标签:rtu header location into grep 损坏 start $? creat
# 什么是高可用
一般是指2台机器启动着完全相同的业务系统,当有一台机器down机了,另外一台服务器就能快速的接管,对于访问的用户是无感知的。
# 高可用常用软件
硬件:F5
软件:keepalived
# keepalived如何实现高可用
keepalived软件是基于VRRP协议实现的,VRRP虚拟路由冗余协议,主要用于解决单点故障问题
· 用户上网通过指定ip经过路由器访问外网,但最开始用户并不知道ip地址所对应mac地址,于是通过ARP地址广播方式找到网关mac地址,找到之后将对应ip地址和mac地址对应信息写入到ARP缓存表中,下次连接pc直接通过缓存表信息连接(无需广播,除非arp缓存表到期),但如果出现网关出现硬件或者逻辑损坏导致不可用,若将另一台硬件设备顶替原本网关,使用旧设备ip地址,则会发现依旧无法上网,原因:用户本身存在ARP缓存表,就算有了新的硬件网关,但ip还是老ip,所以会直接走本身缓存,除非arp缓存表到期,或者手动删除arp缓存表信息,这样用户才会再次发起广播,如下图:
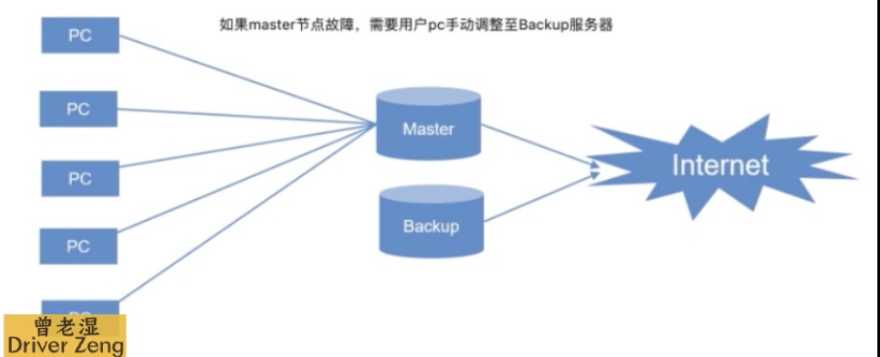
· 但如上面的解决方式问题又来了,要是master恢复正常,是不是还需要重新清空缓存表呢?全都是手动方式,不实际,由此诞生了VRRP,VRPP其实是通过软件或者硬件的形式在Master和Backup外面增加一个虚拟的MAC地址(VMAC)与虚拟ip地址。
漂移地址:当VIP在master中时,则VIP对应mac地址为master网卡mac,若VIP在backup中时,则VIP对应mac为backup网卡mac,所以是会根据vip地址所在主机网卡进行绑定。
1.keepalived分为抢占式和非抢占式,
注意:如果是抢占式,脚本只需要放在MASTER上,如果是非抢占式,脚本必须放在MASTER和BACKUP上
抢占式:当master故障,backup自动接管,但当master恢复后自动抢夺会主位置
非抢占式:当master故障,backup自动接管,但当master恢复后,master并不会采取抢夺,而是等backup故障后在接替。
2.keepalived高可用可利用在很多地方,并不是只能针对nginx使用,有些服务若本身没有自带高可用服务,可使用keepalived为此服务。所以nginx并没有绑定在keepalived上,当nginx故障,keepalived并不会自动停止服务,而是继续工作,vip依然不会漂移,所以在写keepalived配置文件时,需要绑定脚本一起工作,当然脚本需要自己写
3.脑裂问题:。由于某些原因,导致两台keepalived高可用服务器在指定时间内,无法检测到对方的心跳,各自取得资源及服务的所有权,而此时的两台高可用服务器又都还活着。
# keepalived主配置文件介绍
[root@lb01 ~]# vim /etc/keepalived/keepalived.conf # MASTER配置
global_defs { # 全局定义
router_id lb01 # 标识身份名称
}
vrrp_script sh { # 因keepalived并不会做到监控nginx,如nginx停止,
script "/etc/nginx/jiankong.sh" # keepalived服务依然存活,需要监本对nginx实现监控
interval 5 # 这里为指定脚本路径路径,及脚本运行间隔时长
}
vrrp_instance VI_1 { # 实例配置
state MASTER # 标识角色状态
interface eth0 # 网卡绑定接口
virtual_router_id 50 # 虚拟路由id
priority 150 # 优先级
advert_int 1 # 检测检测间隔时间
authentication { # 认证
auth_type PASS # 认证方式
auth_pass 1111 # 认证密码
}
virtual_ipaddress { # 虚拟地址配置
10.0.0.3 # 虚拟VIP地址
}
track_script { # 类似于nginx的引用upstream信息
sh # 这里可理解成引用定义脚本路径名称
}
}
# 创建脚本,使keepalived监测nginx,如nginx停止运行,keeplived也停止,那么master(vip)转移至bakcup上,当然这里的脚本可在被主配置文件所调用
[root@lb01 nginx]# cat /etc/nginx/jiankong.sh
#!/bin/bash
nginx_status=$(ps -C nginx --no-header|wc -l)
if [ $nginx_status -eq 0 ];then
systemctl start nginx
sleep 3
nginx_status=$(ps -C nginx --no-header|wc -l)
if [ $nginx_status -eq 0 ];then
