标签:chmod available 组成 term elm related sudo 应用程序 mos
在生成环境中k8s应用部署众多,需要一款可视化工具方便日常获知集群的实时状态,并为故障排查提供及时和准确的数据支持。在此背景下,Weaveworks的项目Weave Scope 应运而生,其是一款 Docker 和 Kubernetes 可视化监控工具。Scope 提供了至上而下的集群基础设施和应用的完整视图,用户可以轻松对分布式的容器化应用进行实时监控和问题诊断,以确保容器应用程序的稳定性和性能,通过查看容器上下文的度量/标记,以及原数据,在容器内部的进程之间可以轻松的确定运行服务消耗最多CPU/内存资源的容器,
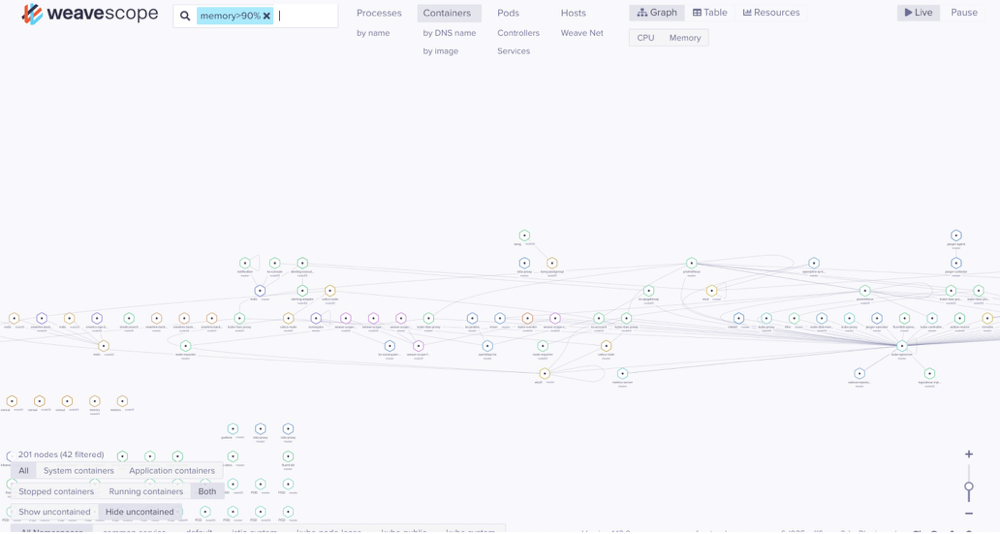
Weave Scope可以监控kubernetes集群中的一系列资源的状态、资源使用情况、应用拓扑、scale、还可以直接通过浏览器进入容器内部调试等,其提供的功能包括:
- 交互式拓扑界面
- 图形模式和表格模式
- 过滤功能
- 搜索功能
- 实时度量
- 容器排错
- 插件扩展
Weave Scope由App和Probe两部分组成:
Probe Agent负责收集容器和宿主的信息,并发送给 App
App 负责处理这些信息,并生成相应的报告,并以交互界面的形式展示
weave-scope-agent,集群每个节点上都会运行的 scope agent 程序,负责收集数据,其部署为DaemonSet模式。weave-scope-app,scope 应用,从 agent 获取数据,通过 Web UI 展示并与用户交互,其部署为Deployment模式。weave-scope-app,默认是 ClusterIP 类型,为了方便已通过 kubectl edit 修改为 NodePort。最初Weave Scope可以在运行Docker容器的宿主机进行安装部署
