Looking into XSRF/CSRF Prevention in ASP.NET MVC and Web Pages it appears that you‘re either sending an incorrect __RequestVerificationToken parameter value or completely miss the step.
If the current HTTP request already contains an anti-XSRF session token (the anti-XSRF cookie __RequestVerificationToken), the security token is extracted from it. If the HTTP request does not contain an anti-XSRF session token or if extraction of the security token fails, a new random anti-XSRF token will be generated.
So your test should look like:
-
Open Login Page (HTTP Get Request)
-
Extract
__RequestVerificationTokendynamic parameter value using suitable JMeter PostProcessor, I would recommend going for CSS Selector Extractor, the configuration would be something like: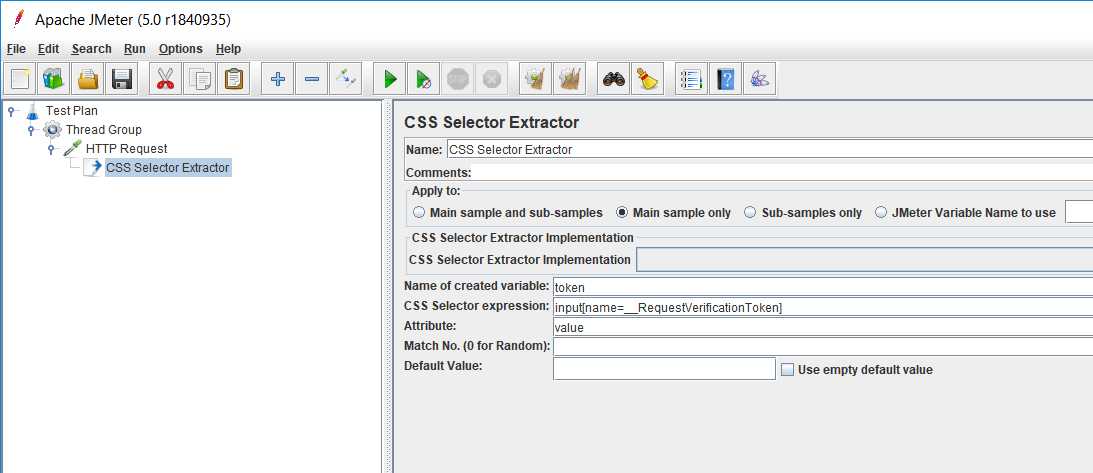
-
-
Once done you can refer the extracted value as
${token}in the next request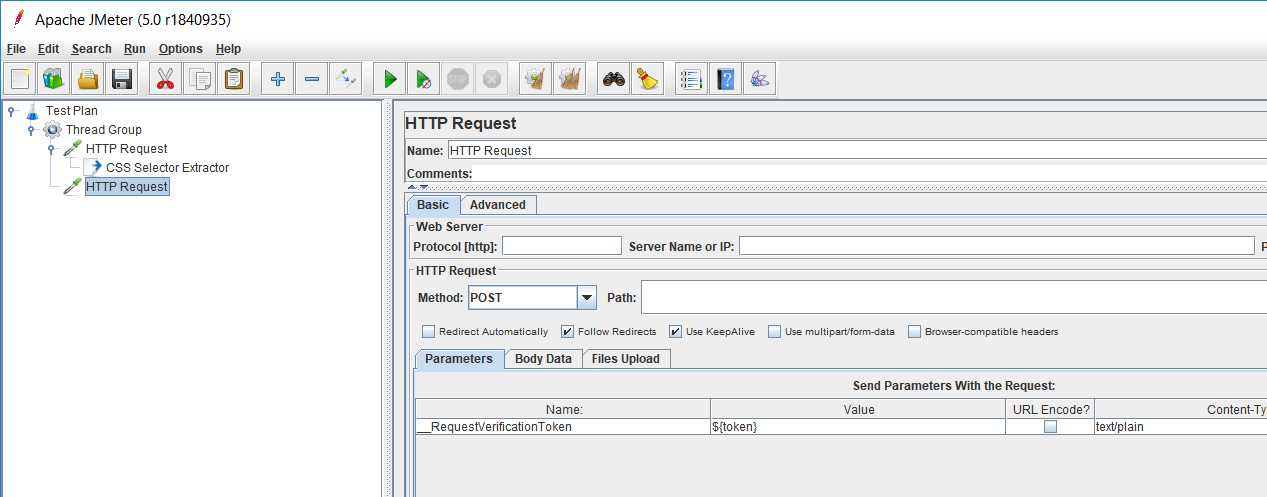
Check out ASP.NET Login Testing with JMeter article for more detailed information and step-by-step instructions if needed