systemctl stop keepalived
fi
fi
# 1.书写脚本(防止出现master和backup无法通讯问题,同时出现两个vip地址,导致地址冲突,网页无法访问)
# 脚本翻译:在backup尝试ping两次master的ip,查看是否通讯,如果可以通讯,出现master和backup中同时存在vip地址,则将backup中的keepalived停止,如出现master具有vip,而backup没有,则页面输出正常,但如果出现最开始的ping都无法ping通master,直接输出信息。(建议最开始要使用密钥对方式连接master,否则,此脚本需要一直输入密码,而且在运行脚本时可以使用sh.sh &放在后台执行。)
[root@lb02 ~]# vim sh.sh
#!/bin/bash
vip=10.0.0.3
lb01_ip=10.0.0.5
while true;do
ping -c 2 $lb01_ip &>/dev/null
if [ $? -eq 0 ];then
lb01_vip_status=$(ssh $lb01_ip "ip add|grep $vip|wc -l")
lb02_vip_status=$(ip add|grep $vip|wc -l)
if [ $lb01_vip_status -eq 1 -a $lb02_vip_status -eq 1 ];then
echo ‘主节点和备节点都有VIP,开始关闭备节点的VIP...‘ >>/var/log/nginx/error.log
systemctl stop keepalived
elif [ $lb01_vip_status -eq 1 -a $lb02_vip_status -eq 0 ];then
echo ‘主节点存在vip,备节点没有vip,正常。。。‘ >>/var/log/messages
fi
else
echo ‘主节点无法通信‘ >>/var/log/nginx/error.log
fi
sleep 5
done
# 这种方式在生产中一般很少使用
1、两个节点的state都必须配置为BACKUP
2、两个节点都必须加上配置 nopreempt
3、其中一个节点的优先级必须要高于另外一个节点的优先级。
两台服务器都角色状态启用nopreempt后,必须修改角色状态统一为BACKUP,唯一的区分就是优先级。
Master配置
vrrp_instance VI_1 {
state BACKUP
priority 150
nopreempt
}
Backup配置
vrrp_instance VI_1 {
state BACKUP
priority 100
nopreempt
}
# **完善架构**
1.web01 02 03 部署nginx 和php 80端口
2.lb部署https证书,80强转443
3.NFS: sersync
4.MySQL
5.RSYNC 实时备份 NFS
- wordpress
- zh
6.搭建keeplived实现两台lb做主备(抢占式)
| 主机名 | 内网ip | 外网ip | 角色 |
|---|---|---|---|
| lb01 | 172.16.1.5 | 10.0.0.5 | 负载均衡/keepalived |
| lb02 | 172.16.1.6 | 10.0.0.6 | 负载均衡/keepalived |
| web01 | 172.16.1.7 | 10.0.0.7 | web服务器 |
| web02 | 172.16.1.8 | 10.0.0.8 | web服务器 |
| web03 | 172.16.1.9 | 10.0.0.9 | web服务器 |
| db01 | 172.16.1.51 | 10.0.0.51 | 数据库服务器 |
| nfs | 172.16.1.31 | 10.0.0.31 | 静态资源存储 |
| backup | 172.16.1.41 | 10.0.0.41 | 备份服务器 |
# 1.安装nginx及php(三台web均需安装)
[root@web01 nginx.php]# yum localinstall -y nginx-1.18.0-1.el7.ngx.x86_64.rpm
[root@web01 nginx.php]# yum localinstall -y php*
# 2.统一用户(三台web均需创建)
[root@web01 conf.d]# groupadd www -g 666
[root@web01 conf.d]# useradd www -u 666 -g 666 -s /sbin/nologin
[root@web01 conf.d]# vim /etc/nginx/nginx.conf
user www;
[root@web01 conf.d]# vim /etc/php-fpm.d/www.conf
user = www
group = www
# 3.书写nginx配置文件搭建知乎及wordpress(web01中书写,其他web直接拷贝web01即可)
[root@web01 conf.d]# vim /etc/nginx/conf.d/wp.conf ---------wordpress配置文件
