标签:source this mode ati def inter 交换机 security 访问
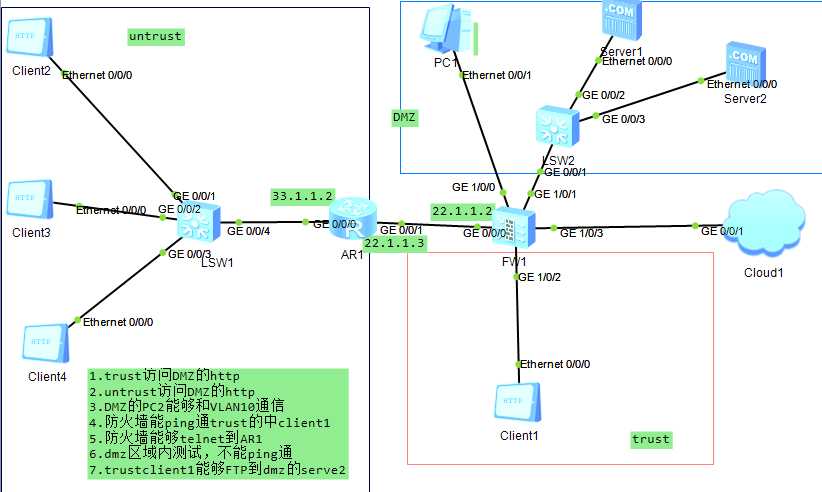
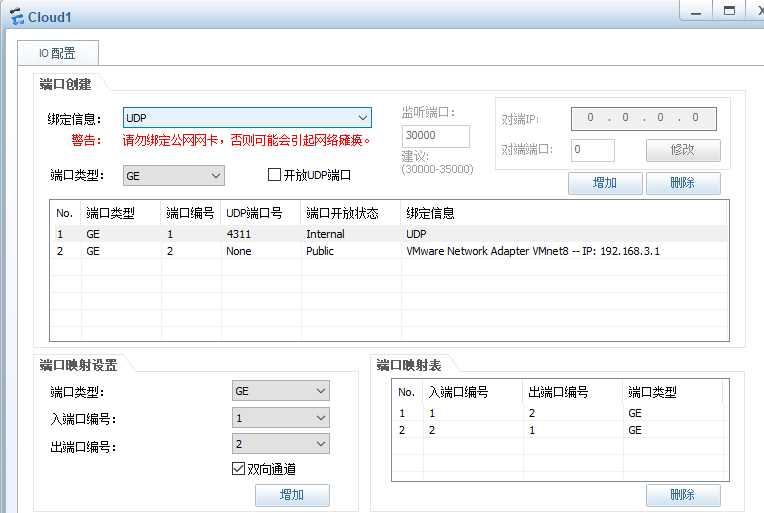
1.配置防火墙:
int g1/0/3
ip add 192.168.3.2
service-manage enable
service-manage all permit
把接口画进zone区域:
[USG6000V1]firewall zone trust
[USG6000V1-zone-trust]add interface gig1/0/3
此时防火墙起来:
6.dmz区域内测试,不能ping通
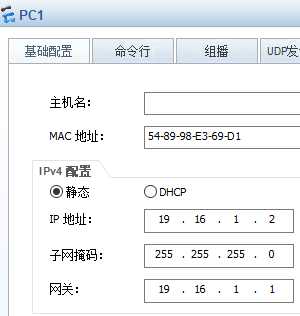
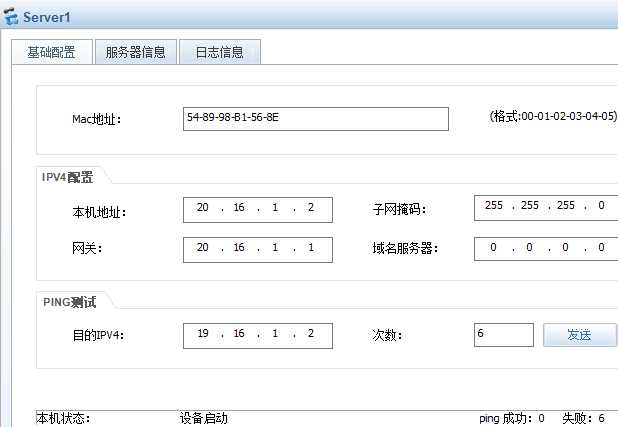
g1/0/0和g1/0/1接口划入dmz区域 并开启功能
[USG6000V1-GigabitEthernet1/0/0]dis this
2019-08-28 12:37:32.860
#
interface GigabitEthernet1/0/0
undo shutdown
ip address 19.16.1.1 255.255.255.0
service-manage enable
service-manage all permit
interface GigabitEthernet1/0/1
undo shutdown
ip address 20.16.1.1 255.255.255.0
service-manage http permit
service-manage https permit
service-manage ping permit
service-manage ssh permit
service-manage snmp permit
service-manage telnet permit
[USG6000V1]firewall zone dmz
[USG6000V1-zone-dmz]dis this
#
firewall zone dmz
set priority 50
add interface GigabitEthernet1/0/0
add interface GigabitEthernet1/0/1
#
此时pc1和 service 1 2 是通的
做策略:
[USG6000V1-policy-security-rule-permit_dmz_dmz]dis this
2019-08-28 12:46:46.920
#
rule name permit_dmz_dmz
source-zone dmz
destination-zone dmz
source-address 19.16.1.0 mask 255.255.255.0
destination-address 20.16.1.0 mask 255.255.255.0
service icmp
action deny
此时pc1和 service 1 2 是不通的
1.trust访问DMZ的http
[USG6000V1-GigabitEthernet1/0/2]dis this
2019-08-28 12:56:56.860
#
interface GigabitEthernet1/0/2
undo shutdown
ip address 23.1.1.1 255.255.255.0
[USG6000V1-zone-trust]dis this
2019-08-28 12:57:23.740
#
firewall zone trust
set priority 85
add interface GigabitEthernet1/0/2
add interface GigabitEthernet1/0/3
#
return
[USG6000V1-policy-security-rule-permit_trust_dmz]dis this
2019-08-28 12:56:21.860
#
rule name permit_trust_dmz
source-zone trust
