标签:process append adb activity 安卓 col 技术 decrypt bad
国外比赛,做着玩
官方wp:https://github.com/tghack/tg20hack
RE1:
Game of Keys
题目提供了两个文件,一个PYC文件,一个wordlist.txt
在线pyc反编译:http://tools.bugscaner.com/decompyle/
import base64 from itertools import cycle class myGame: def __init__(self, xdim=4, ydim=4): self.x = xdim self.y = ydim self.matrix = [] for i in range(self.x): row = [] for j in range(self.y): row.append(0) self.matrix.append(row) def make_keys(self, *args, **kwargs): words = [] with open(‘wordlist.txt‘) as (f): for line in f: words.append(line.strip()) for i in range(self.x): for j in range(self.y): self.matrix[j][i] = words[i + j] keyArray = [] keyArray.append(self.matrix[args[0]][args[1]]) keyArray.append(self.matrix[args[2]][args[3]]) key = ‘‘ for k in keyArray: key = key.strip() + str(k).strip() print(key) return key def checkdata(self, key): f = base64.b64decode(‘NSYDUhoVWQ8SQVcOAAYRFQkORA4FQVMDQQ5fQhUEWUYMDl4MHA==‘) data = f.decode(‘ascii‘) c = ‘‘.join((chr(ord(c) ^ ord(k)) for c, k in zip(data, cycle(key)))) print(‘%s ^ %s = %s‘ % (data, key, c)) if __name__ == ‘__main__‘: mgame = myGame(25, 25) x = input(‘input a number: ‘) y = input(‘input a number: ‘) x1 = input(‘input a number: ‘) y1 = input(‘input a number: ‘) data = mgame.make_keys(int(x), int(y), int(x1), int(y1)) mgame.checkdata(data)
大意就是输入数字,生成key,再生成flag字符串,爆破即可:
import base64 from itertools import cycle words = [] class myGame: def __init__(self, xdim=4, ydim=4): self.x = xdim self.y = ydim self.matrix = [] for i in range(self.x): row = [] for j in range(self.y): row.append(0) self.matrix.append(row) def make_keys(self, *args, **kwargs): global words for i in range(self.x): for j in range(self.y): self.matrix[j][i] = words[i + j] keyArray = [] keyArray.append(self.matrix[args[0]][args[1]]) keyArray.append(self.matrix[args[2]][args[3]]) key = ‘‘ for k in keyArray: key = key.strip() + str(k).strip() #print(key) return