server {
listen 80;
server_name wp.linux.com;
root /code/wp;
index index.php index.html;
location ~ \.php$ {
fastcgi_pass 127.0.0.1:9000;
fastcgi_index index.php;
fastcgi_param SCRIPT_FILENAME $document_root$fastcgi_script_name;
include /etc/nginx/fastcgi_params;
}
}
[root@web01 conf.d]# vim /etc/nginx/conf.d/zh.conf ---------知乎配置文件
server {
listen 80;
server_name zh.linux.com;
root /code/zh;
index index.php index.html;
location ~ \.php {
fastcgi_pass 127.0.0.1:9000;
fastcgi_index index.php;
fastcgi_param SCRIPT_FILENAME $document_root$fastcgi_script_name;
include /etc/nginx/fastcgi_params;
}
}
# 4.检测配置文件,并启动服务
[root@web01 conf.d]# nginx -t
nginx: the configuration file /etc/nginx/nginx.conf syntax is ok
nginx: configuration file /etc/nginx/nginx.conf test is successful
[root@web01 conf.d]# systemctl start nginx php-fpm
# 5.检测服务是否启动
[root@web01 conf.d]# netstat -lntup|grep 80
tcp 0 0 0.0.0.0:80 0.0.0.0:* LISTEN 7308/nginx: master
[root@web01 conf.d]# netstat -lntup|grep 9000
tcp 0 0 127.0.0.1:9000 0.0.0.0:* LISTEN 7307/php-fpm: mast
# 6.根据配置文件创建对应站点目录(三台web均需创建)
[root@web01 conf.d]# mkdir /code/{wp,zh} -p
# 7.将对应压缩包上传至对应站点目录并解压
[root@web01 zh]# unzip WeCenter_3-2-1.zip
[root@web01 wp]# tar xf wordpress-5.0.3-zh_CN.tar.gz
# 8.对站点目录更改权限
[root@web01 wp]# chown -R www.www /code
# 9.页面测试(在windows中配置域名解析)
wp.linux.com
zh.linux.com
# 1.数据库安装
[root@db01 ~]# yum install -y mariadb-server
# 2.启动数据库
[root@db01 ~]# systemctl start mariadb
# 3.为wp和zh创建对应连接用户
MariaDB [(none)]> grant all on *.* to wp_user@‘%‘ identified by ‘123‘;
MariaDB [(none)]> grant all on *.* to zh_user@‘%‘ identified by ‘123‘;
# 4.创建对应数据库
MariaDB [(none)]> create database wp;
MariaDB [(none)]> create database zh;
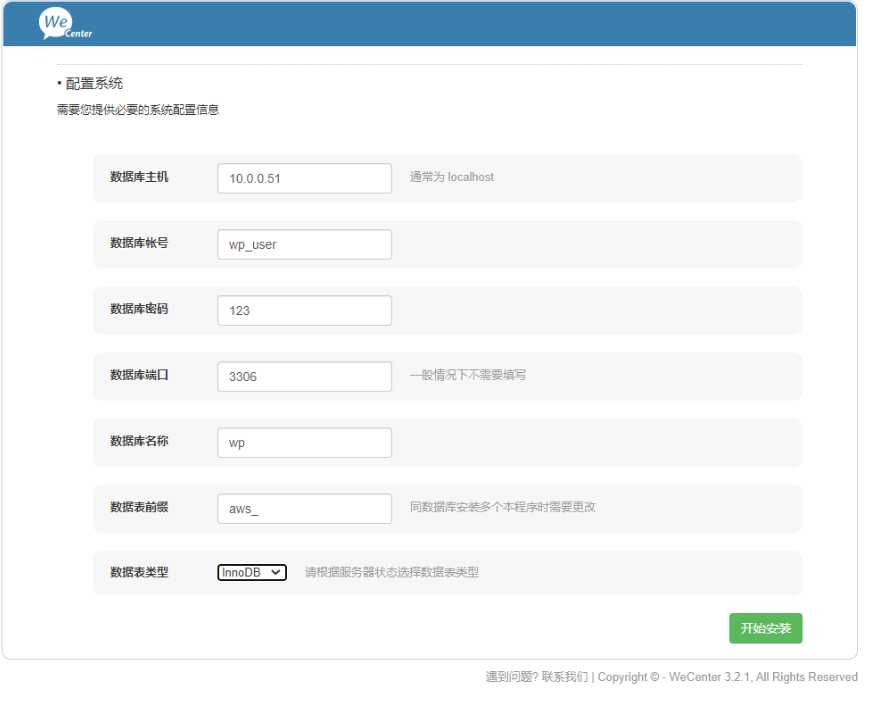
# 5.继续连接web页面,填写数据库信息
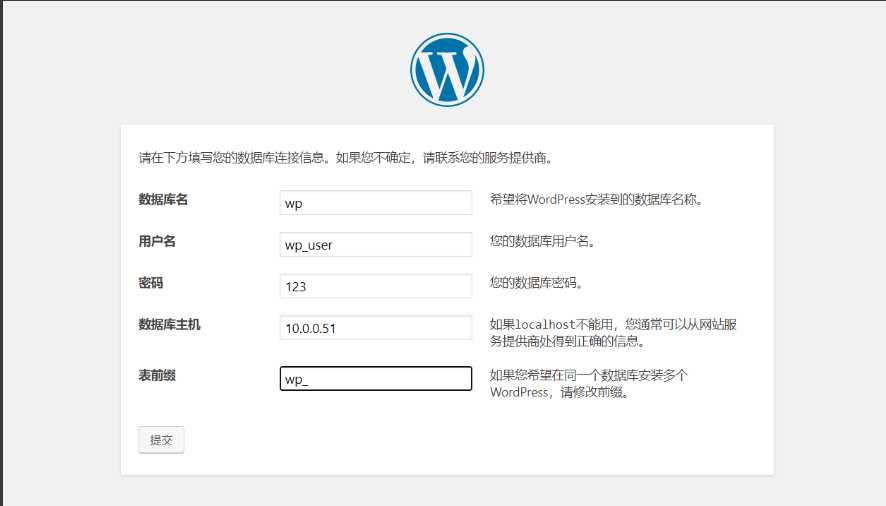
搭建博客
# 1.将web01中的配置文件操作复制到web02和web03中
[root@web01 wp]# cp -r /etc/nginx/conf.d/* root@10.0.0.8:/etc/nginx/conf.d/
[root@web01 wp]# scp -r /etc/nginx/conf.d/* root@10.0.0.9:/etc/nginx/conf.d/
# 2.将web01中的站点目录信息复制到web02和web03中
[root@web01 wp]# scp -r /code/wp/* root@10.0.0.8:/code/wp/
[root@web01 wp]# scp -r /code/zh/* root@10.0.0.8:/code/zh/
