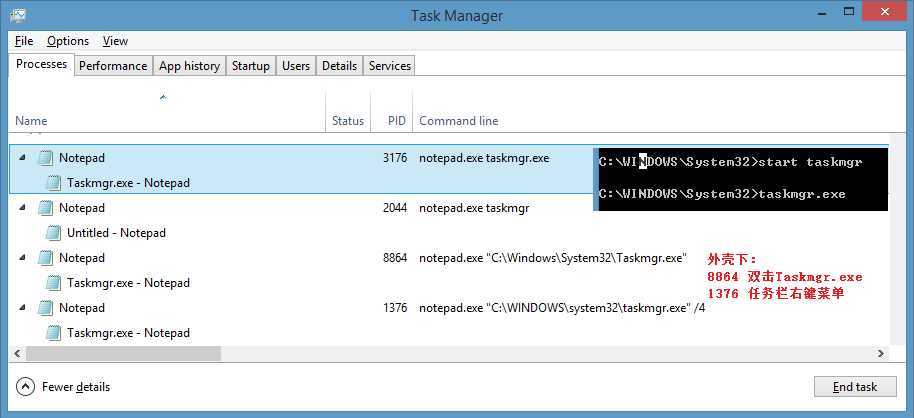
结果:
标签:style blog http color io os ar for strong
原文地址:http://www.cnblogs.com/Fang3s/p/4033800.html