key def checkdata(self, key,f): data = f.decode(‘ascii‘) c = ‘‘.join((chr(ord(c) ^ ord(k)) for c, k in zip(data, cycle(key)))) #print(‘%s ^ %s = %s‘ % (data, key, c)) if(c[0:4]==‘TG20‘): print c return c def makeWord(): words = [] with open(‘wordlist.txt‘) as (f): for line in f: words.append(line.strip()) return words if __name__ == ‘__main__‘: mgame = myGame(25, 25) f = base64.b64decode(‘NSYDUhoVWQ8SQVcOAAYRFQkORA4FQVMDQQ5fQhUEWUYMDl4MHA==‘) fp = open(‘flag.txt‘,‘w‘) words = makeWord() for i in range(0,24): for j in range(0,24): for k in range(0,24): for l in range(0,24): data = mgame.make_keys(int(i), int(j), int(k), int(l)) tmp = mgame.checkdata(data,f) if(tmp[0:4]==‘TG20‘): fp.write(tmp+‘\n‘) fp.close()
最后拿到flag:
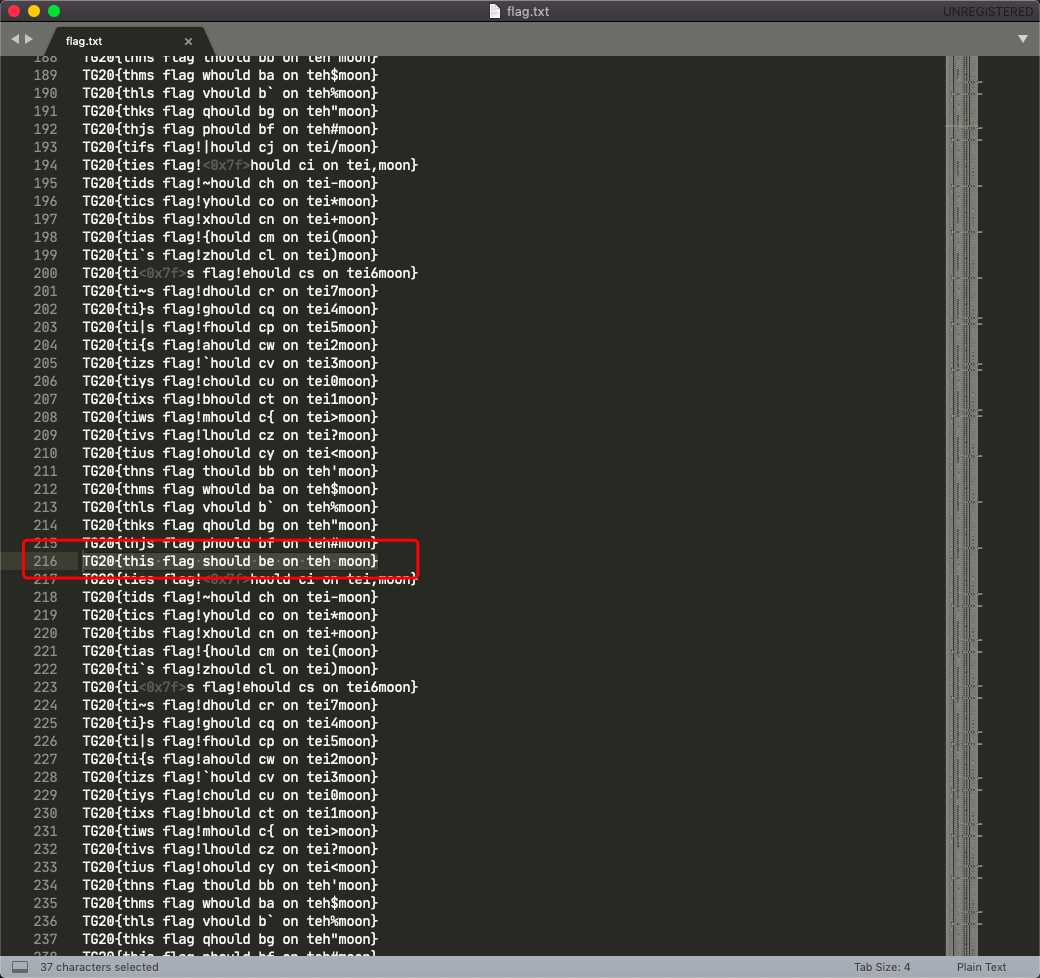
这里之前我还以为是the 交了之后没交上,直接用这个交,就对了。
RE2:Bad intentions
描述:Someone found this very old game lying around. Apparently there is an extremely funny joke in there somewhere.
Hint:Random title?
是一个安卓小游戏,界面:
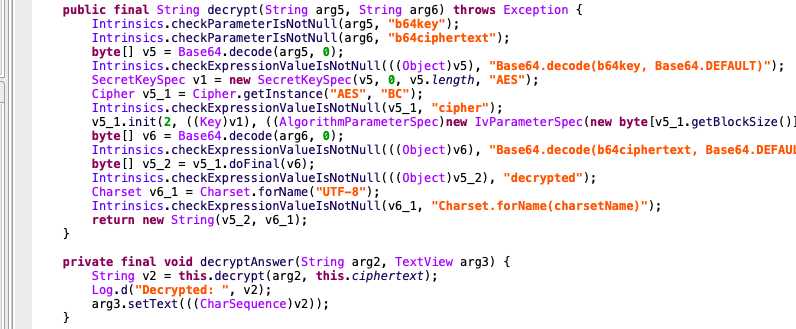
JEB反编译,根据题目,找到一个JokeActivity
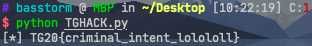
用ADB启动,上Frida拿flag:
adb shell am start -W -n no.tghack.gaiainvaders/.JokeActivity
frida脚本:
import frida, sys source = """ Java.perform(function() { var clazz = Java.use(‘no.tghack.gaiainvaders.JokeActivity‘); clazz.decrypt.implementation = function() { var flag = clazz.decrypt.apply(this,arguments); send(flag); return flag; } }); """ def on_message(message, data): if message[‘type‘] == ‘send‘: print("[*] {0}".format(message[‘payload‘])) else: print(message) process = frida.get_usb_device().attach(‘no.tghack.gaiainvaders‘) script = process.create_script(source) script.on(‘message‘, on_message) script.load() sys.stdin.read()
RE3:Chuck Norris
描述:
Ha-ha! Did you like the joke from the previous challenge? Here, have another one:
Chuck Norris once won a game of Space Invaders without shooting.