[root@web01 wp]# scp -r /code/wp/* root@10.0.0.9:/code/wp/
[root@web01 wp]# scp -r /code/zh/* root@10.0.0.9:/code/zh/
# 3.修改权限
[root@web02 wp]# chown -R www.www /code
[root@web03 conf.d]# chown -R www.www /code
# 1.nfs安装(服务端安装)
[root@nfs ~]# yum install -y nfs-utils
# 2.nfs客户端安装
[root@web02 wp]# yum install -y nfs-utils
[root@web03 wp]# yum install -y nfs-utils
[root@web01 wp]# yum install -y nfs-utils
# 3.修改nfs配置文件
[root@nfs ~]# vim /etc/exports
/wp 172.16.1.0/24(sync,rw,all_squash,anonuid=666,anongid=666)
/zh 172.16.1.0/24(sync,rw,all_squash,anonuid=666,anongid=666)
# 4.创建对应用户及目录
[root@nfs ~]# groupadd www -g 666
[root@nfs ~]# useradd www -u 666 -g 666 -s /sbin/nologin -M
[root@nfs ~]# mkdir /{wp,zh}
[root@nfs ~]# chown -R www.www /wp
[root@nfs ~]# chown -R www.www /zh
# 5.启动服务
[root@nfs ~]# systemctl start nfs-server
[root@nfs ~]# systemctl enable nfs-server
# 6.检测服务是否正常(通过客户端检测)
[root@web01 wp]# showmount -e 172.16.1.31
Export list for 172.16.1.31:
/zh 172.16.1.0/24
/wp 172.16.1.0/24
# 7.客户端将需要挂载文件提前发送至nfs服务端,并修改权限
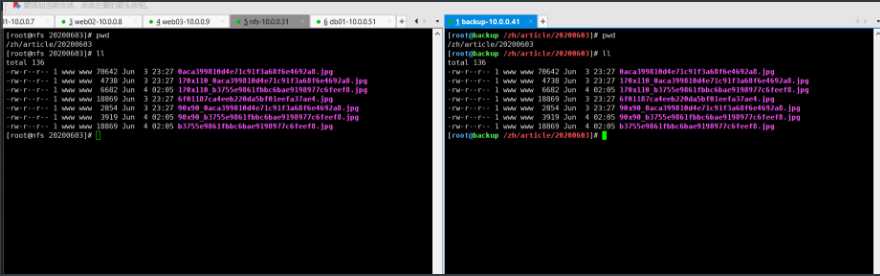
[root@web01 wp]# scp -r /code/wp/wp-content/uploads/* root@10.0.0.31:/wp
[root@web01 wp]# scp -r /code/zh/uploads/* root@10.0.0.31:/zh
[root@nfs wp]# chown -R www.www /wp
[root@nfs wp]# chown -R www.www /zh
# 8.客户端挂载
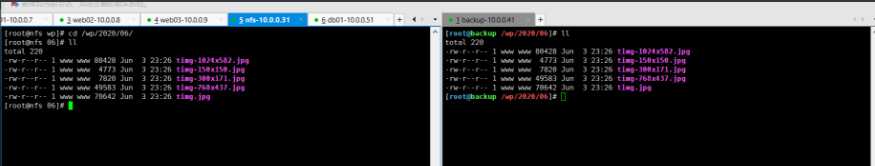
[root@web01 wp]# mount -t nfs 172.16.1.31:/wp /code/wp/wp-content/uploads/
[root@web01 wp]# mount -t nfs 172.16.1.31:/zh /code/zh/uploads/
[root@web02 wp]# mount -t nfs 172.16.1.31:/wp /code/wp/wp-content/uploads/
[root@web02 wp]# mount -t nfs 172.16.1.31:/zh /code/zh/uploads/
[root@web03 wp]# mount -t nfs 172.16.1.31:/wp /code/wp/wp-content/uploads/
[root@web03 wp]# mount -t nfs 172.16.1.31:/zh /code/zh/uploads/
# 1.服务安装(backup服务端)
[root@backup ~]# yum install -y rsync
# 2.配置文件修改
[root@backup ~]# vim /etc/rsyncd.conf
uid = www
gid = www
port = 873
fake super = yes
use chroot = no
max connections = 200
timeout = 600
ignore errors
read only = false
list = false
auth users = rsync_backup
secrets file = /etc/rsync.passwd
log file = /var/log/rsyncd.log
#####################################
[zh]
comment = welcome to oldboyedu backup!
path = /zh
[wp]
comment = welcome to oldboyedu backup!
