标签:文件 一个 顺序 embed ref ret iam sign rpo
今天豆子尝试着使用Cloudformation Designer来创建一个Template 文件。Designer对于初学者还是很有帮助的,一方面可以通过可视界面拖动Resource,另外可以按住Ctrl+Space 来提示对应的Property里面可以配置哪些东西。还可以直接拖动线条来实现依赖关系。当然最重要的一点是可以帮忙进行语法检测。下面是一个小例子。
平常豆子需要经常创建S3的bucket进行备份,对于每个Bucket需要配置lifecycle rule,创建对应的user policy,attach到一个新的User,然后配置这个新用户的Secretkey,最后在客户端写个小脚本定期备份。
现在把AWS的这一部分都改成用Cloudformation实现。
基本的resource就这4个部分。双击rerouce可以进行编辑对应的内容,在空格处随便单击一下 就可以编辑Parameter等section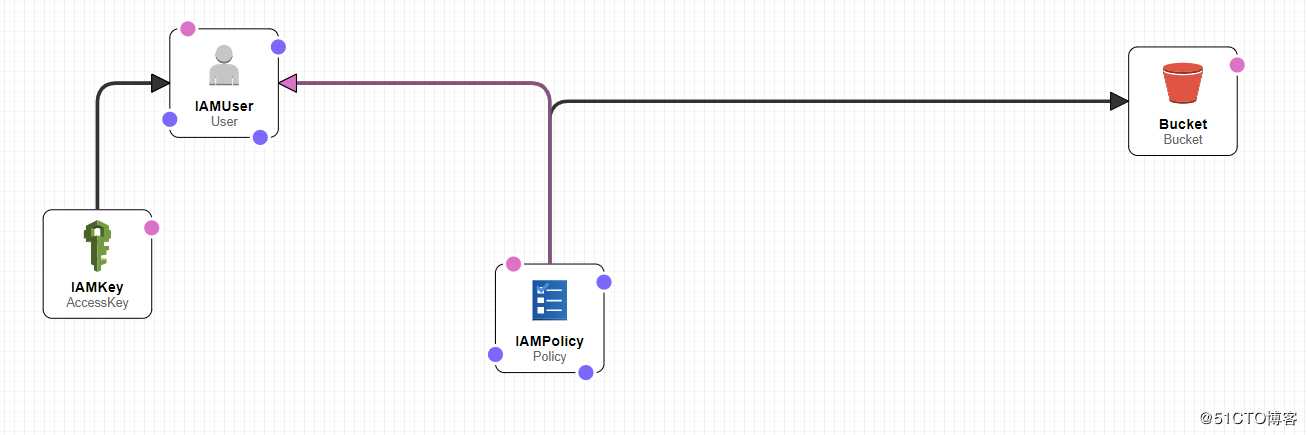
编辑过程中,可以从对应的Resource里面点开他的帮助文档,这个是一个很方便的功能
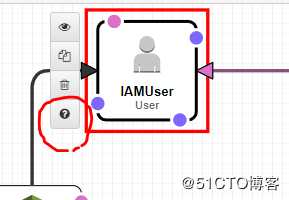
提交之前,记得检查语法。
{
"AWSTemplateFormatVersion": "2010-09-09",
"Metadata": {
"AWS::CloudFormation::Designer": {
"5f48a1ce-1a7b-44e3-b9b6-b83719bded79": {
"size": {
"width": 60,
"height": 60
},
"position": {
"x": 510,
"y": 120
},
"z": 0,
"embeds": []
},
"e0e4e707-9bea-46b5-ab39-588be81cb5e3": {
"size": {
"width": 60,
"height": 60
},
"position": {
"x": -20,
"y": 110
},
"z": 0,
"embeds": []
},
"b81b1033-9cc0-4248-b807-fb575fd54687": {
"size": {
"width": 60,
"height": 60
},
"position": {
"x": 160,
"y": 240
},
"z": 0,
"embeds": [],
"isassociatedwith": [
"e0e4e707-9bea-46b5-ab39-588be81cb5e3"
],
"dependson": [
"e0e4e707-9bea-46b5-ab39-588be81cb5e3"
]
},
"83bda625-f2d4-4de1-8b66-d475476308ed": {
"size": {
"width": 60,
"height": 60
},
"position": {
"x": -90,
"y": 210
},
"z": 0,
"embeds": []
},
"fc691126-aba2-4041-a755-93a1a15ac969": {
"source": {
"id": "b81b1033-9cc0-4248-b807-fb575fd54687",