这道题目的文件和第二题是一样的
JEB中查看到关键点:
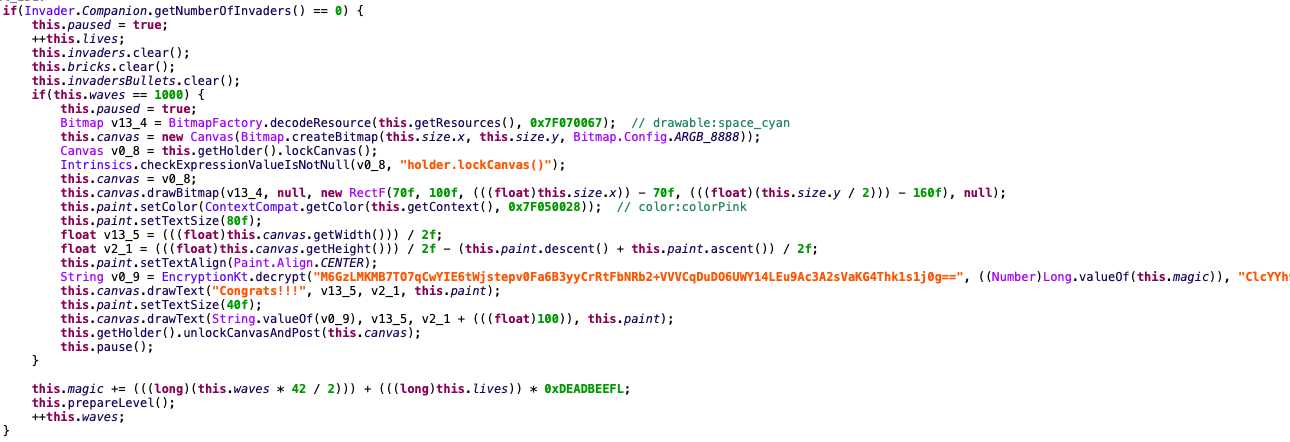
一样的,HOOK:
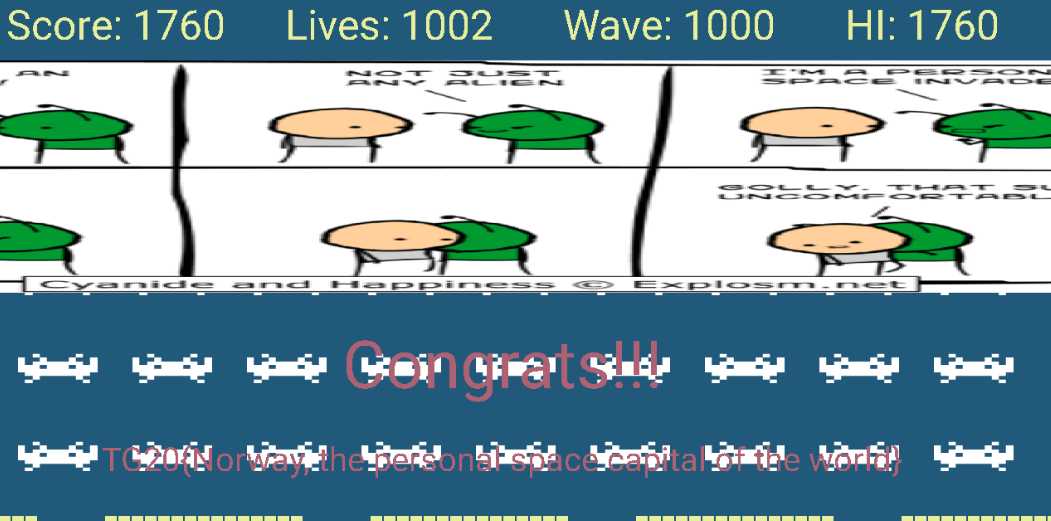
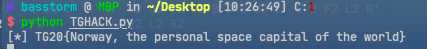
frida脚本:
import frida, sys source = """ Java.perform(function() { var clazz = Java.use(‘no.tghack.gaiainvaders.Invader$Companion‘); clazz.getNumberOfInvaders.implementation = function() { return 0; } var clazzz = Java.use(‘no.tghack.gaiainvaders.EncryptionKt‘); clazzz.decrypt.implementation = function() { var flag = clazzz.decrypt.apply(this,arguments); send(flag); return flag; } }); """ def on_message(message, data): if message[‘type‘] == ‘send‘: print("[*] {0}".format(message[‘payload‘])) else: print(message) process = frida.get_usb_device().attach(‘no.tghack.gaiainvaders‘) script = process.create_script(source) script.on(‘message‘, on_message) script.load() sys.stdin.read()
MISC1:s2s messaging
描述:
Intercepted ship to ship communication. Can you find the message?
