标签:user each awl security cat ram int ORC 图片
Security policies:
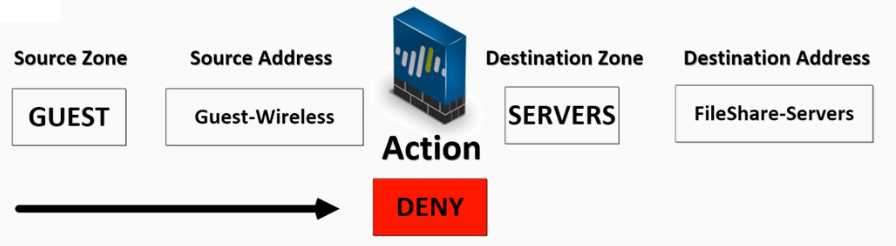
(From Packt)
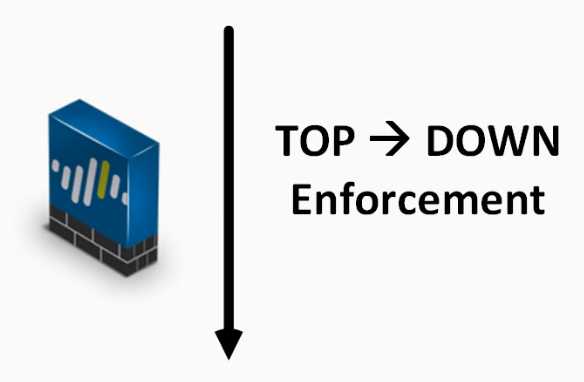
Task 1
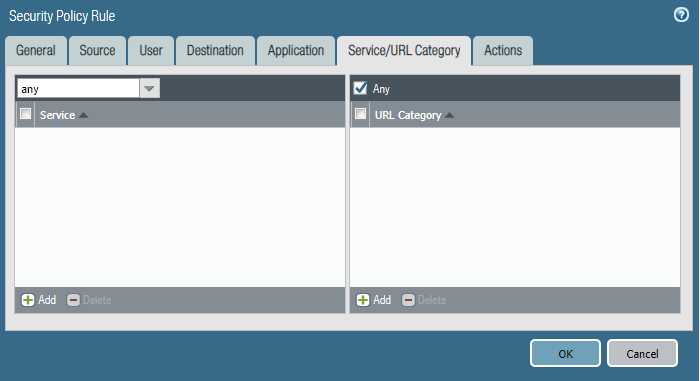
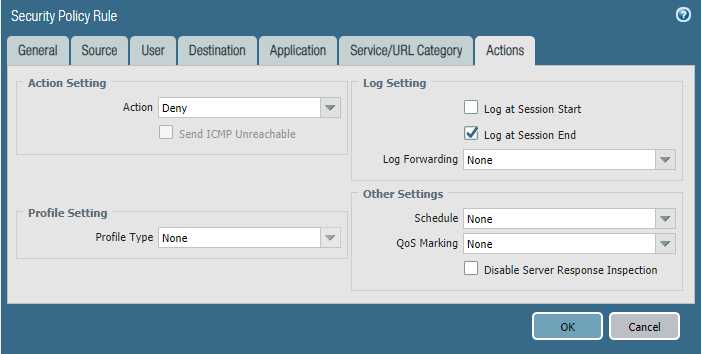
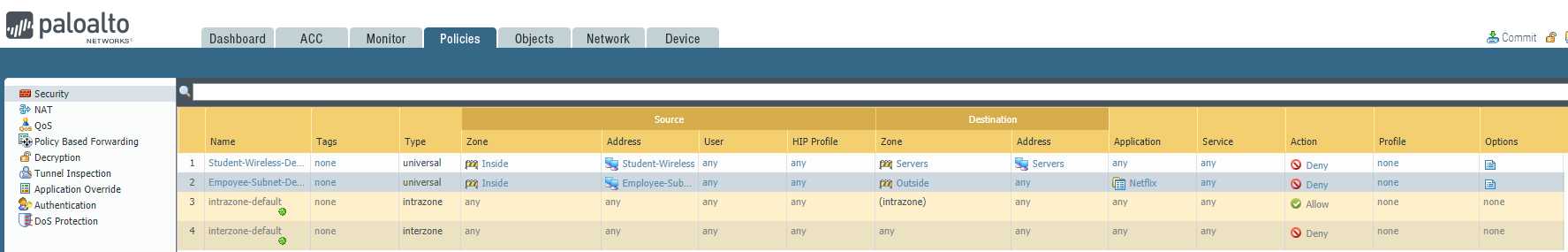
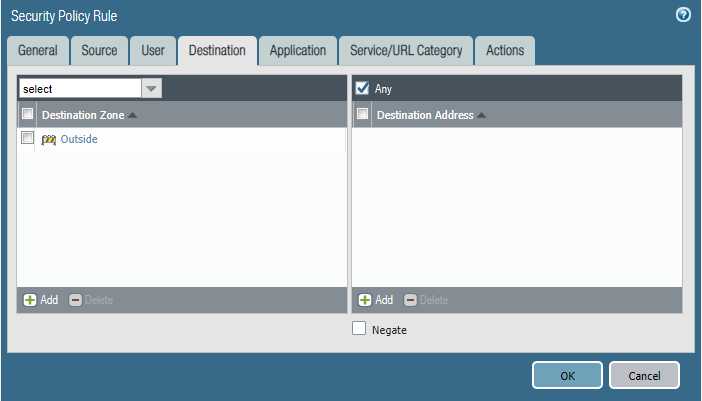
Please block the student wireless network from reaching the server subnet.