sudo curl -L git.io/scope -o /usr/local/bin/scope
sudo chmod a+x /usr/local/bin/scope
scope launch
之后访问http://宿主机IP:4040进行访问
kubectl apply -f "https://cloud.weave.works/k8s/scope.yaml?k8s-version=$(kubectl version | base64 | tr -d ‘\n‘)"
# 修改svc 为NodePort
kubectl patch svc $(kubectl get svc -n weave |grep weave-scope-app |awk ‘{print $1}‘) -p ‘{"spec":{"type": "NodePort"}}‘ -n weave
[root@master ~]# kubectl get svc -n weave |grep weave-scope-app
weave-scope-app NodePort 10.96.244.177 <none> 80:30156/TCP 52s
# 查看weave 的pod
[root@master ~]# kubectl get pod -n weave -o wide
NAME READY STATUS RESTARTS AGE IP NODE NOMINATED NODE READINESS GATES
weave-scope-agent-49csj 1/1 Running 0 7m58s 10.234.2.204 master <none> <none>
weave-scope-agent-lxjkb 1/1 Running 0 7m58s 10.234.2.132 node1 <none> <none>
weave-scope-agent-wp22d 1/1 Running 0 7m58s 10.234.2.160 node2 <none> <none>
weave-scope-app-85966885c8-9gf86 1/1 Running 0 7m59s 10.244.2.246 node2 <none> <none>
weave-scope-cluster-agent-5c9765fff6-hsl9r 1/1 Running 0 7m58s 10.244.2.247 node2 <none> <none>
目前helm 仓库提供了weave-scope编写好的charts,可以fetch到本地,进行简单的修改即可安装,非常方便快捷
[root@master common-service]# helm fetch stable/weave-scope
[root@master common-service]# tar -zxvf weave-scope-1.1.8.tgz
[root@master common-service]# sed -i "s@\ type:\ \"ClusterIP\"@ type: \"NodePort\"@" weave-scope/values.yaml
[root@master common-service]# helm install -n weave-scope --namespace common-service -f weave-scope/values.yaml weave-scope/
NAME: weave-scope
LAST DEPLOYED: Thu Jan 30 18:37:14 2020
NAMESPACE: common-service
STATUS: DEPLOYED
RESOURCES:
==> v1/ConfigMap
NAME DATA AGE
weave-scope-weave-scope-tests 1 1s
==> v1/DaemonSet
NAME DESIRED CURRENT READY UP-TO-DATE AVAILABLE NODE SELECTOR AGE