"selector": "g:nth-child(1) g:nth-child(4) g:nth-child(1) circle:nth-child(1) ",
"port": "AWS::RefLink-AWS::IAM::User-Users"
},
"target": {
"id": "e0e4e707-9bea-46b5-ab39-588be81cb5e3"
},
"z": 12
},
"55264e1b-ae17-48b2-9508-fef96a0ca753": {
"source": {
"id": "b81b1033-9cc0-4248-b807-fb575fd54687",
"selector": "g:nth-child(1) g:nth-child(4) g:nth-child(1) circle:nth-child(1) ",
"port": "AWS::RefLink-AWS::IAM::User-Users"
},
"target": {
"id": "e0e4e707-9bea-46b5-ab39-588be81cb5e3"
},
"z": 12
},
"5585399a-b5be-4e8e-8779-6bc1471da1f5": {
"source": {
"id": "b81b1033-9cc0-4248-b807-fb575fd54687"
},
"target": {
"id": "e0e4e707-9bea-46b5-ab39-588be81cb5e3"
},
"z": 11
}
}
},
"Resources": {
"IAMUser": {
"Type": "AWS::IAM::User",
"Properties": {
"UserName": {
"Ref": "UserName"
}
},
"Metadata": {
"AWS::CloudFormation::Designer": {
"id": "e0e4e707-9bea-46b5-ab39-588be81cb5e3"
}
}
},
"Bucket": {
"Type": "AWS::S3::Bucket",
"Properties": {
"BucketName": {
"Ref": "S3BucketName"
},
"LifecycleConfiguration": {
"Rules": [
{
"Id": "GlacierRule",
"Prefix": "glacier",
"Status": "Enabled",
"ExpirationInDays": "365",
"Transitions": [
{
"TransitionInDays": "1",
"StorageClass": "GLACIER"
}
]
}
]
}
},
"Metadata": {
"AWS::CloudFormation::Designer": {
"id": "5f48a1ce-1a7b-44e3-b9b6-b83719bded79"
}
}
},
"IAMPolicy": {
"Type": "AWS::IAM::Policy",
"Properties": {
"Users": [
{
"Ref": "IAMUser"
}
],
"PolicyName": "Test",
"PolicyDocument": {
"Version": "2012-10-17",
"Statement": [
{
"Sid": "VisualEditor0",
"Effect": "Allow",
