标签:show 图片 search form shell port sts ide func
获取dump的系统版本
root@kali:/test# volatility -f mem.dump imageinfo Volatility Foundation Volatility Framework 2.6 INFO : volatility.debug : Determining profile based on KDBG search... Suggested Profile(s) : Win7SP1x64, Win7SP0x64, Win2008R2SP0x64, Win2008R2SP1x64_23418, Win2008R2SP1x64, Win7SP1x64_23418 AS Layer1 : WindowsAMD64PagedMemory (Kernel AS) AS Layer2 : FileAddressSpace (/test/mem.dump) PAE type : No PAE DTB : 0x187000L KDBG : 0xf80003e02110L Number of Processors : 1 Image Type (Service Pack) : 1 KPCR for CPU 0 : 0xfffff80003e03d00L KUSER_SHARED_DATA : 0xfffff78000000000L Image date and time : 2019-11-13 08:39:44 UTC+0000 Image local date and time : 2019-11-13 16:39:44 +0800
列出进程
root@kali:/test# volatility -f mem.dump --profile=Win7SP1x64 pslist Volatility Foundation Volatility Framework 2.6 Offset(V) Name PID PPID Thds Hnds Sess Wow64 Start Exit ------------------ -------------------- ------ ------ ------ -------- ------ ------ ------------------------------ ----------- 0xfffffa800ccc1b10 System 4 0 88 534 ------ 0 2019-11-13 08:31:48 UTC+0000 0xfffffa800d2fbb10 smss.exe 252 4 2 29 ------ 0 2019-11-13 08:31:48 UTC+0000 0xfffffa800e2227e0 csrss.exe 344 328 9 400 0 0 2019-11-13 08:31:49 UTC+0000 0xfffffa800e3f3340 wininit.exe 396 328 3 79 0 0 2019-11-13 08:31:49 UTC+0000 0xfffffa800e3f77d0 csrss.exe 404 388 10 225 1 0 2019-11-13 08:31:49 UTC+0000 0xfffffa800e41fb10 winlogon.exe 444 388 3 111 1 0 2019-11-13 08:31:49 UTC+0000 0xfffffa800e457060 services.exe 500 396 8 210 0 0 2019-11-13 08:31:49 UTC+0000 0xfffffa800e426b10 lsass.exe 508 396 6 554 0 0 2019-11-13 08:31:49 UTC+0000 0xfffffa800e464060 lsm.exe 516 396 9 145 0 0 2019-11-13 08:31:49 UTC+0000 0xfffffa800e4f8b10 svchost.exe 608 500 10 351 0 0 2019-11-13 08:31:50 UTC+0000 0xfffffa800e52bb10 svchost.exe 684 500 8 273 0 0 2019-11-13 08:31:50 UTC+0000 0xfffffa800e570b10 svchost.exe 768 500 21 443 0 0 2019-11-13 08:31:50 UTC+0000 0xfffffa800e5b5b10 svchost.exe 816 500 16 381 0 0 2019-11-13 08:31:50 UTC+0000 0xfffffa800e5d7870 svchost.exe 860 500 18 666 0 0 2019-11-13 08:31:50 UTC+0000 0xfffffa800e5f8b10 svchost.exe 888 500 37 919 0 0 2019-11-13 08:31:50 UTC+0000 0xfffffa800e66c870 svchost.exe 1016 500 5 114 0 0 2019-11-13 08:31:50 UTC+0000 0xfffffa800e74fb10 svchost.exe 1032 500 15 364 0 0 2019-11-13 08:31:51 UTC+0000 0xfffffa800e510320 spoolsv.exe 1156 500 13 273 0 0 2019-11-13 08:31:51 UTC+0000 0xfffffa800e5b0060 svchost.exe 1184 500 11 194 0 0 2019-11-13 08:31:51 UTC+0000 0xfffffa800e56e060 svchost.exe 1276 500 10 155 0 0 2019-11-13 08:31:52 UTC+0000 0xfffffa800e685060 svchost.exe 1308 500 12 228 0 0 2019-11-13 08:31:52 UTC+0000 0xfffffa800e632060 svchost.exe 1380 500 4 167 0 0 2019-11-13 08:31:52 UTC+0000 0xfffffa800e692060 VGAuthService. 1480 500 4 94 0 0 2019-11-13 08:31:52 UTC+0000 0xfffffa800e7dab10 vmtoolsd.exe 1592 500 11 287 0 0 2019-11-13 08:31:52 UTC+0000 0xfffffa800e8a7720 svchost.exe 1824 500 6 92 0 0 2019-11-13 08:31:53 UTC+0000 0xfffffa800e898300 WmiPrvSE.exe 1980 608 10 203 0 0 2019-11-13 08:31:53 UTC+0000 0xfffffa800e8e9b10 dllhost.exe 2044 500 15 197 0 0 2019-11-13 08:31:53 UTC+0000 0xfffffa800e90d840 msdtc.exe 1320 500 14 152 0 0 2019-11-13 08:31:54 UTC+0000 0xfffffa800e991b10 taskhost.exe 2208 500 10 264 1 0 2019-11-13 08:31:56 