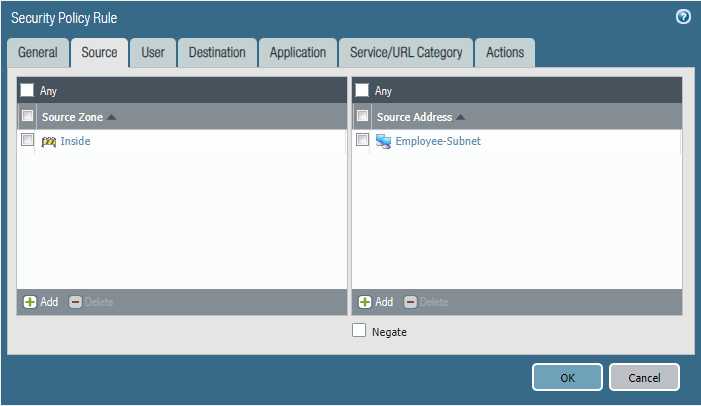
Source Zone Source Address Student Wireless: 10.10.0.0/22 Server Subnet: 10.30.0.0/23 Destination Zone Destination Address
Configure the firewall policy.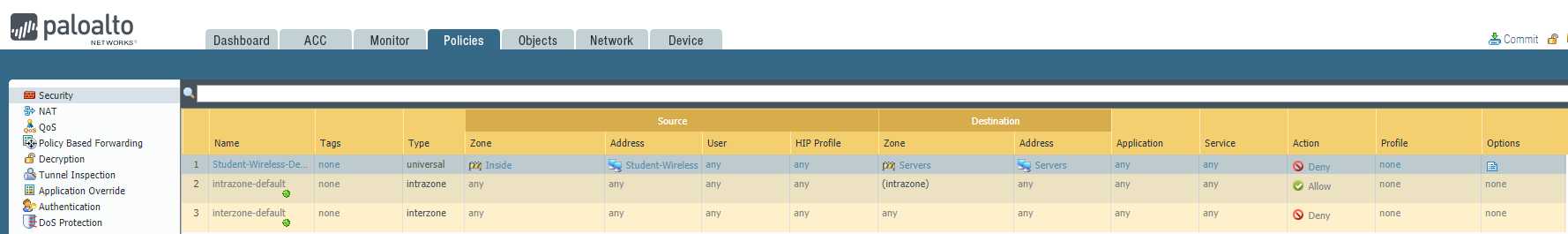
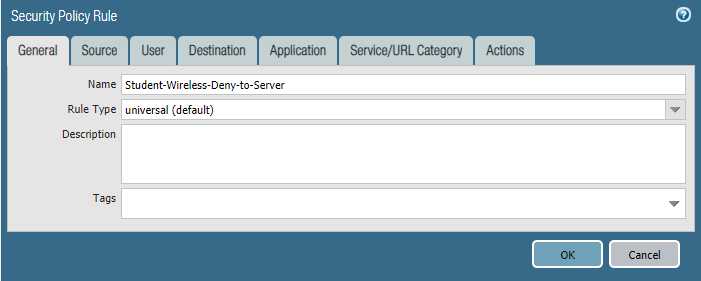
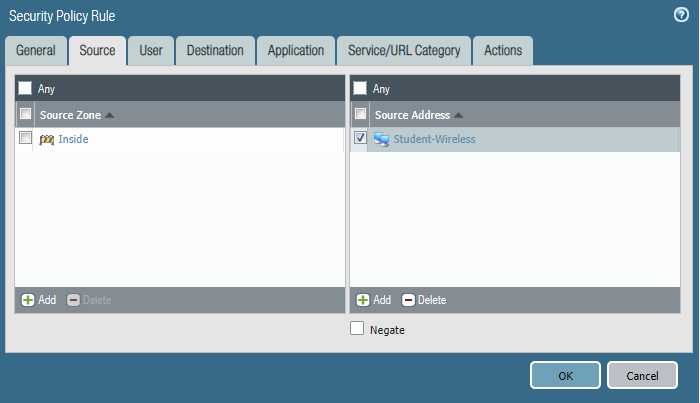
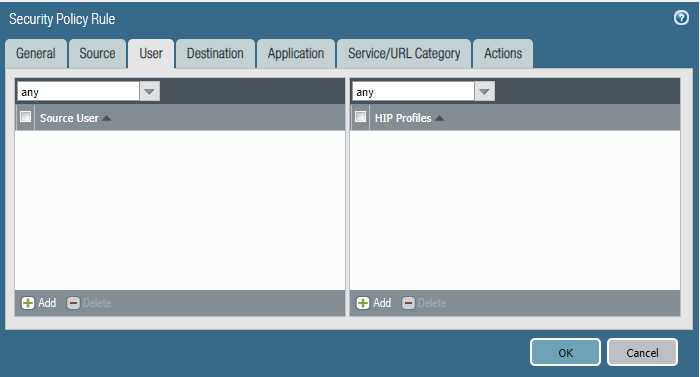
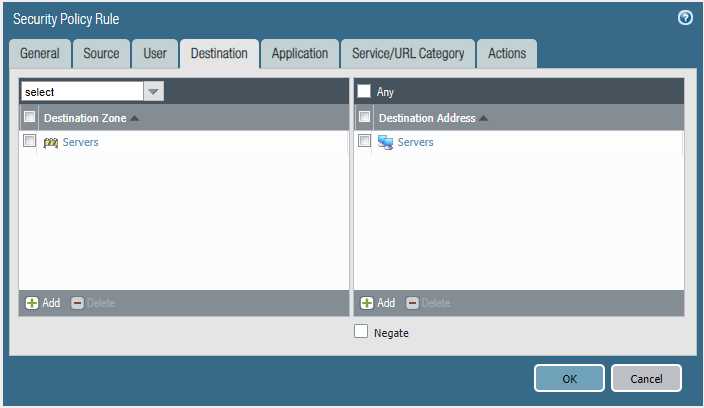
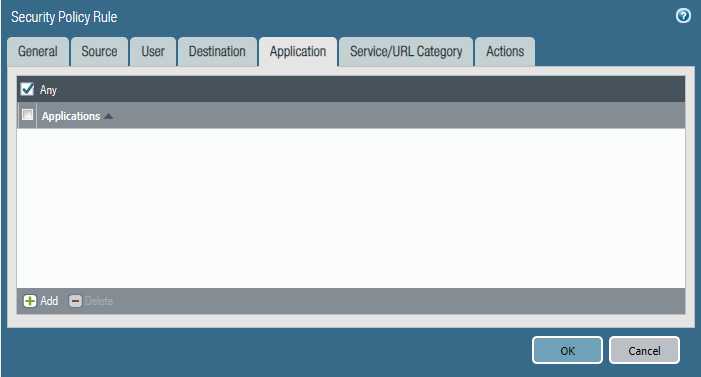
Task 2