path = /wp
# 3.根据配置文件创建用户
[root@backup ~]# groupadd www -g 666
[root@backup ~]# useradd www -u 666 -g 666 -s /sbin/nologin -M
# 4.根据配置文件创建目录
[root@backup ~]# mkdir /{wp,zh}
# 5.授权
[root@backup ~]# chown -R www.www /{wp,zh}
# 6.创建认证用户账号密码,并修改权限
[root@backup ~]# cat /etc/rsync.passwd
rsync_backup:123
[root@backup /zh]# chmod 600 /etc/rsync.passwd
# 7.启动服务
[root@backup ~]# systemctl start rsyncd
[root@backup ~]# systemctl enable rsyncd
# 1.服务安装(backup客户端)
[root@nfs wp]# yum install -y rsync inotify-tools
# 2.下载sersync包
[root@nfs wp]# wget https://raw.githubusercontent.com/wsgzao/sersync/master/sersync2.5.4_64bit_binary_stable_final.tar.gz
# 3.解压
[root@nfs wp]# tar xf sersync2.5.4_64bit_binary_stable_final.tar.gz
# 4.移动目录
[root@nfs wp]# mv GNU-Linux-x86/ /usr/local/sersync
# 5.修改配置文件(只监控nfs中wp目录,还需稍后新增目录)
[root@nfs wp]# vim /usr/local/sersync/confxml.xml
<inotify>
<delete start="true"/>
<createFolder start="true"/>
<createFile start="true"/>
<closeWrite start="true"/>
<moveFrom start="true"/>
<moveTo start="true"/>
<attrib start="true"/>
<modify start="true"/>
</inotify>
<sersync>
<localpath watch="/wp">
<remote ip="10.0.0.41" name="wp"/>
<!--<remote ip="192.168.8.39" name="tongbu"/>-->
<!--<remote ip="192.168.8.40" name="tongbu"/>-->
</localpath>
<rsync>
<commonParams params="-az"/>
<auth start="true" users="rsync_backup" passwordfile="/etc/rsync.passwd"/>
<userDefinedPort start="false" port="874"/><!-- port=874 -->
<timeout start="false" time="100"/><!-- timeout=100 -->
<ssh start="false"/>
</rsync>
# 6.根据配置文件创建密码文件(只需写入用户)
[root@nfs wp]# vim /etc/rsync.passwd
123
# 7.更改密码文件权限
[root@nfs wp]# chmod 600 /etc/rsync.passwd
# 8.监控zh目录,多编写一个配置文件
[root@nfs wp]# cd /usr/local/sersync/
[root@nfs sersync]# cp confxml.xml zh.xml ---和wp相比只需要修改此处即可
<sersync>
<localpath watch="/zh">
<remote ip="10.0.0.41" name="zh"/>
<!--<remote ip="192.168.8.39" name="tongbu"/>-->
<!--<remote ip="192.168.8.40" name="tongbu"/>-->
</localpath>
# 9.启动服务
[root@nfs sersync]# /usr/local/sersync/sersync2 -rdo /usr/local/sersync/zh.xml
[root@nfs sersync]# /usr/local/sersync/sersync2 -rdo /usr/local/sersync/confxml.xml
# 1.服务安装
[root@lb01 nginx.php]# yum localinstall -y nginx-1.18.0-1.el7.ngx.x86_64.rpm
[root@lb02 nginx.php]# yum localinstall -y nginx-1.18.0-1.el7.ngx.x86_64.rpm
# 2.创建证书目录
[root@lb01 nginx.php]# mkdir -p /etc/nginx/{wp_ssl,zh_ssl}
# 3.生成证书
[root@lb01 wp_ssl]# cd /etc/nginx/zh_ssl/
[root@lb01 zh_ssl]# openssl genrsa -idea -out server.key 2048
Generating RSA private key, 2048 bit long modulus
..................+++
........+++
e is 65537 (0x10001)
Enter pass phrase for server.key:
Verifying - Enter pass phrase for server.key:
Verify failure
User interface error
140555897681808:error:0906906F:PEM routines:PEM_ASN1_write_bio:read key:pem_lib.c:385:
[root@lb01 ssl_key]# ls
server.key
# 4.1.生成自签证书,同时去掉私钥密码(为zh生成)
root@lb01 zh_ssl]# openssl req -days 36500 -x509 -sha256 -nodes -newkey rsa:2048 -keyout server.key -out server.crt
Generating a 2048 bit RSA private key
..................................+++
...........................................+++
writing new private key to ‘server.key‘
-----
You are about to be asked to enter information that will be incorporated
into your certificate request.
What you are about to enter is what is called a Distinguished Name or a DN.
There are quite a few fields but you can leave some blank
For some fields there will be a default value,
If you enter ‘.‘, the field will be left blank.