Hint:MQTT
流量分析题,提示了MQTT协议
wireshark过滤MQTT:
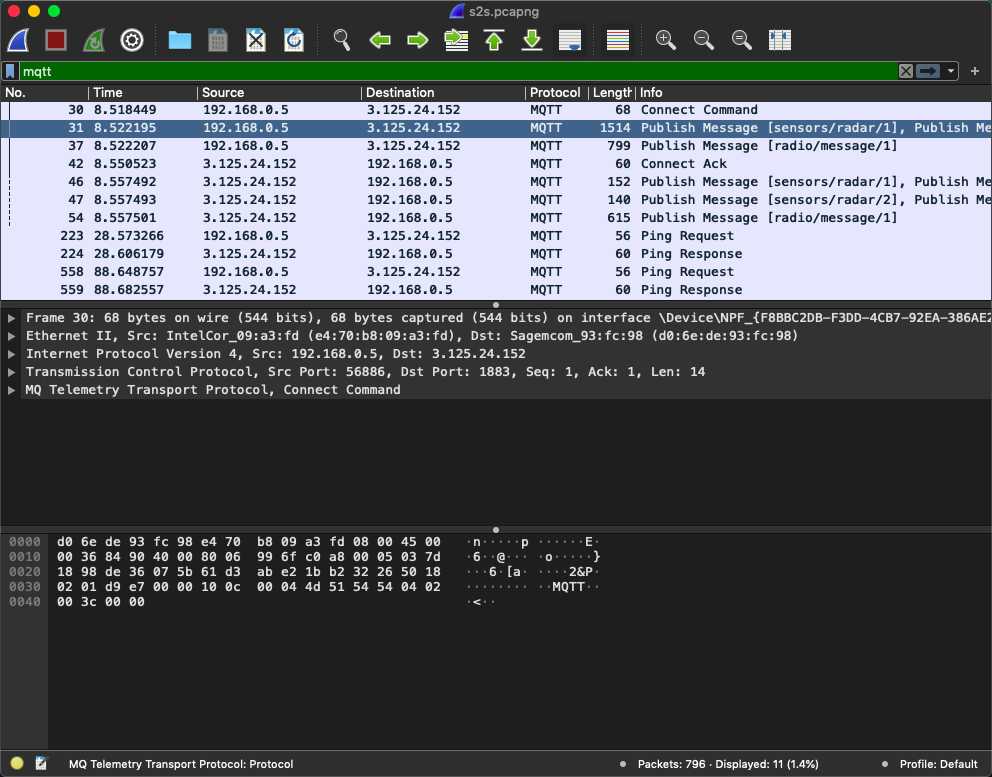
追踪TCP流:
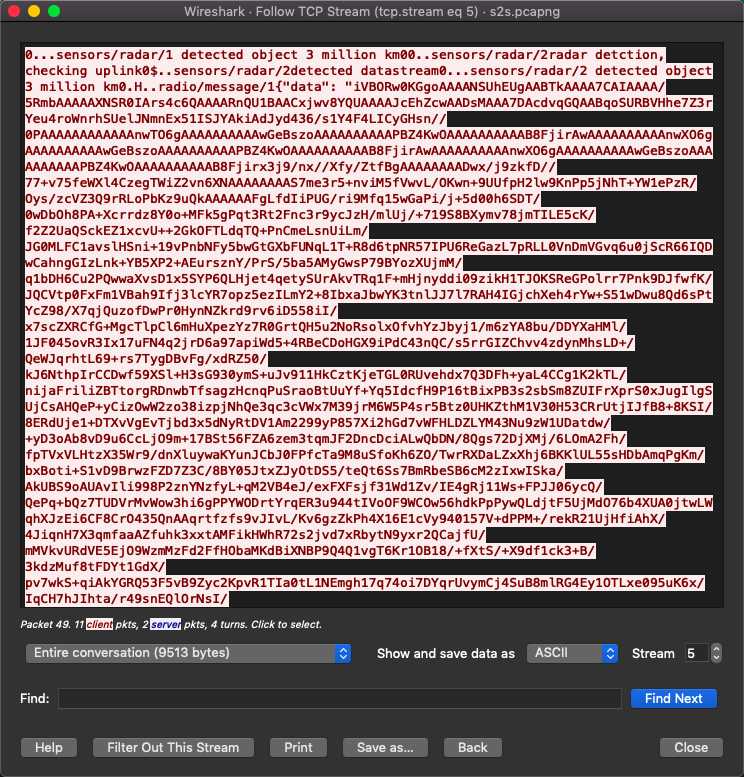
提取json格式的data,base64解密后发现png头:
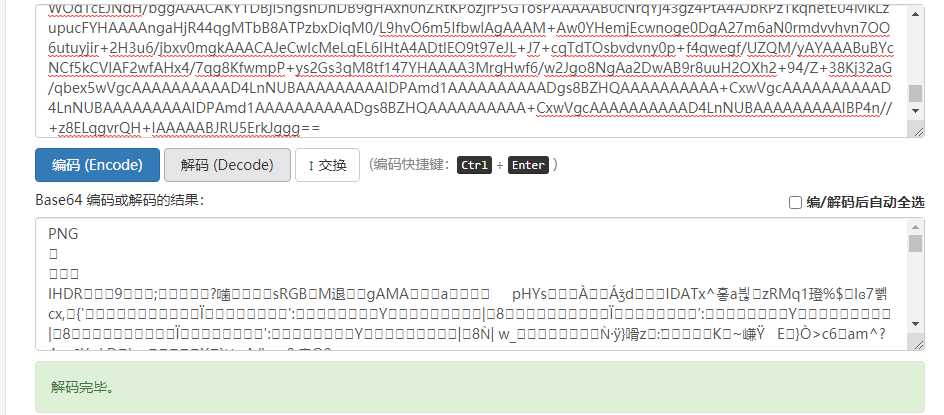
python解码:
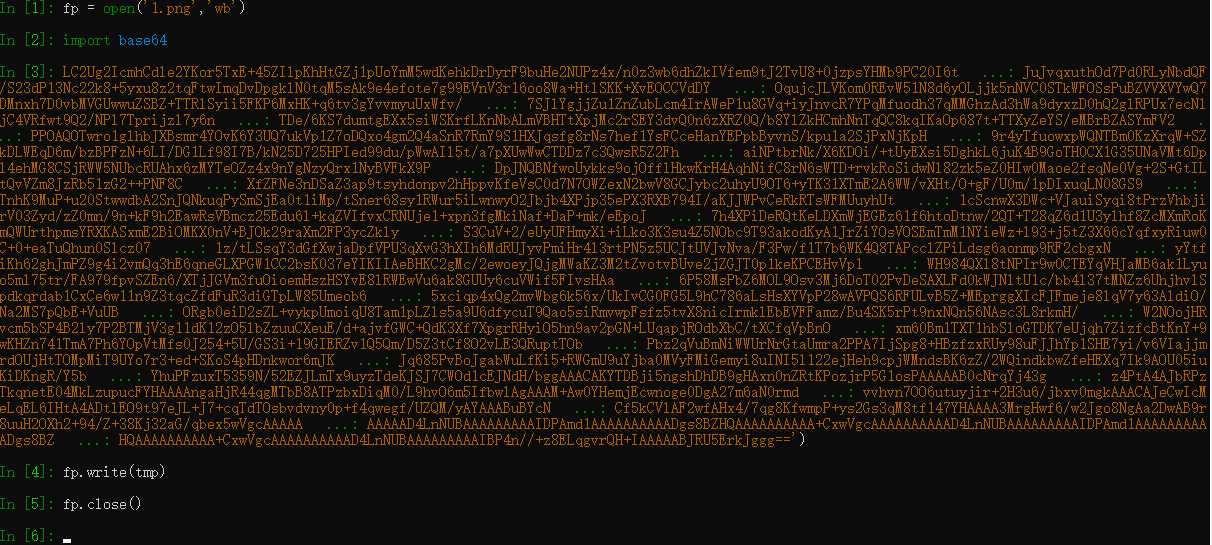
查看图片获得flag:
MISC:.-.-.- .-.-.- .-.-.-
题目描述:
.---$‘4c 53 41 74 4c 53 34 67 4c 69 34 74 4c 53 30 67 4c 53 30 74 4c 53 30 67 65 79 34 74 4c 53 41 75 49 43 38 67‘-------------------------| /-$‘76 49 43 34 67 4c 69 34 75 49 43 30 74 4c 53 41 76 49 43 34 75 49 43 30 75 49 43 38 67 4c 53 30 74 49 43 34 75 4c 53 41 75 4c 53‘--\ | | | _________ | || | ______ | || | | || | ____ ____ | || | __ | || | ______ | || | ___ ____ | | | | | _ _ | | || | .‘ ___ | | || | | || | |_ || _| | || | / \ | || | .‘ ___ | | || | |_ ||_ _| | | | | |_/ | | \_| | || | / .‘ \_| | || | ______ | || | | |__| | | || | / /\ \ | || | / .‘ \_| | || | | |_/ / | | | | | | | || | | | ____ | || | |______| | || | | __ | | || | / ____ \ | || | | | | || | | __‘. | | | | _| |_ | || | \ `.___] _| | || | | || | _| | | |_ | || | _/ / \ \_ | || | \ `.___.‘\ | || | _| | \ \_ | | | | |_____| | || | `._____.‘ | || | | || | |____||____| | || ||____| |____|| || | `._____.‘ | || | |____||____| | | | | | || | | || | | || | | || | | || | | || | | | | | &-‘d3 d3 14 94 93 24 96 c4 76 43 35 c4 57 43 34 94 57 43 34 94 57 43 35 c4 57 14 97 c4 76 43‘$---------------------------------------/ | \-‘14 96 c4 76 03 35 c4 76 03 35 c4 47 14 96 c4 57 43 34 94 67 14 96 c4 57 03 34 94 57 14 96 c4 57 03 34 94 57 14 96 c4 76 43 35 c4‘$----/