"Action": "s3:ListBucket",
"Resource": {
"Fn::Join": [
":",
[
"arn:aws:s3::",
{
"Ref": "Bucket"
}
]
]
}
},
{
"Sid": "VisualEditor1",
"Effect": "Allow",
"Action": [
"s3:ListAllMyBuckets",
"s3:HeadBucket"
],
"Resource": "*"
},
{
"Sid": "VisualEditor2",
"Effect": "Allow",
"Action": "s3:*",
"Resource": {
"Fn::Join": [
"/",
[
{
"Fn::Join": [
":",
[
"arn:aws:s3::",
{
"Ref": "Bucket"
}
]
]
},
"*"
]
]
}
}
]
}
},
"Metadata": {
"AWS::CloudFormation::Designer": {
"id": "b81b1033-9cc0-4248-b807-fb575fd54687"
}
},
"DependsOn": [
"IAMUser"
]
},
"IAMKey": {
"Type": "AWS::IAM::AccessKey",
"Properties": {
"UserName": {
"Ref": "IAMUser"
}
},
"Metadata": {
"AWS::CloudFormation::Designer": {
"id": "83bda625-f2d4-4de1-8b66-d475476308ed"
}
},
"DependsOn": [
"IAMUser"
]
}
},
"Parameters": {
"S3BucketName": {
"Type": "String"
},
"UserName": {
"Type": "String"
},
"PolicyName": {
"Type": "String"
}
},
"Outputs": {
"BucketName": {
"Value": {
"Ref": "Bucket"
},
"Description": "S3 Bucket Name"
},
"SecretAccessKey": {
"Value": {
"Fn::GetAtt": [
"IAMKey",
"SecretAccessKey"
]
},
"Description": "Secret Access Key"
},
"AccessKeyID": {
"Value": {
"Ref": "IAMKey"
},
"Description": "Access ID"
}
}
}下面是stack创建的过程,因为我设置了依赖关系,所以顺序是S3 Bucket, User, UserPolicy和UserKey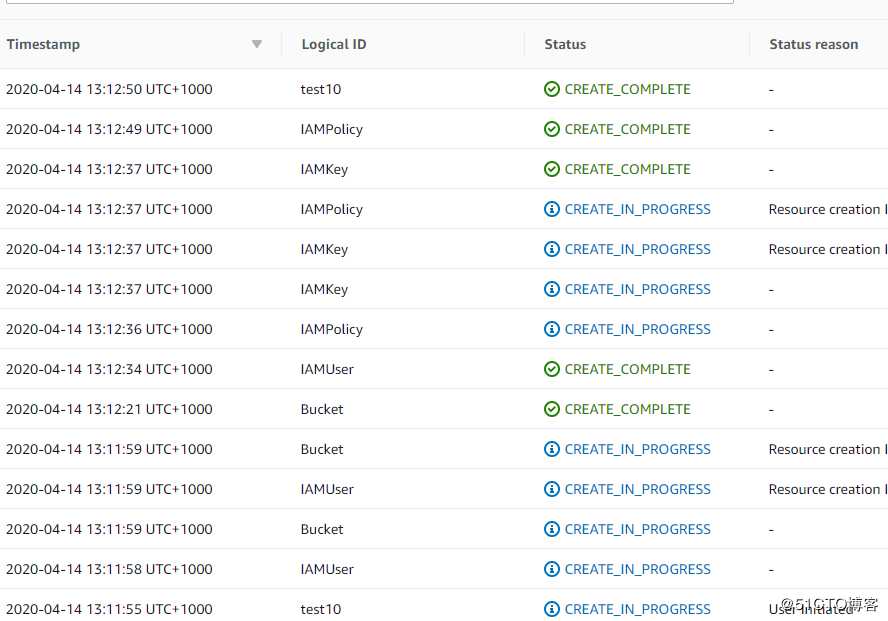
最后输出我的AccessID和SecretKey,这样我在客户端才能调用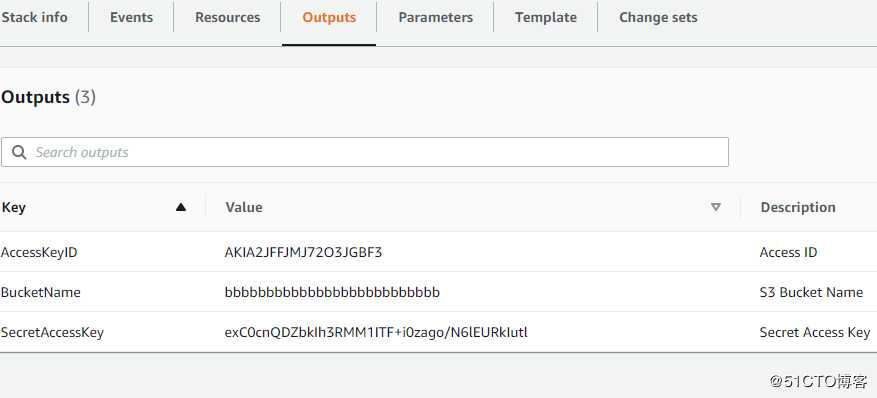
AWS Cloudformation - Designer 的使用
标签:文件 一个 顺序 embed ref ret iam sign rpo
原文地址:https://blog.51cto.com/beanxyz/2487170