weave-scope-agent-weave-scope 4 4 0 4 0 <none> 1s
==> v1/Deployment
NAME READY UP-TO-DATE AVAILABLE AGE
weave-scope-cluster-agent-weave-scope 0/1 1 0 1s
weave-scope-frontend-weave-scope 0/1 1 0 1s
==> v1/Pod(related)
NAME READY STATUS RESTARTS AGE
weave-scope-agent-weave-scope-5xskf 0/1 ContainerCreating 0 1s
weave-scope-agent-weave-scope-76t2s 0/1 ContainerCreating 0 1s
weave-scope-agent-weave-scope-qb74g 0/1 ContainerCreating 0 1s
weave-scope-agent-weave-scope-zggff 0/1 ContainerCreating 0 1s
weave-scope-cluster-agent-weave-scope-5b8bf77f5f-7jkhq 0/1 ContainerCreating 0 1s
weave-scope-frontend-weave-scope-6d985ccff6-xmz2d 0/1 ContainerCreating 0 1s
==> v1/Service
NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE
weave-scope-weave-scope NodePort 10.233.41.4 <none> 80:31709/TCP 1s
==> v1/ServiceAccount
NAME SECRETS AGE
weave-scope-cluster-agent-weave-scope 1 1s
==> v1beta1/ClusterRole
NAME AGE
weave-scope-cluster-agent-weave-scope 1s
==> v1beta1/ClusterRoleBinding
NAME AGE
weave-scope-weave-scope 1s
NOTES:
You should now be able to access the Scope frontend in your web browser, by
going to the address or hostname of any node in the cluster, using http
and the port given by:
SCOPE_PORT=$(kubectl -n common-service get svc weave-scope-weave-scope -o jsonpath=‘{.spec.ports[?(@.name==http)].nodePort}‘); echo $SCOPE_PORT
Most likely one or more of the URLs given by this pipeline will work:
SCOPE_PORT=$(kubectl -n common-service get svc -o jsonpath=‘{.spec.ports[?(@.name==http)].nodePort}‘); kubectl get nodes -o jsonpath=‘{.items[0].status.addresses[*].address}‘ | xargs -I{} -d" " echo http://{}:$SCOPE_PORT
For more details on using Weave Scope, see the Weave Scope documentation:
https://www.weave.works/docs/scope/latest/introducing/
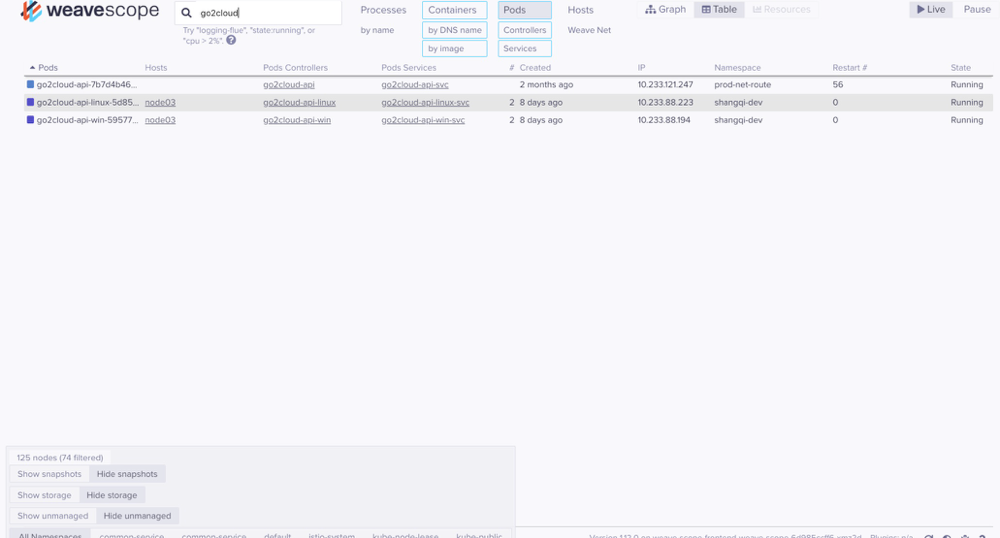
在此以POD资源对象为例,Weave Scope监控对象有进程、容器、pods、主机等,监控项有cpu、内存、平均负载等。
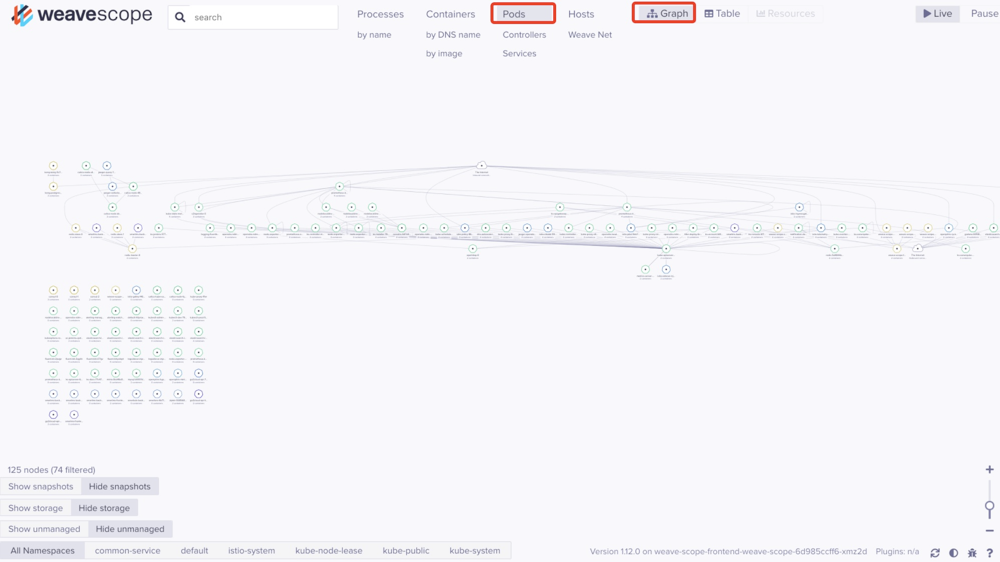
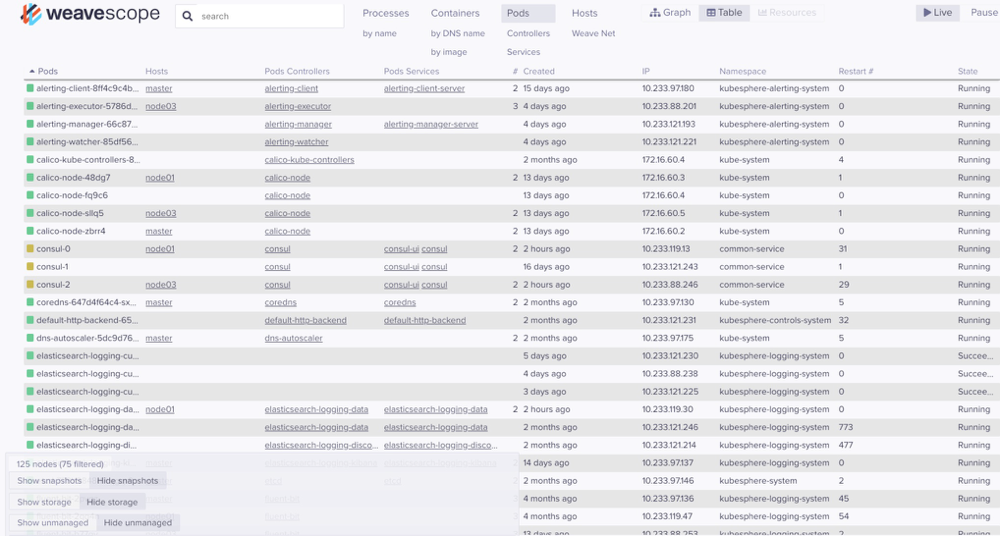
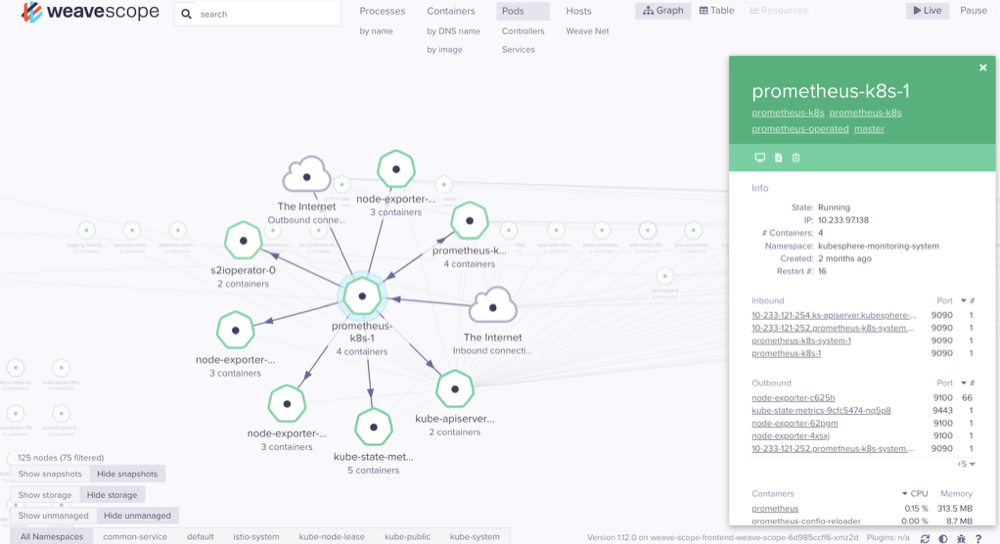
点击某个pod,会展示状态、资源使用、进程等详细信息
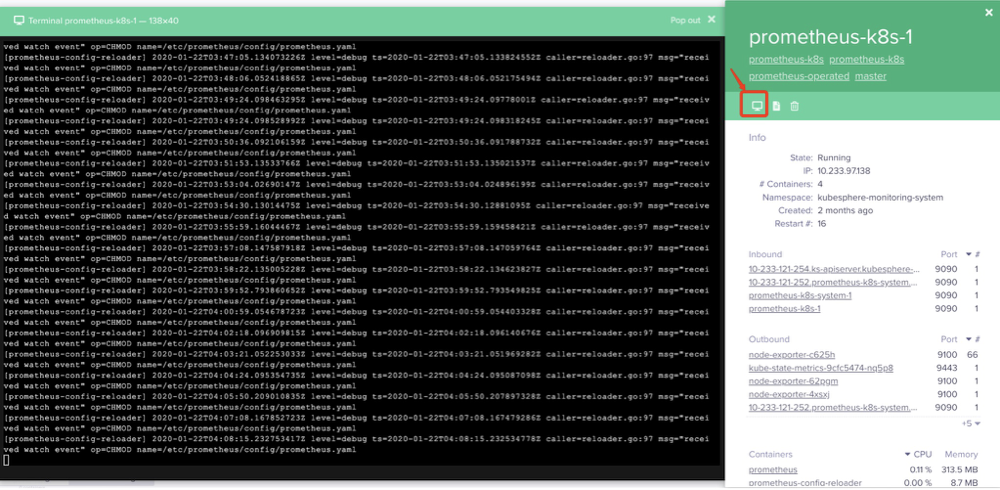
点击具体POD的get logs弹出Terminal窗口查看日志
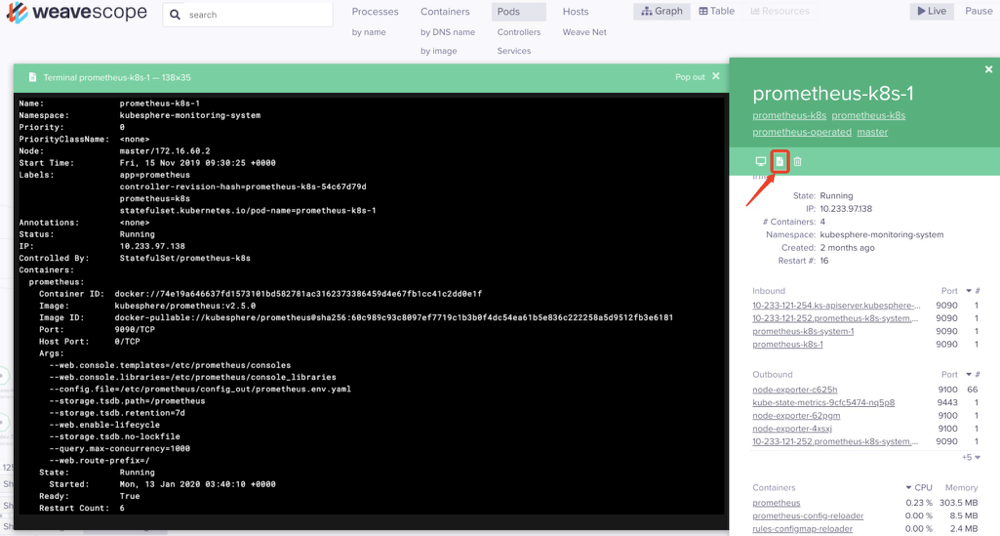
点击具体POD上的describe通过Terminal来查看POD资源信息
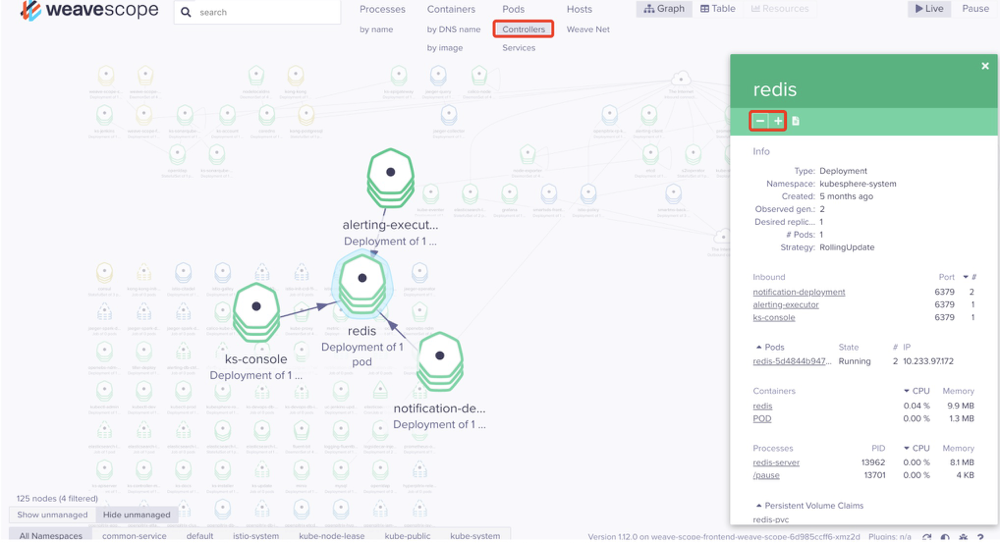
点击deployment类型的Controllers,可以来web界面来扩展或缩小以及查看POD的数量及详细信息。
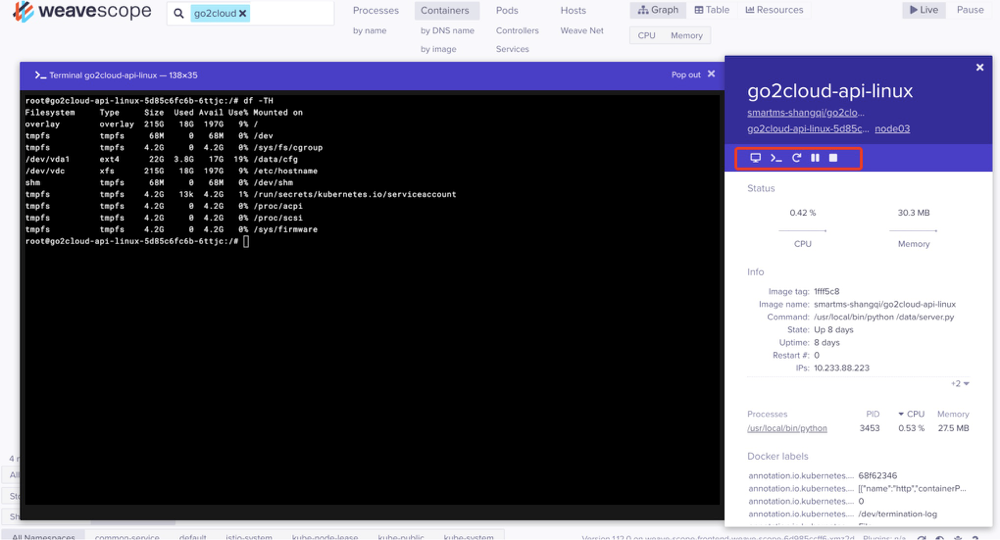
可以对容器进行attach、exec shell、restart、paus和stop操作以及容器日志查看
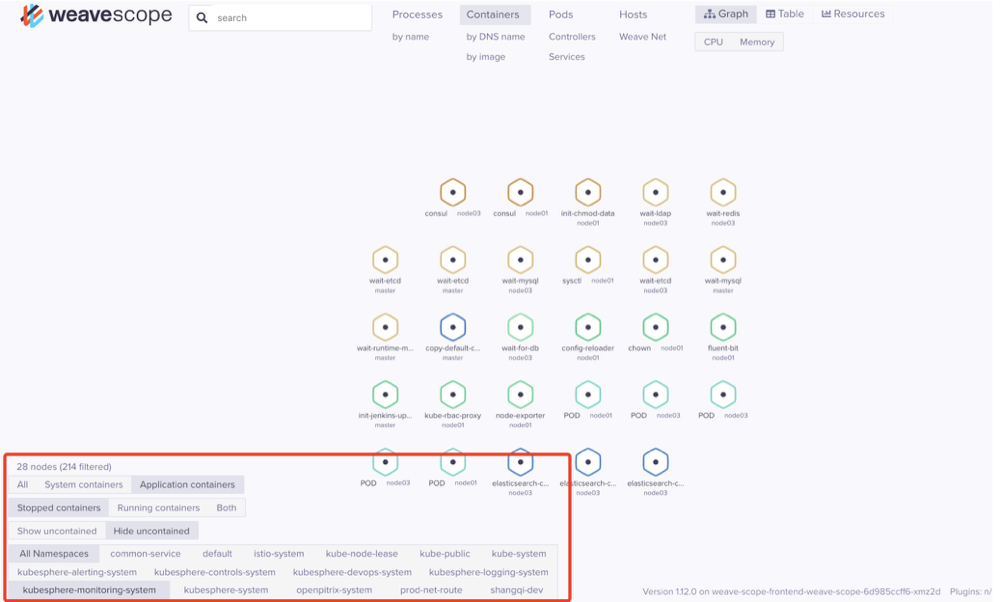
左下角可按条件展示,有容器类型(系统或者应用)、容器状态(停止或者运行)、命名空间等。
标签:chmod available 组成 term elm related sudo 应用程序 mos
原文地址:https://www.cnblogs.com/Python-K8S/p/13212031.html