.---$和
&-‘可以想到,这是asciidot
在线跑一下:
https://asciidots.herokuapp.com/index.html
HEX2ASCII后拿到:LSAtLS4gLi4tLS0gLS0tLS0gey4tLSAuIC8gLS4gLiAuIC0uLiAuIC0uLiAvIC4uLiAtLS0gLS0gLiAvIC4gLi4uIC0tLSAvIC4uIC0uIC8gLS0tIC4uLSAuLS4gLyAuLS4uIC4uIC4uLS4gLiB9IA==
base64解码:- --. ..--- ----- {.-- . / -. . . -.. . -.. / ... --- -- . / . ... --- / .. -. / --- ..- .-. / .-.. .. ..-. . }
摩丝解密:
TG20WENEEDEDSOMEESOINOURLIFE配合base64解码后的{}
得到:TG20{WE NEED SOME ESO IN OUR LIFE}
MISC:poke
拿到题目是一个很长的未知图腾:
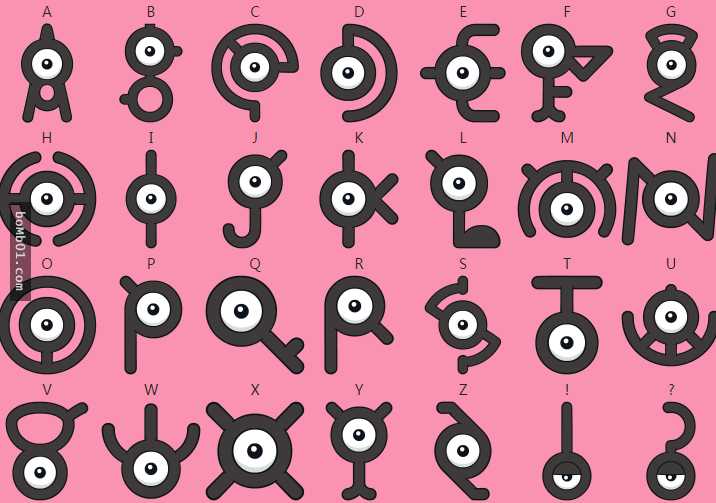
解出是:remember to examine the
binwalk:
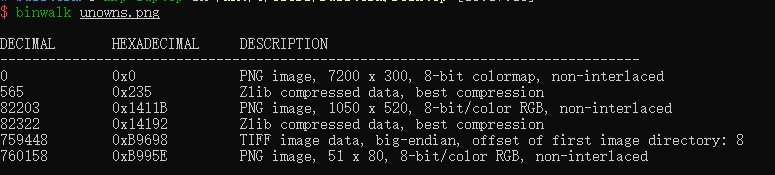
分离后:

拿到个这样的图片和另一张:
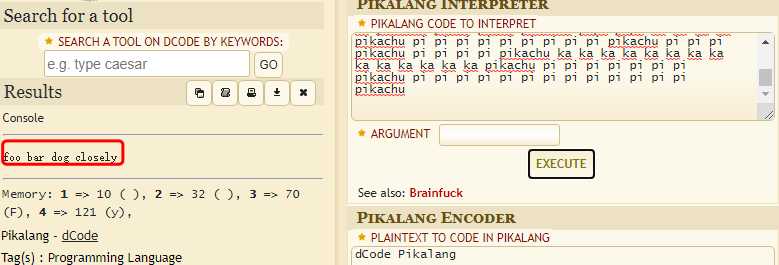
想到了pikalang:
https://www.dcode.fr/pikalang-language
这个图里可以分离到压缩包:
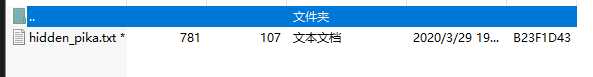
有密码,密码在另一张图的LSB里,使用zsteg:
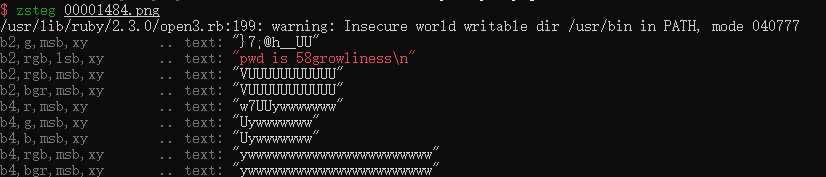
拿到密码,解开:
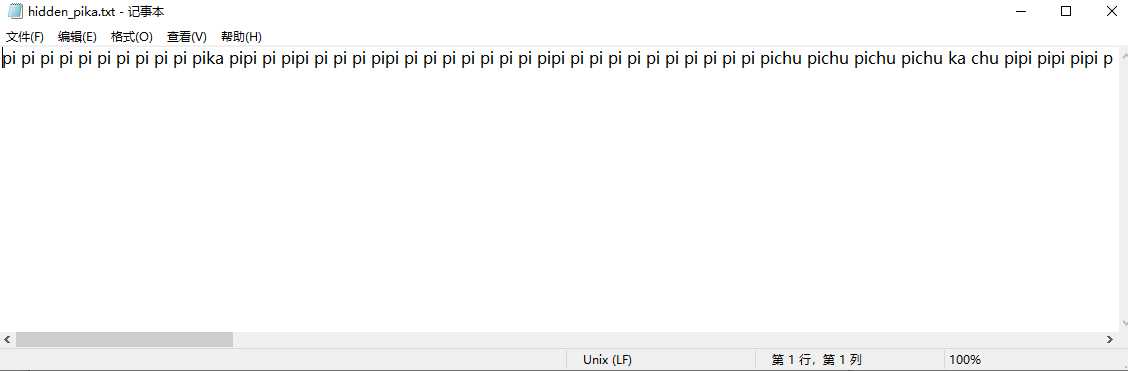
这就是那张图的文本。
解码后:
结合之前位置图腾解出来的:remember to examine the
答案就是 TG20{remember to examine the foo bar dog closely}
misc:cubiksrube
这道题目是看了nepnep的nop的题解:
题目描述:
_sa
l{l
2ii
sG_ atu bpn o_u
Rre oh_ mir _re
yng o‘g Tc} dil
y0k
etb
co_
Oh, and take this! It might help you.
R‘ F2 L2 B2 U‘ B U‘ L R‘
B D‘ U D L‘ L‘ L‘ L2 U F2 U‘ U D2 F‘ R‘ B‘ B D2 L2 B2 F‘ D‘ R‘ L2 L‘ U‘ U‘ R D L2 D R B‘ F‘ U R2 R F L U‘