destination-zone dmz
source-address 23.1.1.0 mask 255.255.255.0
destination-address 19.16.1.0 mask 255.255.255.0
destination-address 20.16.1.0 mask 255.255.255.0
service http
service icmp
action permit
2.untrust访问DMZ的http
配置静态,配置策略,防火墙 口的配置
交换机1:
interface Vlanif10
ip address 101.1.1.1 255.255.255.0
#
interface Vlanif20
ip address 202.1.1.1 255.255.255.0
#
interface Vlanif30
ip address 203.1.1.1 255.255.255.0
#
interface Vlanif100
ip address 33.1.1.1 255.255.255.0
interface GigabitEthernet0/0/1
port link-type access
port default vlan 10
#
interface GigabitEthernet0/0/2
port link-type access
port default vlan 20
#
interface GigabitEthernet0/0/3
port link-type access
port default vlan 30
#
interface GigabitEthernet0/0/4
port link-type access
port default vlan 100
ip route-static 0.0.0.0 0.0.0.0 33.1.1.2
ip route-static 19.16.1.0 255.255.255.0 33.1.1.2
ip route-static 20.16.1.0 255.255.255.0 33.1.1.2
ip route-static 22.1.1.0 255.255.255.0 33.1.1.2
#
user-interface con 0
user-interface vty 0 4
R1:
interface GigabitEthernet0/0/0
ip address 33.1.1.2 255.255.255.0
#
interface GigabitEthernet0/0/1
ip address 22.1.1.3 255.255.255.0
#
interface GigabitEthernet0/0/2
#
interface NULL0
#
ip route-static 19.16.1.0 255.255.255.0 22.1.1.2
ip route-static 20.16.1.0 255.255.255.0 22.1.1.2
ip route-static 101.1.1.0 255.255.255.0 33.1.1.1
ip route-static 202.1.1.0 255.255.255.0 33.1.1.1
ip route-static 203.1.1.0 255.255.255.0 33.1.1.1
FW:
ip route-static 0.0.0.0 0.0.0.0 22.1.1.3
ip route-static 33.1.1.0 255.255.255.0 22.1.1.3
ip route-static 101.1.1.0 255.255.255.0 22.1.1.3
ip route-static 202.1.1.0 255.255.255.0 22.1.1.3
ip route-static 203.1.1.0 255.255.255.0 22.1.1.3
rule name permit_untrust_dmz
source-zone untrust
destination-zone dmz
source-address 101.1.1.100 mask 255.255.255.255
destination-address 19.16.1.2 mask 255.255.255.255