-----
Country Name (2 letter code) [XX]:cn
State or Province Name (full name) []:cn
Locality Name (eg, city) [Default City]:cn
Organization Name (eg, company) [Default Company Ltd]:cn
Organizational Unit Name (eg, section) []:cn
Common Name (eg, your name or your server‘s hostname) []:zh.com # 注意此处需要和web端域名一致
Email Address []:123@qq.com
# 4.2 生成自签证书,为wp生成
[root@lb01 wp_ssl]# cd /etc/nginx/wp_ssl/
[root@lb01 nginx]# cd wp_ssl/
[root@lb01 wp_ssl]# openssl genrsa -idea -out server.key 2048
Generating RSA private key, 2048 bit long modulus
.........................+++
.......................................................................+++
e is 65537 (0x10001)
Enter pass phrase for server.key:
Verifying - Enter pass phrase for server.key:
[root@lb01 wp_ssl]# openssl req -days 36500 -x509 > -sha256 -nodes -newkey rsa:2048 -keyout server.key -out server.crt
Generating a 2048 bit RSA private key
...........................................................................................................................+++
..................................+++
writing new private key to ‘server.key‘
-----
You are about to be asked to enter information that will be incorporated
into your certificate request.
What you are about to enter is what is called a Distinguished Name or a DN.
There are quite a few fields but you can leave some blank
For some fields there will be a default value,
If you enter ‘.‘, the field will be left blank.
-----
Country Name (2 letter code) [XX]:ch
State or Province Name (full name) []:changha^H^H
Locality Name (eg, city) [Default City]:shanghai
Organization Name (eg, company) [Default Company Ltd]:shiwei
Organizational Unit Name (eg, section) []:shiwei
Common Name (eg, your name or your server‘s hostname) []:wp.com # 一定注意为后端web服务器域名
Email Address []:123@qq.com
# 5.查看生成证书,并将证书scp到lb02
[root@lb01 wp_ssl]# ll
total 8
-rw-r--r-- 1 root root 1399 Jun 4 01:35 server.crt
-rw-r--r-- 1 root root 1708 Jun 4 01:35 server.key
[root@lb01 zh_ssl]# ll
total 8
-rw-r--r-- 1 root root 1338 Jun 4 01:36 server.crt
-rw-r--r-- 1 root root 1704 Jun 4 01:36 server.key
[root@lb01 ~]# scp -r /etc/nginx/{wp_ssl,zh_ssl} root@10.0.0.6:/etc/nginx/
# 6.书写配置文件
[root@lb01 zh_ssl]# vim /etc/nginx/conf.d/lb_wp.conf (wp的负载配置文件)
upstream wp {
server 172.16.1.7;
server 172.16.1.8;
server 172.16.1.9;
}
server {
listen 80;
server_name www.wp.com;
return 302 https://$server_name$request_uri;
}
server {
listen 443 ssl;
server_name www.wp.com;
ssl_certificate /etc/nginx/wp_ssl/server.crt; # 指定wp证书地址
ssl_certificate_key /etc/nginx/wp_ssl/server.key; # 指定wp证书地址