这是三阶魔方六面公式,可以写暴力拧魔方脚本,脚本也是nop的,这里改了拧的过程,反着拧
就是U‘ 变成 U U U
U U U变成U‘
再从后往前拧:
u = [[‘_‘,‘s‘,‘a‘], [‘l‘,‘{‘,‘l‘], [‘2‘,"i",‘i‘]] f = [[‘a‘,‘t‘,‘u‘], [‘o‘,‘h‘,‘_‘], [‘o‘,"‘",‘g‘]] d = [[‘y‘,‘0‘,‘k‘], [‘e‘,‘t‘,‘b‘], [‘c‘,"o",‘_‘]] b = [[‘o‘,‘_‘,‘u‘], [‘_‘,‘r‘,‘e‘], [‘d‘,"i",‘l‘]] l = [[‘s‘,‘G‘,‘_‘], [‘R‘,‘r‘,‘e‘], [‘y‘,"n",‘g‘]] r = [[‘b‘,‘p‘,‘n‘], [‘m‘,‘i‘,‘r‘], [‘T‘,"c",‘}‘]] def roll(matrix): #顺时针转 matrix = [[row[col] for row in matrix] for col in reversed(range(len(matrix[0])))] matrix = [[row[col] for row in matrix] for col in reversed(range(len(matrix[0])))] matrix = [[row[col] for row in matrix] for col in reversed(range(len(matrix[0])))] return matrix def PrintOne(w): for i in range(3): for j in range(3): print(w[i][j],end=‘ ‘) print(‘‘) def PrintAll(): global u global f global b global d global l global r m = 12 n = 9 temp = [[‘ ‘] * m for i in range(n) ] for i in range(3): for j in range(3): temp[i][j+3] = u[i][j] for i in range(3): for j in range(3): temp[i+3][j] = l[i][j] for i in range(3): for j in range(3): temp[i+3][j+3] = f[i][j] for i in range(3): for j in range(3): temp[i+3][j+6] = r[i][j] for i in range(3): for j in range(3): temp[i+3][j+9] = b[i][j] for i in range(3): for j in range(3): temp[i+6][j+3] = d[i][j] for i in range(9): for j in range(12): print(temp[i][j],end=‘ ‘) print(‘‘) def roll4(s): global u global f global b global d global l global