标签:mis gen 访问 ons perm image 目的 inter flags
背景与第三方机构对接时,采用nat的方式访问。配置为历史遗留配置,前人测试通过后未正式部署。此次正式部署发现网络不通,NAT也没表项。
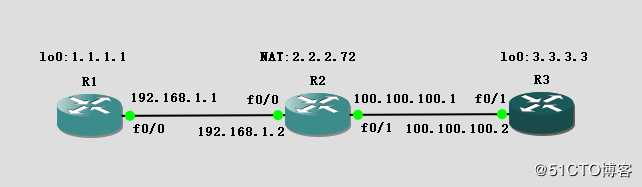
以上图作为示意图,图中1.1.1.1转换成2.2.2.72访问3.3.3.3。R3上只有去2.2.2.72的路由。因此,在没有NAT的情况下,1.1.1.1是无法访问3.3.3.3的。
1、在R1上用1.1.1.1作为源ping R3的3.3.3.3。
R1#ping 3.3.3.3 source 1.1.1.1
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 3.3.3.3, timeout is 2 seconds:
Packet sent with a source address of 1.1.1.1
UUUUU
Success rate is 0 percent (0/5)
2、在R2上show ip nat translations没有看到相关的表项。
1、在R2上debug ip nat相关信息。
R2#debug ip nat
IP NAT debugging is on
R2#
May 20 22:34:48.567: NAT: translation failed (A), dropping packet s=1.1.1.1 d=3.3.3.3
May 20 22:34:48.667: NAT: translation failed (A), dropping packet s=1.1.1.1 d=3.3.3.3
May 20 22:34:48.771: NAT: translation failed (A), dropping packet s=1.1.1.1 d=3.3.3.3
May 20 22:34:48.875: NAT: translation failed (A), dropping packet s=1.1.1.1 d=3.3.3.3
*May 20 22:34:48.975: NAT: translation failed (A), dropping packet s=1.1.1.1 d=3.3.3.3
可以看到转换失败。说明故障点在NAT上。
加上detaild参数,寻找详细信息。
R2#debug ip nat detailed
IP NAT detailed debugging is on
R2#
May 20 22:35:10.371: NAT: address not stolen for 1.1.1.1, proto 1 port 5
May 20 22:35:10.371: NAT: failed to allocate address for 1.1.1.1, list/map 110
May 20 22:35:10.371: NAT: Can‘t create new inside entry - forced_punt_flags: 0
May 20 22:35:10.379: NAT: address not stolen for 1.1.1.1, proto 1 port 5
May 20 22:35:10.379: NAT: failed to allocate address for 1.1.1.1, list/map 110
*May 20 22:35:10.379: NAT: translation failed (A), dropping packet s=1.1.1.1 d=3.3.3.3
以上详细信息说明了转换失败的原因,看着感觉是地址耗尽。可是查看了NAT转换表,作为PAT这个转换地址连一个条目都没有。
检查ACL发现有命中,检查NAT的转换信息,转换都是miss条目。
R2#show ip access-lists
Extended IP access list 110
10 permit ip host 1.1.1.1 host 3.3.3.3 (51 matches)R2#show ip nat statistics
Total active translations: 0 (0 static, 0 dynamic; 0 extended)
Outside interfaces:
FastEthernet0/1
Inside interfaces:
FastEthernet0/0
Hits: 10 Misses: 0
CEF Translated packets: 10, CEF Punted packets: 25
Expired translations: 1
Dynamic mappings:
-- Inside Source
[Id: 1] access-list 110 pool pool-110 refcount 0
pool pool-110: netmask 255.255.255.248
start 2.2.2.72 end 2.2.2.72
type generic, total addresses 1, allocated 0 (0%), misses 50
nat-limit statistics:
max entry: max allowed 0, used 0, missed 0
仔细检查了下NAT的配置:
R2:
ip access list extend 110
10 permit ip host 1.1.1.1 host 3.3.3.3ip nat pool pool-110 2.2.2.72 2.2.2.72 netmask 255.255.255.248
ip nat inside source list 110 pool pool-110 overload
发现pool条目的掩码是255.255.255.248,对于2.2.2.72而言,配合这个掩码,这个地址就是个网络地址,因此无法被正常转换。
于是修改掩码为255.255.255.0,ping测试正常通过。
R1#ping 3.3.3.3 source 1.1.1.1
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 3.3.3.3, timeout is 2 seconds:
Packet sent with a source address of 1.1.1.1
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 92/125/148 ms
在网络配置过程中,每一个参数都有它独特的意义。在NAT配置过程中,NAT地址的MASK往往是被忽略的一部分。然而,在本例中,就是因为这个不起眼的参数导致了网络不通。
标签:mis gen 访问 ons perm image 目的 inter flags
原文地址:https://blog.51cto.com/juispan/2497142