UTC+0000 0xfffffa800e44a7a0 dwm.exe 2268 816 7 144 1 0 2019-11-13 08:31:57 UTC+0000 0xfffffa800e9b8b10 explorer.exe 2316 2260 25 699 1 0 2019-11-13 08:31:57 UTC+0000 0xfffffa800ea4f060 vm3dservice.ex 2472 2316 2 40 1 0 2019-11-13 08:31:57 UTC+0000 0xfffffa800ea54b10 vmtoolsd.exe 2480 2316 9 188 1 0 2019-11-13 08:31:57 UTC+0000 0xfffffa800ea9ab10 rundll32.exe 2968 2620 6 611 1 1 2019-11-13 08:32:02 UTC+0000 0xfffffa800e8b59c0 WmiPrvSE.exe 2764 608 11 316 0 0 2019-11-13 08:32:13 UTC+0000 0xfffffa800ea75b10 cmd.exe 2260 2316 1 20 1 0 2019-11-13 08:33:45 UTC+0000 0xfffffa800e687330 conhost.exe 2632 404 2 63 1 0 2019-11-13 08:33:45 UTC+0000 0xfffffa800e41db10 WmiApSrv.exe 2792 500 4 113 0 0 2019-11-13 08:34:27 UTC+0000 0xfffffa800ed68840 CnCrypt.exe 1608 2316 4 115 1 1 2019-11-13 08:34:40 UTC+0000 0xfffffa800e4a5b10 audiodg.exe 2100 768 6 130 0 0 2019-11-13 08:39:29 UTC+0000 0xfffffa800ea57b10 DumpIt.exe 1072 2316 1 26 1 1 2019-11-13 08:39:43 UTC+0000 0xfffffa800ea1c060 conhost.exe 2748 404 2 62 1 0 2019-11-13 08:39:43 UTC+0000 root@kali:/test#
常见的命令
Supported Plugin Commands: amcache Print AmCache information apihooks Detect API hooks in process and kernel memory atoms Print session and window station atom tables atomscan Pool scanner for atom tables auditpol Prints out the Audit Policies from HKLM\SECURITY\Policy\PolAdtEv bigpools Dump the big page pools using BigPagePoolScanner bioskbd Reads the keyboard buffer from Real Mode memory cachedump Dumps cached domain hashes from memory callbacks Print system-wide notification routines clipboard Extract the contents of the windows clipboard cmdline Display process command-line arguments cmdscan Extract command history by scanning for _COMMAND_HISTORY consoles Extract command history by scanning for _CONSOLE_INFORMATION crashinfo Dump crash-dump information deskscan Poolscaner for tagDESKTOP (desktops) devicetree Show device tree dlldump Dump DLLs from a process address space dlllist Print list of loaded dlls for each process driverirp Driver IRP hook detection drivermodule Associate driver objects to kernel modules driverscan Pool scanner for driver objects dumpcerts Dump RSA private and public SSL keys dumpfiles Extract memory mapped and cached files dumpregistry Dumps registry files out to disk editbox Displays information about Edit controls. (Listbox experimental.) envars Display process environment variables eventhooks Print details on windows event hooks filescan Pool scanner for file objects gahti Dump the USER handle type information gditimers Print installed GDI timers and callbacks getservicesids Get the names of services in the Registry and return Calculated SID getsids Print the SIDs owning each process handles Print list of open handles for each process hashdump Dumps passwords hashes (LM/NTLM) from memory hibinfo Dump hibernation file information hivedump Prints out a hive hivelist Print list of registry hives. hivescan Pool scanner for registry hives hpakextract Extract physical memory from an HPAK file hpakinfo Info on an HPAK file iehistory Reconstruct Internet Explorer cache / history imagecopy Copies a physical address space out as a raw DD image imageinfo Identify information for the image impscan Scan for calls to imported functions joblinks Print process job link information kdbgscan Search