location / {
proxy_pass http://wp;
include proxy_params;
}
}
[root@lb01 conf.d]# vim lb_zh.conf (zh负载配置文件)
upstream zh {
server 172.16.1.7;
server 172.16.1.8;
server 172.16.1.9;
}
server {
listen 80;
server_name www.zh.com;
return 302 https://$server_name$request_uri;
}
server {
listen 443 ssl;
server_name www.zh.com;
ssl_certificate /etc/nginx/zh_ssl/server.crt; # 指定zh证书路径
ssl_certificate_key /etc/nginx/zh_ssl/server.key; # 指定zh证书路径
location / {
proxy_pass http://zh;
include proxy_params;
}
}
# 7.将配置文件scp到lb02中
[root@lb01 ~]# scp -r /etc/nginx/conf.d/* root@10.0.0.6:/etc/nginx/conf.d/
[root@lb02 /etc/nginx/conf.d]# ll
total 8
-rw-r--r-- 1 root root 514 Jun 6 05:04 lb_wp.conf
-rw-r--r-- 1 root root 514 Jun 6 05:04 lb_zh.conf
# 8.重启服务
[root@lb01 conf.d]# nginx -t
nginx: the configuration file /etc/nginx/nginx.conf syntax is ok
nginx: configuration file /etc/nginx/nginx.conf test is successful
[root@lb01 conf.d]# systemctl restart nginx
[root@lb02 /etc/nginx/conf.d]# systemctl restart nginx
# 1.web开启https(三台web的wp文件都需要增加,或者可以在include文件中增加开启信息)
[root@web01 conf.d]# vim /etc/nginx/conf.d/wp.conf
server {
listen 80;
server_name www.wp.com;
root /code/wp;
index index.php index.html;
location ~ \.php$ {
fastcgi_pass 127.0.0.1:9000;
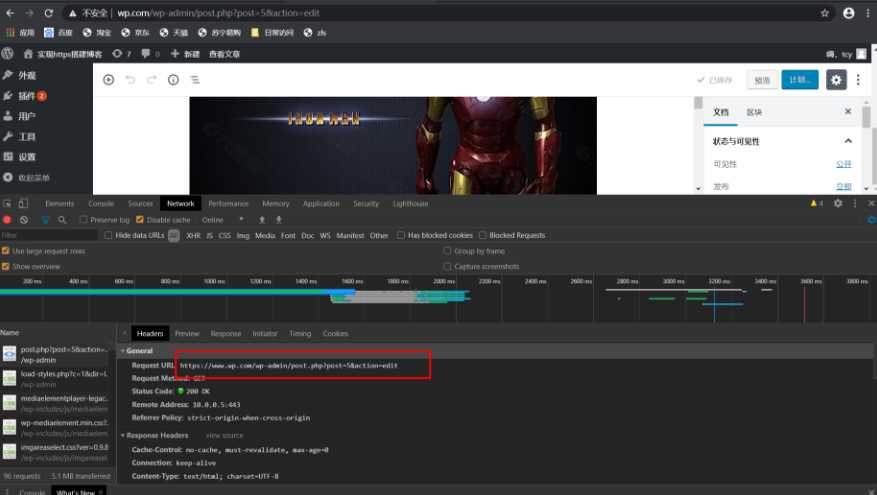
fastcgi_param HTTPS on; # 仅增多了此行
fastcgi_index index.php;
fastcgi_param SCRIPT_FILENAME $document_root$fastcgi_script_name;
include /etc/nginx/fastcgi_params;
}
}
# 2.web中开启https (三台web的zh配置文件都如下放所以,多增加注释一行信息)
[root@web01 conf.d]# vim /etc/nginx/conf.d/zh.conf
server {
listen 80;
server_name www.zh.com;
root /code/zh;
index index.php index.html;
location ~ \.php {
fastcgi_pass 127.0.0.1:9000;
fastcgi_param HTTPS on; # 多增加此行信息
fastcgi_index index.php;
fastcgi_param SCRIPT_FILENAME $document_root$fastcgi_script_name;
include /etc/nginx/fastcgi_params;
}
}
# 3.每台web都需重载配置文件
[root@web02 conf.d]# systemctl restart nginx
# 4.浏览器测试(先做好域名解析)
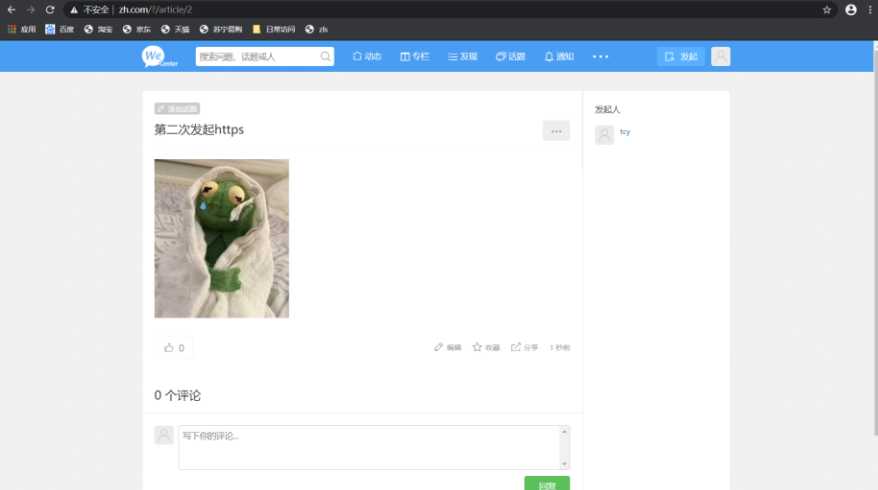
访问www.zh.com页面
查看之前新增页面
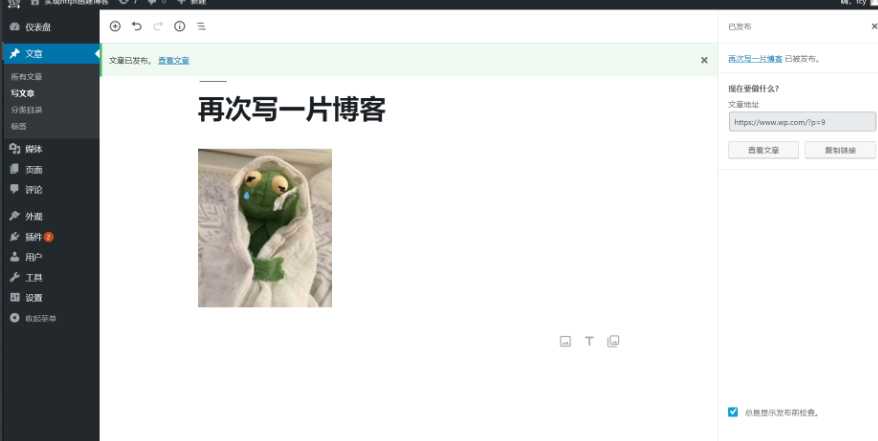
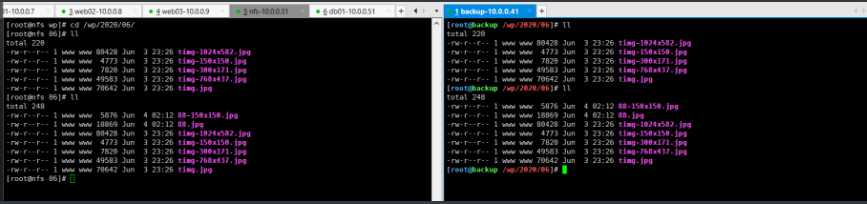
尝试多写一片文章,看后端是否会自动备份
# 1.keepalived安装
[root@lb01 ~]# yum install -y keepalived
[root@lb02 ~]# yum install -y keepalived
# 2.修改高可用配置文件
[root@lb01 ~]# vim /etc/keepalived/keepalived.conf # MASTER配置
global_defs { # 全局定义
router_id lb01 # 标识身份名称
}
vrrp_script sh { # 因keepalived并不会做到监控nginx,如nginx停止,
script "/etc/nginx/jiankong.sh" # keepalived服务依然存活,需要监本对nginx实现监控
interval 5 # 这里为指定脚本路径路径,及脚本运行间隔时长
}
vrrp_instance VI_1 { # 实例配置
state MASTER # 标识角色状态
interface eth0 # 网卡绑定接口
