标签:这一 extends ever 图片 文件 action 查看 val ges
https://buuoj.cn/challenges#findit
一开始尝试用dex2jar生成jar然后用JD-GUI反编译查看,找到MainActivity.class代码如下:
package com.example.findit;
import android.os.Bundle;
import android.support.v7.app.ActionBarActivity;
import android.view.MenuItem;
import android.view.View;
import android.widget.Button;
import android.widget.EditText;
import android.widget.TextView;
public class MainActivity extends ActionBarActivity {
protected void onCreate(Bundle paramBundle) {
super.onCreate(paramBundle);
setContentView(2130903064);
Button button = (Button)findViewById(2131034173);
final EditText edit = (EditText)findViewById(2131034174);
final TextView text = (TextView)findViewById(2131034175);
button.setOnClickListener(new View.OnClickListener() {
public void onClick(View param1View) {
char[] arrayOfChar1 = new char[17];
char[] arrayOfChar2 = new char[38];
int i = 0;
while (true) {
String str;
if (i >= 17) {
if (String.valueOf(arrayOfChar1).equals(edit.getText().toString())) {
for (i = 0;; i++) {
if (i >= 38) {
str = String.valueOf(arrayOfChar2);
text.setText(str);
return;
}
if ((b[i] >= ‘A‘ && b[i] <= ‘Z‘) || (b[i] >= ‘a‘ && b[i] <= ‘z‘)) {
arrayOfChar2[i] = (char)(b[i] + 16);
if ((arrayOfChar2[i] > ‘Z‘ && arrayOfChar2[i] < ‘a‘) || arrayOfChar2[i] >= ‘z‘)
arrayOfChar2[i] = (char)(arrayOfChar2[i] - 26);
} else {
arrayOfChar2[i] = b[i];
}
}
break;
}
} else {
if ((a[i] < ‘I‘ && a[i] >= ‘A‘) || (a[i] < ‘i‘ && a[i] >= ‘a‘)) {
str[i] = (char)(a[i] + 18);
} else if ((a[i] >= ‘A‘ && a[i] <= ‘Z‘) || (a[i] >= ‘a‘ && a[i] <= ‘z‘)) {
str[i] = (char)(a[i] - 8);
} else {
str[i] = a[i];
}
i++;
continue;
}
text.setText(");
return;
}
}
});
}
public boolean onOptionsItemSelected(MenuItem paramMenuItem) {
return (paramMenuItem.getItemId() == 2131034176) ? true : super.onOptionsItemSelected(paramMenuItem);
}
}
发现找不到数组a和b的定义,比较懵。然后尝试了第二种反编译方法,即使用apktool.jar,这一次能将xml的乱码消除,并且产生了很多.smali文件,还是不太懂,遂去查wp,发现用APKIDE直接打开就行。