for and dump potential KDBG values kpcrscan Search for and dump potential KPCR values ldrmodules Detect unlinked DLLs lsadump Dump (decrypted) LSA secrets from the registry machoinfo Dump Mach-O file format information malfind Find hidden and injected code mbrparser Scans for and parses potential Master Boot Records (MBRs) memdump Dump the addressable memory for a process memmap Print the memory map messagehooks List desktop and thread window message hooks mftparser Scans for and parses potential MFT entries moddump Dump a kernel driver to an executable file sample modscan Pool scanner for kernel modules modules Print list of loaded modules multiscan Scan for various objects at once mutantscan Pool scanner for mutex objects netscan Scan a Vista (or later) image for connections and sockets objtypescan Scan for Windows object type objects patcher Patches memory based on page scans poolpeek Configurable pool scanner plugin pooltracker Show a summary of pool tag usage printkey Print a registry key, and its subkeys and values privs Display process privileges procdump Dump a process to an executable file sample pslist Print all running processes by following the EPROCESS lists psscan Pool scanner for process objects pstree Print process list as a tree psxview Find hidden processes with various process listings qemuinfo Dump Qemu information raw2dmp Converts a physical memory sample to a windbg crash dump screenshot Save a pseudo-screenshot based on GDI windows sessions List details on _MM_SESSION_SPACE (user logon sessions) shellbags Prints ShellBags info shimcache Parses the Application Compatibility Shim Cache registry key shutdowntime Print ShutdownTime of machine from registry ssdt Display SSDT entries strings Match physical offsets to virtual addresses (may take a while, VERY verbose) svcscan Scan for Windows services symlinkscan Pool scanner for symlink objects thrdscan Pool scanner for thread objects threads Investigate _ETHREAD and _KTHREADs timeliner Creates a timeline from various artifacts in memory timers Print kernel timers and associated module DPCs truecryptmaster Recover TrueCrypt 7.1a Master Keys truecryptpassphrase TrueCrypt Cached Passphrase Finder truecryptsummary TrueCrypt Summary unloadedmodules Print list of unloaded modules userassist Print userassist registry keys and information userhandles Dump the USER handle tables vaddump Dumps out the vad sections to a file vadinfo Dump the VAD info vadtree Walk the VAD tree and display in tree format vadwalk Walk the VAD tree vboxinfo Dump virtualbox information verinfo Prints out the version information from PE images vmwareinfo Dump VMware VMSS/VMSN information volshell Shell in the memory image windows Print Desktop Windows (verbose details) wintree Print Z-Order Desktop Windows Tree wndscan Pool scanner for window stations yarascan Scan process or kernel memory with Yara signatures
查看cmd历史记录
root@kali:/test# volatility -f mem.dump --profile=Win7SP1x64 cmdscan Volatility Foundation Volatility Framework 2.6 ************************************************** CommandProcess: conhost.exe Pid: 2632 CommandHistory: 0x242350 Application: cmd.exe Flags: Allocated, Reset CommandCount: 1 LastAdded: 0 LastDisplayed: 0 FirstCommand: 0 CommandCountMax: 50 ProcessHandle: 0x60 Cmd #0 @ 0x2229d0: flag.ccx_password_is_same_with_Administrator ************************************************** CommandProcess: conhost.exe Pid: 2748 CommandHistory: 0x2926d0 Application: DumpIt.exe Flags: Allocated CommandCount: 0 LastAdded: -1 LastDisplayed: -1 FirstCommand: 0 CommandCountMax: 50 ProcessHandle: 0x60