virtual_router_id 50 # 虚拟路由id
priority 150 # 优先级
advert_int 1 # 检测检测间隔时间
authentication { # 认证
auth_type PASS # 认证方式
auth_pass 1111 # 认证密码
}
virtual_ipaddress { # 虚拟地址配置
10.0.0.3 # 虚拟VIP地址
}
track_script { # 类似于nginx的引用upstream信息
sh # 这里可理解成引用定义脚本路径名称
}
}
# 3.创建脚本,使keepalived监测nginx,如nginx停止运行,keeplived也停止,那么master(vip)转移至bakcup上
[root@lb01 nginx]# cat /etc/nginx/jiankong.sh
#!/bin/bash
nginx_status=$(ps -C nginx --no-header|wc -l)
if [ $nginx_status -eq 0 ];then
systemctl start nginx
sleep 3
nginx_status=$(ps -C nginx --no-header|wc -l)
if [ $nginx_status -eq 0 ];then
systemctl stop keepalived
fi
fi
# 4.将脚本权限授予执行权限
[root@lb01 nginx]# chmod +x /etc/nginx/jiankong.sh
# 5.为lb02配置keepalived配置文件
[root@lb02 ~]# vim /etc/keepalived/keepalived.conf
global_defs {
router_id lb02 # 标识身份名称(不要和master一致,区分身份使用)
}
vrrp_instance VI_1 {
state backup # 标识角色状态
interface eth0 # 网卡绑定接口
virtual_router_id 50 # 虚拟路由id
priority 100 # 优先级(因是backup需要低于master,数值越大优先级越高)
advert_int 1 # 检测间隔时间
authentication { # 认证
auth_type PASS # 认证方式
auth_pass 1111 # 认证密码
}
virtual_ipaddress {
10.0.0.3 # 虚拟ip(需要和master中保持一致)
}
}
## 注意:如果是抢占式,脚本只需要放在MASTER上,如果是非抢占式,脚本必须放在MASTER和BACKUP上,所以此处backup不需要书写脚本
# 6.启动服务
[root@lb01 /]# systemctl start keepalived
[root@lb02 /]# systemctl start keepalived
# 1.书写脚本(防止出现master和backup无法通讯问题,同时出现两个vip地址,导致地址冲突,网页无法访问)
# 脚本翻译:在backup尝试ping两次master的ip,查看是否通讯,如果可以通讯,出现master和backup中同时存在vip地址,则将backup中的keepalived停止,如出现master具有vip,而backup没有,则页面输出正常,但如果出现最开始的ping都无法ping通master,直接输出信息。(建议最开始要使用密钥对方式连接master,否则,此脚本需要一直输入密码,而且在运行脚本时可以使用sh.sh &放在后台执行。)
[root@lb02 ~]# vim sh.sh
#!/bin/bash
vip=10.0.0.3
lb01_ip=10.0.0.5
while true;do
ping -c 2 $lb01_ip &>/dev/null
if [ $? -eq 0 ];then
lb01_vip_status=$(ssh $lb01_ip "ip add|grep $vip|wc -l")
lb02_vip_status=$(ip add|grep $vip|wc -l)
if [ $lb01_vip_status -eq 1 -a $lb02_vip_status -eq 1 ];then
echo ‘主节点和备节点都有VIP,开始关闭备节点的VIP...‘ >>/var/log/nginx/error.log
systemctl stop keepalived
elif [ $lb01_vip_status -eq 1 -a $lb02_vip_status -eq 0 ];then
echo ‘主节点存在vip,备节点没有vip,正常。。。‘ >>/var/log/messages
fi
else
echo ‘主节点无法通信‘ >>/var/log/nginx/error.log
fi
sleep 5
done
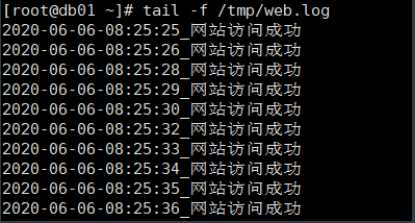
# 1.书写脚本,持续对网页状态码监控(因是https方式访问,出现长连接情况,此处需要301状态码为正常)
#!/bin/bash
while true;do
code_status=$(curl -I -m 10 -o /dev/null -s -w %{http_code} www.wp.com)
if [ $code_status -eq 301 ];then
echo "$(date +%F-%T)_网站访问成功" >> /tmp/web.log
else
echo "$(date +%F-%T)_网站访问失败,状态码是: $code_status" >> /tmp/web.log
fi
sleep 1
done
标签:rtu header location into grep 损坏 start $? creat
原文地址:https://www.cnblogs.com/tcy1/p/13061844.html