查看MainActivity.smali,发现一些16进制数,联想到刚刚看到的数组a和b
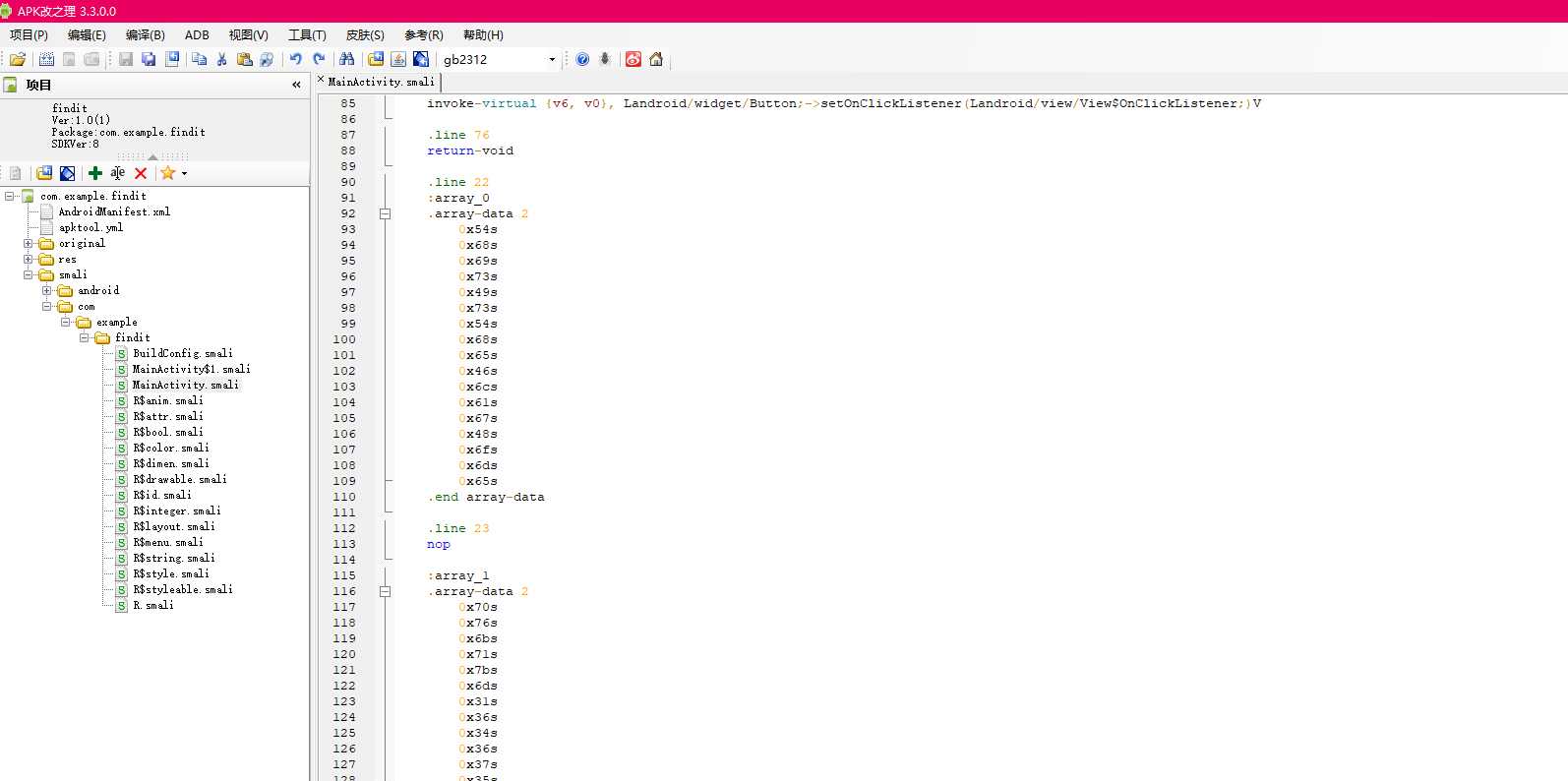
复制这俩数组的数,写脚本转成ascii码
# -*- coding: utf-8 -*-
# @Time : 2020/4/6 22:27
# @Author : 20181218-sl
# @Email : 1743207528@qq.com
# @File : findit.py
# @Software: PyCharm
a="""
0x54s
0x68s
0x69s
0x73s
0x49s
0x73s
0x54s
0x68s
0x65s
0x46s
0x6cs
0x61s
0x67s
0x48s
0x6fs
0x6ds
0x65s
0x70s
0x76s
0x6bs
0x71s
0x7bs
0x6ds
0x31s
0x36s
0x34s
0x36s
0x37s
0x35s
0x32s
0x36s
0x32s
0x30s
0x33s
0x33s
0x6cs
0x34s
0x6ds
0x34s
0x39s
0x6cs
0x6es
0x70s
0x37s
0x70s
0x39s
0x6ds
0x6es
0x6bs
0x32s
0x38s
0x6bs
0x37s
0x35s
0x7ds
"""
a = a.replace(‘ ‘,‘‘)
a = a.replace(‘\n‘,‘‘)
l = a.split(‘s‘)
del l[-1]
for c in l:
print(chr(int(c,16)),end=‘‘)
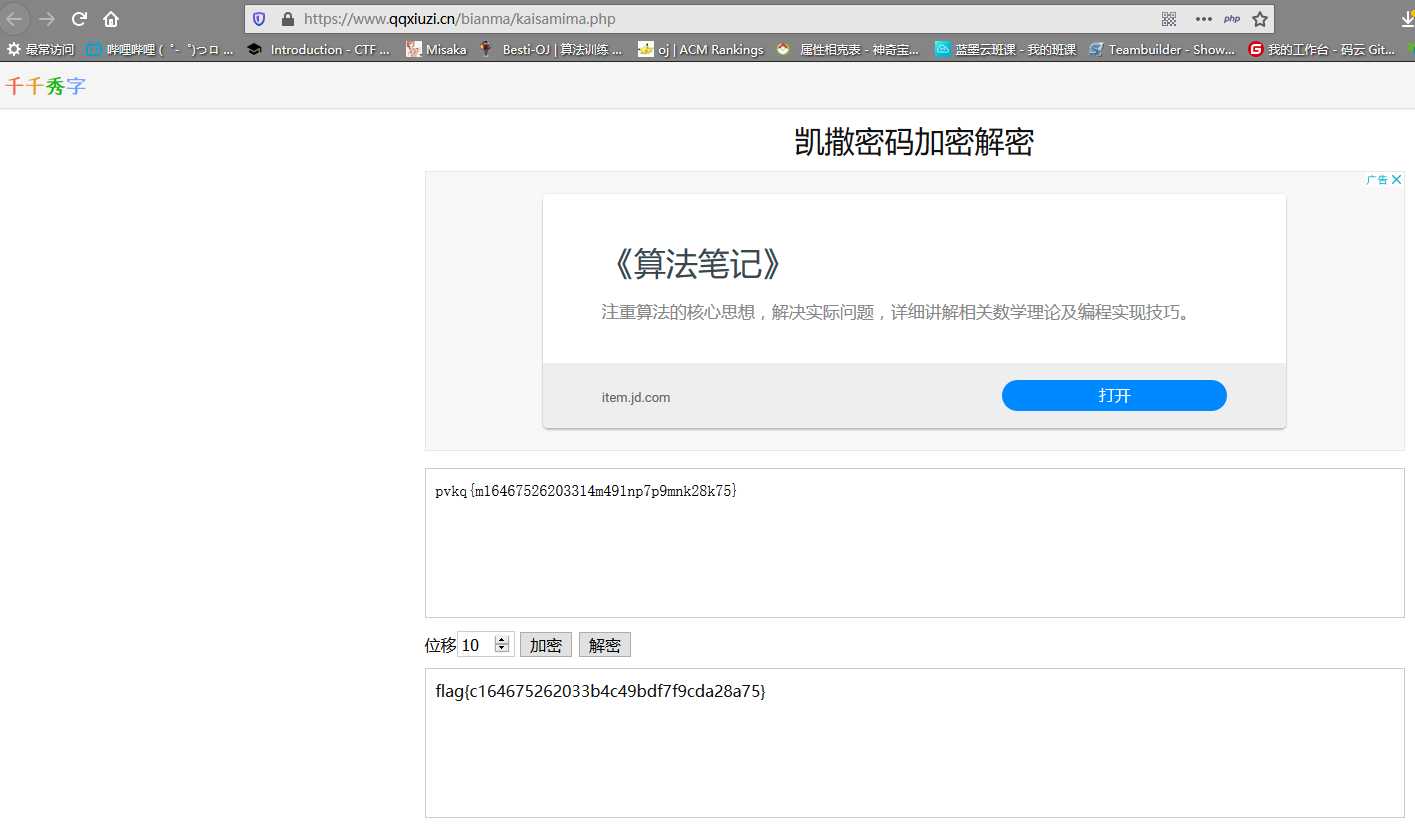
跑完脚本得到的后部分用恺撒加密进行解密,试试位移,为10时解密出flag。
apk反编译工具可以参考Android反编译apk逆向分析
BUUCTF Reverse helloword、findit
标签:这一 extends ever 图片 文件 action 查看 val ges
原文地址:https://www.cnblogs.com/hardcoreYutian/p/12650328.html