标签:cat img min 权限 ica ide logs ram imp
有几种方式其他的记不住了,这里把我常用的一种介绍一下。
shiro这个功能对应五张数据库表
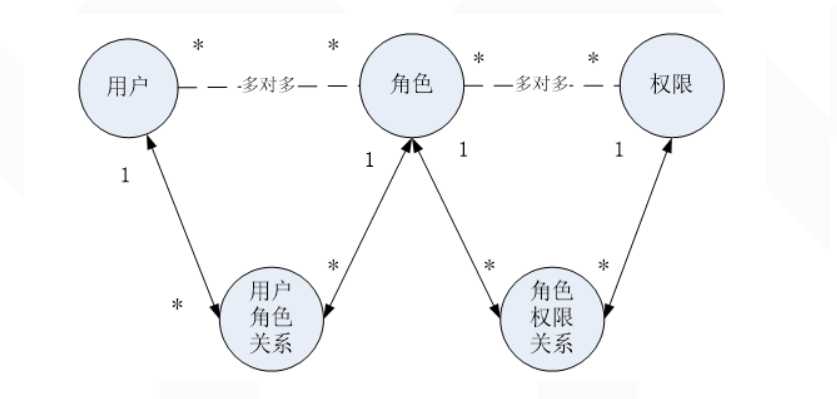
一个人可以有多个角色,一个角色可以有多个权限
先写一个配置文件
<?xml version="1.0" encoding="UTF-8"?> <beans xmlns="http://www.springframework.org/schema/beans" xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance" xsi:schemaLocation="http://www.springframework.org/schema/beans http://www.springframework.org/schema/beans/spring-beans.xsd"> <!-- 配置自定的Realm类 --> <bean id="myRealm" class="com.zhiyou.shiro.realm.MyRealm"/> <!-- 配置SecurityManager的bean --> <bean id="securityManager" class="org.apache.shiro.web.mgt.DefaultWebSecurityManager"> <property name="realm" ref="myRealm"/> </bean> <!-- 请求过滤器 id必须与web.xml文件中的过滤器名称相同 --> <bean id="shiroFilter" class="org.apache.shiro.spring.web.ShiroFilterFactoryBean"> <!-- 如果你的请求未login.html那么放行 --> <property name="loginUrl" value="/login.html"></property> <!-- 该过滤器与SecurityManager关联再一起 --> <property name="securityManager" ref="securityManager"></property> <!-- 如果没有权限则跳转到该页面 --> <property name="unauthorizedUrl" value="/403.html"></property> <!--设置规则 anno:允许匿名访问 authc: 需要认证才可以访问 --> <property name="filterChainDefinitions"> <value> /css/** = anon /images/** = anon /js/** = anon /user/login= anon /login.jsp=anon /**=authc </value> </property> </bean> </beans>
web.xml里面写一个过滤
<filter>
<filter-name>shiroFilter</filter-name>
<filter-class>org.springframework.web.filter.DelegatingFilterProxy</filter-class>
</filter>
<filter-mapping>
<filter-name>shiroFilter</filter-name>
<url-pattern>/*</url-pattern>
</filter-mapping>
jar包
<dependency>
<groupId>org.apache.shiro</groupId>
<artifactId>shiro-core</artifactId>
<version>1.4.0</version>
</dependency>
<dependency>
<groupId>org.apache.shiro</groupId>
<artifactId>shiro-web</artifactId>
<version>1.4.0</version>
</dependency>
<dependency>
<groupId>org.apache.shiro</groupId>
<artifactId>shiro-spring</artifactId>
<version>1.4.0</version>
</dependency>
封装一个验证权限的类
package com.zhiyou.shiro.realm; import org.apache.shiro.authc.AuthenticationException; import org.apache.shiro.authc.AuthenticationInfo; import org.apache.shiro.authc.AuthenticationToken; import org.apache.shiro.authc.SimpleAuthenticationInfo; import org.apache.shiro.authz.AuthorizationInfo; import org.apache.shiro.realm.AuthorizingRealm; import org.apache.shiro.subject.PrincipalCollection; import com.zhiyou.bean.User; public class MyRealm extends AuthorizingRealm{ @Override protected AuthorizationInfo doGetAuthorizationInfo(PrincipalCollection principals) { // TODO Auto-generated method stub return null; } @Override protected AuthenticationInfo doGetAuthenticationInfo(AuthenticationToken token) throws AuthenticationException { String username = token.getPrincipal().toString(); System.out.println("开始认正用户:"+username); //根据此账户查信息 User user=new User(1,"ss","123456"); SimpleAuthenticationInfo info=new SimpleAuthenticationInfo(username,user.getPassword(),getName()); return info; } }
有权限的功能的例子
package com.zhiyou.shiro.realm; import java.util.Arrays; import java.util.List; import org.apache.shiro.authc.AuthenticationException; import org.apache.shiro.authc.AuthenticationInfo; import org.apache.shiro.authc.AuthenticationToken; import org.apache.shiro.authc.SimpleAuthenticationInfo; import org.apache.shiro.authz.AuthorizationInfo; import org.apache.shiro.authz.SimpleAuthorizationInfo; import org.apache.shiro.realm.AuthorizingRealm; import org.apache.shiro.subject.PrincipalCollection; import com.zhiyou100.sh.bean.User; import com.zhiyou100.sh.bean.role; import com.zhiyou100.sh.dao.UserDao; public class MyRealm extends AuthorizingRealm{ UserDao userDao=new UserDao(); @Override protected AuthorizationInfo doGetAuthorizationInfo(PrincipalCollection principals) { System.out.println("开始授权"); String username = principals.toString(); System.out.println("要授权的姓名:"+username); //根据用户查询该用户具有的角色 List<role> list = userDao.findByname(username); System.out.println(list); if(list.size()==0) { return null;//该角色没有任何权限 } SimpleAuthorizationInfo info=new SimpleAuthorizationInfo(); for(role l:list) { System.out.println(l.getRname()+"dd"); info.addRole(l.getRname());//角色名添加到info里 //根据该角色查询相应的权限 if(l.getRname().equals("admin")) { info.addStringPermissions(Arrays.asList("user:create","user:delete")); } if(l.getRname().equals("manage")) { info.addStringPermissions(Arrays.asList("cc:create","user:delete")); } } return info; } @Override protected AuthenticationInfo doGetAuthenticationInfo(AuthenticationToken token) throws AuthenticationException { System.out.println("开始执行认证功能"); //获取你输入的账号 String username=(String) token.getPrincipal(); //根据该账号查询数据库。 User user = userDao.selectByname(username); if(user==null) { return null; //该账号对应的用户不存在。 } //principal账号 你输入的账号 //credentials:根据账号查询的密码 //realmName:随便给 但是再企业中习惯用 getName() //info:对象会帮你比较 密码是否一致 SimpleAuthenticationInfo info=new SimpleAuthenticationInfo(username, user.getPassword(), getName()); return info; } }
可以看看大佬的shiro的介绍
https://www.cnblogs.com/tony-hyn/p/11593241.html
标签:cat img min 权限 ica ide logs ram imp
原文地址:https://www.cnblogs.com/sh-0131/p/11743157.html