r if(s == ‘F‘): f = roll(f) x = u[2][0] y = u[2][1] z = u[2][2] u[2][0] = l[2][2] u[2][1] = l[1][2] u[2][2] = l[0][2] l[2][2] = d[0][2] l[1][2] = d[0][1] l[0][2] = d[0][0] d[0][2] = r[0][0] d[0][1] = r[1][0] d[0][0] = r[2][0] r[0][0] = x r[1][0] = y r[2][0] = z elif(s == ‘U‘): u = roll(u) x = b[0][0] y = b[0][1] z = b[0][2] b[0][0] = l[0][0] b[0][1] = l[0][1] b[0][2] = l[0][2] l[0][0] = f[0][0] l[0][1] = f[0][1] l[0][2] = f[0][2] f[0][0] = r[0][0] f[0][1] = r[0][1] f[0][2] = r[0][2] r[0][0] = x r[0][1] = y r[0][2] = z elif(s == ‘D‘): d = roll(d) x = f[2][0] y = f[2][1] z = f[2][2] f[2][0] = l[2][0] f[2][1] = l[2][1] f[2][2] = l[2][2] l[2][0] = b[2][0] l[2][1] = b[2][1] l[2][2] = b[2][2] b[2][0] = r[2][0] b[2][1] = r[2][1] b[2][2] = r[2][2] r[2][0] = x r[2][1] = y r[2][2] = z elif(s == ‘L‘): l = roll(l) x = u[0][0] y = u[1][0] z = u[2][0] u[0][0] = b[2][2] u[1][0] = b[1][2] u[2][0] = b[0][2] b[2][2] = d[0][0] b[1][2] = d[1][0] b[0][2] = d[2][0] d[2][0] = f[2][0] d[1][0] = f[1][0] d[0][0] = f[0][0] f[0][0] = x f[1][0] = y f[2][0] = z elif(s == ‘L‘): l = roll(l) x = u[0][0] y = u[1][0] z = u[2][0] u[0][0] = b[2][2] u[1][0] = b[1][2] u[2][0] = b[0][2] b[2][2] = d[0][0] b[1][2] = d[1][0] b[0][2] = d[2][0] d[2][0] = f[2][0] d[1][0] = f[1][0] d[0][0] = f[0][0] f[0][0] = x f[1][0] = y f[2][0] = z elif(s == ‘R‘): r = roll(r) x = u[0][2] y = u[1][2] z = u[2][2] u[0][2] = f[0][2] u[1][2] = f[1][2] u[2][2] = f[2][2] f[0][2] = d[0][2] f[1][2] = d[1][2] f[2][2] = d[2][2] d[0][2] = b[2][0] d[1][2] = b[1][0] d[2][2] = b[0][0] b[0][0] = z b[1][0] = y b[2][0] = x elif(s == ‘B‘): b = roll(b) x = u[0][0] y = u[0][1] z = u[0][2] u[0][0] = r[0][2] u[0][1] = r[1][2] u[0][2] = r[2][2] r[0][2] = d[2][2] r[1][2] = d[2][1] r[2][2] = d[2][0] d[2][0] = l[0][0] d[2][1] = l[1][0] d[2][2] = l[2][0] l[0][0] = z l[1][0] = y l[2][0] = x roll4(‘U‘) roll4(‘L‘) roll4(‘L‘) roll4(‘L‘) roll4(‘F‘) roll4(‘F‘) roll4(‘F‘) roll4(‘R‘) roll4(‘U‘) roll4(‘U‘) roll4(‘U‘) roll4(‘F‘) roll4(‘B‘) roll4(‘R‘) roll4(‘R‘) roll4(‘R‘) roll4(‘D‘) roll4(‘D‘) roll4(‘D‘) roll4(‘L‘) roll4(‘L‘) roll4(‘D‘) roll4(‘D‘) roll4(‘D‘) roll4(‘R‘) roll4(‘R‘) roll4(‘R‘) roll4(‘U‘) roll4(‘U‘) roll4(‘L‘) roll4(‘L‘) roll4(‘L‘) roll4(‘R‘) roll4(‘D‘) roll4(‘F‘) roll4(‘B‘) roll4(‘B‘) roll4(‘L‘) roll4(‘L‘) roll4(‘D‘) roll4(‘D‘) roll4(‘R‘) roll4(‘F‘) roll4(‘D‘) roll4(‘D‘) roll4(‘F‘) roll4(‘F‘) roll4(‘U‘) roll4(‘U‘) roll4(‘U‘) roll4(‘L‘) roll4(‘D‘) roll4(‘D‘) roll4(‘D‘) roll4(‘U‘) roll4(‘U‘) roll4(‘U‘) roll4(‘D‘) roll4(‘B‘) roll4(‘B‘) roll4(‘B‘) roll4(‘R‘) roll4(‘L‘) roll4(‘L‘) roll4(‘L‘) # roll4(‘U‘) roll4(‘B‘) roll4(‘B‘) roll4(‘B‘) roll4(‘U‘) roll4(‘B‘) roll4(‘B‘) roll4(‘L‘) roll4(‘L‘) roll4(‘F‘) roll4(‘F‘) roll4(‘R‘) PrintAll()
标签:process append adb activity 安卓 col 技术 decrypt bad
原文地址:https://www.cnblogs.com/basstorm/p/12665281.html