destination-address 20.16.1.0 mask 255.255.255.0
service http
service icmp
action permit
firewall zone untrust
set priority 5
add interface GigabitEthernet0/0/0
注意zone口的划分。
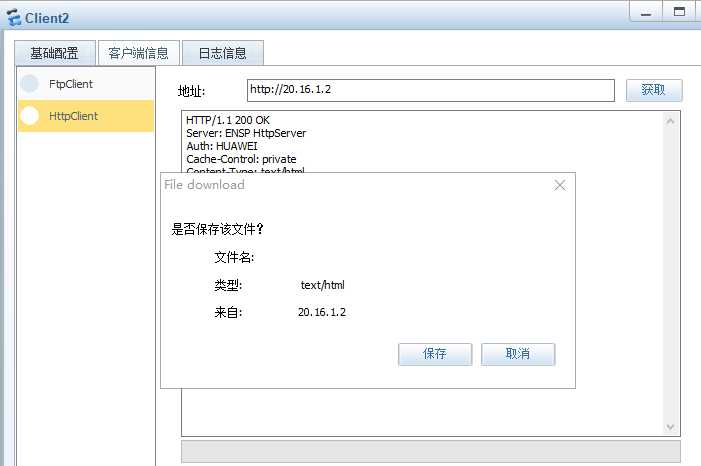
3.DMZ的PC2能够和VLAN10通信
rule name permit_dmz_untrust
source-zone dmz
destination-zone untrust
source-address 19.16.1.0 mask 255.255.255.0
destination-address 101.1.1.0 mask 255.255.255.0
service http
service icmp
action permit
策略不可以双向通;
要想防火墙通别人,写策略
4.防火墙能ping通trust的中client1
[USG6000V1-policy-security-rule-permit_local_trust]dis this
2019-08-29 08:45:08.510
#
rule name permit_local_trust
source-zone local
destination-zone trust
source-address 23.1.1.0 mask 255.255.255.0
destination-address 23.1.1.0 mask 255.255.255.0
service http
service icmp
action permit
#
return
源zone区域为local
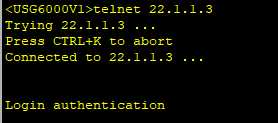
5.防火墙能够telnet到AR1
AR1:
做个aaa认证:
aaa
local-user qqq password cipher %$%$&LR6E7OJzVkDhT&/8=5UEmdJ%$%$
local-user qqq privilege level 15
local-user qqq service-type telnet
调用:
user-interface vty 0 4
authentication-mode aaa
protocol inbound all
.防火墙:
rule name permit_local_untrust
source-zone local
destination-zone untrust
service icmp
service telnet
action permit
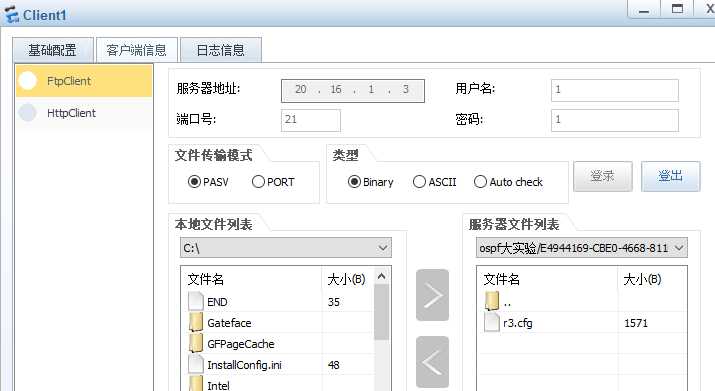
7.trust client1能够FTP到dmz的serve2
开启ftp服务:
[USG6000V1-policy-security-rule-permit_trust_dmz]dis thi
2019-08-29 09:37:08.820
#
rule name permit_trust_dmz
source-zone trust
destination-zone dmz
source-address 23.1.1.0 mask 255.255.255.0
destination-address 19.16.1.0 mask 255.255.255.0
destination-address 20.16.1.0 mask 255.255.255.0
service ftp
service http
service icmp
action permit
#
return
注意:
交换机和路由器之间不用做trunk
只有交换机和交换机之间做trunk
交换机的g0/0/0是untrust区域
---恢复内容结束---
标签:source this mode ati def inter 交换机 security 访问
原文地址:https://www.cnblogs.com/mqqq/p/11430913.html