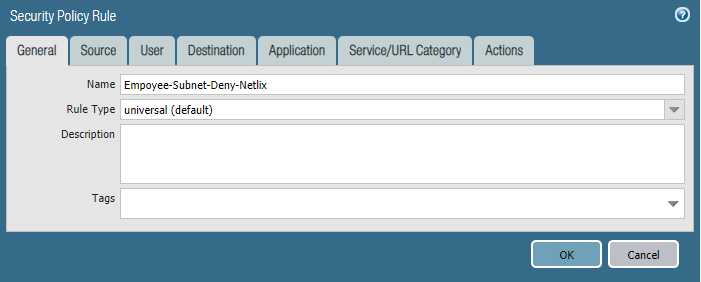
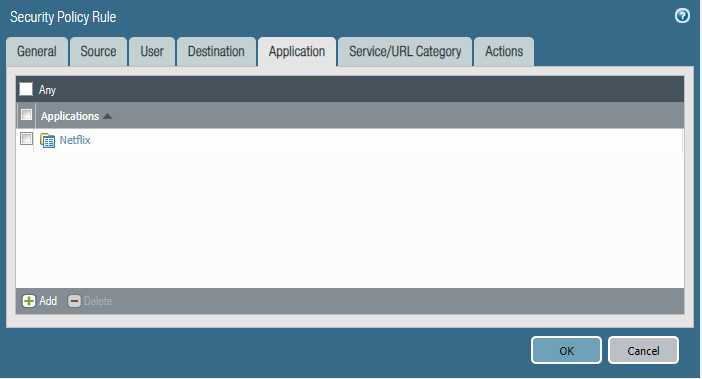
We are getting complaints of employees watching Netflix during work hours and it‘s causing our internet connection to crawl.
- Please block the employee subnet 10.25.0.0/23 from accessing Netflix.
Configure the firewall policy.
Cyber Security - Palo Alto Security Policies(1)
标签:user each awl security cat ram int ORC 图片
原文地址:https://www.cnblogs.com/keepmoving1113/p/12496683.html