得知存在flag.ccx文件且密码和Administrator密码相同
查找flag文件
root@kali:/test# volatility -f mem.dump --profile=Win7SP1x64 filescan | grep flag Volatility Foundation Volatility Framework 2.6 0x000000003e435890 15 0 R--rw- \Device\HarddiskVolume2\Users\Administrator\Desktop\flag.ccx
得知flag文件地址为0x3e435890
dump目标文件(flag.ccx)
root@kali:/test# volatility -f mem.dump --profile=Win7SP1x64 dumpfiles -Q 0x3e435890 --dump-dir=./ Volatility Foundation Volatility Framework 2.6 DataSectionObject 0x3e435890 None \Device\HarddiskVolume2\Users\Administrator\Desktop\flag.ccx
寻找Administrator的密码
列出SAM表用户
root@kali:/test# volatility -f mem.dump --profile=Win7SP1x64 printkey -K "SAM\Domains\Account\Users\Names" Volatility Foundation Volatility Framework 2.6 Legend: (S) = Stable (V) = Volatile ---------------------------- Registry: \SystemRoot\System32\Config\SAM Key name: Names (S) Last updated: 2019-10-15 02:56:47 UTC+0000 Subkeys: (S) Administrator (S) Guest Values: REG_NONE : (S)
获取System和ASM的虚拟地址
root@kali:/test# volatility -f mem.dump --profile=Win7SP1x64 hivelist Volatility Foundation Volatility Framework 2.6 Virtual Physical Name ------------------ ------------------ ---- 0xfffff8a001cfd010 0x0000000039828010 \??\C:\Users\Administrator\AppData\Local\Microsoft\Windows\UsrClass.dat 0xfffff8a002fa2010 0x0000000013a3f010 \??\C:\System Volume Information\Syscache.hve 0xfffff8a00000f010 0x0000000023385010 [no name] 0xfffff8a000024010 0x0000000023510010 \REGISTRY\MACHINE\SYSTEM 0xfffff8a000064010 0x0000000023552010 \REGISTRY\MACHINE\HARDWARE 0xfffff8a0000e7410 0x0000000011bcc410 \??\C:\Windows\ServiceProfiles\NetworkService\NTUSER.DAT 0xfffff8a000100360 0x0000000015346360 \SystemRoot\System32\Config\SECURITY 0xfffff8a0003f4410 0x000000001527d410 \SystemRoot\System32\Config\DEFAULT 0xfffff8a0007ae010 0x000000001d867010 \Device\HarddiskVolume1\Boot\BCD 0xfffff8a0012d4010 0x000000001c938010 \SystemRoot\System32\Config\SOFTWARE 0xfffff8a001590010 0x000000001151a010 \SystemRoot\System32\Config\SAM 0xfffff8a0015ca010 0x00000000111a3010 \??\C:\Windows\ServiceProfiles\LocalService\NTUSER.DAT 0xfffff8a001c34010 0x0000000039803010 \??\C:\Users\Administrator\ntuser.dat
System:0xfffff8a000024010
ASM: 0xfffff8a001590010
hashdump获取用户密码的hash值
命令:volatility -f name --profile=WinXPSP2x86 hashdump -y (注册表 system 的 virtual 地址 )-s (SAM 的 virtual 地址)
root@kali:/test# volatility -f mem.dump --profile=Win7SP1x64 hashdump -y 0xfffff8a000024010 -s 0xfffff8a001590010 Volatility Foundation Volatility Framework 2.6 Administrator:500:6377a2fdb0151e35b75e0c8d76954a50:0d546438b1f4c396753b4fc8c8565d5b::: Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
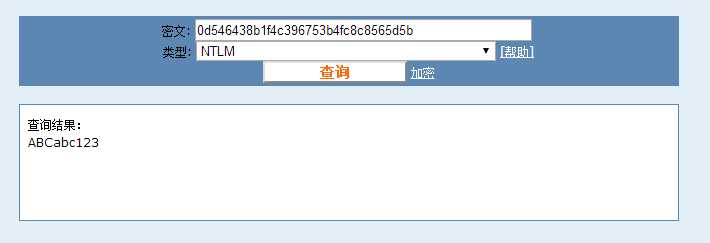
得知Administrator密码的hash值为0d546438b1f4c396753b4fc8c8565d5b
解码得到ABCabc123
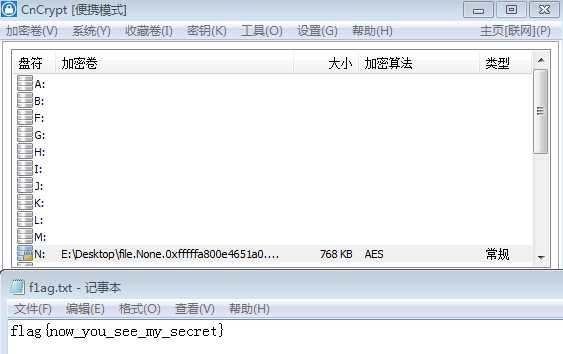
使用CnCrypt加载flag文件
题目地址:链接:https://pan.baidu.com/s/1WMyjP7E66fbT0KECBfAAig 提取码:a1nm
参考:https://www.52pojie.cn/thread-1079259-1-1.html
标签:show 图片 search form shell port sts ide func
原文地址:https://www.cnblogs.com/luocodes/p/12128880.html